Palo Alto
Firewalls are architected to safely enable applications and prevent modern threats. It identifies all network traffic based on applications, users, content and devices. The firewall(s) and another security device initiate and terminate VPN connections across the two networks. To set up the VPN tunnel and send traffic between the IKE Gateways, each peer must have an IP address—static or dynamic—or FQDN. The VPN peers use preshared keys or certificates to mutually authenticate each other.
Using Panorama by Palo Alto Networks?
Configure Panorama as a firewall, using the steps below.
Before You Begin
You must configure log forwarding for Palo Alto in order to collect the logs. You can read directions on how to do so at: https://docs.paloaltonetworks.com/pan-os/9-1/pan-os-admin/monitoring/configure-log-forwarding
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Palo Alto Networks Firewall & VPN in the event sources search bar.
- In the Product Type filter, select Firewall.
- Select the Palo Alto Networks Firewall & VPN event source tile.
- Choose your collector and event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Select an attribution source.
- Configure your default domain and any Advanced Event Source Settings.
- Select a collection method and specify a port and a protocol.
- Optionally choose to Encrypt the event source if choosing TCP by downloading the Rapid7 Certificate.
- Click Save.
Forward Palo Alto Traffic Logs to Syslog Server
You can learn about how to configure log forwarding in Palo Alto here:
https://live.paloaltonetworks.com/t5/Featured-Articles/Tips-amp-Tricks-Forward-traffic-logs-to-a-syslog-server/ta-p/71966 .
VPN and Wildfire logs
The Palo Alto event source includes firewall, VPN, and Wildfire logs.
Troubleshooting
If you are receiving firewall logs but not VPN logs, confirm that system logs are turned on and configured to forward to syslog. For more information, see https://docs.paloaltonetworks.com/pan-os/8-1/pan-os-admin/monitoring/view-and-manage-logs/log-types-and-severity-levels/system-logs.html .
To configure log forwarding to syslog follow these steps:
- Under the Device tab, navigate to Server Profiles > Syslog
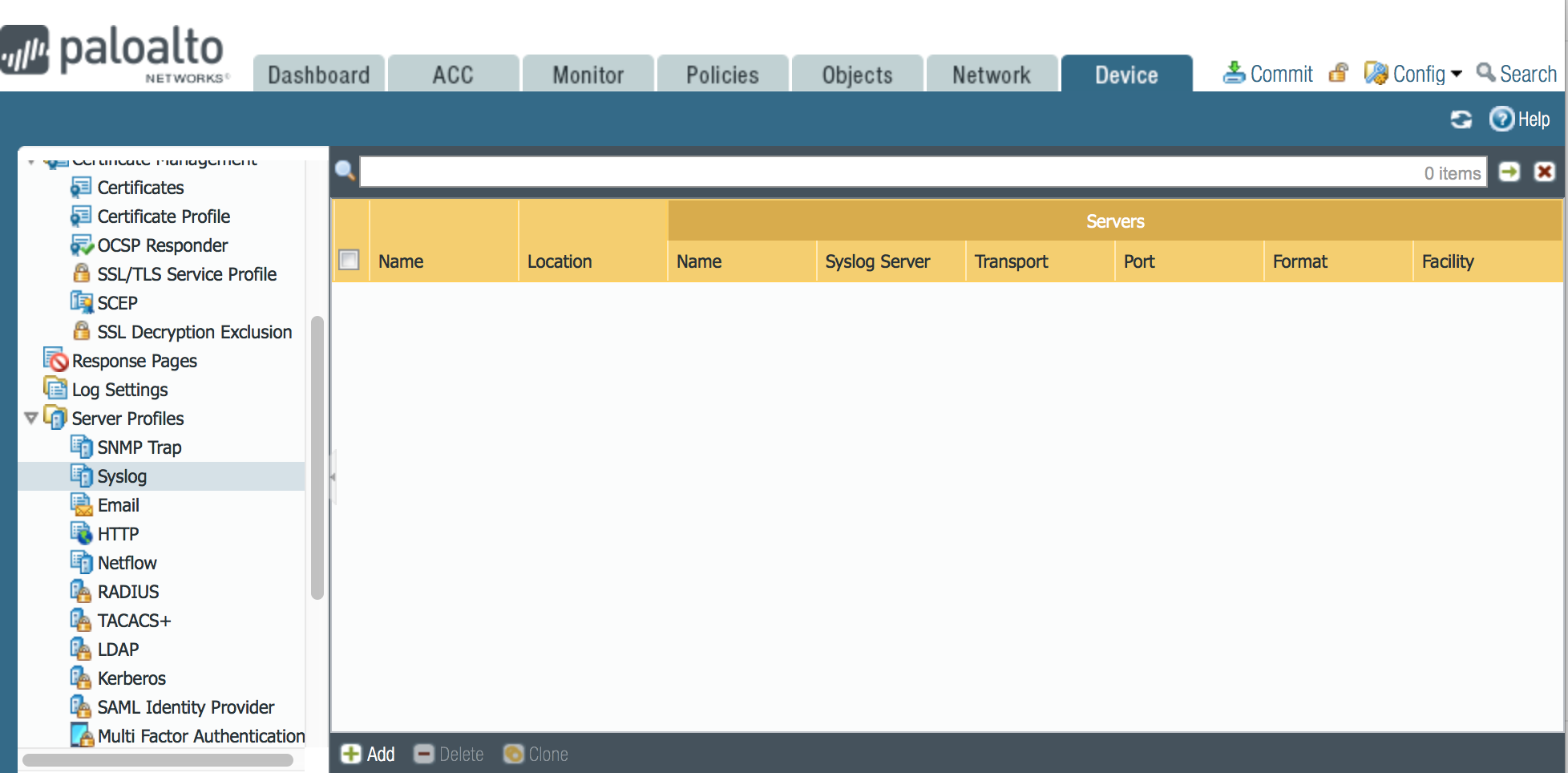
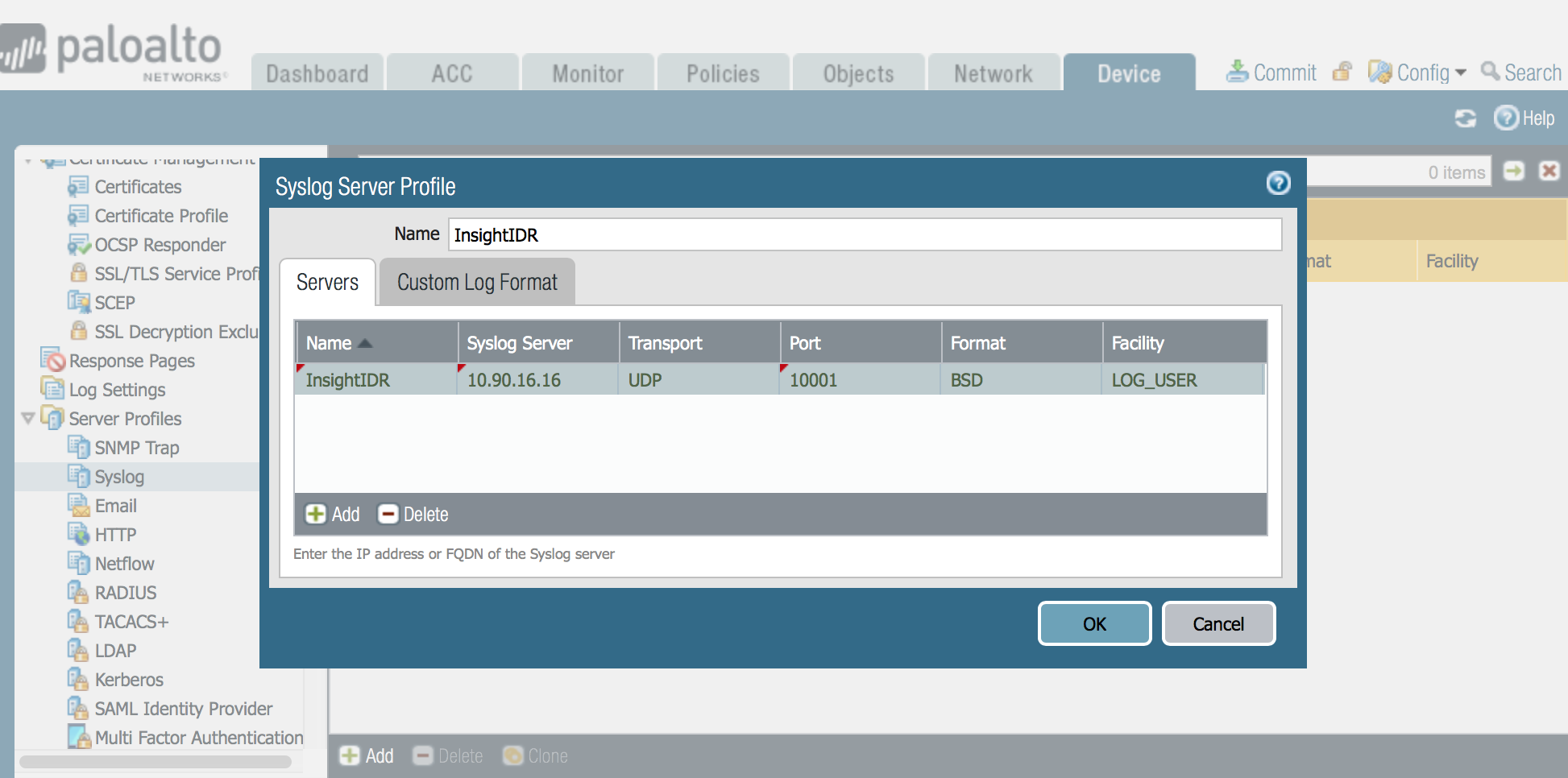
- Click Add to configure the log destination on the Palo Alto Network. You will need to enter the:
- Name for the syslog server
- Syslog server IP address
- Port number (change the destination port to the port on which logs will be forwarded; it is UDP 514 by default)
- Format (keep the default log format, BSD)
- Facility
- Click OK and your server profile will be created.
For more information, visit: https://knowledgebase.paloaltonetworks.com/KCSArticleDetail?id=kA10g000000ClRxCAK