View IOCs and CVEs with Rapid7 Extend
Extend comprises two synergetic parts:
- Summary window with enrichment data and additional actions.
- On-page highlights and enrichment data.
Extend works very similarly for IOCs and CVEs. In the following sections, we will point out the differences, when applicable.
View IOCs and CVEs
Extend behavior is determined by the default scraping method. It is recommended to enable the Always on mode.
You can change that default, as described in Change default Extend scraping method.
Prerequisites:
- Rapid7 Extend must be installed.
- To view IOCs, you must have a subscription to the Threat Command TIP module and a subscription to Extend.
- To view CVEs, you must have a subscription to the Threat Command Vulnerability Risk Analyzer module and a subscription to Extend.
- You must be able to log in to the Threat Command.
To view IOCs and CVEs in the Extend summary window:
When scraping is in the Always on mode, the Extend summary window is shown for every web page that you visit. If Extend is in the Scan on demand mode, follow the procedure below to display the Extend summary window.
- From a Chrome browser, visit any web page.
- From the Chrome menu, click
 .
.
The web page is scraped and the Extend summary window is displayed over the web page: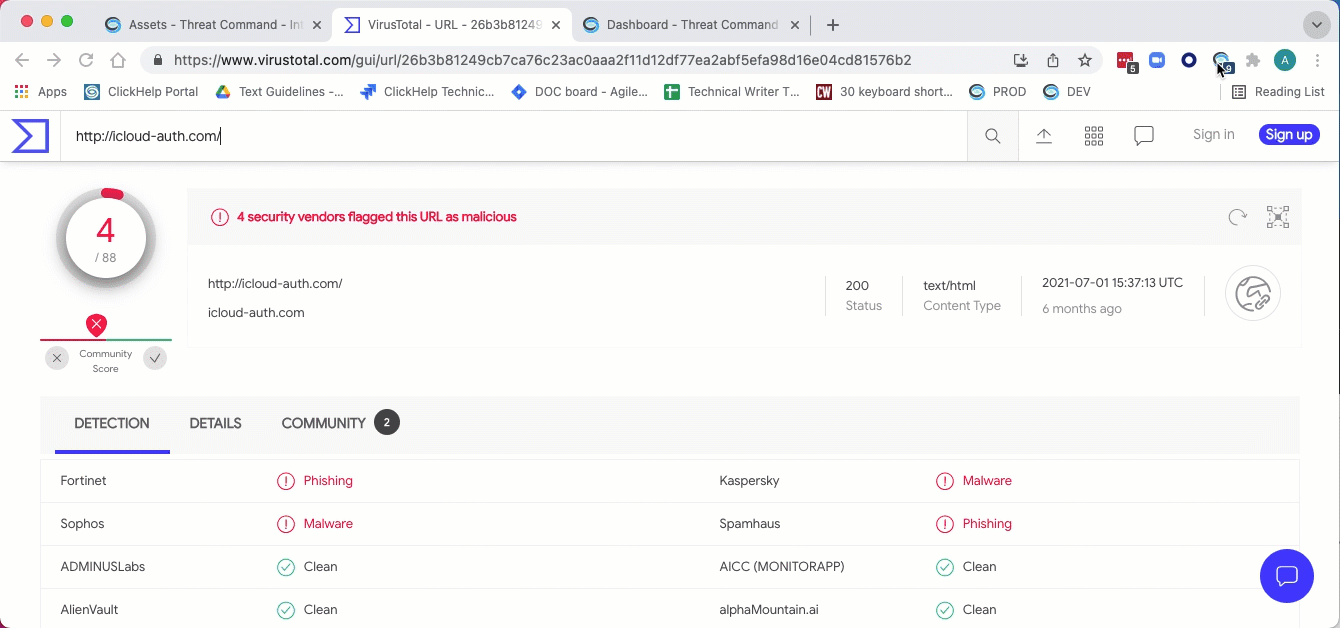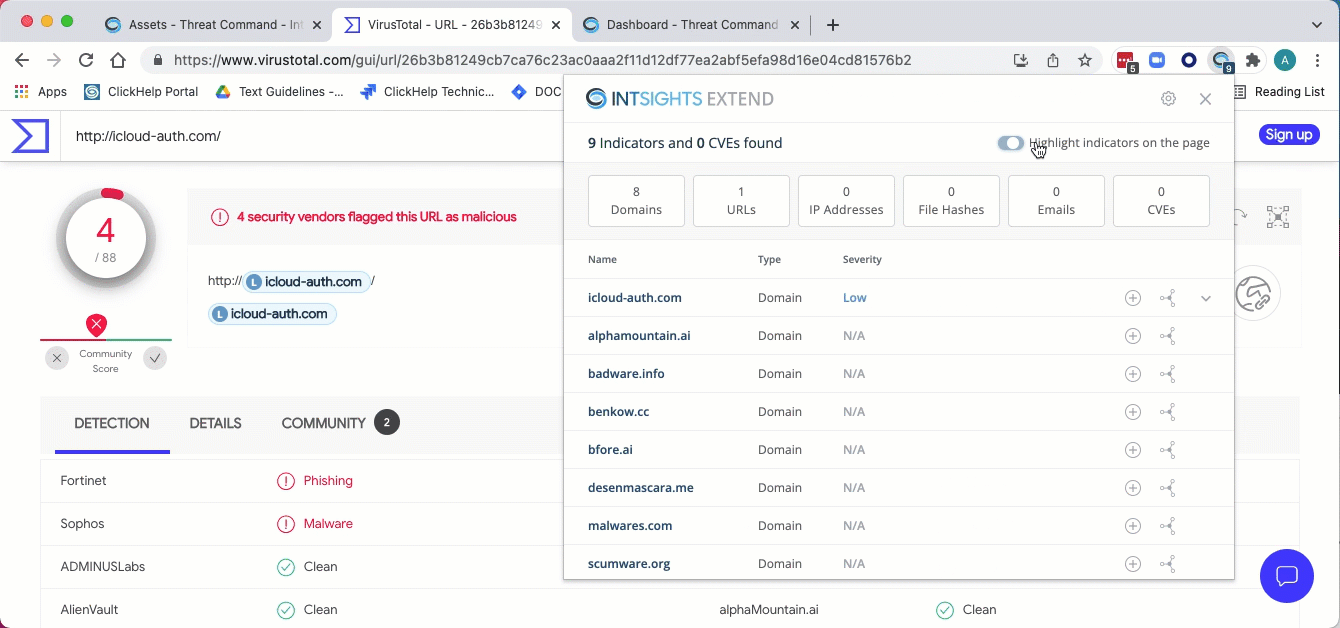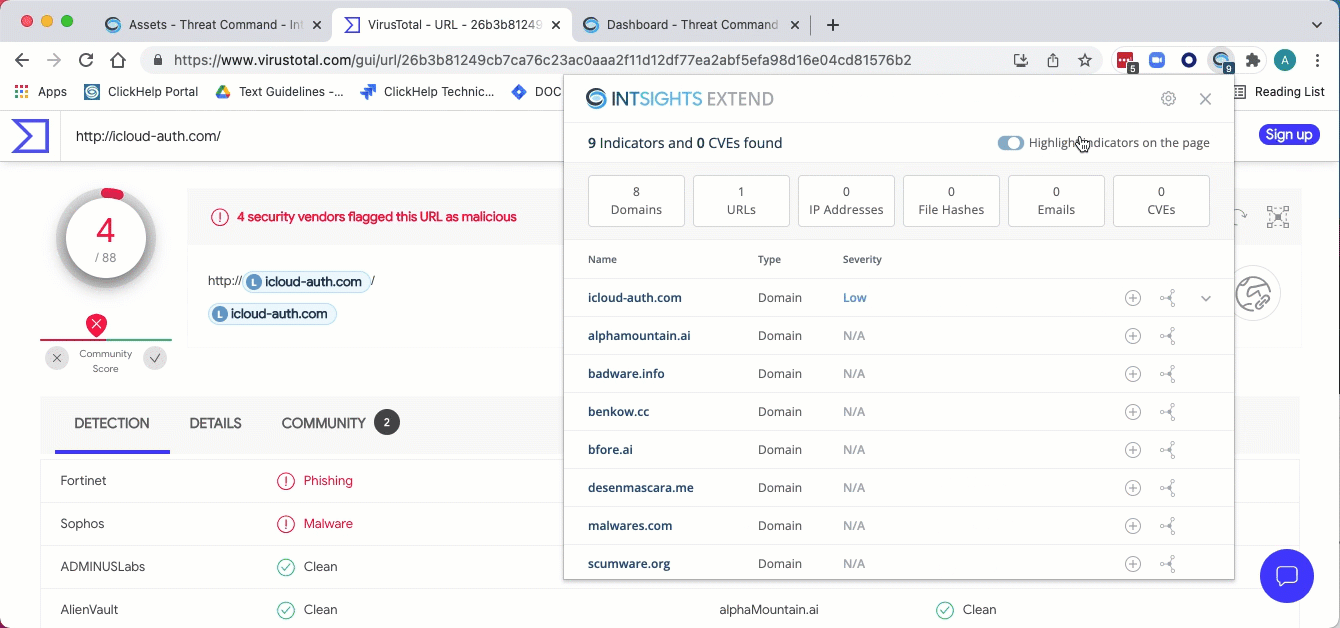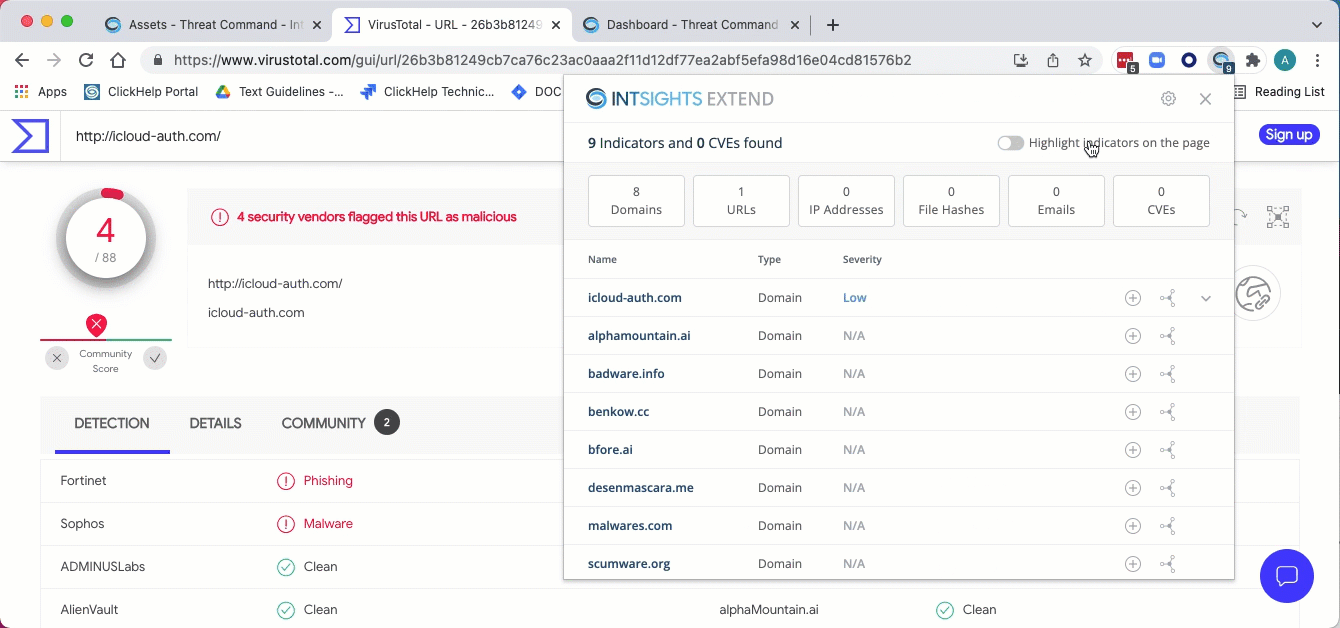

About highlighting
If Highlight indicators on the page is selected, those indicators that are already present in the Threat Command are highlighted. You can toggle this setting from the summary window.
Highlighted page entries include an severity indicator. You can click an entry to see more details about it. (If the entry is not highlighted, clicking it will cause the default page action.)
Only indicators that are IOCs are highlighted, subject to the following:
- If the domain is an IOC, but the subdomain is not, only the domain is highlighted.
- If only the subdomain is an IOC, then only the subdomain is highlighted.
- If both the domain and the subdomain are IOCs, then only the subdomain is highlighted. Not sure about this?
Using the Extend summary window
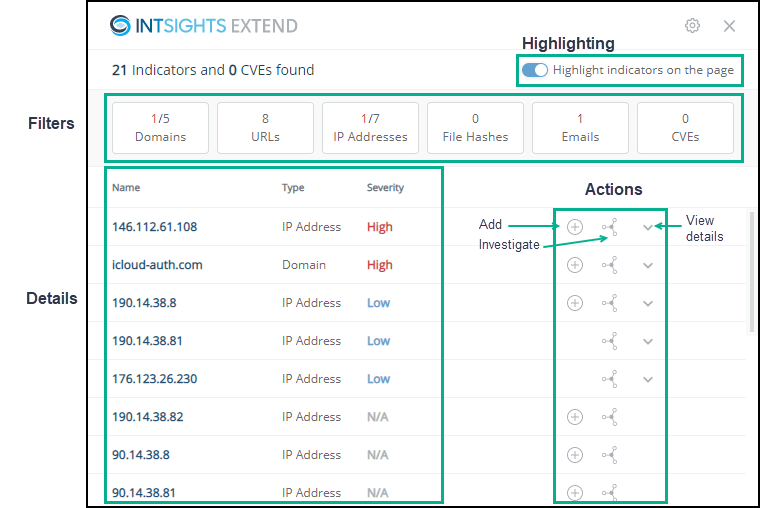
The Extend summary window shows all the entries that were found on the page (maximum of 300). If an entry is on the page more than once, it is listed in the summary window only once.
The top line displays the total amount of entries (indicators and CVEs) that were scraped from the page. For those entries that are already present in the Threat Command, severity and additional enrichment data are available.
The entry details are presented in order of severity, highest severity first.
Once a page has been scraped, you can do the following activities in the Extend summary window:
| To do this | Use this part of the window |
|---|---|
| Filter the presented entries | Click a filter button. In this page, for example, to see only the domains. click 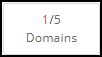 . 1 domain is of the highest severity. . 1 domain is of the highest severity. |
| Toggle whether web page entries are highlighted | Click Highlight indicators on the page. IOCs and CVEs from the Threat Command are now highlighted. Note that highlighted entries, aside from being easier to see, can also be clicked to view additional data. |
| Change the default scanning method | Click the settings gear, make the change, then click Done. |
| See the summary of entries | See the details section. This section is described fully in Using the details section of the Extend Summary window. Each entry is listed only once, even though it may be on the web page multiple times. |
| Add the entry to the Threat Command | Click An IOC will be added to the Browser Extension feed, as a document in the TIP Sources page. You can use that feed in IOC policies just like any other feed. A CVE will be added to the Threat Command Vulnerabilities Risk Analyzer (VRA). If the IOC or CVE is already present in the Threat Command (either as an IOC in a feed or as a CVE in the account), the + is not displayed. |
| Investigate an IOC | Click The IOC is searched for in the Investigation module. This option is available for IOCs, only. |
| See a CVE in the VRA page | Click The CVE is searched for in theVulnerability Risk Analyzermodule. This option is available for CVEs, only. |
| View entry details | Click The entry enrichment details are displayed. These are the same details that are displayed if you click the highlighted entry on the web page. 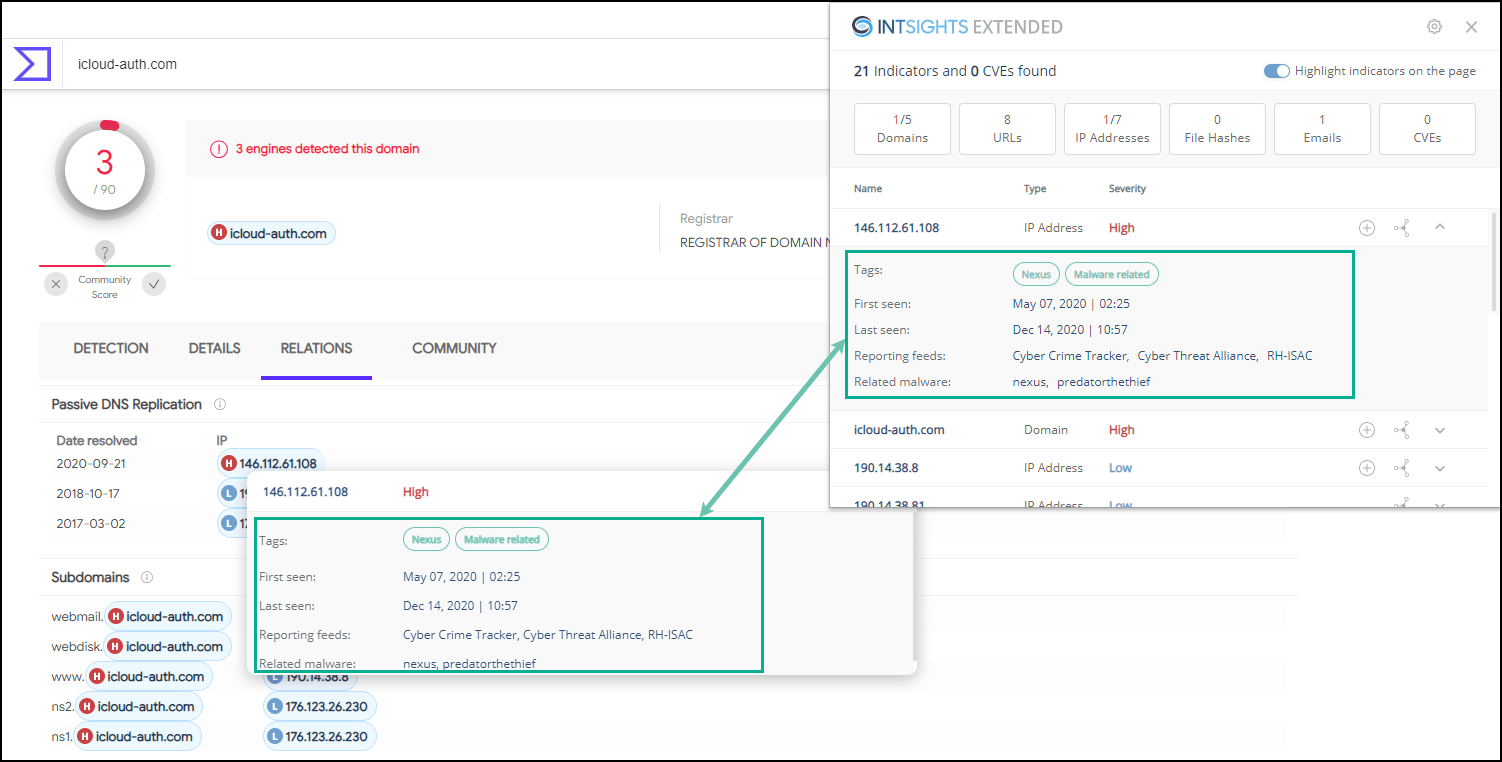 |
Using the details section of the Extend summary window
The summary window lists all entries found on the web page. Those entries that already exist in the Threat Command have additional information displayed:
Severity
Each entry is coded with its severity (for IOCs: High, Medium, or Low; for CVEs: Critical, High, Medium, or Low). For entries that are not in the Threat Command, the severity is N/A.Enrichment data
For existing entries, click to see the enrichment data from Threat Command.
to see the enrichment data from Threat Command.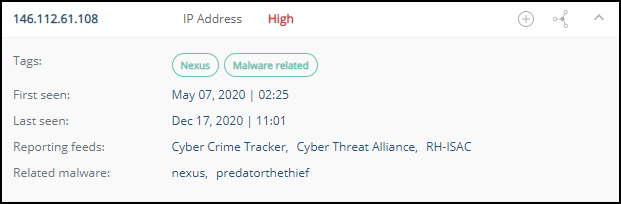
The details for an IOC entry may include the following:- Tags
System tags are shown in green; user tags in blue. - First seen and last seen
When the IOC was seen. - Reporting feeds
From which Threat Command feeds this IOC was found. - Related malware or threat actors
To which malware or threat actors the IOC is related - Triggered alert
If the IOC related to an alert in the Threat Command Threat Command, that alert header is displayed. To see the alert in the Alerts page, click . In addition, from the IOCs page, you can filter by Intelligence feed+
. In addition, from the IOCs page, you can filter by Intelligence feed+
The details for a CVE entry may include the following:
- Vendor & product
The CPE to which the CVE relates. - NVD publish date and CVSS score
Information from NVD - Rapid7 score
The severity score from Rapid7 - Overall mentions
The amount of times in which this CVE is mentioned. - Last mentioned and First mentioned
When the CVE was last seen and first seen - Exploit available
Whether an exploit is available for this CVE.
- Tags
If an IOC has been correlated in an integrated Splunk or Azure Sentinel app, it will be marked as “Found in your environment.”
If a CVE has an exploit, it will be marked as "Exploit available."