Cisco Umbrella
Cisco Umbrella is a DNS, firewall, secure web gateway and cloud access security broker (CASB) event source that collects information about services, incidents and threats found on your network.
The event types that SIEM (InsightIDR) parses from this event source are:
- IP events
- AnyConnect events
- DNS events
- Cloud Firewall events
- Proxy events
Cisco Umbrella product logs can contain information about hosts and accounts, in addition to the source address. When you set up Cisco Umbrella as an event source, you will have the ability to specify the primary attribution source.
There are two ways to send data from your Cisco Umbrella account to SIEM (InsightIDR):
Access and secret keys must be rotated every 90 days
On May 15, 2025, Cisco-managed S3 buckets will require access and secret key rotation every 90 days. If your keys are not rotated within a 90-day period, data will not be sent from the Cisco-managed S3 buckets to SIEM (InsightIDR). Remember to update your event source configuration with the regenerated keys to ensure data collection is not interrupted.
For more information about this change, view Cisco’s announcement .
To set up the Cisco Umbrella event source, complete these steps:
- Read the requirements and complete any prerequisite steps.
- Configure Cisco Umbrella to send data to SIEM (InsightIDR).
- Configure SIEM (InsightIDR) to receive data from the event source.
- Test the configuration.
You can also:
Requirements
Before you start the configuration:
- To receive logs from Cisco Umbrella in SIEM (InsightIDR), you must configure an Amazon S3 Bucket to store the logs. Follow the instructions in the Cisco Umbrella documentation at: https://docs.umbrella.com/deployment-umbrella/docs/log-management#logging-to-amazon-s3 .
- Read about the supported regions for Amazon S3 in our Data Archiving documentation.
- If you have a Cisco managed bucket, your bucket’s Data Path might look something like this:
s3://my-managed-bucket/abcd1234. In this example, the Amazon S3 bucket name ismy-managed-bucketand the key prefix isabcd1234/. Learn more about key prefixes by visiting the AWS documentation at: https://docs.aws.amazon.com/AmazonS3/latest/userguide/object-keys.html .
Access Keys in AWS
In AWS, access keys consist of two parts: an access key ID, for example, AKIAIOSFODNN7EXAMPLE and a secret access key, for example, wJalrXUtnFEMI/K7MDENG/bPxRfiCYEXAMPLEKEY. You must use both the access key ID and secret access key together to authenticate your requests.
Configure Cisco Umbrella to send data to SIEM (InsightIDR)
To allow SIEM (InsightIDR) to receive data from Cisco Umbrella, you must configure the settings in your Cisco account to provide access to its data.
- Log in to the Cisco Umbrella console and go to Settings > Log Management.
- Select the option to use either your own Amazon S3 bucket or the Cisco-managed S3 bucket.
- Select your region and click Save. The console takes a few moments to activate.
- Record the Bucket Name, Access Key, and Secret Key from the confirmation message to enter later in SIEM (InsightIDR).
- Select Got It and click Continue. A confirmation message informs you that Cisco is sending logs to the Amazon S3 bucket.
Configure SIEM (InsightIDR) to receive data from the event source
After you complete the prerequisite steps and configure the event source to send data, you must add the event source in SIEM (InsightIDR).
Task 1: Select Cisco Umbrella
- From the Command Platform main menu, go to Data Connectors > Data Collectors.
- Go to the Event Sources tab, then click Add Event Source.
- Do one of the following:
- Search for Cisco Umbrella in the event sources search bar.
- In the Product Type filter, select DNS.
- Select the Cisco Umbrella event source tile.
Task 2: Set up your collection method
There are two methods of collecting data from Cisco Umbrella; through a cloud connection or through a Collector.
New credentials are required for cloud event sources
You cannot reuse existing on-premise credentials to create a cloud connection with this event source. You must create new credentials.
Use the Cloud Connection method
- In the Add Event Source panel, select Run On Cloud.
- In the Event source name field, name the event source. This will become the name of the log that contains the event data in Log Search. If you do not name the event source, the log name defaults to Cisco Umbrella.
- Under Connectivity Details, click Add a New Connection.
- On the Create a Cloud Connection screen, enter a name for the new connection in the Connection Name field.
- In the Bucket Region field, enter the region of the Amazon S3 bucket. For the precise format of this value, review the table of supported regions.
- In the AWS Access Key ID field, add a new credential:
- Name your credential.
- Describe your credential.
- Select the credential type.
- Enter the AWS Access Key ID, which is the Access Key you obtained in Configure Cisco Umbrella to send data to SIEM (InsightIDR).
- Specify the product access for this credential.
- In the AWS Secret Access Key field, add a new credential:
- Name your credential.
- Describe your credential.
- Select the credential type.
- Enter the AWS Secret Access Key, which is the Secret Key you obtained in Configure Cisco Umbrella to send data to SIEM (InsightIDR).
- Specify the product access for this credential.
- Click Save to save the the new connection and return to the Add Event Source panel.
- In the Amazon S3 Bucket Name field, enter the name of the Amazon S3 Bucket that you created. For example, if your bucket data path is
s3://my-managed-bucket/abcd1234, the bucket name ismy-managed-bucket. - Optionally, specify a folder path in the Amazon S3 Key Prefix field, followed by a
/. This prefix defines the folder where your logs are stored within your S3 bucket. For example, if your bucket path iss3://my-managed-bucket/abcd1234, the key prefix isabcd1234/. Be sure to include the/at the end of the prefix string.- If your logs aren’t stored in a specific folder, leave this field blank.
- Learn more about prefixes at: https://docs.aws.amazon.com/AWSImportExport/latest/DG/ManipulatingS3KeyNames.html .
- Optionally, select the option to send unparsed data.
- Under User Attribution, select an attribution source.
- Click Save.
Use the Collector method
- In the Add Event Source panel, select Run On Collector.
- In the Event source name field, name the event source. This will become the name of the log that contains the event data in Log Search. If you do not name the event source, the log name defaults to Cisco Umbrella.
- Select your collector from the Collector dropdown menu.
- Select an AWS Authentication option. We recommend that you select IAM User Credential.
- Select your existing credentials from the Credential dropdown or, optionally, create a new credential.
- In the Amazon S3 Bucket Name field, enter the name of the Amazon S3 Bucket that you created. For example, if your bucket data path is
s3://my-managed-bucket/abcd1234, the bucket name ismy-managed-bucket. - Optionally, specify a folder path in the Amazon S3 Key Prefix field, followed by a
/. This prefix defines the folder where your logs are stored within your S3 bucket. For example, if your bucket path iss3://my-managed-bucket/abcd1234, the key prefix isabcd1234/. Be sure to include the/at the end of the prefix string.- If your logs aren’t stored in a specific folder, leave this field blank.
- Learn more about prefixes at: https://docs.aws.amazon.com/AWSImportExport/latest/DG/ManipulatingS3KeyNames.html .
- Select the Bucket Region Name.
- Enter the refresh rate in minutes. A recommended rate is 10 minutes.
- Optionally, choose to send unparsed logs.
- Select an attribution source.
- Set the timezone to UTC, as Cisco Umbrella always uses the UTC time zone for logging.
- Click Save.
Supported Amazon S3 Bucket Regions
The value you enter for the Cisco Amazon S3 bucket region must follow a specific shortened format. For example, if the bucket region is US_WEST_N_CALIFORNIA, you must enter the corresponding short name, us-west-1.
| Amazon S3 Region | Short Name | URL |
|---|---|---|
| AF_CAPE_TOWN (Africa (Cape Town)) | af-south-1 | https://s3-af-south-1.amazonaws.com |
| AP_HONG_KONG (Asia Pacific (Hong Kong)) | ap-east-1 | https://s3-ap-east-1.amazonaws.com |
| AP_JAKARTA (Asia Pacific (Jakarta)) | ap-southeast-3 | https://s3-ap-southeast-3.amazonaws.com |
| AP_MUMBAI (Asia Pacific (Mumbai)) | ap-south-1 | https://s3-ap-south-1.amazonaws.com |
| AP_OSAKA (Asia Pacific (Osaka)) | ap-northeast-3 | https://s3-ap-northeast-3.amazonaws.com |
| AP_SEOUL (Asia Pacific (Seoul)) | ap-northeast-2 | https://s3-ap-northeast-2.amazonaws.com |
| AP_SINGAPORE (Asia Pacific (Singapore)) | ap-southeast-1 | https://s3-ap-southeast-1.amazonaws.com |
| AP_SYDNEY (Asia Pacific (Sydney)) | ap-southeast-2 | https://s3-ap-southeast-2.amazonaws.com |
| AP_TOKYO (Asia Pacific (Tokyo)) | ap-northeast-1 | https://s3-ap-northeast-1.amazonaws.com |
| CA_CENTRAL (Canada (Central)) | ca-central-1 | https://s3-ca-central-1.amazonaws.com |
| EU_FRANKFURT (EU (Frankfurt)) | eu-central-1 | https://s3-eu-central-1.amazonaws.com |
| EU_IRELAND (EU (Ireland)) | eu-west-1 | https://s3-eu-west-1.amazonaws.com |
| EU_LONDON (EU (London)) | eu-west-2 | https://s3-eu-west-2.amazonaws.com |
| EU_MILAN (EU (Milan)) | eu-south-1 | https://s3-eu-south-1.amazonaws.com |
| EU_PARIS (EU (Paris)) | eu-west-3 | https://s3-eu-west-3.amazonaws.com |
| EU_STOCKHOLM (EU (Stockholm)) | eu-north-1 | https://s3-eu-north-1.amazonaws.com |
| ME_BAHRAIN (Middle East (Bahrain)) | me-south-1 | https://s3-me-south-1.amazonaws.com |
| MME_UAE (Middle East (UAE)) | me-central-1 | https://s3-me-south-1.amazonaws.com |
| SA_SAO_PAULO (South America (Sao Paulo)) | sa-east-1 | https://s3-sa-east-1.amazonaws.com |
| US_EAST_GOV (US East (GovCloud)) | us-gov-east-1 | https://s3-us-gov-east-1.amazonaws.com |
| US_EAST_GOV_FIPS (US East (FIPS GovCloud)) | us-gov-east-1 | https://s3-fips-us-gov-east-1.amazonaws.com |
| US_EAST_OHIO (US East (Ohio)) | us-east-2 | https://s3-us-east-2.amazonaws.com |
| US_EAST_VIRGINIA (US Standard) | us-east-1 | https://s3.amazonaws.com |
| US_WEST_GOV (US West (GovCloud)) | us-gov-west-1 | https://s3-us-gov-west-1.amazonaws.com |
| US_WEST_GOV_FIPS (US West (FIPS GovCloud)) | us-gov-west-1 | https://s3-fips-us-gov-west-1.amazonaws.com |
| US_WEST_N_CALIFORNIA (US West (N. California)) | us-west-1 | https://s3-us-west-1.amazonaws.com |
| US_WEST_OREGON (US West (Oregon)) | us-west-2 | https://s3-us-west-2.amazonaws.com |
Test the configuration
The event types that SIEM (InsightIDR) parses from this event source are:
- IP events
- AnyConnect events
- DNS events
- Cloud Firewall events
- Proxy events
To test that event data is flowing into SIEM (InsightIDR) through the cloud-to-cloud connection:
- View the raw logs.
- From the Data Collection Management page, click the Event Sources tab.
- Find the event source you created and click View raw log. If the Raw Logs modal displays raw log entries, logs are successfully flowing to SIEM (InsightIDR).
- Use Log Search to find the log entries. After approximately seven minutes, you can verify that log entries are appearing in Log Search.
- From the left menu, go to Log Search.
- In the Log Search filter, search for the new event source you created.
- Select the log sets and the log names under each log set. Cisco Umbrella logs flow into these log sets:
- DNS Query Documents: Contains DNS events.
- Web Proxy Documents: Contains proxy events.
- Advanced Malware Documents: Contains IP events.
- Firewall Documents: Contains Cloud Firewall events.
- Set the time range to Last 10 minutes and click Run.
The Results table displays all log entries that flowed into SIEM (InsightIDR) in the last 10 minutes. The keys and values that are displayed are helpful when you want to build a query and search your logs.
Sample logs
To help you visualize the event logs that this event source generates, here are some sample logs:
Example DNS Event
"\"2020-05-12 14:24:50\",\"Rapid.Seven (Rapid.Seven@gmail.\",\"Rapid.Seven (Rapid.Seven@gmail.,VPN,HQ,HQ\",\"20.21.103.71\",\"174.237.215.230\",\"Allowed\",\"1 (A)\",\"NOERROR\",\"rapid.seven.yahoo.com.\",\"Search Engines,Infrastructure\",\"AD Users\",\"AD Users,Internal Networks,Sites,Networks\",\"\""Example Proxy Event (22 fields)
"\"2020-06-16 05:06:14\",\"RPD07 (RPD07@rapid7.com)\",\"170.10.200.60\",\"80.240.220.170\",\"100.160.180.70\",\"\",\"ALLOWED\",\"http://some-location.com/hello.txt\",\"\",\"Microsoft-CryptoAPI/10.0\",\"200\",\"211\",\"1240\",\"\",\"\",\"Software/Technology,Business Services,Infrastructure\",\"\",\"\",\"\",\"\",\"\",\"AD Users\""Example Proxy Event (23 fields)
"\"2020-06-16 13:38:26\",\"RPD-7-10001337\",\"190.160.1.170\",\"70.170.40.50\",\"20.40.200.20\",\"text/plain\",\"ALLOWED\",\"http://some-location.com/hello.txt\",\"\",\"Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:77.0) Gecko/20100101 Firefox/77.0\",\"200\",\"\",\"377\",\"8\",\"81b2bd4ea98c8db66554fbc8d7637a1a69a130f331feb732b75abc1234568fd5\",\"Infrastructure\",\"\",\"\",\"\",\"\",\"\",\"Anyconnect Roaming Client\",\"\""Example IP Event
"\"2020-04-22 22:54:21\",\"R7's MacBook Pro\",\"100.109.104.218\",\"46292\",\"64.251.89.57\",\"554\",\"Malware\",\"Roaming Computers\""Example Cloud Firewall Event
"\"2019-01-14 18:03:46\",\"[322140933]\",\"Passive Monitor\",\"CDFW Tunnel Device\",\"OUTBOUND\",\"1\",\"84\",\"173.18.4.5\",\"46292\",\"147.113.255.130\",\"554\",\"ams1.edc\",\"12\",\"ALLOW\""Troubleshooting
If you experience issues with the Duo Security event source, try the solutions provided in this section.
- S3 Error: AccessDenied, Access Denied
- Unexpected Request Code 301
- Unable to Find Valid Certification Path to Requested Target
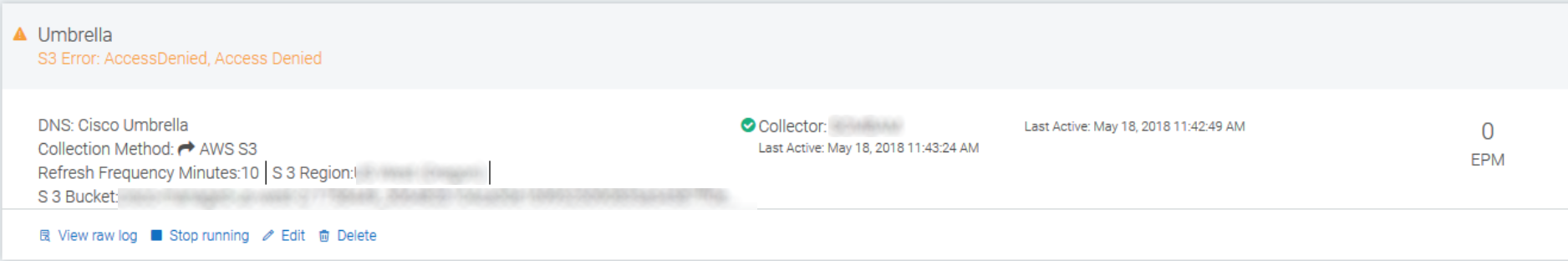
S3 Error: AccessDenied, Access Denied
If you see this error on your Cisco Umbrella event source, you may have entered some information incorrectly (specifically the S3 Bucket and the Key Prefix). First, verify that the information was entered correctly from the Cisco Umbrella configuration. If you still see this error, delete and reconfigure the event source.
Second, verify that the AmazonS3ReadOnlyAccess managed policy is attached to the IAM credentials that are configured in the event source connection. This is necessary to be able to read from the bucket. For more information, visit https://docs.aws.amazon.com/aws-managed-policy/latest/reference/AmazonS3ReadOnlyAccess.html .
If this error is still present after you have confirmed that all the information is correct, test your credentials for AWS using the AWS Command Line Interface (CLI). See the instructions on configuring your AWS CLI at: https://docs.aws.amazon.com/cli/latest/userguide/cli-chap-getting-started.html .
Non-Cisco Managed Customers
If you are experiencing the error above, try adding a trailing / to your S3 prefix.
Integration warning: unexpected error in the integration pipeline
If you encounter this error while configuring a cloud connection, ensure that you entered the correct short name in the Bucket Region field. Do not enter long name for the S3 bucket region.
To find the short name value you must enter, review the table in the Supported Amazon S3 bucket regions section.
Unexpected Request Code 301
If you encounter this error, ensure that you are using the correct S3 bucket region.
Unable to Find Valid Certification Path to Requested Target
If you encounter this error, there is an issue with your certificate likely caused by a web proxy performing SSL/TLS inspection.
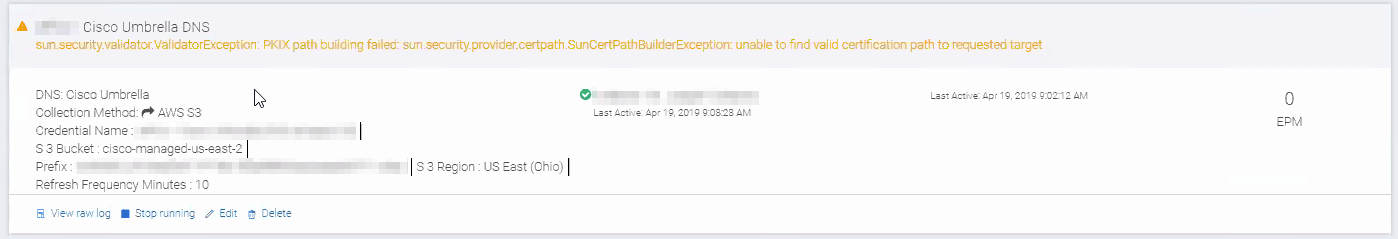
You can perform the following in attempt to resolve this issue:
- Reconfigure the appropriate proxy to allow traffic to the S3 address where your bucket is located.
- Check that Cisco Umbrella has allowed traffic to the S3 address where your bucket is located.
- Check that Cisco Umbrella is not blocking traffic to your desired S3 bucket location.