ISC Bind9
ISC Bind9 is an open source software that allows you to publish your DNS events. Read more about Bind on their website: https://www.isc.org/downloads/bind/
Before You Begin
In order to capture data in SIEM (InsightIDR) from this event source, you must configure ISC Bind9 to send all query logs to syslog, and then forward them to the SIEM (InsightIDR) Collector. Read about how to do so on the Syslog Logging page.
You can configure ISC Bind9 to forward syslog by reading the directions in their logging recommendations here: https://kb.isc.org/article/AA-01526/0/BIND-Logging-some-basic-recommendations.html .
Configuring Linux
You must first enable and configure Linux to send logs
To configure logging on Linux configurations using RHEL7/OEL7/Centos7:
- Navigate to the location where you installed ISC Bind9.
- Using an SSH-Telnet Terminal emulator, enter the command
cat /etc/named.confto edit the filenamed.conf - Add the following channel to the
logging{} blocksection:
channel queries_log {
syslog local4;
print-time yes;
print-category yes;
print-severity yes;
severity debug;
};
category queries { queries_log; };Note that syslog local4 is the local facility that you are designating for syslog.
When you have completed, the logging{} section should look like this:
logging {
channel default_debug {
file "data/named.run";
severity dynamic;
};
channel queries_log {
syslog local4;
print-time yes;
print-category yes;
print-severity yes;
severity debug;
};
category queries { queries_log; };
};- Restart the
namedservice by entering the command:# systemctl restart named. This will stop, restart, and reload the configuration file. Note that#indicates that you are the administrator or root user. - Next, configure your local syslog daemon to send logs to your Collector. To do that, enter the following command
vi rsyslog.conf. Open the file in a text editor (such as Vim). - Then go to the bottom of the file and find
remote host is. Here, add in the IP address and host of your collector.
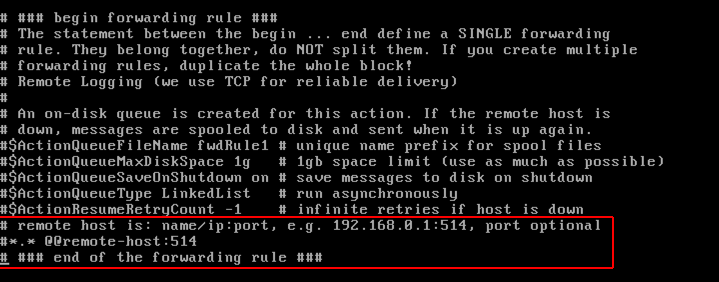
- Save your file.
- Finally, restart the
rsyslog servicewith the following command:# systemctl restart rsyslog
Expected Format
The Insight platform will process logs from this event source in the following format:
\<30>Apr 12 11:57:50 mydnsserver-03 named[32176]: 12-Apr-2018 11:57:50.373 client 10.1.1.101#24360 (ssl.gstatic.com): query: ssl.gstatic.com IN A + (10.2.1.22)Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for ISC Bind9 in the event sources search bar.
- In the Product Type filter, select DNS.
- Select the ISC Bind9 event source tile.
- Choose your collector. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally, choose to send unparsed logs.
- Configure the inactivity timeout threshold in minutes.
- Select a collection method and specify a port and a protocol.
- Optionally, choose to Encrypt the event source if choosing TCP by downloading the Rapid7 Certificate.
- Click Save.