OS Command Injection (OS Commands)
OS Commands is a serious vulnerability that allows malicious actors to execute commands on the host operating system. This vulnerability is typically discovered using common security tools and scanners, such as Burp Suite. tCell protects your application from OS Commands attacks by monitoring all commands that your application issues to the operating system, and blocking all commands that aren't allowlisted.
What is it?
An OS Commands attack occurs when a malicious actor is able to successfully execute arbitrary commands on a host operating system by exploiting a vulnerability in an application. A successful attack allows a malicious actor to have access to the host operating system with the privileges of the application server. As a security best practice, you can avoid vulnerabilities by always validating input, keeping all 3rd-party packages and libraries up to date, and using frameworks features to tightly control how commands are launched to design a more secure application. OWASP’s Injection Prevention Cheat Sheet can help you learn more about preventing OS Commands attacks.
How do malicious actors find vulnerabilities?
Most malicious actors begin by using an application security scanner to scan an application for OS Commands vulnerabilities. Actors will also manually investigate and discover all of the application’s HTTP headers, as well as parameters in the URL and body. Using this information, they can test modifications to those values to discover OS Commands vulnerabilities using techniques more sophisticated than the security scanner. Additionally, actors will analyze HTTP response headers and error messages to gain more information about your application server, such as the server and framework versions. If the version has a known OS Commands CVE listed in a vulnerability database, the actor would try to test the application server using frameworks such as Metasploit. A good example of this is the Apache Struts vulnerability (CVE-2017-9805) where versions 2.1.2 - 2.3.33 and 2.5 - 2.5.12 are vulnerable to a Java deserialization attack that allows command execution. If the actor discovers that you are using a vulnerable version of Apache Struts, they would use the Metasploit Framework to exploit your application. For more details, check out https://www.rapid7.com/db/modules/exploit/multi/http/struts2_rest_xstream
How do I use tCell to protect my application?
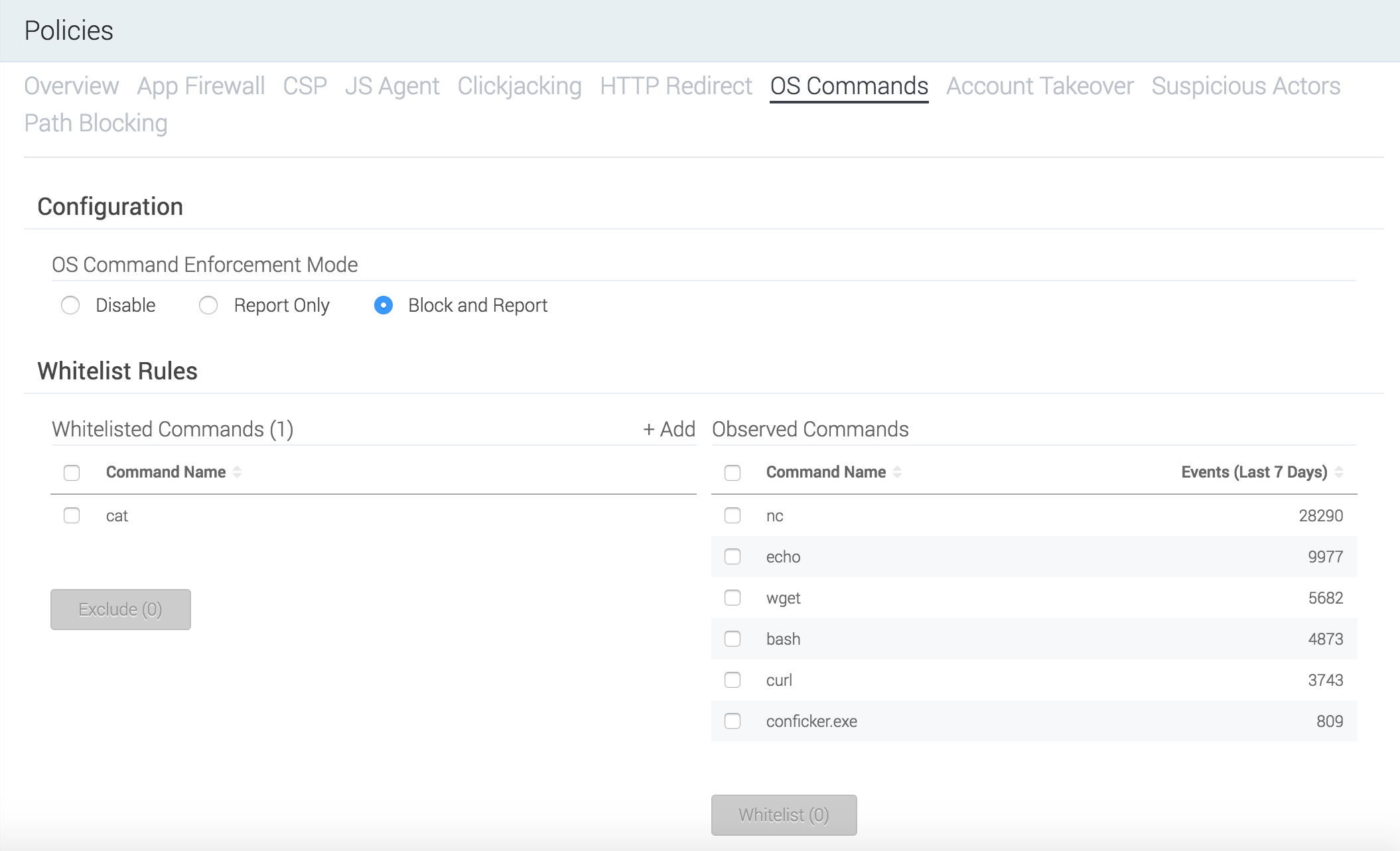
tCell can detect and block successful OS Commands attacks. We instrument your application and monitor the commands it issues to the host operating system. In the default Report Only mode, OS Commands will relay the commands being run to the tCell service, but will not prevent any from running.
In your tCell console, go to Policies > OS Commands and look at the Observed Commands column. Note that at this time tCell displays only the command and not any parameters that may have been sent as part of the command. For example, if the command is curl www.tcell.io, the list will display curl. It’s recommended that you run the application in a test environment that is not internet accessible with simulated regular user traffic and then allowlist all of the commands that appear in that column. After you’ve created a list of allowlisted commands, change the OS Command Enforcement Mode from Report Only to Block and Report. tCell continues monitoring the commands issued to the host operating system and blocks any commands that are not allowlisted. This protects your application from being exploited from well-known, as well as 0–day, OS Commands vulnerabilities.
As an additional layer of security, tCell also detects OS Commands attack attempts and protects against them with the App Firewall feature. Please see our guide on SQL Injection to learn more about this feature.
Some more reading: