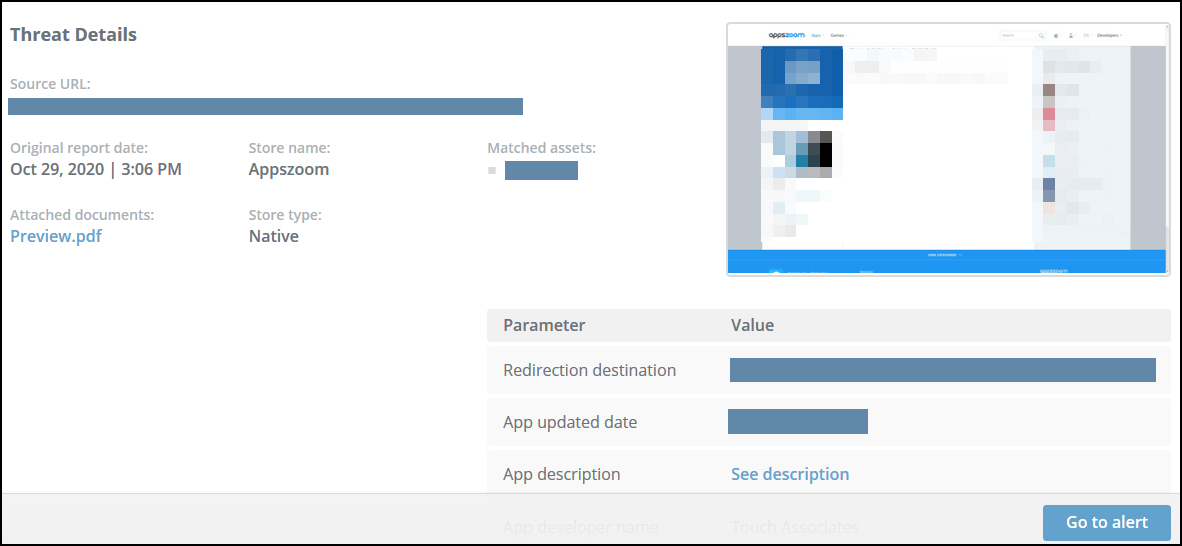
Mobile Applications Threats
The Mobile Applications tab displays details of unauthorized applications. This includes applications that match company applications or use company assets, brand or company name. These apps may be: malicious, the sites that host them may host malicious code, or they may be exact copies of valid company apps, but they are being made available in regions in which the company does not authorize their distribution.
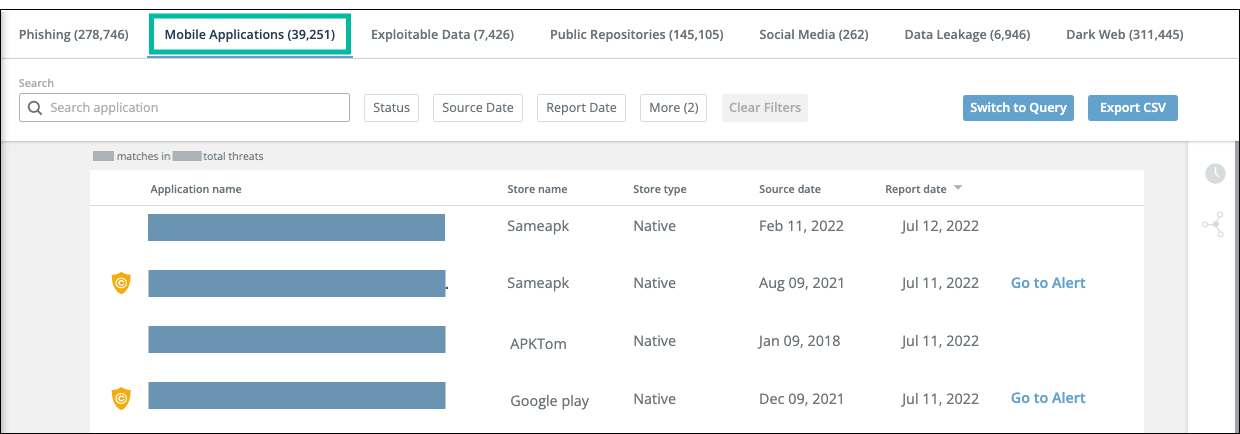
From the Mobile Applications tab, you can also launch an investigation on a threat. Mobile application threats are sorted by date of the last report, by default. You can filter the view by clicking the filter buttons above the table or by using the Query Language. For more information, see Filter and search threats.
Mobile applications threat details screen