Exploitable Data Threats
The Exploitable Data tab alerts IT professionals to vulnerabilities in company hardware and software:
- Open Ports threats
- DMARC/SPF threats
- SSL Certificates threats
- SSL Issues threats
- Exposed Services threats
Exploitable data threats are displayed if they are open at the present time (there is not historical reporting), sorted by date of last update, by default. You can change the sort order, or search for specific IP addresses. On some of the tabs, you can also filter the list using the Query Language, as described in Filter and search threats.
Open Ports threats
This section illustrates the Open Ports threats page and threat details.
Open Ports threats page
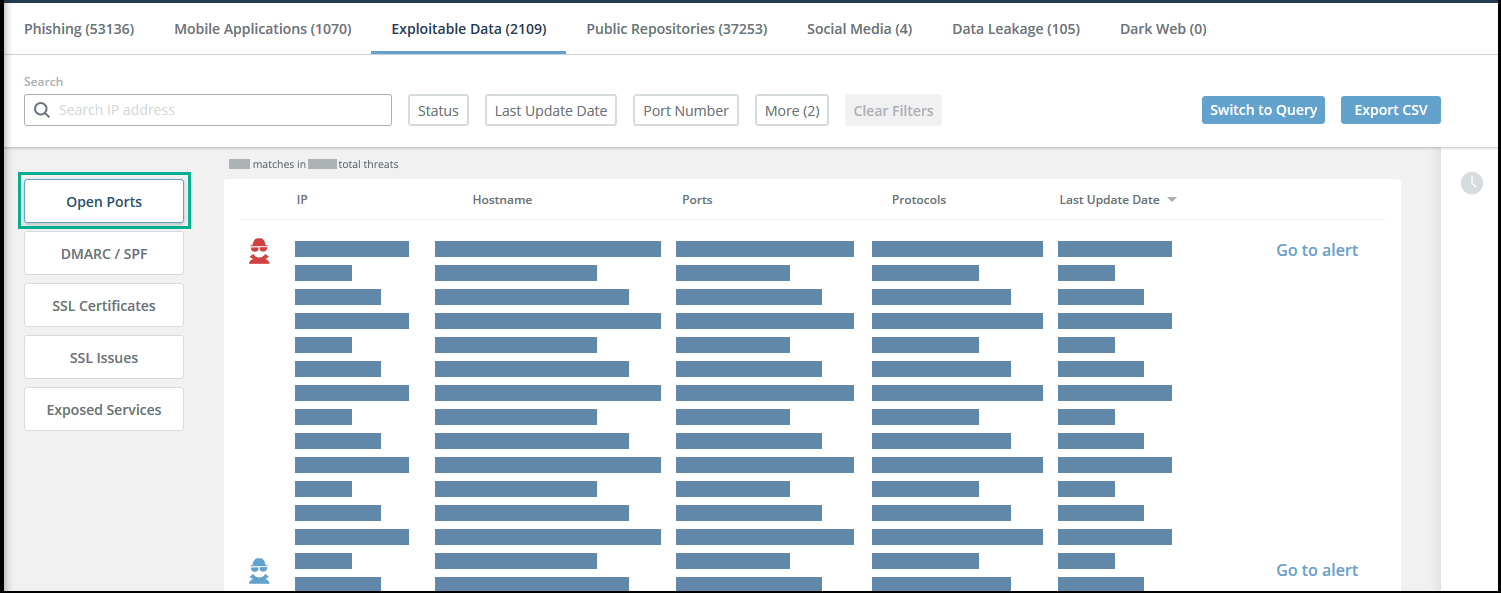
Open Ports threat details

DMARC/SPF threats
This section illustrates the DMARC/SPF threats page and threat details.
DMARC/SPF threats page
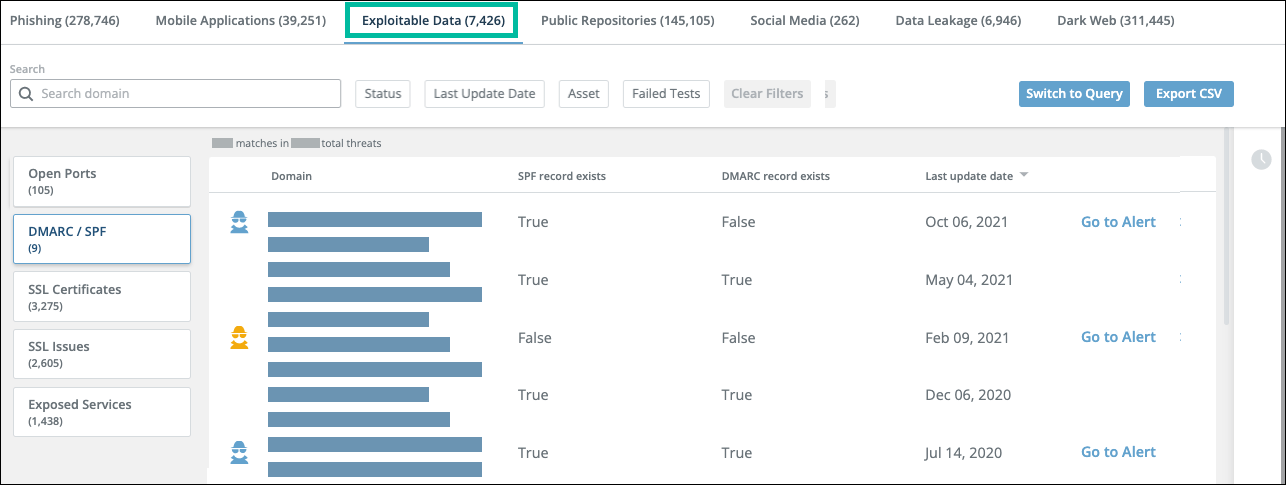
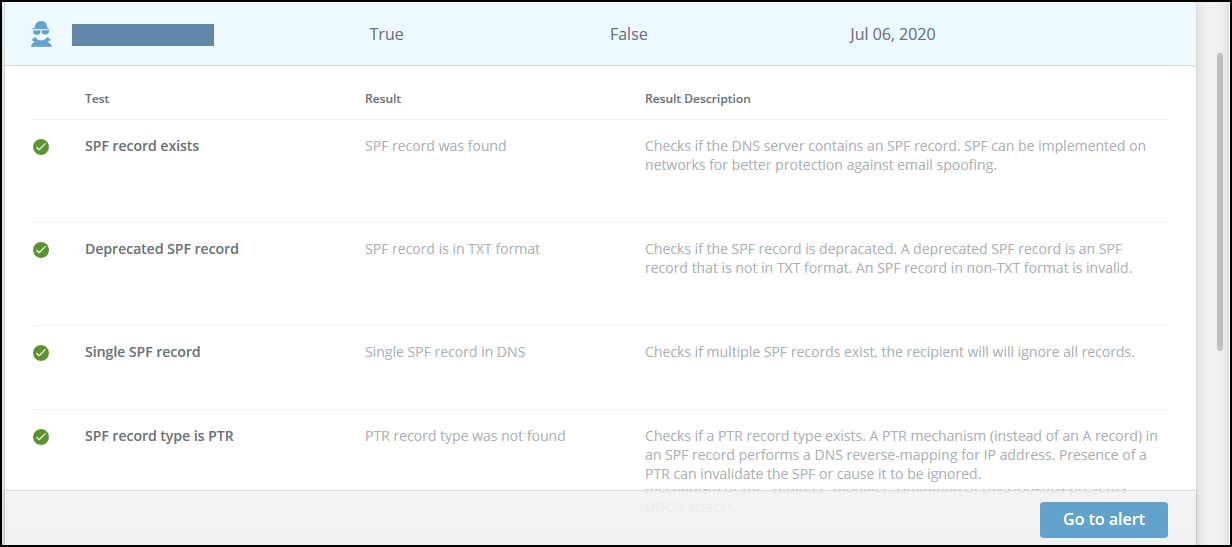
DMARC/SPF threat details
SSL Certificates threats
This section illustrates the SSL Certificates threats page and threat details and provides a description of the potential issues.
SSL Certificates threats page
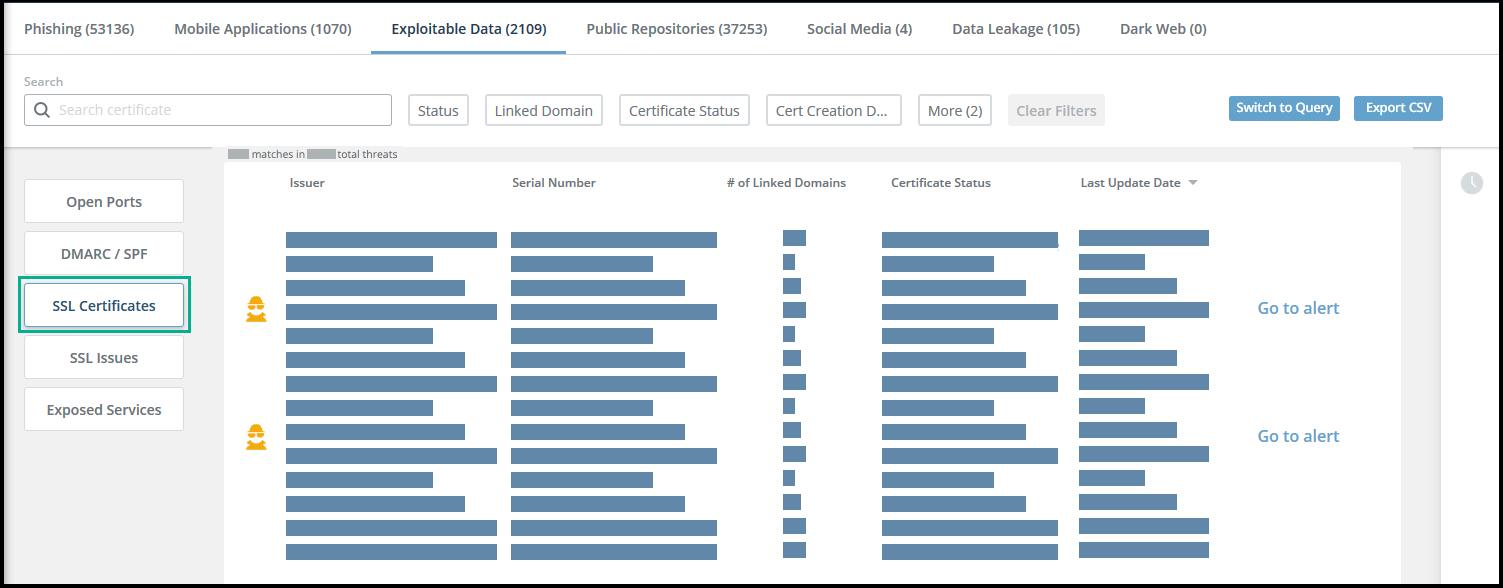
SSL Certificates threat details
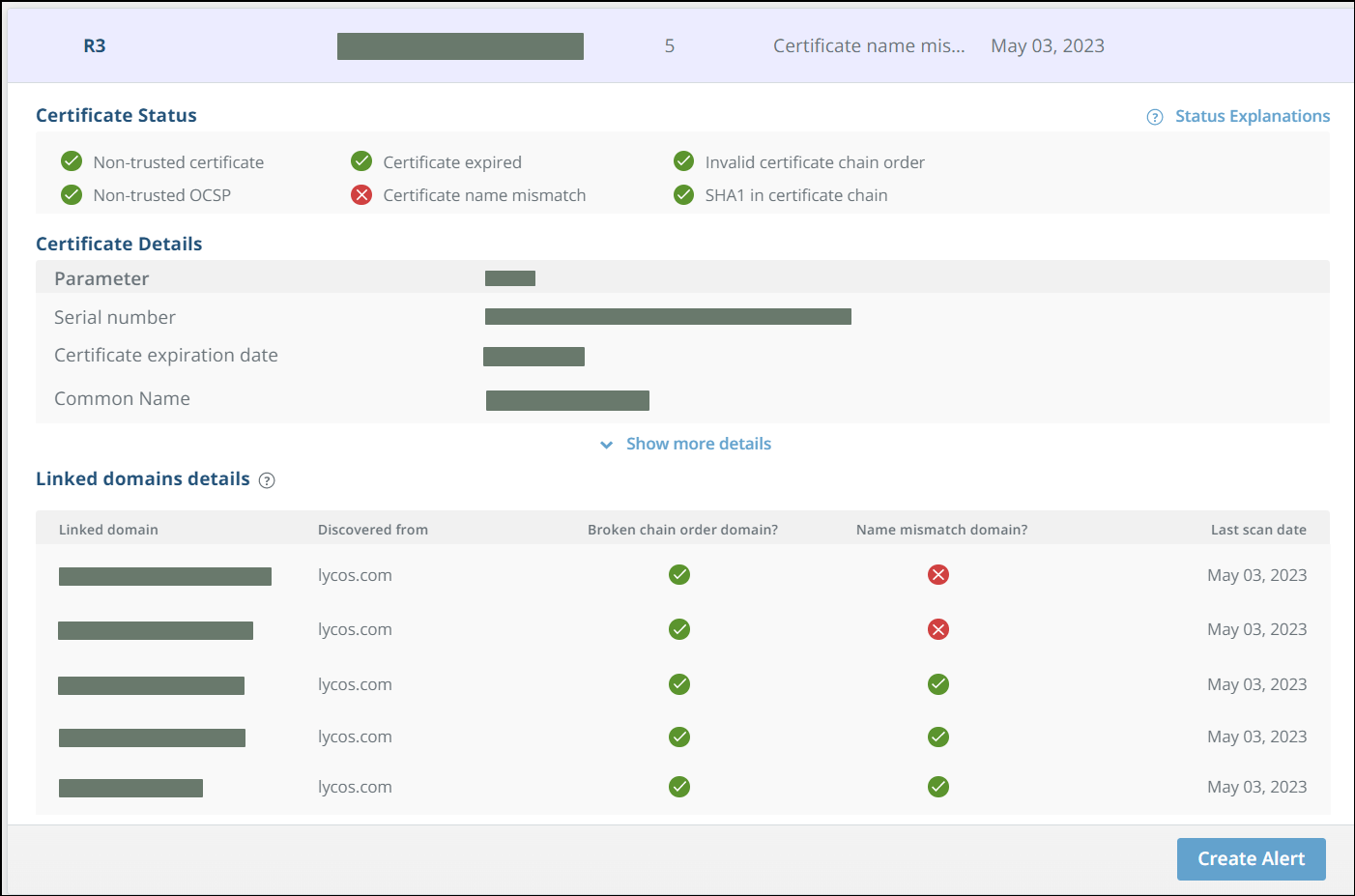
SSL Certificates description
| Issue | Description | Recommendation |
|---|---|---|
| Non-trusted certificate | The certificate is not trusted by a known, trusted certificate authority. This could mean that the certificate is not installed correctly, or that a self-signed certificate is installed on the server instead of a certificate signed by a certificate authority. | Verify that the certificate on the server is installed correctly, or sign your certificate with a known, trusted certificate authority. |
| Certificate expired | An expired certificate is considered invalid. Keeping an invalid certificate implemented causes connections to be insecure. | To avoid this, a new certificate should be implemented prior to the current one expiring. |
| Invalid certificate chain order | The certificate chain order is broken. This causes a problem in tracing back the original root certificates and verifying their validity to establish a secure connection. | To fix this issue, the right order of the intermediary certificates should be validated with the issuing party. |
| Non-trusted OCSP | The online certificate status protocol (OCSP) used to obtain the revocation status of the digital certificate is not trusted. The OCSP provider may no longer be authorized to sign the certificates. | It is recommended to end all communication with them and define a new provider. |
| Certificate name mismatch | The certificate common name (domain name) doesn’t match the DNS name. This means that the implemented certificate doesn’t sign this domain, and an unsecured connection can be established. | To fix this, a new certificate that matches the domain name should be issued. |
| SHA-1 in certificate chain | SHA-1 is an insecure algorithm that allows the client to trust low-security certificates. This will make your client more susceptible to imposter certificates. | It is recommended to use certificates that avoid both SHA-1 and MD5 algorithms. |
SSL Issues threats
This section illustrates the SSL Issues threats page and threat details and provides a description of the potential issues.
SSL Issues threats page
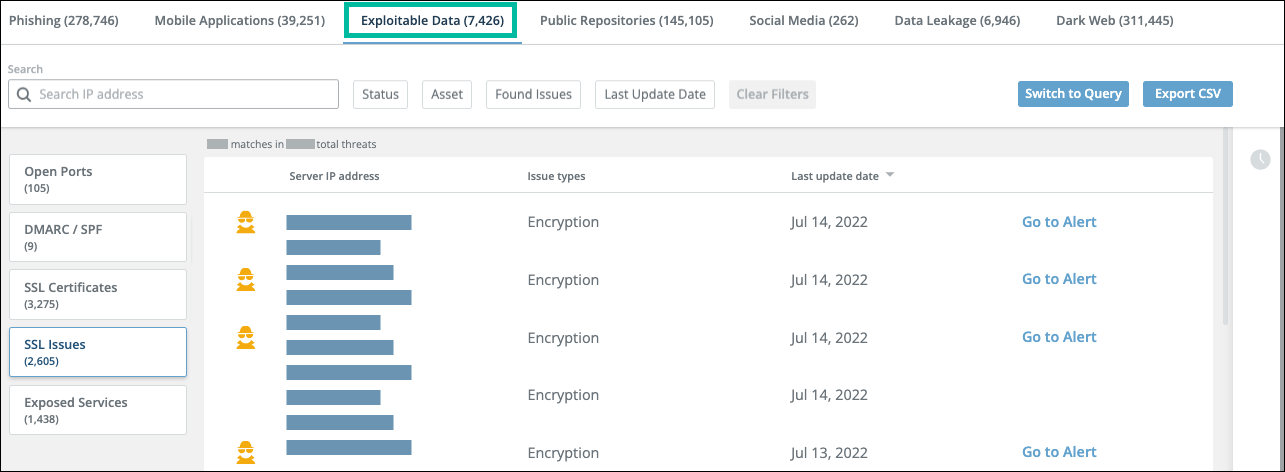
SSL Issues threat details
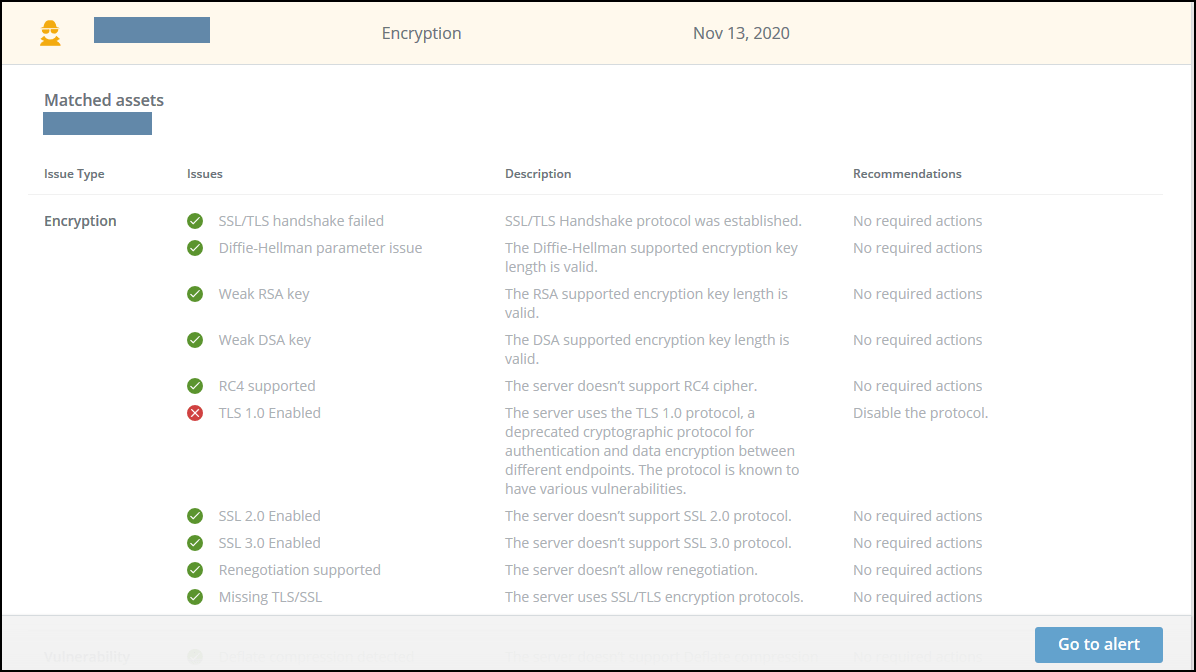
SSL Issues description
| Issue type | Failed description | Recommendation |
|---|---|---|
| Deflate compression detected | The server supports Deflate compression protocol, which makes it vulnerable to CRIME attacks. The protocol is a compression algorithm that allows recovering of original data. This method can be used to recover the content of secret authentication cookies, and to use it as a way to brute force the server (Replay attack). | Disable the protocol on the server |
| Diffie-Hellman parameter issue | The Diffie-Hellman supported encryption key length is too short and is at risk of being compromised. | Strengthen the supported key length. |
| Downgrade supported | The server supports the use of a degraded version of communication protocol between the client and the server. This can allow attackers to connect to the server using weaker protocols that have exploitable vulnerabilities. | Disable protocols such as TLS 1.0. SSL 2.0, SSL 3.0 |
| DROWN vulnerability | The server is vulnerable to DROWN attacks (CVE-2016-0800). DROWN allows attackers to decrypt the communication and steal sensitive information such as passwords, credit cards, etc. | Patch your server to an updated version |
| Heartbleed vulnerability detected’ | The server is vulnerable to Heartbleed (CVE-2014-0160), which weakens the security of the communication protocols. Affected websites are exposed to disclosure of confidential data. | Patch the server to an updated version |
| Missing TLS/SSL | The server doesn’t use SSL/TLS encryption protocols. This can enable the interception of data exchange with end-users. | Consider supporting SSL/TLS |
| OpenSSL vulnerability detected | The server is vulnerable to OpenSSL CCS flaw (CVE-2014-0224). This vulnerability exposes the server to man-in-the-middle attacks, where attackers can intercept data stream, and than decrypt, view, and manipulate the data. | Patch your server to an updated version |
| POODLE SSL vulnerability detected | The server is vulnerable to POODLE over SSL (CVE-2014-3566). POODLE, a form of protocol downgrade attack, causes connection failures that will force the browser to fall back and to choose an older and vulnerable SSL connection. | Patch your server to an updated version |
| POODLE TLS vulnerability detected | The server is vulnerable to POODLE over TLS (CVE-2014-8730). The attacks exploit an implementation flaw in the TLS 1.0-1.2 protocol, that makes the server vulnerable to POODLE even if SSL 3.0 is disabled. | Patch your server to an updated version |
| RC4 supported | The server supports RC4 cipher which is deprecated. | Update the supported cipher methods. |
| Renegotiation supported | The server honors insecure client-intiated renegotiation. Renegotiation can open the door to attacks such as man-in-the-middle and DoS. | Patch your server to an updated version |
| ROBOT vulnerability | The server is vulnerable to ROBOT over RSA. An attacker can recover the session key used for one or more sessions, and thereby decrypt communications to and from the web server. | Patch the server to an updated version |
| SSL 2.0 Enabled | The server uses the SSL 2.0 protocol, a deprecated cryptographic protocol for authentication and data encryption between different endpoints. The protocol is known to have various vulnerabilities. | Disable the protocol. |
| SSL 3.0 Enabled | The server uses the SSL 3.0 protocol, a deprecated cryptographic protocol for authentication and data encryption between different endpoints. The protocol is known to have various vulnerabilities. | Disable the protocol |
| SSL/TLS handshake failed | The server SSL/TLS handshake protocol has failed. This error may indicate a configuration problem in the client side or in the server side. | Check wether the problem is on the client side (browser) or server side. For details on the different problems that can generate this error, see: https://www.thesslstore.com/blog/tls-handshake-failed/ |
| TLS 1.0 Enabled | The server uses the TLS 1.0 protocol, a deprecated cryptographic protocol for authentication and data encryption between different endpoints. The protocol is known to have various vulnerabilities. | Disable the protocol. |
| TLS version outdated | The TLS engine does not support TLS v1.3, thus making it prone to vulnerabilities. | Consider supporting updated TLS version. |
| Weak DSA key | The DSA supported encryption key length is too short and is at risk of being compromised. | Strengthen the supported key length. |
| Weak RSA key | The RSA supported encryption key length is too short and is at risk of being compromised. | Strengthen the supported key length. |
Exposed Services threats
This section illustrates the Exposed Services threats page and threat details and provides a list of the covered services.
Exposed Services threats page
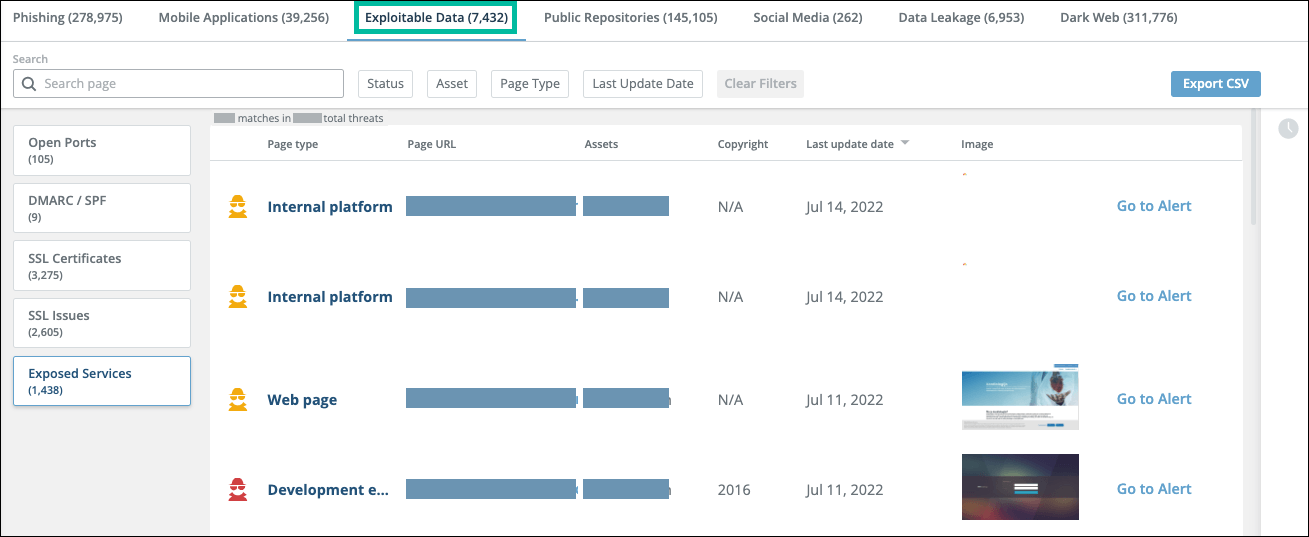
Exposed Services threat details
The following threats are covered:
| Development systems | Development environments | Web interfaces | Internal environments | Internal services |
|---|---|---|---|---|
| Cpanel | AWS cloud | Admin | APPX | Active directory |
| Git | Databases | Admin Management | CISCO | Atlassian |
| Grafana | Dev env | API | FTP | AWS |
| Jaeger | Monitoring servers | Backend | Manage | Basecamp |
| Jenkins | Staging env | CMS | SSH | Citrix |
| Kibana | CP | SYS | Competitive Programming (CP) | |
| Mongo | CRM | Dropbox | ||
| phpMyAdmin | Ingress | HubSpot | ||
| Plesk | Pilot | Jira | ||
| SVN (Apache Subversion) | LDAP | |||
| Webmin | Lync | |||
| Zpanel | Marketo |