Sentinel IPS
Sentinel Intrusion Prevention Systems (IPS) is network security software that provides threat protection and visibility, threat detection and response, and improved network performance. You can send Sentinel IPS logs to SIEM (InsightIDR) for IDS events.
To get started:
- Create a Network Address Translation
- Configure Remote Logging in Sentinel IPS
- Create an IDS Event Source
Create a Network Address Translation
Network Address Translation (NAT) protects the identity of a network by controlling traffic on your network’s internal and public IP addresses. Learn more about NAT here: https://www.cisco.com/c/en/us/support/docs/ip/network-address-translation-nat/26704-nat-faq-00.html
Because your Sentinel IPS appliance usually has a public IP address and your SIEM (InsightIDR) Collector will have an internal IP address, you will likely need to configure NAT or port-forwarding rules on your firewall or networking device to ensure Sentinel IPS can forward traffic to the SIEM (InsightIDR) Collector.
On your firewall during port forwarding or NAT configuration, we also advise that you restrict the source IP address to that of the Sentinel lPS device to ensure the SIEM (InsightIDR) Collector is secure.
Configure Remote Logging
After you create a NAT, you must add the SIEM (InsightIDR) Collector as a remote logging host for Sentinel IPS.
To configure remote logging for Sentinel IPS:
- Sign in to your Sentinel IPS console.
- From the top menu bar, select Configuration > System Controls > Remote Logging.
- In the “IP Address” field, provide the IP address of your SIEM (InsightIDR) Collector.
- In the “Port” field, enter the unique port through which SIEM (InsightIDR) will accept the Sentinel IPS traffic.
- Optionally choose which protocol you want to use, UDP or TCP.
- Click the Save button.
For more information on Sentinel IPS configuration, you can read the user guide here: https://sentinelips.com/wp-content/uploads/2017/09/Sentinel4UserInterfaceGuide.pdf
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
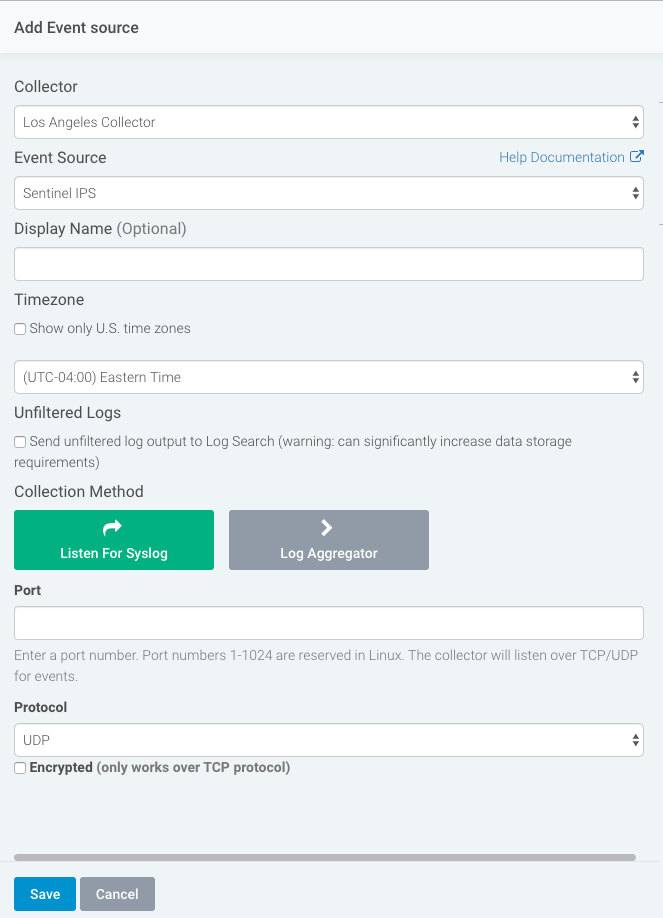
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Sentinel IPS in the event sources search bar.
- In the Product Type filter, select IDS.
- Select the Sentinel IPS event source tile.
- Choose your collector and select Sentinel IPS as your event source. You can also name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Select Syslog as your data collection method and specify the port and protocol you configured in Sentinel IPS.
- Click the Save button.