Welcome to Managed Detection & Response (MDR)
This page outlines the technical overview of what to expect with the Managed Detection & Response service.
MDR Technical Overview
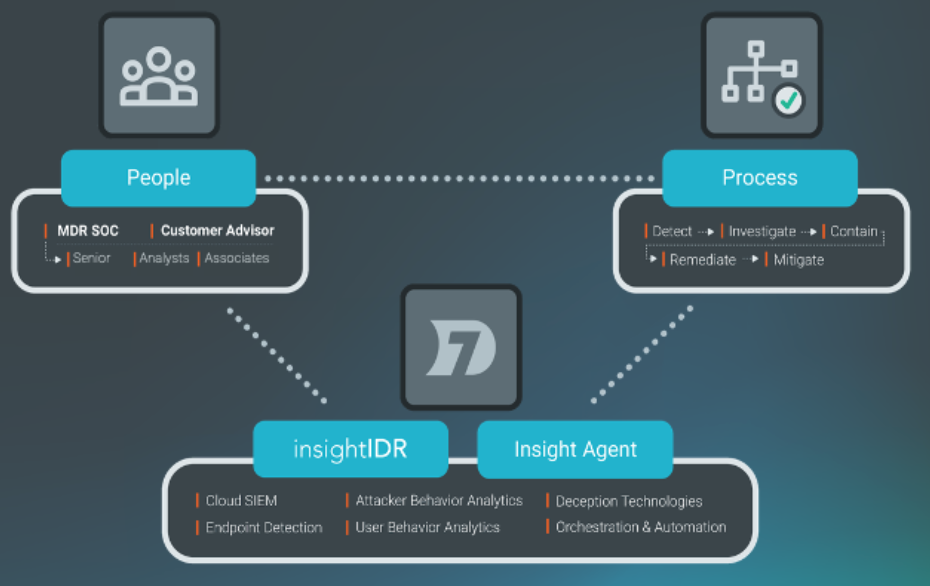
Rapid7’s Managed Detection and Response (MDR) service offers a combination of expertise and technology to detect dynamic threats quickly across your entire ecosystem, powered by Rapid7’s purpose-built technology stack, threat intelligence infrastructure, and our Security Operations Center (SOC) experts.
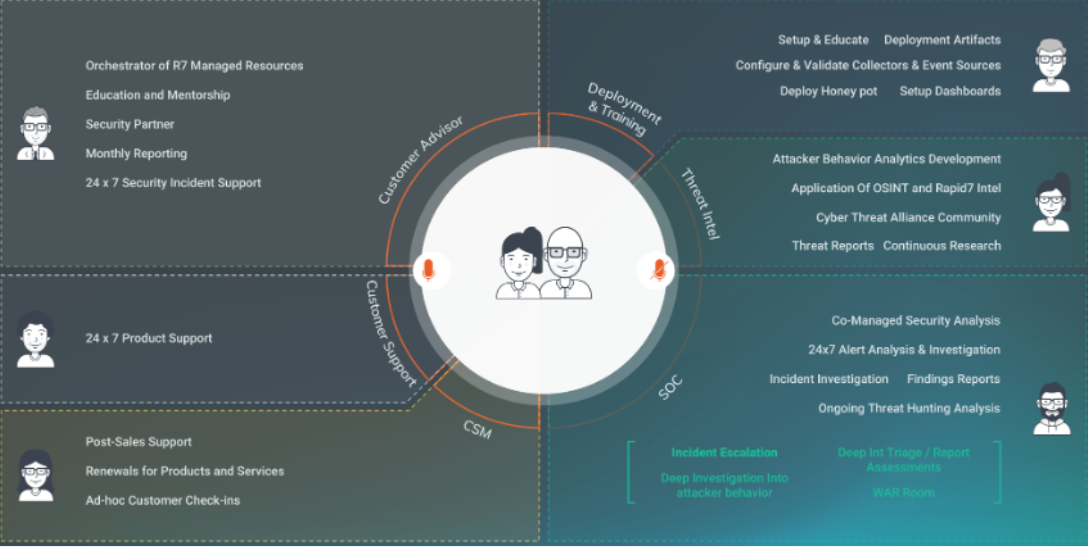
Cybersecurity Advisor Engagement
During the course of your MDR service, your team will engage with your assigned CA. This resource is available to answer any questions about the MDR service and offer security advisorship to advance your security maturity.
Cybersecurity Advisors are available during normal business hours by phone and email. During non-business hours, a member of the CA team is on-call via the CA Hotline if malicious activity is detected in your environment. Please see Contact Us tab for more information.
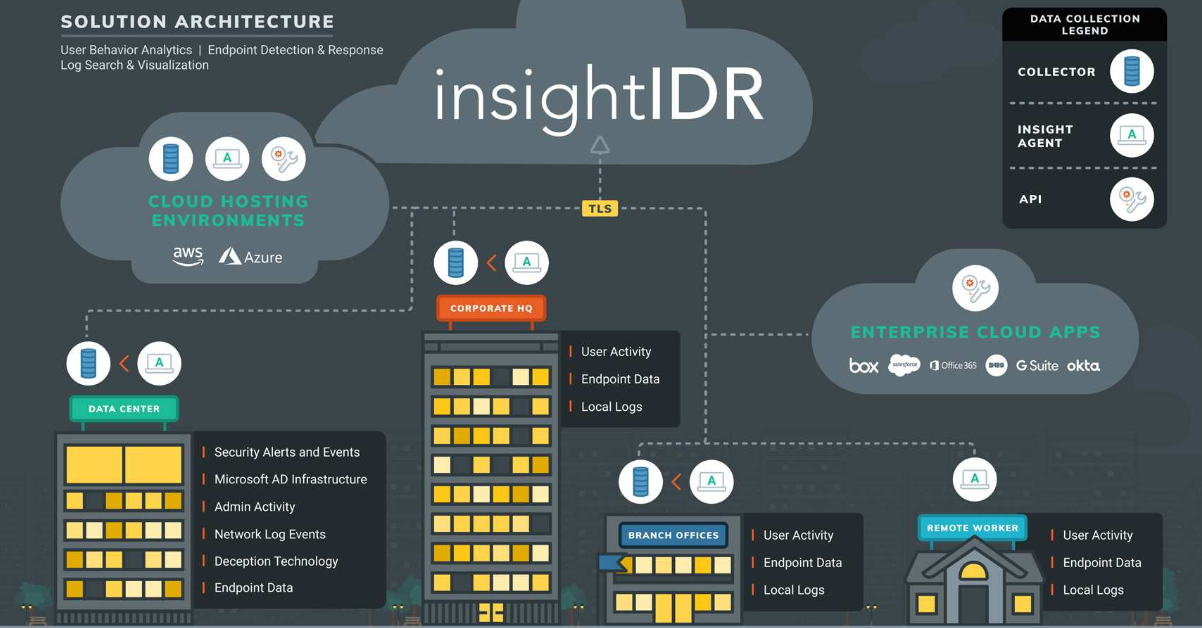
Event Collection
During the onboarding process, Rapid7’s MDR team will assist you in deploying the Rapid7 Agent (Insight Agent), a lightweight agent that sends endpoint event data to a data collector sitting behind your firewall. The purpose of this collector is to continuously gather real-time events from numerous log sources in the environment, including security event sources from a variety of network and security devices, such as firewalls, intrusion detection and prevention systems, DNS servers, cloud hosting environments, enterprise cloud applications, and security information and event management tools (SIEMs). This data is then synchronized with other event sources that include Active Directory to acquire user and permission details, which are then passed along with endpoint logs (user activities, endpoint data, and local logs on assets with the Rapid7 Agent (Insight Agent)). This data is sanitized to remove any noisy log data, encrypted, and sent to Rapid7’s Insight cloud. The agents and collector are provided by Rapid7 and installed by the customer. Updates are automatically pushed from Rapid7 to the collector and agents as needed.
Threat Detection
Throughout your onboarding onto the Insight cloud and the MDR service, our team is also learning about your network. Later, we’ll perform a Security Posture Assessment to further develop our intimate understanding of your environment. This enables our team to spot possible threats earlier when your event data is analyzed against our external threat intelligence and validated by the SOC team. Possible threats are identified using multiple threat detection methods, including:
- User Behavior Analytics (UBA): Analyzes user behavior and applies a series of heuristic and analytic rules to detect abnormalities such as compromised credentials, lateral movement, and other malicious behavior.
- Attacker Behavior Analytics (ABA): Analyzes endpoint behaviors to cross-reference against known attacker tactics, techniques, and procedures to find unknown attackers earlier in the attack chain.
- Deception Technologies: Set decoy technology assets (honeypots, honey users, and honey credentials) to find attackers and prevent them from infiltrating deep into the network.
- Threat Intelligence: Combines knowledge across research, threat intel, and the security community to continuously update rules and analytics capabilities to identify malicious activity in the customer’s environment.
- Threat Hunting: MDR analysts leverage metadata collected by the Rapid7 Agent (Insight Agent) to proactively hunt for persistent malware, historical application execution, unusual processes and network communications, Powershell invocation, ingress authentications, potentially unwanted programs or applications, and per-system anomalies that may be indicative of compromise or potential vulnerabilities.