Manage Command Platform users with role-based access control (RBAC)
User Management within the Command Platform provides a central location to create and manage users who need access to your Rapid7 Insight products. This user management system is powered by a role-based access control (RBAC) framework, which allows you to tune users’ access to products and data privileges according to their role within your organization.
RBAC encourages the principle of least privilege, which helps prevent users from accessing sensitive data or information irrelevant to their roles.
The Command Platform’s implementation of RBAC provides these benefits:
- Granular control: Control access to capabilities and resources at a granular level.
- SIEM (InsightIDR) and Log Management (InsightOps) customers can control access to logs and their related dashboards and reports.
- Application Security (InsightAppSec) customers can control access to products and features.
- Reduced administrative burden: Manage access for many users at once by altering the privileges associated with roles and user groups.
- Reduced complexity and errors: Create and maintain user accounts with ease by granting access based on user roles within your company.
Objects of the Command Platform RBAC system
The Command Platform’s implementation of RBAC defines these objects that you can use to configure access privileges for users:
- Product roles - You can assign multiple roles to a user to provide the level of access that is appropriate for their job duties. For example, a user may have an Administrator role in Application Security (InsightAppSec) and an Analyst role in SIEM (InsightIDR) at the same time.
- Product-specific Rapid7 built-in roles - These roles can vary by Insight product, and are based on common use cases and scenarios.
- Custom roles - SIEM (InsightIDR), Application Security (InsightAppSec), Log Management (InsightOps), and Attack Surface Management (Surface Command) customers can create custom roles or copy and customize Rapid7 built-in roles to suit your needs.
- User groups - Create user groups to easily manage product access, role assignment, and data access for many users at once.
- Data access - Configure specific data access rules by specifying the resources a user or user group should have access to.
Overview
You can take actions to manage your users’ permissions and access from the User Management Overview page:
- You can get an overview of the total number of users, groups, roles, conflicts, and access requests, so you can quickly take action to grant access, resolve conflicts, or edit users, groups, or roles.
- You can create new users, create new groups, and create new roles from the Quick Tasks section.
- The Authentication Health report gives you an insight of the authentication settings and their status.
Manage users
In this section, we explain how to add, edit, and delete users, as well as how to view user access and troubleshoot some user account issues.
Create users
Platform Administrators can add a user to the Command Platform and grant them access to any product. Product Administrators can also add users, but can only grant access to products they themselves have access to.
To add a user:
- From the left menu of the Platform Home page, click User Management > Overview.
- Click Create New User. The Create User panel appears.
- Enter user details:
- Email: This must be a valid email address associated with the user. You can use a distribution list as the user email address if you want, but if you do, make sure to assign read-only access to the associated user account and verify that the account does not have Administrator privileges
- First name, last name, and time zone: These fields are editable after the account is created from the user’s Profile Settings.
- Click Create User. The User is created and you are redirected to the User profile/user details page.
- Here you can assign Group access and Individual access (including data access) for the user.
Create a custom role
Platform administrators can also create custom roles which can provide users with a combination of feature permissions for Application Security (InsightAppSec), SIEM (InsightIDR), Log Management (InsightOps), and Attack Surface Management (Surface Command).
Not available in InsightGovCloud
This feature is not available for InsightGovCloud customers.
To create a custom role:
- From the left menu of the Platform Home page, click User Management > Overview.
- Click Create New Role.
- Provide a name and description of the custom role.
- In Permissions, select the products that you want to grant permissions for in this custom role.
- In the Feature Permissions table, select the features that you want to grant permissions for in this custom role and the permission level required.
- Click Create New Role.
Edit and delete users
You may need to edit an existing user’s privileges, product access, data access, or account details, or you may need to delete their account altogether. You can do all of this from the individual user’s pages in Users.
Edit group access
- From the left menu of the Platform Home page, click the User Management dropdown and click Users.
- Find the user you want to make changes to and click the User Name.
- In Group Assignments, click Manage Group Assignments.
- Select or deselect the checkbox for each of the groups you want to add or remove a user from. There is an overview of the products, roles, and users, as well as additional group details in each group detail.
- Click Save Group Access to apply your changes.
Edit individual access
- From the left menu of the Command Platform home page, select User Management > Users.
- Find the user you want to make changes to and click the User Name.
- In Individual Privileges, click Manage Individual Privileges.
- Select or deselect the checkbox for each of the capabilities you want to add or remove access for.
- In roles, add or remove roles as required.
- If applicable, in the Manage data access dropdown, assign the specific data access required.
- Click Save Individual Privileges to apply your changes.
Edit user name and time zone
- From the left menu of the Platform Home page, click the User Management dropdown and click Users.
- Find the user you want to make changes to and click the User Name.
- Click Edit User Details.
- Adjust the user’s First Name, Last Name, and Time Zone as needed.
- Click Save User Details to apply your changes.
Delete a user
- From the left menu of the Platform Home page, click the User Management dropdown and click Users.
- Find the user you want to delete and click to open the user overview.
- Click Delete User.
View user access
You can access individual user profiles to view all of the products, roles, groups, and resources a user is assigned. The user profile also highlights whether access was assigned directly or if it was inherited through a user group. This is helpful if you’re trying to troubleshoot issues with a specific user’s level of access.
Authentication health scorecard
You can review SSO (Single Sign On), MFA (Multi-Factor Authentication), and Password Policy from Overview. The health report provides an overview of the authentication settings in your account, including whether these authentication options are active for your organization, what these authentication options do, and directing you to the settings pages for each of these authentication steps. Based on the status of these settings, we may recommend changes to improve security.
Troubleshoot user account issues
If a user is having issues accessing their Command Platform account, see the following common troubleshooting scenarios and the steps you can take to resolve the issue.
Account locked
If a user is having trouble signing in to the Command Platform, you can use the Reset Password button to send an email to the user, allowing them to reset their password, security question, and security question answer.
Account not activated
If a user’s account status shows that it is pending activation, you can use the Resend Activation Email button to send an email to the user, providing them with a new activation link.
Multi-factor authentication issue
If the user has issues with their multi-factor authentication (MFA) configuration or needs to register a new device for MFA, click the Reset MFA button and the user will receive an email letting them know how to reconfigure their MFA settings.
How to create and manage user groups
User groups are collections of users that are assigned the same products, roles, and data access. What users, products, roles, and data access you include in a user group is entirely up to you. You can also include users in many user groups, giving you flexibility to manage access in the way that works best for you.
Create a user group
- From the left menu of the Platform Home page, click the User Management dropdown and click Overview.
- Click Create New Group.
- Enter a Group Name and a Group Description to make it easy for you and others to find and identify this user group in the future.
- Click Create Group.
- Your group has been created and you can now assign product access and roles in Group Privileges. Select the required products and roles and click Save Group Access once you’re done.
- You can select users to add to this newly created group in Group Members. Select the users you want to add to this group and click Save Group Members when you’ve finished your selection.
Edit a user group
- From the left menu of the Platform Home page, click the User Management dropdown and click Groups.
- Find the user group you want to edit and click to open the Group overview.
- You can edit the group name and description.
- Click Manage Group Privileges and select or deselect the checkbox to modify permissions. You can also edit the user role and data access as required. Click Save Group Access once you’re done.
- Click Manage Group Members and select users to add to the group. Click Save Group Members when you’re done.
Delete a user group
- From the left menu of the Platform Home page, click the User Management dropdown and click Groups.
- Find the group you want to delete and click the ellipsis (…) and click Delete Group.
- Confirm that deleting this group won’t lead to any users losing required access.
- Click Delete Group.
Roles
Platform Administrator
A Platform Administrator user has full, administrative access to the Command Platform and can perform all of the tasks outlined in the Platform overview, including all aspects of User Management, Company Settings, and Platform Reporting and Dashboard permissions. You should appoint more than one Platform Administrator to ensure you have adequate administrative coverage.
The Platform Administrator role is distinct from other user roles and is treated as a binary state — a user can be a Platform Administrator, or not a Platform Administrator. When creating a new user, this will be the first data privilege decision you make.
Product access for Platform Administrators
Platform Administrators do not have product access by default and can’t complete product-specific tasks unless assigned to a product. If you want a user to have full administrative capabilities on the Command Platform as well as within each product they’re assigned, ensure they are set as a Platform Administrator and are assigned the Admin user role for each product.
Rapid7 built-in roles
Rapid7 built-in roles are available to users of SIEM (InsightIDR), Application Security (InsightAppSec), and Log Management (InsightOps). These roles are defined and maintained by Rapid7 and vary by Insight product to align with product-specific workflows and contexts.
SIEM (InsightIDR) built-in roles
Feature reference
For more information on what each feature governs as well as the levels of access available to the feature, review the following table:
| Feature | Permissions Options | Description |
|---|---|---|
| SIEM (InsightIDR) Core | View Only, View and Change, Administer | Determines access to all of the SIEM (InsightIDR) features that are not managed by another feature, including Assets and Endpoints, Automation, Alerts, Investigations, and Detection Rules
|
| Collector | View Only, Administer | Determines access to collectors and event sources
|
| Log Search Dashboards | View Only, View and Change, Administer | Determines access to Dashboards and Reports
|
| Log Management and Querying | View Only, View and Change, Administer | Determines access to log management and query features
|
| Hosted Velociraptor (if included in your license) | Investigate (create and edit Velociraptor Investigations) and View only (read existing Velociraptor results) | Determines access to Hosted Velociraptor features. This can be configured in custom roles, but is not included in any built-in roles. |
Built-in roles reference
For more information on what each SIEM (InsightIDR) built-in role can access within the product, review the following drop-down sections:
SIEM (InsightIDR) Admin
The SIEM (InsightIDR) Admin role has full access to the product. The role allows for View and Change privileges on all product features, allows the user to view and manage collectors and other data collection objects, and includes Platform Reporting and Dashboard permissions. This role is suitable for use with the following products:
- SIEM (InsightIDR)
| Feature | Permission |
|---|---|
| SIEM (InsightIDR) Core | Administer |
| Collector | Administer |
| Detection and Response Dashboards | Administer |
SIEM (InsightIDR) Analyst
The SIEM (InsightIDR) Analyst role has partial View and Change privileges and is able to edit most parts of the product except for collectors and data management in general. This role includes Platform Reporting and Dashboard permissions. This role is suitable for use with the following products:
- SIEM (InsightIDR)
| Feature | Permission |
|---|---|
| SIEM (InsightIDR) Core | View and Change |
| Detection and Response Dashboards | View and Change |
SIEM (InsightIDR) Viewer
The SIEM (InsightIDR) Viewer role allows for viewing most parts of the product. This role is suitable for use with the following products:
- SIEM (InsightIDR)
| Feature | Permission |
|---|---|
| SIEM (InsightIDR) Core | View Only |
| Detection and Response Dashboards | View Only |
Log Search Admin
The Log Search Admin role has administrator privileges on Log Search features. This role is suitable for use with the following products:
- SIEM (InsightIDR)
- Log Management (InsightOps)
| Feature | Permission |
|---|---|
| Log Management and Querying | Administer |
| Log Management (InsightOps) Log Archiving | Administer |
| Log Management (InsightOps) Log Usage | View Only |
Log Search View and Change
The Log Search View and Change role has View and Change privileges on Log Search features. This role is suitable for use with the following products:
- SIEM (InsightIDR)
- Log Management (InsightOps)
| Feature | Permission |
|---|---|
| Log Management and Querying | View and Change |
| Log Management (InsightOps) Log Archiving | View and Change |
| Log Management (InsightOps) Log Usage | View Only |
Log Search View Only
The Log Search View Only role has View privileges on Log Search features. However, the user will be unable to save queries, create alerts, create dashboards, or manage S3 archiving. This role is suitable for use with the following products:
- SIEM (InsightIDR)
- Log Management (InsightOps)
| Feature | Permission |
|---|---|
| Log Management and Querying | View Only |
| Log Management (InsightOps) Log Archiving | View Only |
| Log Management (InsightOps) Log Usage | View Only |
Log Search Rapid7 Agent (Insight Agent) Service role
The Log Search Rapid7 Agent (Insight Agent) Service role has View privileges on Log Search features. However, the user will be unable to save queries, create alerts, create dashboards, or manage S3 archiving. This role is suitable for use with the following products:
- SIEM (InsightIDR)
- Log Management (InsightOps)
| Feature | Permission |
|---|---|
| Log Management and Querying | View Only |
| Log Management (InsightOps) Log Archiving | View Only |
| Log Management (InsightOps) Log Usage | View Only |
Log Management (InsightOps) built-in Roles
| Role | Suitable for use with | Capabilities |
|---|---|---|
| Log Management (InsightOps) Admin | Log Management (InsightOps) | The Log Management (InsightOps) Admin role has full access to the product. This role includes Platform Reporting and Dashboard permissions. |
| Log Management (InsightOps) View and Change | Log Management (InsightOps) | The Log Management (InsightOps) View and Change role has partial View and Change privileges throughout the product except for data management in general. |
| Log Management (InsightOps) View Only | Log Management (InsightOps) | The Log Management (InsightOps) View Only role has limited View access to the product. |
| Log Search Admin | SIEM (InsightIDR) and InsightOps | The Log Search Admin role has administrator privileges on Log Search features. |
| Log Search View and Change | SIEM (InsightIDR) and InsightOps | The Log Search View and Change role has View and Change privileges on Log Search features. |
| Log Search View Only | SIEM (InsightIDR) and InsightOps | The Log Search View Only role has View privileges on Log Search features. However, the user will be unable to save queries, create alerts, create dashboards, or manage S3 archiving. |
Application Security (InsightAppSec) built-in roles
| Role | Suitable for use with | Capabilities |
|---|---|---|
| Application Security (InsightAppSec) Admin | Application Security (InsightAppSec) | The Application Security (InsightAppSec) Admin role has full access to the product. This role includes Platform Reporting and Dashboard permissions. |
| Application Security (InsightAppSec) View and Change | Application Security (InsightAppSec) | The Application Security (InsightAppSec) View and Change role has partial View and Change privileges throughout the product. This role includes Platform Reporting and Dashboard permissions. |
| Application Security (InsightAppSec) View Only | Application Security (InsightAppSec) | The Application Security (InsightAppSec) View Only role has limited View access to the product. |
| Application Security (InsightAppSec) App Owner | Application Security (InsightAppSec) | The App Owner role can set up apps and configure settings within the app, but has lesser privileges to scan configurations and vulnerabilities. |
| Application Security (InsightAppSec) Scan Manager | Application Security (InsightAppSec) | The Scan Manager role can create scan configurations and run scans, but can’t edit apps or view vulnerabilities. |
| Application Security (InsightAppSec) Remediator | Application Security (InsightAppSec) | The Remediator role can fix, manage, and replay attacks on vulnerabilities within apps they can access, but can’t manage apps or scans. |
Cloud Security (InsightCloudSec) built-in roles
| Role | Suitable for use with | Capabilities |
|---|---|---|
| ICS Domain Viewer | Cloud Security (InsightCloudSec) | ICS Domain Viewers have all permissions for all cloud resources throughout Cloud Security (InsightCloudSec) but cannot take any actions. This role includes Platform Reporting and Dashboard permissions. |
| ICS Basic User | Cloud Security (InsightCloudSec) | ICS Basic Users start with no access to cloud resources and must be granted permissions explicitly |
| ICS Domain Administrator | Cloud Security (InsightCloudSec) | ICS Domain Administrators have all permissions for all cloud resources across the entire Cloud Security (InsightCloudSec) Platform installation. This role includes Platform Reporting and Dashboard permissions. |
| ICS Organization Administrator | Cloud Security (InsightCloudSec) | ICS Organization Administrators have all permissions for all cloud resources within a given Cloud Security (InsightCloudSec) organization or organizations. This role includes Platform Reporting and Dashboard permissions. |
Attack Surface Management (Surface Command) built-in roles
| Role | Suitable for use with | Capabilities |
|---|---|---|
| Attack Surface Management (Surface Command) Admin | Attack Surface Management (Surface Command) | Attack Surface Management (Surface Command) Admins have access to all functionality in Attack Surface Management (Surface Command). This role includes Platform Reporting and Dashboard permissions. |
Shared built-in roles by product
Product roles sometimes vary
Many Insight products use these shared user roles. However, some products interpret or apply these product user roles differently based on specific product use cases.
Vulnerability Management (InsightVM)
Product roles assigned to Vulnerability Management (InsightVM) users at the Platform level are ignored in favor of the more detailed and specialized Vulnerability Management (InsightVM) user roles, which are assigned to users by a Global Administrator in InsightVM. That means Platform users who are also Vulnerability Management (InsightVM) users are given Vulnerability Management (InsightVM) privileges associated with whatever role they’re assigned in InsightVM. Platform users who are not also Vulnerability Management (InsightVM) users are treated as Global Administrators.
Automation (InsightConnect)
Due to the nature of using Automation, Automation (InsightConnect) provides full access to all users who are assigned the Automation (InsightConnect) product. The View and View and Change roles at the user level do not apply. To restrict access to Automation (InsightConnect), deselect the Automation (InsightConnect) product for the given user.
Additional role information
Check out our Manage user groups and Manage users sections to learn more about how to assign these roles to groups as well as individual users.
Manage resource access
Manage resource access, which is available when creating or editing individual access for a user or user group, displays the available resources you can assign to users depending on the Insight products selected.
You can choose to view all available resource sets within an account or to view only the resource sets currently selected for the user. Use the check boxes to control which resources a user has access to.
Logs and log sets
Logs are available as assignable resources when there is an active InsightIDR or Log Management (InsightOps) product associated with your Insight account.
Default log access
By default, SIEM (InsightIDR) and Log Management (InsightOps) users will be assigned access to all current and future logs and log sets. The ability to manage log access at a user or user group level will not be available within from this page unless this default behavior is turned off.
You can turn off this default setting from the User Management Overview page so that all log access must be assigned to specific users or user groups by an Administrator in your account.
Restrict log access
As with other resources, use the check box next to each log to specify which user can access that particular log. Additionally, and unlike other resources, you have the option to restrict data access to individual logs by clicking the restricted icon in the log table.
If a user doesn’t belong to a user group, restricting log access amounts to the same thing as simply leaving the log unselected. However, if a user does belong to a user group, restricting log access allows you to override any log access the user inherited from the group.
To illustrate how restricting log access works in practice, here are a few common scenarios:
- A user is individually given access to Log A, and Log B is left unchecked.
- Result: The user only has access to Log A.
- A user is individually given access to Log A, and Log B is left unchecked. However, the user is also a part of a user group that has access to Log B.
- Result: The user has access to Log A and Log B.
- A user is individually given access to Log A, and Log B is marked as restricted. But the user is also a part of a user group that has access to Log B.
- Result: The user only has access to Log A.
Log and log set selection
Log and log set selection
When you select which logs a user should have access to, you can select entire groups of logs, called log sets, by clicking the check box next to the name of the log set. Alternatively, you can select every log within the log set. Regardless of your assignment method, giving a user access to an entire log set automatically grants them access to any logs added to that log set in the future.
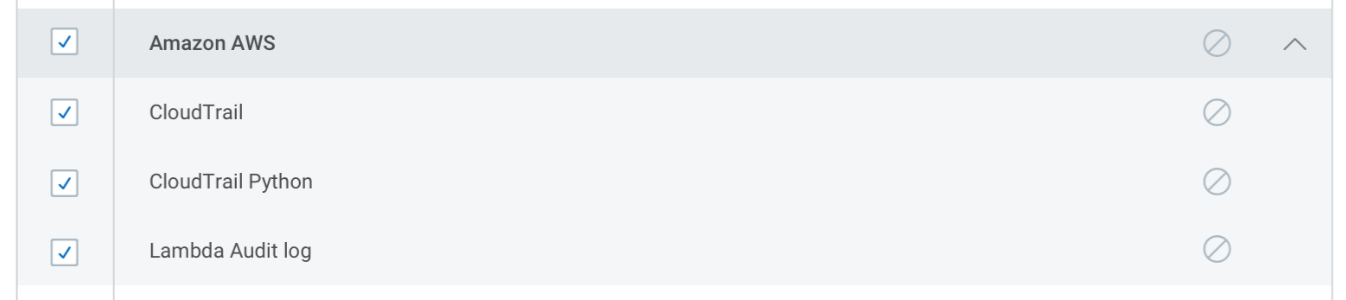
Similarly, if you restrict access to a log set, every log within the set is automatically restricted, as are any logs that are added to the set in the future.
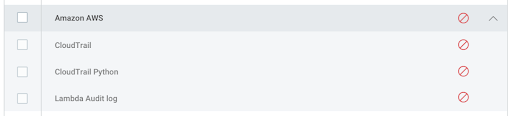
You can also select, deselect, and restrict access to individual logs within a set.
If you select only some, and not all, of the logs within a particular log set, the user is only given access to the selected logs, even if additional logs are added to the set in the future.
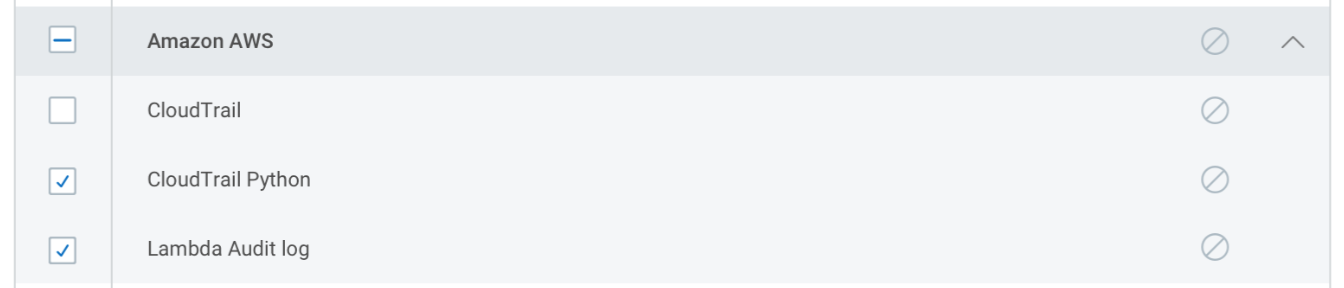
Similarly, if you select a log set, but restrict access to at least one log within the set, the user is only given access to the selected logs, even if additional logs are added to the set in the future.

Resolve permission conflicts
The nature of RBAC assignments means that conflicts in privileges may sometimes arise.
- Platform Administrators for individual products can resolve any conflicts by reviewing the cause of the conflict and adjusting privileges as needed.
- Product Administrators can only resolve conflicts if they are limited to the products they administer.
- There may be conflicts a Product Administrator can view but not resolve because the conflict includes access beyond their administration scope.
Causes of privilege conflicts
You can review any conflicts in User Management > Conflicts to get more details about the type of conflict and a conflict description. There are 3 categories of conflicts: group conflicts, user conflicts, and conflicts associated with limited access. For group conflicts and user conflicts, the Command Platform defaults to the principle of least privilege, meaning the user is given the lowest privilege assigned to them until the source of the conflict is resolved.
User conflicts
A user conflict can be caused by:
- Directly assigning a user 1 role that has conflicting privileges with a role they inherited from a user group.
- Inheriting roles with conflicting privileges from one or more user groups
- Via the Insight Account API directly assigning a user 2 roles that grant them access to the same feature but with different levels of privilege.
Group conflicts
This is only possible via the InsightAccount API. A conflict can occur within a single user group when 2 or more roles within the group contain conflicting privileges. As always, the access level of all users within the group will be based on the principle of least privilege, meaning users will be granted the lowest privilege assigned to them.
Note: Groups created before previously may have this conflict.
Limited access conflicts
You’re notified of a limited access conflict when a user does not have the minimum required access for a product they are assigned. Minimum required access is what Rapid7 defines as the least access required for a user to be able to get value from the product they have access to. If these conflicts are not resolved, they impact a user’s ability to get valuable information from the product.
Rapid7 Agent (Insight Agent) Service role
You may frequently see limited access conflicts related to the Rapid7 Agent (Insight Agent) Service role. This is expected. The only purpose of this role is to allow you to configure the Rapid7 Agent (Insight Agent) to send logs.
Resolve a privilege conflict
Privilege conflict resolution methods vary by conflict type.
To identify the type of conflict:
- From the left menu of the Platform Home page, click the User Management>Conflicts.
- You can then view conflicts by type by selecting either the Group Conflicts, User Conflicts, or Insufficient Access tabs.
To resolve group conflicts:
- Click on the Group Name in the Group Conflicts tab. Review Features with conflicts to identify what changes are required to resolve the conflict.
- Click Edit Group Privileges to edit the group access or group members.
To resolve user conflicts:
- Click on the User Name in the User Conflicts tab. Review Features with conflicts to identify what changes are required to resolve the conflict.
- Edit the groups that the user is assigned to.
- Edit the individual product access and roles the user has.
To resolve insufficient access conflicts:
- Find the User Name in the Insufficient Access tab. Review Features with conflicts to identify what changes are required to resolve the conflict.
- Click Edit Individual Privileges and edit the users’ product roles as required.
Access requests
Platform Administrators manage all product access and trial requests, any requests to add a new user to your company account, or to grant access to an external user (such as Rapid7 Support). A Product Administrator can only view and manage product access requests for products they administer.
How to grant or reject access requests
- In the left menu of the Command Platform user interface, click User Management>Access Requests.
- The Access Requests page provides an overview of the number of open requests in each category. Click the relevant tab:
- Product Access Requests
- Product Trial Requests
- New User Requests
- External User Requests
- Click Approve or Reject for each of the open requests.