Infoblox Trinzic
Infoblox Trinzic appliances are hardware devices that form the foundation of an organization’s network services and reporting solutions. You can configure this event source to send both DHCP and DNS logs.
Configure DHCP Logs
Before you can configure the SIEM (InsightIDR) event source, you must send Infoblox Trinzic messages to a syslog server from the NIOS appliance.
- From the “Grid” tab, select the Grid Manager > Members tab, and then click Grid Properties > Edit from the Toolbar.
- In the Grid Properties editor, select the Monitoring tab.
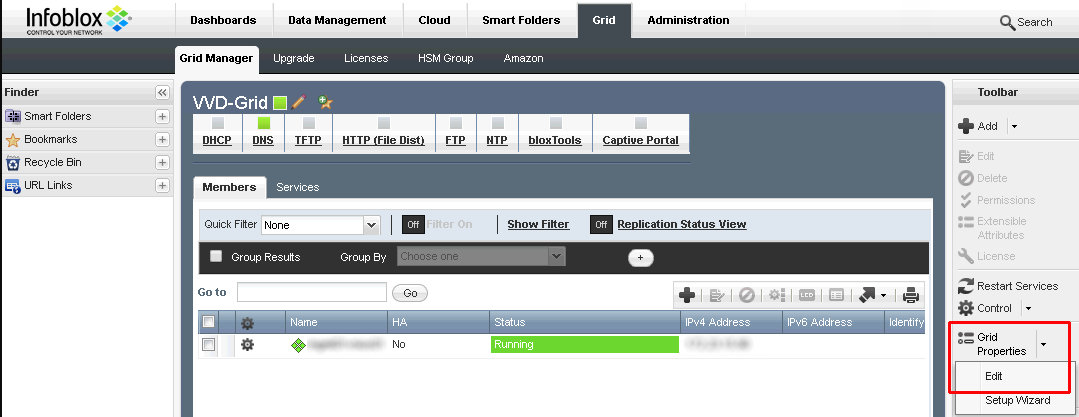
- In the “Syslog” section, specify the maximum size for a syslog file. Enter a value between 10 and 300. The default is 300.
- Check on the Log to External Syslog Servers checkbox.
- Click the + button to add a new server.
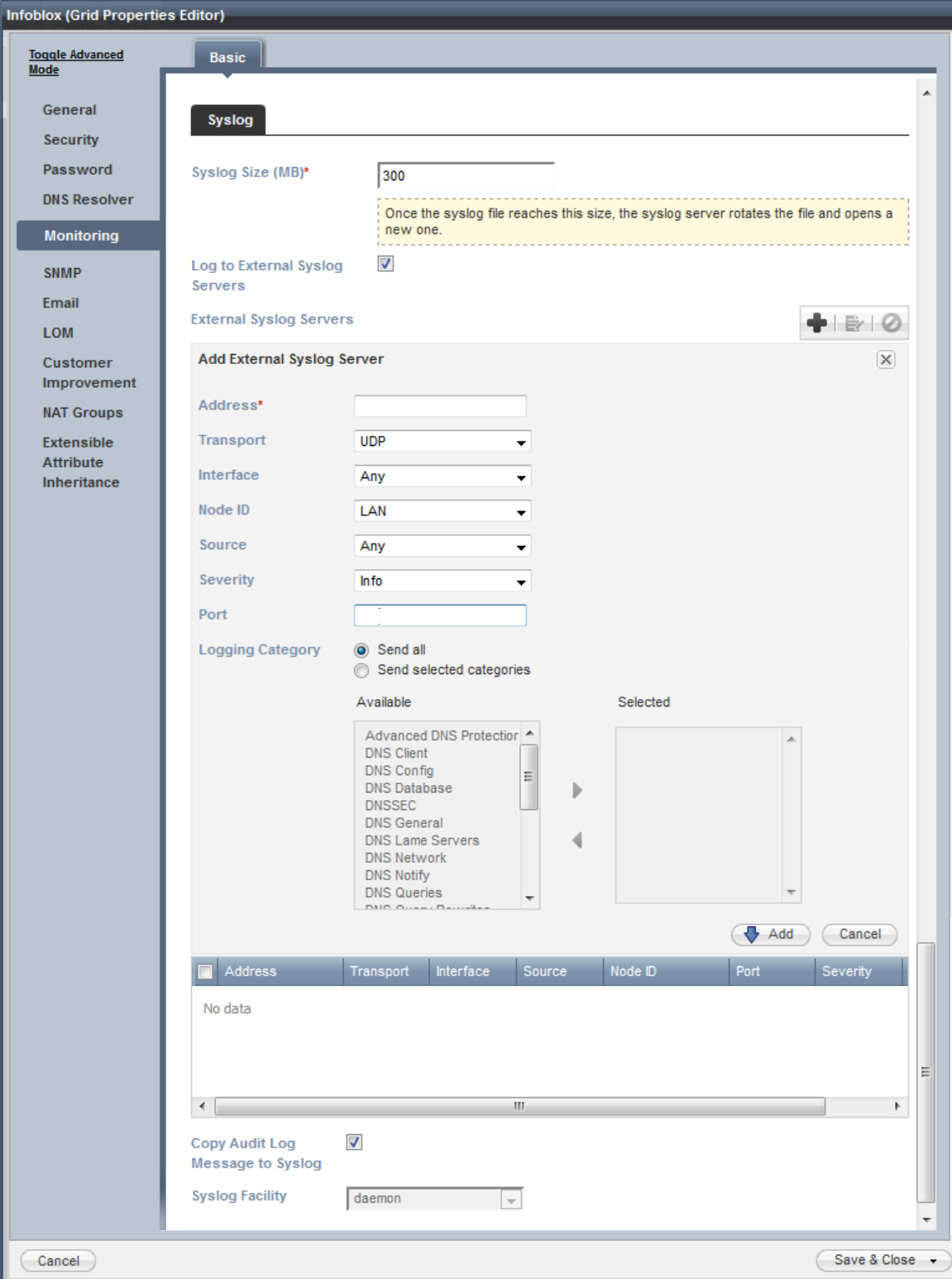
- In the “Address” field, enter the IP address of the SIEM (InsightIDR) collector.
- In the “Transport” field, select whether you want to send logs with TCP or UDP.
- From the “Interface” dropdown, select which appliance should be the origin of the Infoblox logs.
- From the “Source” dropdown, select which syslog messages you want to receive on the Collector.
- In the “Port” field, enter the port you want to use for the DHCP logs.
- From the “Severity” dropdown, select the severity filter “Info” to ensure that IDR receives DHCPACK messages.
- Check the Copy Audit Log Messages to Syslog checkbox to include audit log messages it sends to the syslog server.
- Select an option from the Syslog Facility dropdown that determines the processes and daemons from which the log messages are generated.
- Click the Save & Close button to save the configuration and click the Restart button if it appears at the top of the screen.
This configuration will parse Infoblox Trinzic as both DHCP and DNS.
If you ONLY want to send DNS logs, configure this event source as a DNS event source following the instructions below.
However, if you configure Infoblox Trinizic as a DHCP event source with DNS configured, and configure a separate DNS event source, your DNS events will be duplicated.
Configure DNS Logs
Infoblox Trinzic also supports DNS logs. However, you must configure DNS through the Infoblox Data Connector with these instructions: https://docs.infoblox.com/display/BloxOneThreatDefense/Data+Connector
Follow the instructions to:
- Install the Infoblox Data Connector
- Deploy the Infoblox Data Connector
You do not need to follow the instructions for the SIEM Integration.
When deploying the Data Connector, configure the external server as your SIEM (InsightIDR) Collector.
For further details, see their deployment guide for Implementing Infoblox Data Connector 3.0 here: https://docs.infoblox.com/download/attachments/8945695/deployment%20guide%20-%20data%20connector%203.0_Revised.pdf?version=1&modificationDate=1552637732892&api=v2
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Infoblox Trinzic in the event sources search bar.
- In the Product Type filter, select DHCP.
- Select the Infoblox Trinzic event source tile.
- Choose your collector. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Configure any Advanced Event Source Settings.
- Configure inactivity timeout threshold in minutes.
- Select a collection method.
- Optionally, choose to Encrypt the event source if choosing TCP by downloading the Rapid7 Certificate.
- Click Save.