Threats
The Digital Risk Protection (Threat Command) Threats page gives you a deep look into potential threats in the following scenarios:
- Phishing - Domains or websites that may be used to launch future phishing attacks, typically against company employees or customers. Also shows the Phishing Watch threats when a company website is copied or redirected to an illegitimate site.
- Mobile Applications - Mobile applications that use company-like branding or other similarities, which may carry malicious code or otherwise endanger the user or the company.
- Exploitable Data - Hardware or software vulnerabilities: open ports, SPF/DMARC records, SSL certificate, SSL issues, and exposed services. This information is primarily for IT use.
- Public Repositories - Potentially leaked secrets or company assets in public repositories.
- Social Media - Non-authorized Twitter profiles that use company trademarks illegally or impersonate a company VIP, or public, relevant Twitter communications that mention your company assets.
- Data Leakage - Ransomware data leaks or exposure of internal or confidential company documents.
- Dark Web - Company credit cards, bot-harvested credentials, or products offered for sale on dark web black markets
If there is no alert icon, then the identified threat has not passed the threshold to elevate it to an alert.
Click a threat to see its details.
Each threat area has a dedicated tab on the Threats page. The following figure illustrates the Phishing tab:
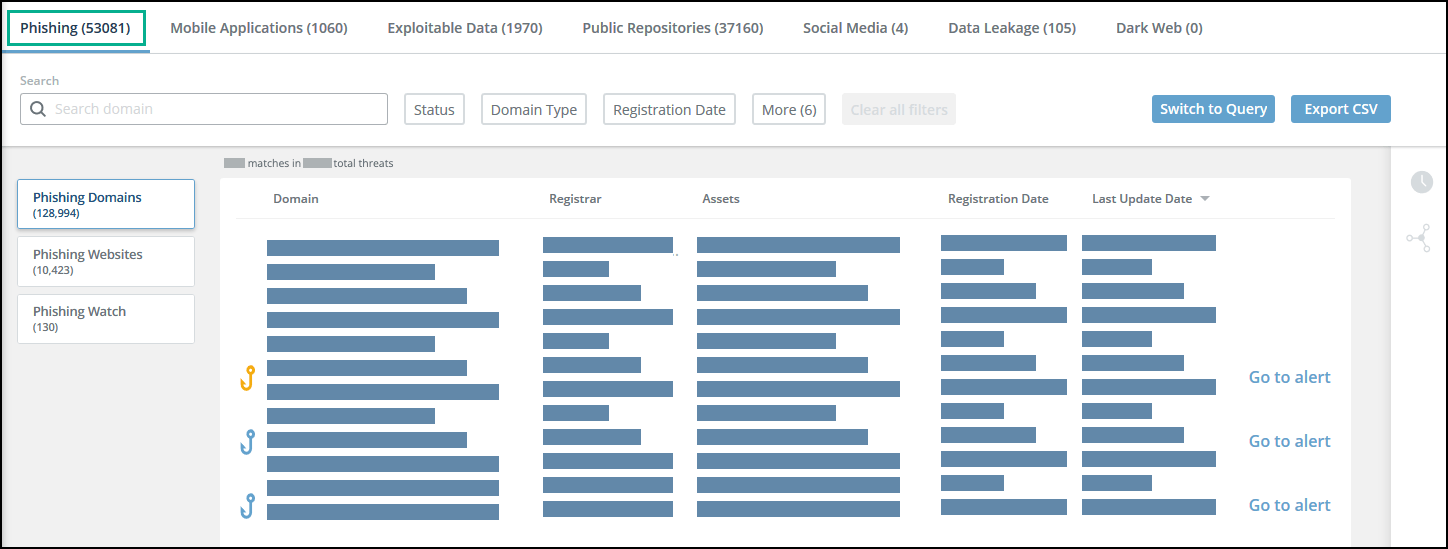
Using the Threats pages gives the following benefits:
- Better intelligence and transparency - For each monitored threat, you can see the criteria that are part of the Digital Risk Protection (Threat Command) algorithm, for example, which developer uploaded a commit to GitHub, or values of different leaked information.
- Correlate between different threats - Use the filter and search features to show similar threats. For example, showing all domains created by the same registrant can lead to a fuller picture of what a specific registrant is doing with your brand name, a picture that cannot be seen by looking at a single domain. Or, perhaps the same developer is uploading apps to various stores. You can pivot on monitored threat based on over ten search criteria, so you can make more relevant decisions.
- Understand why alerts are triggere d - Any significant event in a monitored threat (like adding an MX record) will cause that threat to be elevated to an alert.
The tabs have similar functionality, so those functions are described together. To see how to use the tab functions see View threat details.