Audit logging
Audit logging allows you to record both user driven and automated activity relating to your Rapid7 solutions. For every auditable action, you can see what the action was, the time that the action occurred, and who completed the action. By enabling audit logging, you have the ability track activity for investigative purposes. Audit logging will also help you fulfill compliance requirements if these details are requested by an external auditor.
You must have Administrator permissions to enable audit logging and to view audit log events.
Not available in InsightGovCloud
This feature is not available for InsightGovCloud customers.
To use the audit logging feature in the Command Platform:
Enable audit logging
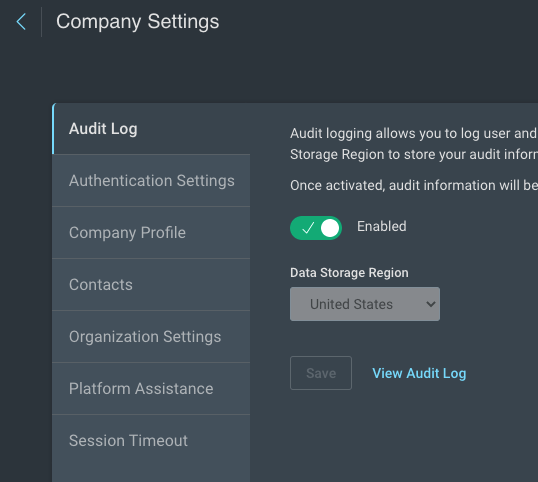
To enable audit logging:
- From the left menu of the Rapid7 Command Platform Home page, click the Administration link.
- On the Settings page, go to Audit Logs.
- Set the toggle to Enabled.
- Select the region where you want to store your audit log data.
You enabled audit logging!
Once you turn on audit logging, the Command Platform will immediately begin collecting all Platform and SIEM (InsightIDR) events.
View your audit log events
You can view your audit Log events in the Command Platform by going to the top navigation menu and clicking Settings > Audit Log.
To view your events, you can use the Audit Source log selector drop down to filter the table to show specific audit logs. You can also choose to view All Audit Logs. For each event on the table, you can see the time that the action occurred, details (Name and Email) of who completed the action and the product that the action occurred within.
You can filter to view actions taken by a specific user by searching for their username in the search bar. You also have the ability to search for any string within this search bar, such as an email or action.
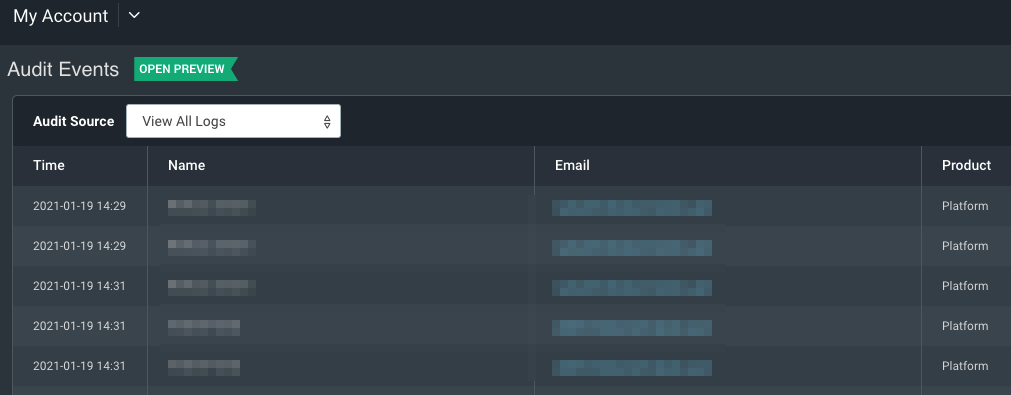
You can also confine your search to specific date ranges using the date selector component as part of the search bar. You can either type in the date range manually using the date/time box provided or you can click on the calendar to select the date range.
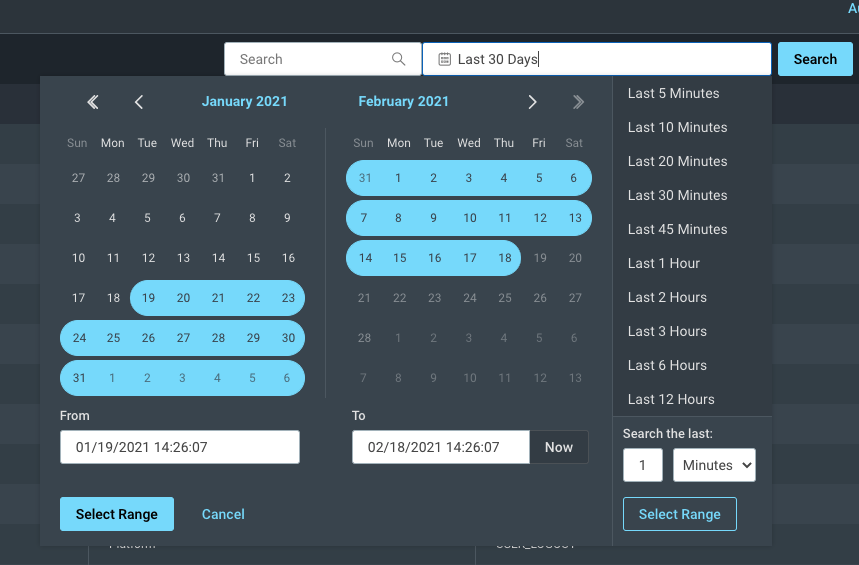
You can export your log search results to a CSV file directly from the Audit Table using the Export to CSV function beside the search bar. Once the CSV file has been exported, a green bar will appear and you will have the option to download it.
To view more details about an audit log Event, click View More in the More Details column. A window with additional details about the specific audit log event will appear.
SIEM (InsightIDR) audit log events
To see the SIEM (InsightIDR) audit log messages, read the audit logging documentation on the SIEM (InsightIDR) documentation site.
Application Security (InsightAppSec) audit log events
For information about Application Security (InsightAppSec) audit log messages, see audit logging in the Application Security (InsightAppSec) documentation site.
Custom Policy Builder
Within Vulnerability Management (InsightVM)‘s Custom Policy Builder, you can use audit logging to capture every policy update implemented by users. Audit logs record who, when, and what changes were made to a policy so a user or an auditor can view the change history of any policy at a later date. For more information, see the audit logs topic of the Custom Policy Builder Vulnerability Management (InsightVM) documentation.
Platform audit log events
This section outlines audit log events currently generated by Command Platform Services. The events are sorted into the following categories:
- API Key
- External Identity Provider (IDP)
- Key Contacts
- Multi-Factor Authentication (MFA)
- Organization
- Password Policy
- Organization Product
- User
- User Role
- User Access
- Customer
- Role Based Access Control (RBAC)
- Audit Log
API key events
| Action | Description |
|---|---|
| API_KEY_CREATED | New API key was created |
| API_KEY_DELETED | API key was deleted |
| API_KEY_MOVED | API key was moved to a new customer account due to a customer account merge |
When scheduled reports generate, they automatically create and delete API keys. These API key events (specifically the Create and Delete events) appear in your audit log. This is expected behavior and indicates that the reports have generated correctly.
Manual report generation uses temporary API keys
When you manually create a report, or generate one from a dashboard, Rapid7 creates a temporary API key in your customer account. This temporary key is created so that when the report runs, it is associated with the specific user who created it. The temporary key is used to create the report, then it is automatically deleted when the report has generated. This means the creation and deletion of the temporary API key is visible in your audit log.
External identity provider (IDP) events
| Action | Description |
|---|---|
| EIDP_ENABLED | User Authentication using an External IDP was enabled |
| EIDP_DISABLED | User Authentication using an External IDP was disabled |
| EIDP_X509_CERT_UPLOADED | An X509 security certificate was uploaded for the External IDP |
| EIDP_UPDATED | The configuration profile for the External IDP used for user authentication was updated |
| EIDP_DELETED | The configuration profile for the External IDP used for user authentication was deleted |
| JIT_PROFILE_UPDATED | The Just In Time provisioning profile applied to users accessing the Command Platform from an External IDP was updated |
Key contact events
| Action | Description |
|---|---|
| KEY_CONTACT_ADDED | New Key Contact was added |
| KEY_CONTACT_REMOVED | Key Contact was removed |
Multi-factor authentication (MFA) events
| Action | Description |
|---|---|
| MFA_UPDATED | MFA configuration data was changed |
Organization events
| Action | Description |
|---|---|
| ORG_NAME_UPDATED | Organization Display Name was changed |
| ORGANIZATION_MOVED | The organization was moved from one customer account to another due to a customer account merge |
Password policy events
| Action | Description |
|---|---|
| PASSWORD_POLICY_UPDATED | Password policy was modified |
Organization product events
| Action | Description |
|---|---|
| ORG_PRODUCT_CREATED | A new Rapid7 Product License was added to the Customer’s organization |
| PRODUCT_TRIAL_EVENT | A new product free trial was started |
User events
| Action | Description |
|---|---|
| USER_ACCOUNT_RESET | User account was reset |
| USER_CREATED | New user was created |
| USER_DELETED | User account was deleted |
| USER_MFA_RESET | User MFA was reset |
| USER_SUCCESS_LOGIN | User logged in |
| USER_UPDATED | User profile was updated |
| USER_ACTIVATED | User account was activated |
| USER_CHANGED_PASSWORD | User changed their password |
| USER_CHANGED_SECURITY_QUESTION | User changed their security question |
| USER_ACTIVATION_RESENT | User account activation email resent |
| USER_FORGOTTEN_PASSWORD | User forgot their password |
| USER_MOVED | User account was moved to another customer account due to a customer account merge |
| USER_LOGOUT | User logged out |
User role events
| Action | Description |
|---|---|
| USER_ROLE_SET | User role was set or updated |
User access events
| Action | Description |
|---|---|
| USER_TO_ORG_PRODUCT_CREATED | A user was assigned access to a product |
| USER_TO_ORG_PRODUCT_DELETED | A user was unassigned access to a product |
| USER_TO_PRODUCT_NAVIGATION | A user navigated to access a specified product |
| USER_SWITCHED_CUSTOMER | A user with multi customer account access navigated from their primary customer account to access another customer account |
| USER_CUSTOMER_MOVED | A user account was moved from one customer account to another due to a customer account merge |
Customer events
| Action | Action |
|---|---|
| CUSTOMER_NAME_UPDATED | The Customer Account Name was updated |
| CUSTOMER_MERGED | The Customer account was merged with another customer account |
Audit log events
| Action | Description |
|---|---|
| AUDIT_LOG_OPT_IN | Audit Logging was turned on |
| AUDIT_LOG_OPT_OUT | Audit Logging was turned off |