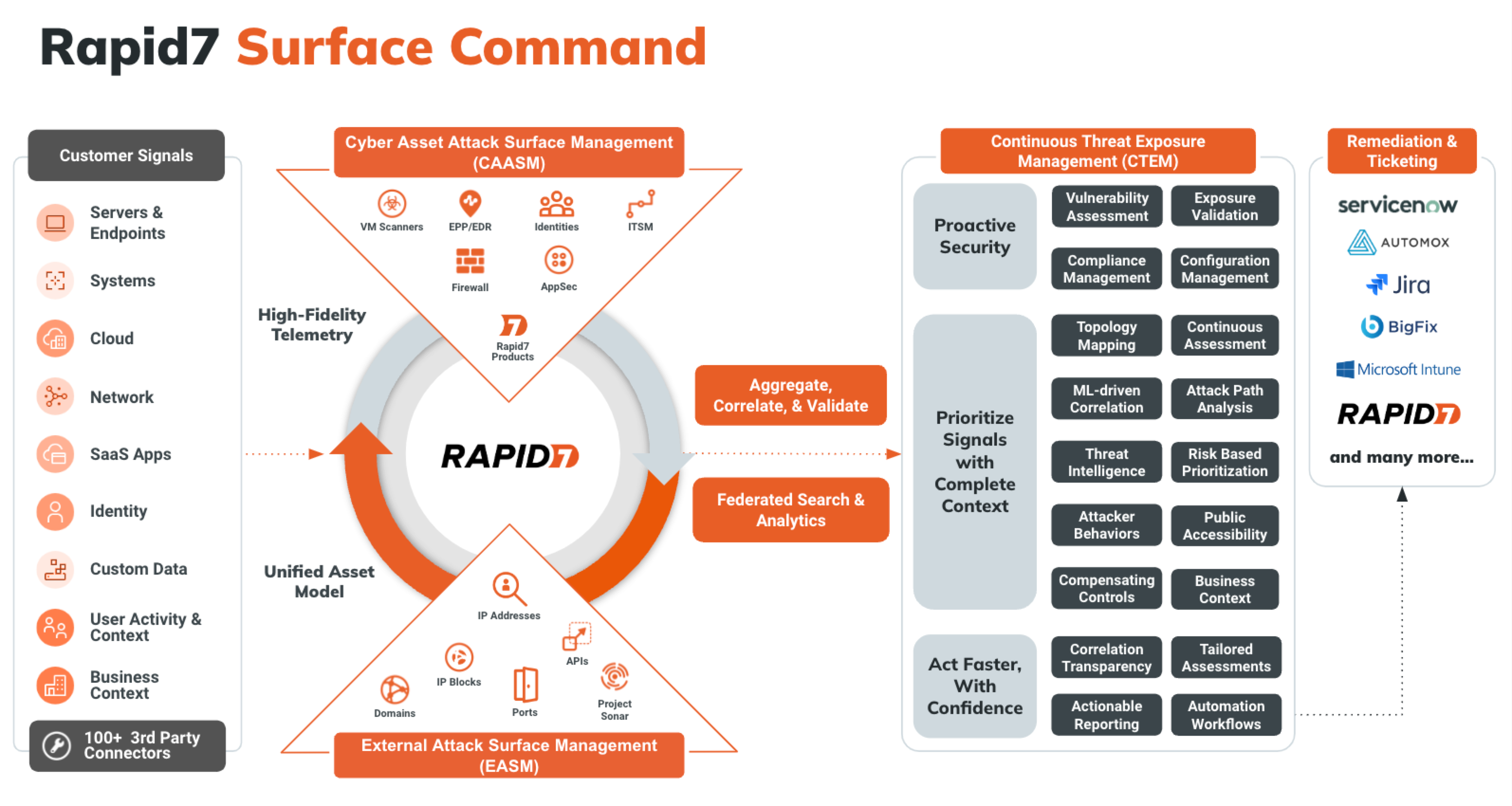
Surface Command Overview
Surface Command breaks down data silos by combining comprehensive attack surface visibility across hybrid environments to build a dynamic 360-degree view of your entire attack surface in one place. External scans provide an adversary’s perspective on the attack surface, detecting and validating exposures while highlighting areas attackers are most likely to target.
Surface Command combines these external scans with a detailed inventory of your internal assets, no matter the security or IT tool used to scan them. This process delivers complete visibility into your attack surface without the risk of blind spots, unprotected assets, and ungoverned access. Understanding how assets are configured assists in quickly identify and address misconfigurations, shadow IT, and compliance issues. This integrated approach gives you a holistic view of your digital landscape, enabling proactive risk mitigation, threat prevention, and rapid response.
Surface Command is accessible from the Solutions sub-menu on the Command Platform. You can also navigate directly to points of interest within Surface Command by interacting with the Attack Surface Overview or the other Attack Surface-related navigation menu items.
Looking for Surface Command Access Control?
For detailed information on Surface Command entitlements and access control, visit Role-Based Access Control.
Key concepts and components
- Connectors - A software component that Surface Command uses to interface with an information source to collect data about the objects in their environment. An information source is an existing system or data source, such as vulnerability scanning tools, endpoint protection technologies, or cloud service providers, that has information about any object of interest. Each connector is designed to understand the specifics of the targeted information source’s API and data schemas. Surface Command provides Connectors for most major security tools, but custom Connectors can be built for your enterprise-specific systems. Review Connectors for more information.
- Orchestrator - A server that can access and collect data from information sources and execute operations. An orchestrator is installed in the customer’s environment when the Surface Command platform cannot access an information source, such as an application behind a firewall, or when an application's APIs reside on a private cloud network. Once deployed, an orchestrator is paired to the platform. 1 or more Connectors are then assigned to the orchestrator.
- Profile - A distinct grouping of credentials and import feeds for a given connector.
- Import Feed - A scheduled software job that performs a specific process like importing data from an information source. Connectors can have multiple associated Import Feeds.
- Attack Surface - Your attack surface is divided into two parts: internal and external. In Surface Command, your internal attack surface is composed of assets and identities while your external attack surface is composed of IP addresses, domains, network services, and certificates. The external attack surface discovery process is driven by domain and IP seeds. For more information, review Explore Your Attack Surface.
- Asset - Assets are network-attached compute devices, including servers, workstations, mobile devices, storage devices, network devices, and printers. Surface Command creates the representations of assets automatically when data is ingested into the system by a Connector.
- Identity - Identities are identification-based entities, including user names, service accounts, shared email inboxes, and other non-human identities.
- Seed - A domain, subdomain, CIDR range, or IP address that is externally accessible and can be used to discover other externally accessible assets, such as an SSL certificate, subdomain, or network service (for example, SMTP, FTP).
- Type - Describes the structure of the data for a specific type of asset or identity. Every data record is associated with an exact technical description of the structure and semantics of its properties. Each Connector defines its own set of types. Surface Command unifies all the types that pertain to the same class of object, such as a server or a vulnerability, into a set of pre-defined unified types. For example, different information sources might provide information about a single device from the perspective of an EC2 Instance, CrowdStrike Device, SentinelOne Agent, and Tenable.io Asset. They all pertain to the same device and the unified type would be Server. You can use unified asset types, each information source’s asset types, or both when writing queries to select specific results. For more information on the Unified Asset Model, review Explore unified properties.
- Query - A tool used to select and display specific data that was ingested by Connectors. A query cannot add or change data. Some queries are included with Surface Command by default or included with a given Connector. You can also write your own queries to retrieve the data of interest to you. Queries are written in Cypher, which is a standards-based graph query language. Surface Command also provides a graphical interface for building basic queries without needing to understand Cypher. For more information, review Workspace and Queries.
- Reference list - Enterprise or industry data that is not accessible by a Connector but is collected from Microsoft Excel (
.xlsx) or CSV files. For example, it could be a spreadsheet that maps network addresses to physical locations or business owners. Reference lists let you combine this data with other information pulled from information sources when building queries.
- Reference list - Enterprise or industry data that is not accessible by a Connector but is collected from Microsoft Excel (
- Dashboard - A user-created collection of widgets. You can use and organize dashboards to present and monitor any aspect of your security posture. For more information, review Dashboards and Widgets.
- Widget - A component that displays a specific dataset in a dashboard. A widget retrieves data from a query, filters the results to show specific data, and presents that data in a customized chart or graphic. You can configure the type of graph and how it calculates values. Since a widget filters the results from a query, you can have several different widgets based on a single query. The Surface Command home page has a set of pre-defined widgets, where each widget provides a count of assets of a specific unified type. These are not editable.
- Workflow - A set of steps that perform 1 or more actions driven by query results that define a repeatable process. You can associate workflows with queries to generate automatic responses to specific changes or invoke them manually as needed. For more information, review Workflows.
- Function - Code that interacts with a remote application or program to retrieve data or perform an action. It is used as a building block for workflows. When creating workflows, you can leverage functions and chain them together to achieve comprehensive operations. Functions are provided with the Connectors by default.
Data flow
Surface Command pulls data from the various connectors to provide a complete picture of your environment. Surface Command also monitors the data for changes, and optionally, takes action using workflows. There are several parts to this process:
- Ingestion - Surface Command pulls data using Connectors. Connectors' ingestion can be scheduled to run at the time and frequency that is most appropriate for your environment (typically daily).
- Correlation - As data comes in from Connectors, Surface Command correlates the data that refers to the same object and provides a unified view of that object. Each unified view of an object is represented as an asset in the system. Each of the records that are determined to be referring to the same object are linked to that unified asset. Correlation also tracks relationships between data. If an information source indicates a relationship between two objects (for example, a Machine has a specific IP address or owner), those relationships are inherited by the unified object they are correlated with.
- Unified property fulfillment - Each unified asset has a list of properties that are common for that type of asset. The most appropriate value for each of those properties is determined by evaluating the related properties of the correlated information source records and choosing the best value to include in the property of the unified asset. When you run queries for unified assets and look at their details, you are presented with these fulfilled unified properties, but you can also display all of the information source properties that were considered.
Surface Command features
Rapid7 currently offers the following product options containing Surface Command:
- Surface Command is for teams looking to consolidate their attack surface into a unified, single-pane-of-glass view.
- Exposure Command Essentials is for teams looking for a holistic view of their attack surface as well as on-premise monitoring, risk prioritization, and vulnerability management.
- Exposure Command is for teams looking for a holistic view of their attack surface as well as some cloud and on-premise monitoring, including attack path analysis, risk prioritization, and vulnerability management.
- Exposure Command Advanced is for teams looking for a holistic view of their attack surface as well as extensive cloud and on-premise monitoring, compliance alignment, infrastructure as code (IaC) scanning, automation capabilities, least privileged access management, and threat detection.
Feature comparison
The following table lists key differences between the products at a feature-level.
| Capability | Surface Command | Exposure Command Essentials | Exposure Command | Exposure Command Advanced |
|---|---|---|---|---|
| Asset Discovery and Unified Inventory | ✓ | ✓ | ✓ | ✓ |
| Attack Surface Visibility, including Identities, Software, and Controls | ✓ | ✓ | ✓ | ✓ |
| Asset Enrichment with Security Context | ✓ | ✓ | ✓ | ✓ |
| Blast Radius Mapping with Asset Graph | ✓ | ✓ | ✓ | ✓ |
| Built-In Automation and Policy Enforcement | ✓ | ✓ | ✓ | ✓ |
| External Attack Surface Discovery | ✓ | ✓ | ✓ | ✓ |
| Continuous Assessment Service (Coming Soon) | Add-On | Add-On | Add-On | Add-On |
| Remediation Hub | - | ✓ | ✓ | ✓ |
| Bulk Data Export API (Coming Soon) | - | ✓ | ✓ | ✓ |
| 450+ Out-of-the-Box Integrations with Security and ITOps Tools | - | ✓ | ✓ | ✓ |
| Security, Orchestration, Automation, and Response (SOAR) | - | ✓ | ✓ | ✓ |
| Discovery, Vulnerability, and Policy Scanning | - | ✓ | ✓ | ✓ |
| Agent-Based Vulnerability and Policy Assessment | - | ✓ | ✓ | ✓ |
| Dynamic Asset Tagging with Criticality Rating | - | ✓ | ✓ | ✓ |
| Threat Aware Active Risk Score | - | ✓ | ✓ | ✓ |
| Customizable Live Dashboards and Reporting | - | ✓ | ✓ | ✓ |
| Remediation Workflows | - | ✓ | ✓ | ✓ |
| Goals & SLAs | - | ✓ | ✓ | ✓ |
| Multi-cloud Visibility Across AWS, Azure, GCP, and Kubernetes (limited to CIS Compliance-related resources)¹ | - | - | ✓ | ✓ |
| Cloud and Container Vulnerability Assessment | - | - | ✓ | ✓ |
| Best Practices Configuration Assessment, including CIS | - | - | ✓ | ✓ |
| Contextual Risk Prioritization (Layered Context) | - | - | ✓ | ✓ |
| Attack Path Analysis | - | - | ✓ | ✓ |
| Notifications and Integrations | - | - | ✓ | ✓ |
| 100s of Out-of-the-Box Compliance Policies and Industry Standards | - | - | ✓ | ✓ |
| Executive Risk View | - | - | ✓ | ✓ |
| Extended Cloud Visibility Across AWS, Azure, GCP, Kubernetes, Oracle Cloud Infrastructure, and Alibaba Cloud (all resource types) | - | - | - | ✓ |
| Infrastructure as Code (IaC) Scanning | - | - | - | ✓ |
| Effective and Least Privileged Access (LPA) Management | - | - | - | ✓ |
| Cloud Threat Detection | - | - | - | ✓ |
| Automated Cloud Remediation | - | - | - | ✓ |
| Dynamic Application Security Testing (DAST) | - | - | - | ✓ |
¹ Exposure Command Product Resource Limitations
The Exposure Command product is limited to monitoring only the resources that are related to CIS and AWS Foundations compliance. The resource types in the following table come directly from the InsightCloudSec inventory view.
| Resource Type | AWS Type | Azure Type | GCP Type | Kubernetes Type |
|---|---|---|---|---|
| Access List | NACL/Security Group | Network Security Group | Network Firewall | |
| Access List Flow Log | NSG Flow Logs | |||
| Access List Rule | NACL/Security Group Rules | Security Rules | Firewall Rules | |
| API Access Key | IAM User Access Key | Application Credentials | Service Account Key | |
| API Accounting Config | CloudTrail | Logs Storage | ||
| App Configuration | App Configuration | |||
| Automation Account | Automation Account | |||
| Autoscaling Group | Autoscaling Group | Virtual Machine Scale Sets | Autoscalers | |
| Batch Environment | Batch Compute Environment | Batch Account | ||
| Big Data Instance | Redshift | |||
| Big Data Workspace | Synapse | |||
| Bot Service | Bot Service | |||
| Cache Instance | ElastiCache | Redis Cache | Memorystore | |
| Cloud Account | Cloud Account | Subscription | Project | |
| Cloud Access Point | S3 Access Point | |||
| Cloud App | App Registration | |||
| Cloud Credentials | API Keys | |||
| Cloud Dataset | Big Query Dataset | |||
| Cloud Group | IAM Group | Azure Active Directory Group | Group | |
| Cloud Policy | IAM Policy (Customer Managed) | Role Definition | Role Permission Set | |
| Cloud Region | Region | Region | Region | |
| Cloud Role | IAM Role | Azure Active Directory Service Principal | Service Account | |
| Cloud User | IAM User | Azure Active Directory User | User | |
| Clusters | EKS/ECS/Fargate Cluster | Kubernetes Service | GKE | |
| Cognitive Search | Cognitive Search | |||
| Cold Storage | Glacier | |||
| Container Registry | Container Registry (ECR) | Container Registry | Container Registry | |
| Content Delivery Network | CloudFront | CDN Profile, Front Door (Standard/Premium) | Cloud CDN | |
| Control Plane | Control Plane | |||
| Database | SQL Database/Dedicated SQL Pool | Cloud SQL Database | ||
| Database Cluster | RDS Aurora, Neptune, DocumentDB | |||
| Database Instance | RDS Database, Neptune, DocumentDB | SQL Server, Azure Database for PostgreSQL/MySQL/MariaDB | Cloud SQL | |
| Databricks Workspace | Databricks Workspace | |||
| Data Factory | Data Factory | Data Fusion | ||
| Data Stream | Kinesis | Event Hub Namespace | ||
| Dataflow Job | Dataflow Job | |||
| Delivery Stream | Firehose | |||
| Directory Service | Directory Service | |||
| Distributed Table | DynamoDB | Azure Cosmos DB | ||
| Distributed Table Cluster | DynamoDB Accelerator (DAX) | Bigtable | ||
| DLP Job | DLP Inspection Job | |||
| DNS Zone | Route53 DNS Zone | DNS Zone | DNS Zone | |
| Elasticsearch Instance | OpenSearch | |||
| Encryption Key | KMS | Key Vault Key | Cloud KMS CryptoKey | |
| Encryption Key Vault | Key Vault | Cloud KMS Keyring | ||
| Event Grid Topic | Event Grid Topic | |||
| Global Load Balancer | Global Accelerator | Front Door (Classic) | ||
| GraphQL API | AppSync API | |||
| Instance | EC2 Instance | Virtual Machine | Compute Engine | |
| Load Balancer | Load Balancer (ELB/ALB/NLB/Gateway) | Load Balancer/Application Gateway | Load Balancer | |
| Log Group | CloudWatch Log Group | |||
| Logic App | Logic App | |||
| Machine Learning Instance | Sagemaker Notebook | AI Platform Notebook | ||
| MapReduce Cluster | Elastic MapReduce (EMR) | HDInsightCluster | Dataproc | |
| Message Queue | Simple Queue Service (SQS) | Service Bus Queue | ||
| Network | VPC | Virtual Network | VPC | |
| Network Peer | VPC Peer | Peerings | Network Peer | |
| Pods | Pod | |||
| Private Subnet | VPC Subnet | Subnet | Subnetwork | |
| Secret | Secret | Secret | Secret | Secret |
| Serverless Function | Lambda | Function | Cloud Function | |
| Shared File System | EFS/FSx | File Share | Cloud Filestore | |
| SSL Certificate | IAM/ACM SSL Certificate | SSL Certificate | SSL Certificate | |
| Storage Account | Storage Account | |||
| Storage Container | S3 Bucket | Blog Storage Container | Cloud Storage | |
| Stream Instance | MSK Instance | |||
| Task Definitions | Task Definition (ECS) | |||
| Volume | EBS Volume | Disk | Persistent Disk | |
| Web App | Elastic Beanstalk Environment | App Service | ||
| Web Application Firewall | Web Application Firewall | Web Application Firewall Policies | Cloud Armor | |
| Workspace | Workspace Instances |
Onboarding experiences
The following table lists the different experiences and onboarding timelines for each of the offerings:
| Implementation Success Package | Exposure Command | Exposure Command Advanced |
|---|---|---|
| Attack Surface Management | - | - |
| Cloud Security | 2 Half-Day sessions | 2 days |
| On-Prem Vulnerability Management | Workshops and Technical Assistance | 2 days |