Public Repositories Threats
The Public Repositories tab shows the following threats:
- Leaked secret threats Potential company secrets that are leaked in public repositories
- Asset mention threats Company assets that are leaked in public repositories
To enable searching for potential leaks, you must define certain assets:
- For leaked secrets, you must define at least one Public repository queries, Public repositories, or Domains asset.
- For asset mentions, you must define at least one Code mentions** or Domains asset.
The threats are refreshed each time you open the tab, so they are shown only if they are currently a threat. By default, the threats are sorted by the date of the last report, with the most recent first. You can reverse the sort order or sort by the number of mentions.
You can filter the view by clicking the filter buttons above the table or by using the Query Language. For more information, see Filter and search threats.
Leaked secret threats
Each line on the Leaked Secrets tab displays a potential leaked secret that was found in a single Git public repository:
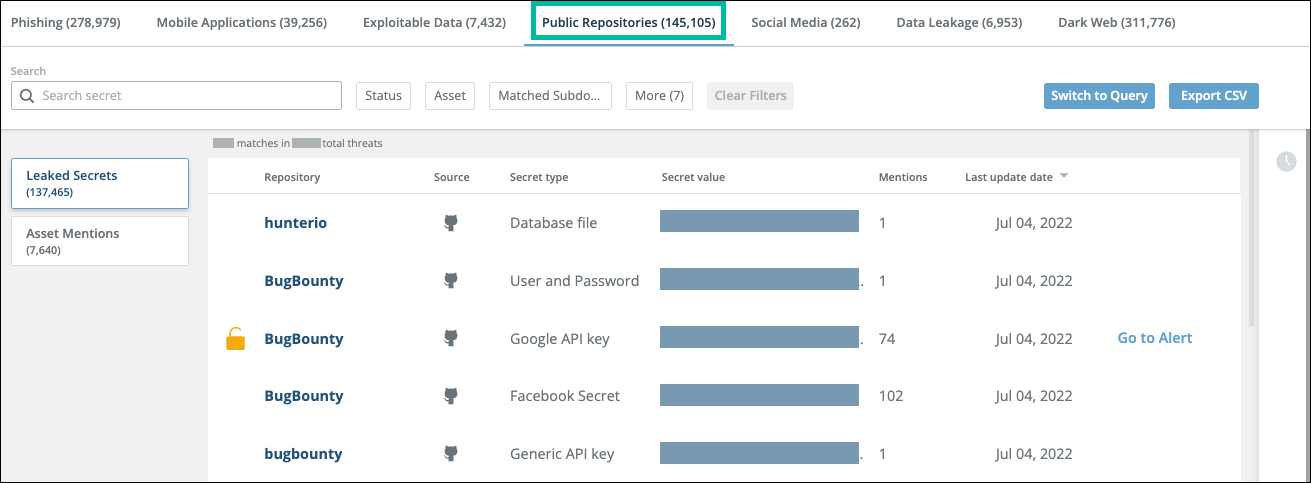
The threats displayed in the previous figure were found in separate repositories, with 1, 1, 74, 102, and 1 mentions in each repository, respectively.
To see the threat details, click the threat line. The following figure shows the detail of the last threat in the previous figure:
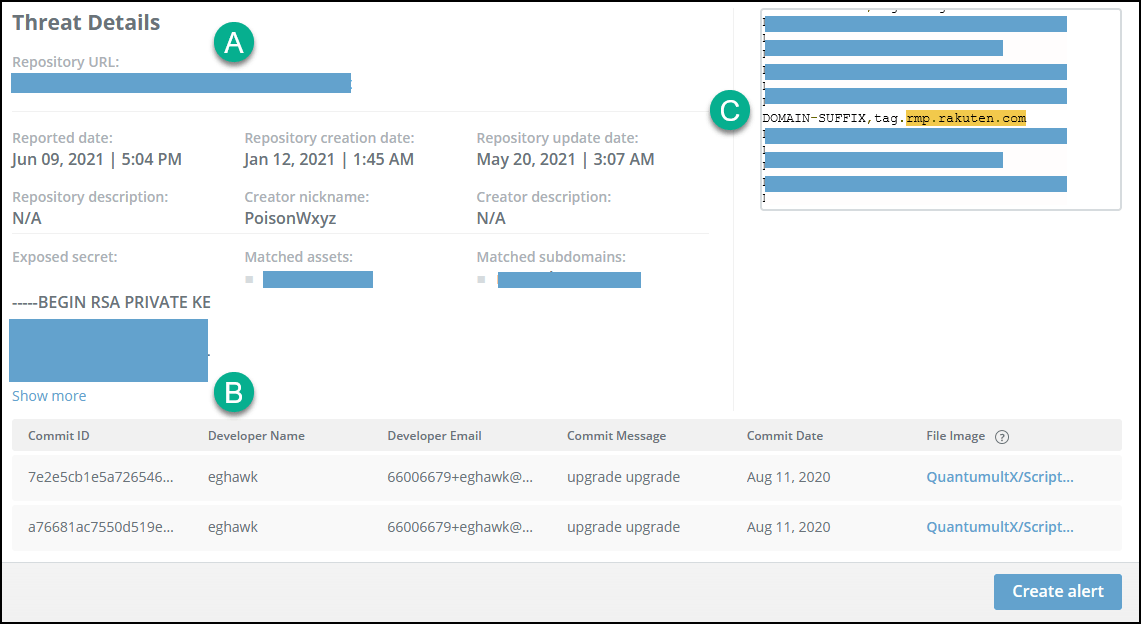
The threat details are presented in these sections:
-
Repository information (section A) - Displays all relevant information about the detected repository and the assets that matched the repository content. The details show a highlighted image of the matched assets in the relevant parts of the code (section C).
-
Secret code exposure locations (section B)- Displays a table that details all the places in the code where the secret was exposed. Every mention of the secret includes information about the commit, developers, relevant dates, and the file. To review all the specific secret mentions and to see the context, click the filename. A highlighted image of the mention in that file is displayed.
-
Scroll to see multiple mentions.
The following leaked secrets are searched for:
| AWS client ID | AWS MWS key | AWS secret key | Connection string | Database file |
|---|---|---|---|---|
| Facebook access token | Facebook secret | Generic API key | Generic secret | GitHub |
| Google API key | Google OAuth | Google OAuth access token | Heroku API key | Htpasswd File |
| LinkedIn secret | Log file | Mailchimp API key | Managed cloud services | Outlook Team |
| Password In CURL | Password In URL | Password manager file | PayPal Braintree access token | Picatic API key |
| Private key | Private key file | Remote Desktop Connection file | SFTP configuration file | Slack |
| Slack webhook | Square access token | Square OAuth secret | SSH key | SSH password |
| Stripe API key | Twilio API key | Twitter secret | User and password | User password and domains |
Asset mention threats
Each line on the Asset Mentions tab displays a company asset that was found in a single Git public repository. These assets are defined in the Code mentions and Domains assets.
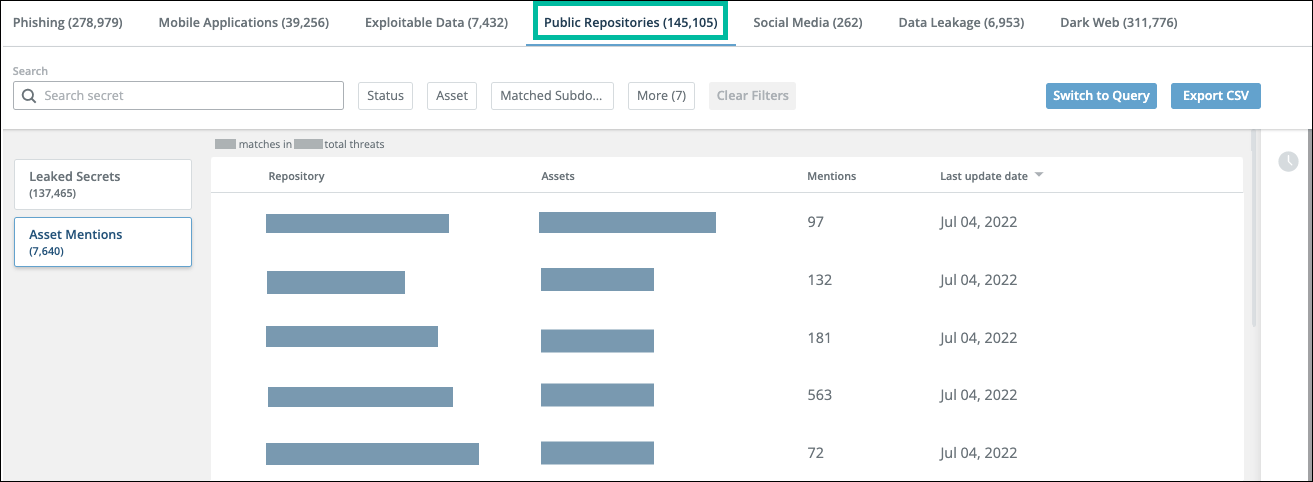
The threats displayed in the previous figure were found in separate repositories, with 97, 132, 181, 563, and 72 mentions in each repository, respectively.
To see the threat details, click the threat line:
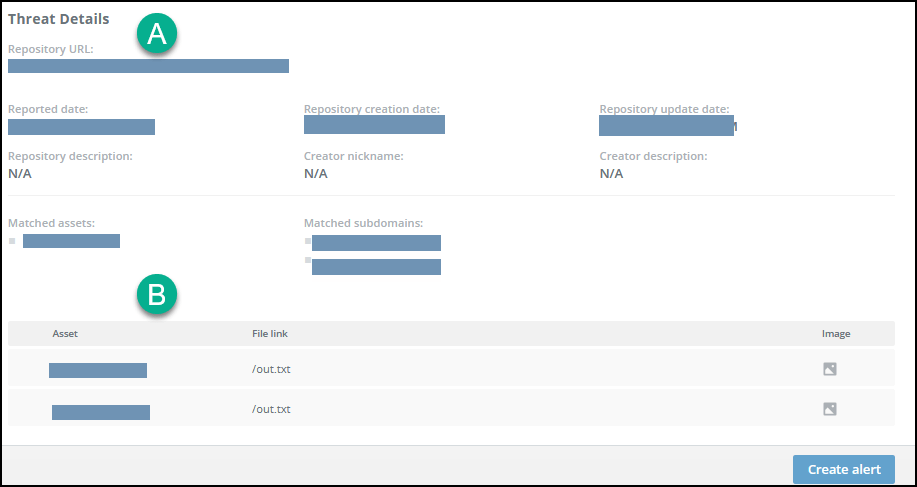
The threat details are presented in these sections:
-
Repository information (section A) - Displays all relevant information about the detected repository and the assets that matched the repository content.
-
Asset mention details (section B) - Displays a table that details all the places in the code where the assets were mentioned. Every mention includes information about the. A highlighted image of the mention in that file is displayed. Scroll to see multiple mentions.
You can use the Alert Profilerto fine-tune which threats trigger alerts.