Symantec Endpoint Protection
Symantec Endpoint Protection (SEP) utilizes the endpoints on your network to work together in protecting data.
Before You Begin
SIEM (InsightIDR) can ingest data from Symantec Endpoint Protection in two ways: syslog and Watch Directory.
Syslog
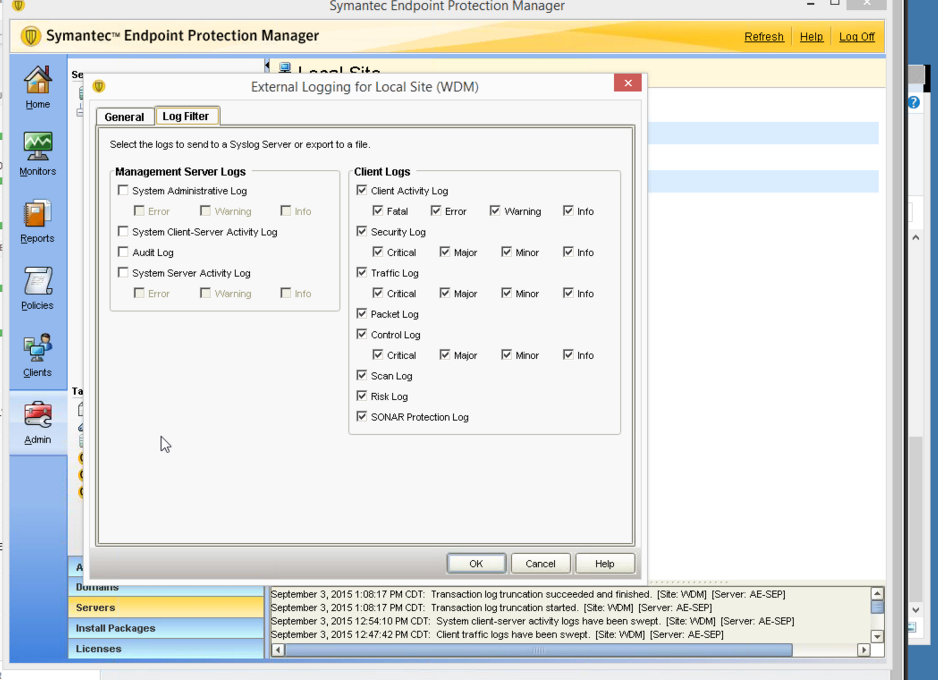
In the SEP Management Console, you must configure Symantec to send logs through syslog in the “External Logging settings” section. Read instructions on page 705 of the Administrator’s Guide here: https://support.symantec.com/en_US/article.DOC8645.html
Watch Directory
In the SEP Management Console, you must configure Symantec to send logs to a folder in the “External Logging settings” section. When configuring Symantec for syslog delivery, check off Export Logs to a Dump File. This option will log data to a single log folder instead of sending the logs to syslog.
Configure SIEM (InsightIDR) to collect data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
To configure the new event source in SIEM (InsightIDR):
- From the left menu, go to Data Collection and click Setup Event Source > Add Event Source.
- Do one of the following:
- Search for Symantec Endpoint Protection in the event sources search bar.
- In the Product Type filter, select Virus Scan.
- Select the Symantec Endpoint Protection event source tile.
- Select your collector and event source. You can name your event source if you want.
- Choose the timezone that matches the location of your event source logs.
- Optionally choose to send unparsed logs.
- Select an attribution source.
- Configure your default domain and any Advanced Event Source Settings.
- Select a collection method.
- Click Save.
Not seeing log data?
SIEM (InsightIDR) only parses an event from your Virus Scan event source when a virus is found.