Manage Alerts
Alerts are the main output of the Digital Risk Protection (Threat Command) module. Managing alerts is the process of reviewing and remediating identified threats.
Digital Risk Protection (Threat Command) sends alerts that are relevant to your company, based on the defined company assets. To define assets, see Configuring Assets.
Alert information is based on information that is scoured on all web sources: clear, deep, and dark web. Every alert is clearly marked to give you maximum control of the alert management process.
You manage alerts from the * Digital Risk Protection (Threat Command) > Alerts** page.
The Alerts page displays the Alerts list, and the Alert header, Description, Banner and Options pane.
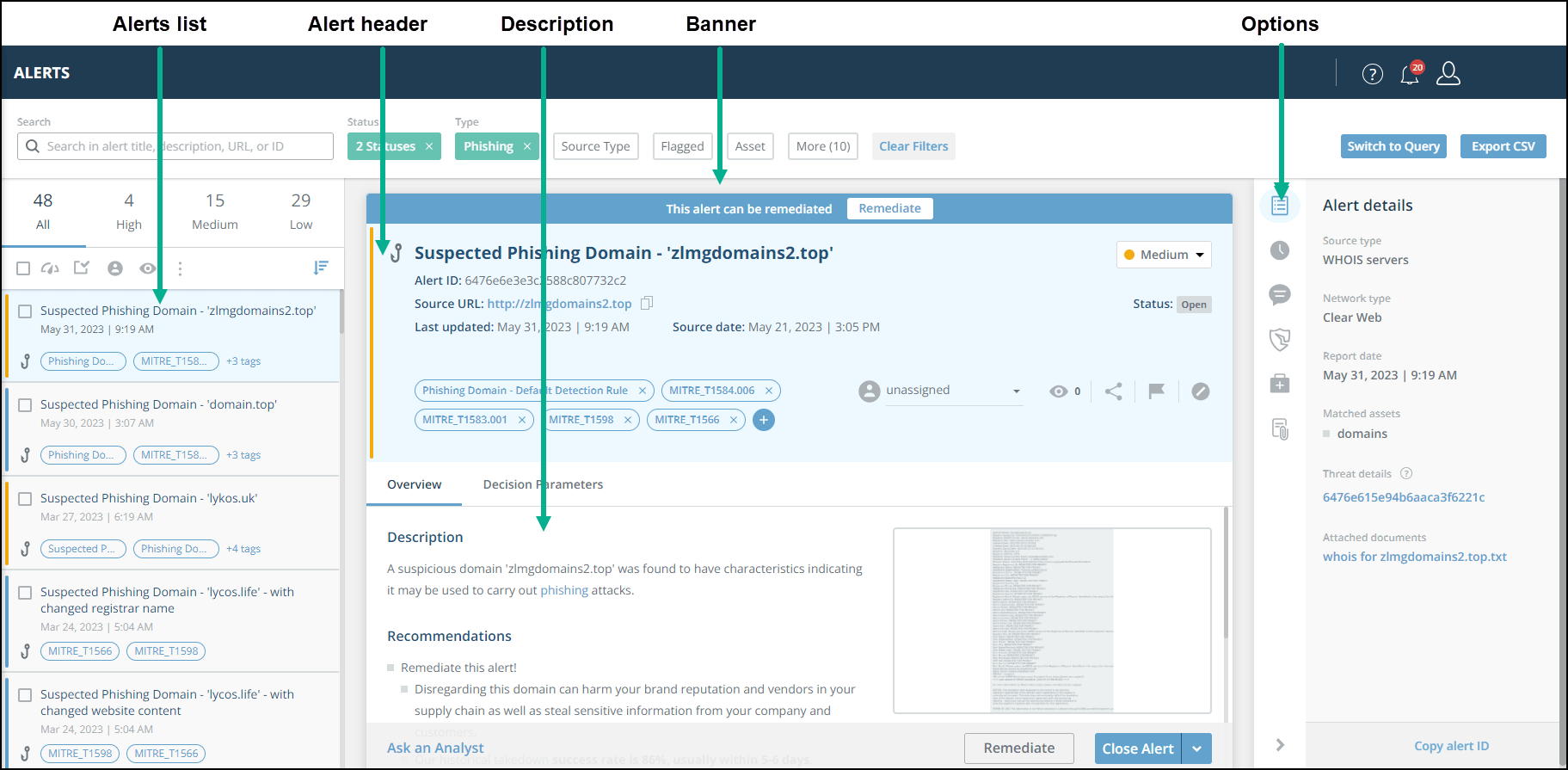
Alerts page
The Alerts list displays all alerts, with the last-updated, open or in-progress alerts listed first (by default). Every alert is labeled by severity and threat type, so you can quickly identify important alerts before digging further.
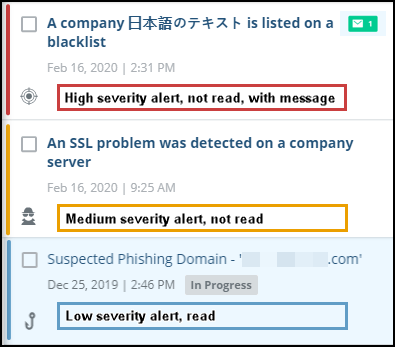
Alerts list example
There is a special alert, the summary alert, that can also be displayed in the Alerts list. The summary alert informs you that a recent enhancement in the Digital Risk Protection (Threat Command) detection algorithms has caused the creation of many new alerts.
In order not to flood your system, these new alerts are given a different status, pending. For more information on the summary alert and how to best manage the alerts that it describes, see Managing the summary alert.
In addition to red, yellow, or blue severity colors and alert type, the Alerts list shows the following:
- Read or not read - The title text of non-read alerts is bold on a white background; read alerts are not bold, on a grey background.
- Analyst or remediation updates - If present, are indicated in these ways:
- In the Alerts list, an envelope icon is displayed on the alert.
- In the Alert options pane, a circle is displayed, like
 .
.
- Alert status - If the alert is In Progress or Closed, that status is shown.
At the top of the Alerts list, you can use these tools:
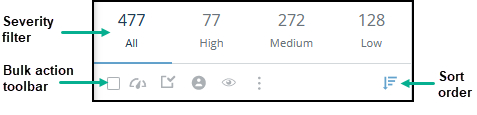
- Severity filter - Click one or more severities to view only alerts of those severities.
The selected severities are marked with a color band under them. - Bulk action toolbar - Perform various actions on selected alerts, as described in the Alert actions table.
- Sort order Click to reverse the sort order (Last updated, descending is default).
Alert types
Alert type classifications are shown in the following table:
| Icon | Alert type | Description |
|---|---|---|
| Attack Indication | Detection of intentions of cyberattacks on websites, forums, and social media (for example, use of the company name in target lists, credit cards for sale, or a bid for attacking the company in hacker forums). | |
 | Phishing | Detection of potential phishing domains soon after they are registered gives you time to prepare for and prevent attacks. |
 | Exploitable Data | Detection of information that has been indexed by search engines and can be exploited by hackers (for example, web vulnerability information related to internal confidential networks or databases and software used). |
 | Data Leakage | Detection of when user confidential data has been leaked to the web (for example, employee account credentials, secret documents concerning company projects, or information about the company’s internal network). |
 | Brand Security | Detection of fake social media profiles and pages or fake mobile applications. |
 | VIP | Detection of intentions to attack VIPs and fake VIP profiles on social media and other websites. |
Alert actions
All actions that you can perform on an alert are listed in the following table, in order of their appearance in theAlerts page. Actions marked with an * can be performed on multiple alerts, as described in Perform actions on multiple alerts.
Alert actions table
| To do this | Use this feature | Click this | Description |
|---|---|---|---|
| Select all alerts | Perform actions on multiple alerts |  | Select (or deselect) all alerts in one click. |
| Change the severity of alerts* | Change alert severity | Change the severity assigned to alerts. You can change the severity of a single alert by selecting the new severity in theAlert header. | |
| Change alert status* | Change alert status | Change the status of alerts to Open, In Progress, or Closed. | |
| Assign alerts* | Assign alerts |  | Assign (or unassign) alerts to an analyst. You can assign (or unassign) a single alert from  in the Alert header. in the Alert header. |
| Add watchers* | Add a watcher |  | Add a watcher to alerts. You can add a watcher to a single alert from  in the Alert header. in the Alert header. |
| Flag alerts* | Flag alerts |  thenFlag | Flag alerts to draw attention to them. You can flag a single alert from  in the Alert header. in the Alert header. |
| Mark alerts unread or read* | Mark alerts as read or unread |  thenMark | Change whether alerts are unread or read. |
| Get input about alerts from others* | Share alerts |  thenShare | Share alerts with someone outside of the Rapid7 system. You can share a single alert from  in the Alert header. in the Alert header. |
| Tag alerts* | Add or edit alert tags |  thenTag | Add a user-defined tag to alerts. You can tag a single alert from in the Alert header. in the Alert header. |
| Exclude domains | Exclude irrelevant domains |  | Remove certain domains from triggering phishing domain alerts. |
| View alert details | View alert details |  | See expanded alert details. |
| View alert history | View alert history |  | See the alert timeline. |
| Ask an intelligence analyst for input on an alert | Ask an analyst |  | Ask for clarification, context, or a recommendation from an intelligence analyst. |
| Remediate an alert | Remediate an alert | Click Remediate in the alert banner or footer, or click | Request that Rapid7 intervene to remediate an alert. Only displayed for alerts that can be remediated. |
| Add an IOC to the Remediation Blocklist | Add an IOC to blocklist remediation |  | Add an alert URL or domain to an internal Remediation Blocklist, to be fed to security devices. Only displayed foralerts that can be remediated. |
| Add notes to an alert* | Add notes to an alert | Attach an internal note to alerts. | |
| Add a document to an alert* | Add document to an alert | Upload a document to alerts. | |
| View alert ID | See alert ID |  | See the unique alert ID. |
| Visit the source site | Visit an alert source site | Source URL link | See the actual site where the malicious code was found. Certain Attack Indication alerts include an arrow that indicates whether the sale site is currently reachable, for example:  Note: These sites are potentially malicious. Use this feature with extreme caution. |
| Preview the source site | Preview an alert source site | Source URL link | View a PDF of the malicious site, without visiting the site. |
| Download alerts | Export alerts to a CSV |  | Download a CSV with selected alert information. |