Configure Azure as an SSO source for the Command Platform
This article covers how to configure a Rapid7 Command Platform single sign-on (SSO) source for use with Azure.
Create the Rapid7 Command Platform application in Azure
To create a new enterprise application in Azure:
- In Azure, navigate to Enterprise Applications > New Application > Create your own Application.
- In the application wizard on the right side of the screen, give your application an identifiable name such as
Rapid7. Select the option Integrate any other application you don’t find in the gallery and click Create.
Basic SAML configuration in Azure
Before you can download your SAML Certificate, you must first complete the Basic SAML Configuration in Azure.
To complete the Basic SAML Configuration:
- In the Basic SAML Configuration section in Azure, click Edit.
- In the Command Platform, navigate to Company Settings > Authentication Settings > SSO Settings.
- From the Select your identity provider (IdP) dropdown, select Azure.
- From the section titled Copy the following data into your external IdP, copy the Identifier (Entity ID) and replace the default URL in Azure with this.
- Next, copy the Reply URL and paste this into Azure.
- Finally, copy the Relay State and paste this into Azure and click Save.
Now that the Basic SAML Configuration is complete, your SAML Certificate becomes downloadable.
Add the Azure certificate to the Command Platform
Before downloading the certificate:
-
Edit Certificates.
-
Update Signing options to “Sign Assertion and Response” and save.
-
Create a new certificate and activate it.
-
Delete the old certificate.
To download the certificate:
- Ensure you have completed the Basic SAML Configuration section in Azure.
- In the SAML Signing Certificate section, click Download next to Certificate (Base64).
To add the IdP certificate to the Command Platform:
- From the left menu of the Platform Home page, click the Administration link.
- In the left menu of the Administration page, click Settings.
- Click the SSO Settings tab in the Authentication Settings section.
- Drag and drop your IdP certificate, or click Browse to search for it on your local machine.
Attributes and claims
Attribute statements are mandatory for authentication to the Command Platform.
To configure these attribute statements:
- Click Edit on the Attributes and Claims section in Azure.
- Leave Unique User Identifier (Name ID) unchanged.
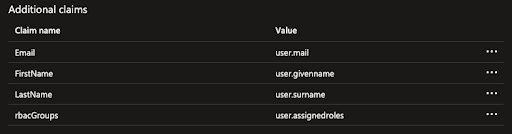
- Edit the user.mail claim by changing the Name value to
Emailand removing the Namespace value, then click Save. - Edit the user.givenname claim by changing the Name value to
FirstNameand removing the Namespace value, then click Save. - Edit the user.surname claim by changing the Name value to
LastNameand removing the Namespace value, then click Save. - Close the Attributes and Claims window.
Configure the Command Platform
Next, you will need to configure the Command Platform with fields from Azure.
To complete the Command Platform configuration:
- From the section Set up Command Platform (or your chosen name for the app) in Azure, copy the URL labeled Azure AD Identifier and paste it into the corresponding field in the SSO Settings tab in the Command Platform.
- Copy the field labeled Login URL and paste it into the corresponding field in the SSO Settings tab in the Command Platform.
The Command Platform should now be fully configured as an SSO-enabled enterprise app in your deployment of Azure AD, and you can now test SSO to verify this. Ensure you test the connection with a user that has been assigned to the Command Platform app in Azure.
Set up a default access profile
A default access profile allows you to define the products and roles that are automatically assigned to new users provisioned in Azure. See our default access profile documentation for instructions.
Group Synchronization
Group Synchronization allows you to control user group assignment from within your IdP.
This capability is made possible by including an attribute in your SAML response that contains the name(s) of the Command Platform User Groups for each user. Your users will be automatically assigned to the corresponding groups in the Command Platform and will inherit the product, role, and resource access associated with those groups.
With Group Sync enabled, IdP users will be removed from any Command Platform groups not included in their SAML assertion. IdP Users will retain any roles or permissions assigned directly to them, including those from a default access profile.
Configure user groups
As Group Synchronization requires the use of Command Platform User Groups, it is important that you have configured groups before activating. Read our Command Platform User Groups documentation for details on how to do this.
Adding the Group Attribute
To synchronize groups from Azure, the name of your Command Platform user groups must not contain any spaces.
In Azure, the first step is to create App Roles that will map to your Command Platform user groups.
To create App Roles:
- In Azure Active Directory, navigate to App Registrations > All Applications.
- Search for your Rapid7 application.
- Click App Roles, then click Create app role.
- Give your Role a display name, then select Users and Groups as the Allowed member type.
- In the Value field, enter the name of the corresponding Command Platform user group.
The Value field is the value that will be included in the SAML assertion, and so it must be the same as the name of the Command Platform user group this role corresponds to. As Azure forces this value to contain no spaces, ensure your Command Platform user groups also do not contain spaces.
- Enter a description for this role, then click Apply.
- Repeat this for all your Command Platform user groups.
The next step is to assign the appropriate App Roles to your users.
To assign App Roles:
- In Azure Active Directory, navigate to Enterprise Applications and select your Rapid7 application.
- Navigate to Users and Groups.
- To begin assigning roles to users, click Add user/group.
- Search for and select the users and groups that should be assigned a given role.
- Select the role that represents this group of users in the Command Platform.
- Click Assign.
Once your App Roles are configured and assigned to users and groups, you now need to add an attribute to the SAML assertion containing the names of the groups each user is assigned to.
To add this attribute to your SAML assertion in Azure:
- In Azure Active Directory, navigate to Enterprise Applications and select your Rapid7 application.
- Click Single sign-on, then click Edit in the Attributes and Claims section.
- Click Add new claim and name it
rbacGroups. - Select user.assignedroles as the Source attribute.
- Click Save.
All the information we require from your IdP to synchronize users to Command Platform user groups will now be included when users authenticate using SSO.
Activate Group Synchronization
If you have your Command Platform user groups configured with corresponding IdP user groups included in the SAML configuration, you are ready to activate Group Synchronization.
Once Group Synchronization is activated, users will have their group memberships synced on each sign-in. This means that changes to group membership in your IdP will not be reflected in the Command Platform until the next time the user signs in.
The Command Platform does not support SCIM provisioning, so users removed from your IdP will need to manually deleted in the Command Platform.