TIP Sources
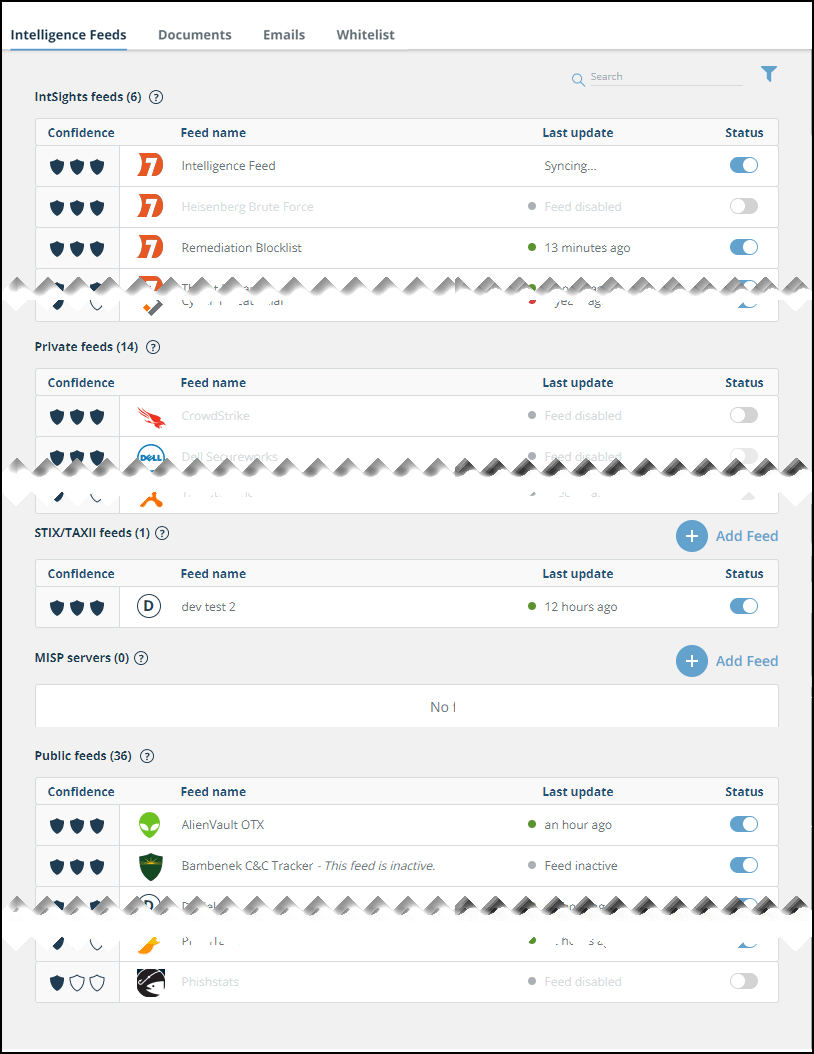
The first step in using the TIP module is to select the intelligence feeds that provide IOCs. There are many intelligence feeds listed on the Sources page.
TIP source feeds
- Rapid7 feeds - Private feeds that are provided exclusively to Rapid7 customers, free of charge. Rapid7 feeds includes indicators that are extracted from threat reports generated in the Rapid7 Research module. Rapid7 is a member of the Cyber Threat Alliance (CTA) and US-CERT, so these IOC feeds are also available.
- Private feeds - Private feeds are provided by security companies and organizations on a subscription basis. Customers can use Threat Command to automatically pull threat data from feeds they are subscribed to, to use in addition to those feeds that Threat Command provides. To use these feeds, the user must subscribe directly with the provider, and then enter their user credentials into Threat Command.
- STIX/TAXII feeds - Private or public feeds, that are not yet supported, that send data over TAXII in the STIX v1.x or v2.x format. These feeds can be added, per user, for that user's use only. To add a STIX/TAXII feed, see here.
- MISP server feeds - Private feed from an MISP server. MISP is a community-driven software project that enables sharing, storing, and correlation of IOCs of targeted attacks. To add a MISP feed, see here.
- Public feeds - Public Feeds are provided by companies and organizations without charge. You can enable or disable each listed intelligence feed. Once an intelligence feed is enabled, Rapid7 will retrieve intelligence from it, and the IOCs will be available for sharing.
You can enable or disable all the feeds that are available in your account.
The following tables describe the Rapid7 intelligence feeds that are part of the TIP sources.
Alternatively, you can see the description by clicking a feed name in Threat Command.
Rapid7 feeds
Private feeds
| Confidence | Feed | Description | |
|---|---|---|---|
| High | CrowdStrike | CrowdStrike Falcon X combines automated analysis with human intelligence to provide real-time threat alerts. For CrowdStrike configuration, see Add the CrowdStrike Feed. File hash IOCs in this feed are assigned a severity from the feed itself, not from Threat Command enrichment. | |
| High | Mandiant | Mandiant Threat Intelligence gives security practitioners unparalleled visibility and expertise into threats that matter to their business right now. | |
| Medium | A-ISAC | The Aviation ISAC feed is a focal point for security information sharing across the aviation sector. The feed facilitates the sharing of timely and actionable information related to threats, vulnerabilities, incidents, potential protective measures, and best practices. | |
| Medium | Canadian Center for Cyber Security | The Canadian Center for Cyber Security feed enriches, analyzes, and shares cyber threat information across business sectors and from Canadian and international cyber threat sharing hubs. CCCS provides actionable cyber threat intelligence with a Canadian focus. | |
| Medium | E-ISAC | The Electricity Information Sharing and Analysis Center feed aggregates cyber and physical threat intelligence for the electricity industry. | |
| Medium | FS-ISAC | The Financial Services Information Sharing and Analysis Center is the global financial industry's go-to resource for cyber and physical threat intelligence analysis and sharing. | |
| Medium | GovCERT.ch | The Computer Emergency Response Team of the Swiss government feed supports the critical IT infrastructure in Switzerland in dealing with cyberthreats by providing services such as technical analyses and information about targeted (but not limited to) attacks against the national critical IT infrastructure. | |
| Medium | Guardicore | Guardicore provides unique information on malicious IP addresses and domains. Threat information is based on three main resources: Guardicore Global Sensors Network (GGSN), Guardicore Reputation Services, and the insights of the Guardicore Labs team. | |
| Medium | H-ISAC | The Health Information Sharing and Analysis Center feed aggregates health care cybersecurity and threat intelligence. | |
| Medium | LS-ISAO | The Legal Services Information Sharing and Analysis Organization feed provides IOC and CVE information based on data exchange from governments and security vendors on topics ranging from phishing campaigns and ransomware threats to BEC attacks and APT activity. | |
| Medium | RH-CISC | The Retail and hospitality Information Sharing & Analysis Center (ISAC) component of the RH-CISC functions as a forum for retailers to share threat information and leading practices with each other to enhance the security of the retail industry’s most authoritative open threat information sharing and analysis network. OTX provides access to a global community of threat researchers and security professionals who contribute over 19 million threat indicators daily. OTX allows anyone in the security community to actively discuss, research, validate, and share the latest threat data, trends, and techniques. | |
| Medium | SWIFT-ISAC | SWIFT ISAC provides malware details such as file hashes, YARA rules, and IOCs that have been shared with the SWIFT community. | |
| Medium | ThreatConnect | This feed distills millions of data points to provide immediate insight into how widespread and relevant a threat is. The feed also provides IOCs for ONG-ISAC members, serving as a central point of coordination and communication to aid in the protection of exploration and production, transportation, refining, and delivery systems of the oil and gas industry, through the analysis and sharing of trusted and timely cyber threat information, including vulnerability and threat activity specific to ICS and SCADA systems. |
STIX/TAXII feeds
These feeds are added by the user and are available only in that user's environment.
MISP server feeds
These feeds are added by the user and are available only in that user's environment.
Public feeds
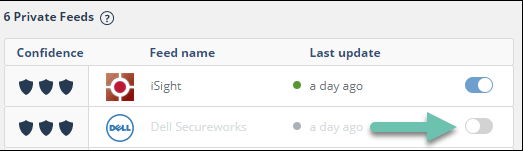
Enable or disable an alert source feed
You can turn a feed on or off. A feed that is off will not supply new IOCs.
To enable or disable a feed:
Using feeds and other IOC sources in other areas of Threat Command
The enabled intelligence feeds, STIX/TAXII feeds, as well as IOCs that you upload can be used in automation policies and IOC groups to pass to integrated devices, as described in Automation.
The following figure demonstrates how uploaded documents and emails are presented when creating an automation policy: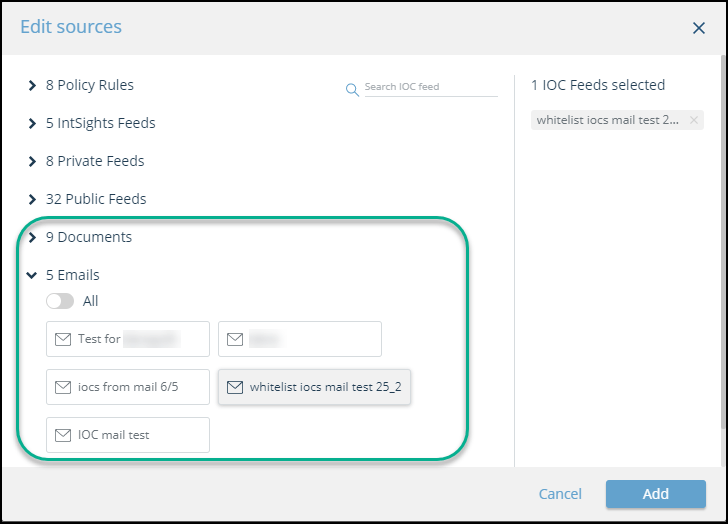
The following figure shows how an emailed IOC is shown in the Investigation page as the reporting feed: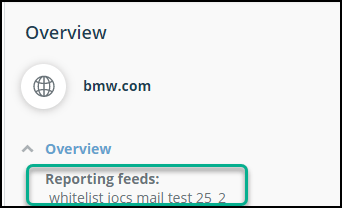
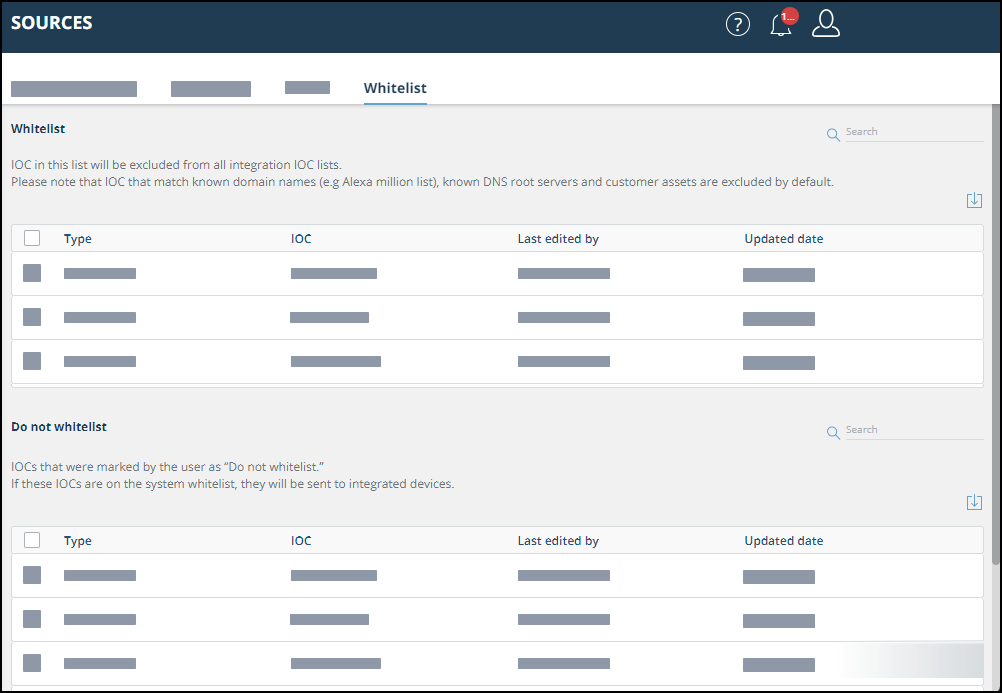
Whitelisted IOCs
Whitelisted IOCs are not treated as IOCs, that is, they are not sent to integrated devices.
There is a system-defined whitelist, for example, all company assrts and popular domains. The user can create a company-specific whitelist, as described in Add (or remove) IOCs to the user whitelist.
Whitelisted and "Do not whitelist" IOCs are displayed in the Whitelist tab: