SQL Injection
SQL Injection is a serious vulnerability that allows malicious actors to execute SQL statements. This could lead to data theft, data loss and account takeover. This vulnerability is typically discovered using common security tools and scanners, such as Burp Suite. tCell's App Firewall monitors your application for SQL injection and SQL exception events and uses its analytics engine to determine and then block Suspicious Actors.
What is it?
A SQL injection attack occurs when a malicious actor injects a SQL statement into an application for execution. A successful attack allows a malicious actor to retrieve and modify the contents of a database, potentially causing a myriad of issues such as data theft, data loss, and account takeover. The security best practice to avoid being vulnerable is to parameterize all SQL queries. OWASP’s SQL Injection Prevention Cheat Sheet is a great resource to learn more about preventing SQL injection.
How do malicious actors find vulnerabilities?
Most commonly, a malicious actor would use an application security scanner, such as Burp Suite to scan an application for SQL injection vulnerabilities. The actor would also spend time to manually discover all of the application’s parameters in the URL, header and body, and then modify them to test them for SQL injection vulnerabilities using techniques that are more sophisticated than the security scanner. Here is a good SQL injection cheat sheet.
How do I use tCell to protect my application?
SQL injection detection is part of tCell's App Firewall feature and is enabled by default. To verify that it’s enabled, log in to your tCell console and go to Policies > App Firewall. Ensure that Enabled is checked for the "App Firewall" and ensure that Enabled is checked under the "SQL Injection" category. You will also see the settings for SQL Injection in this section. While the default settings may work for some customers, it may not work for others. Please see our guide on tuning the App Firewall for more information. Additionally, ensure that Enabled is checked under "App Exceptions" and that SQL Exceptions is checked under the "Settings" below.
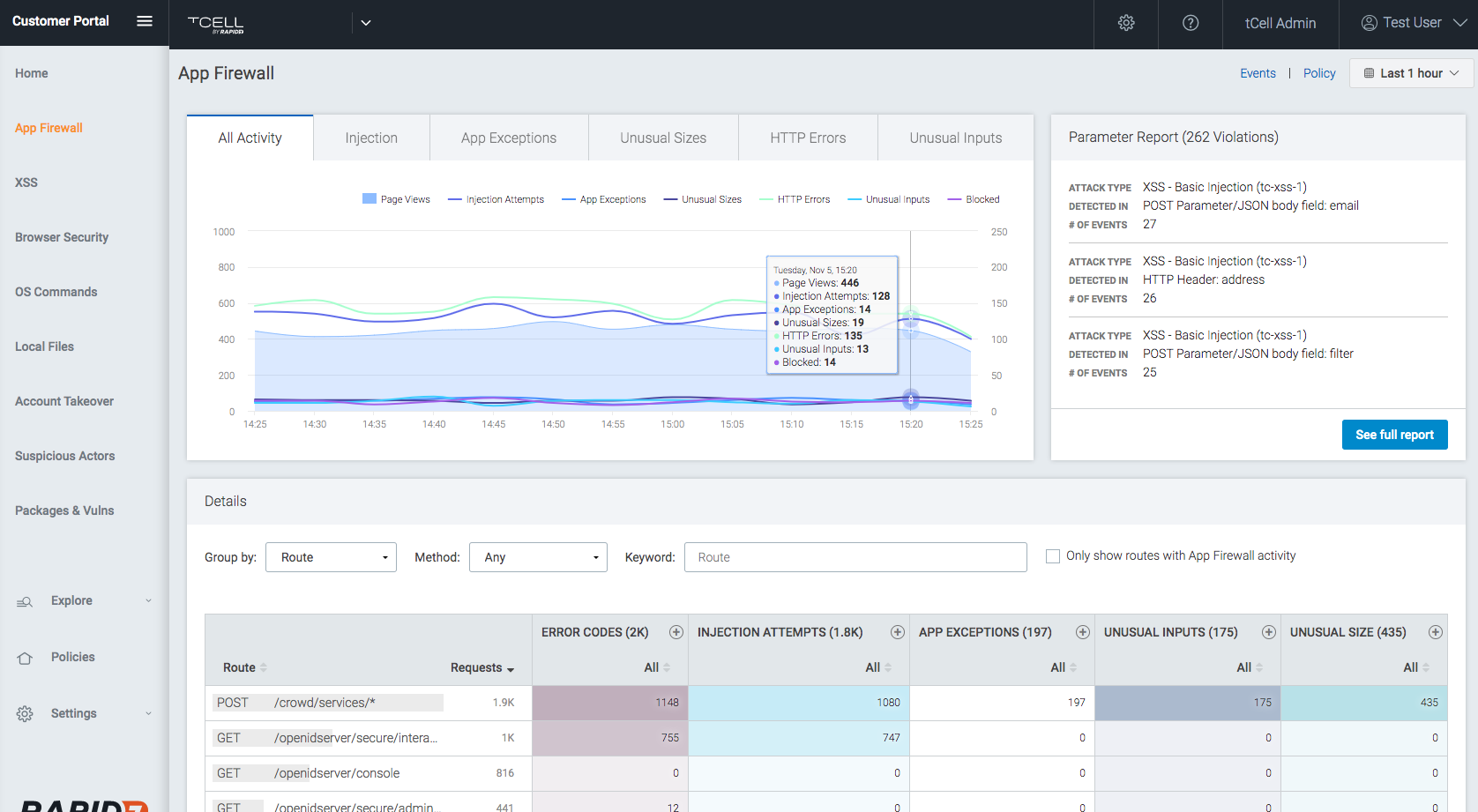
The App Firewall will detect and track SQL injection attempts as well as SQL exception events. To see these events, in your tCell console, go to Dashboards -> App Firewall. It will display charts showing the frequency of these events. On the top right, you can change the time range.
To get more details about an individual event, click on the event count in any column of the Activity chart or go to Events -> App Firewall. Under Filter By, make sure that Detection Point and Includes are selected. Enter sql in the field and click Add. To see the SQL exception events, repeat the steps above entering exsql in the field. To get more details about a particular event in the list, click on the right arrow next to the IP address for that event.
It’s important to note that if a SQL exception happens due to a SQL injection attempt, it’s likely a malicious actor has discovered a SQL injection vulnerability in the application. Although tCell can protect you from the attack, the security best practice is to also fix the vulnerability in the code.
All of the events detected by the App Firewall feed tCell’s analytics engine which determines Suspicious Actors. This is a different technique than older technologies, such as a WAF, as tCell doesn’t make decisions on a per transaction basis. This allows us to cut the noise and significantly decrease the amount of false positives. Note, a malicious actor will continue to be identified as suspicious until all suspicions activity has ceased from the actor’s IP for a period of 24 hours. You can always see a list of current Suspicious Actors by going to Dashboards -> Suspicious actors.
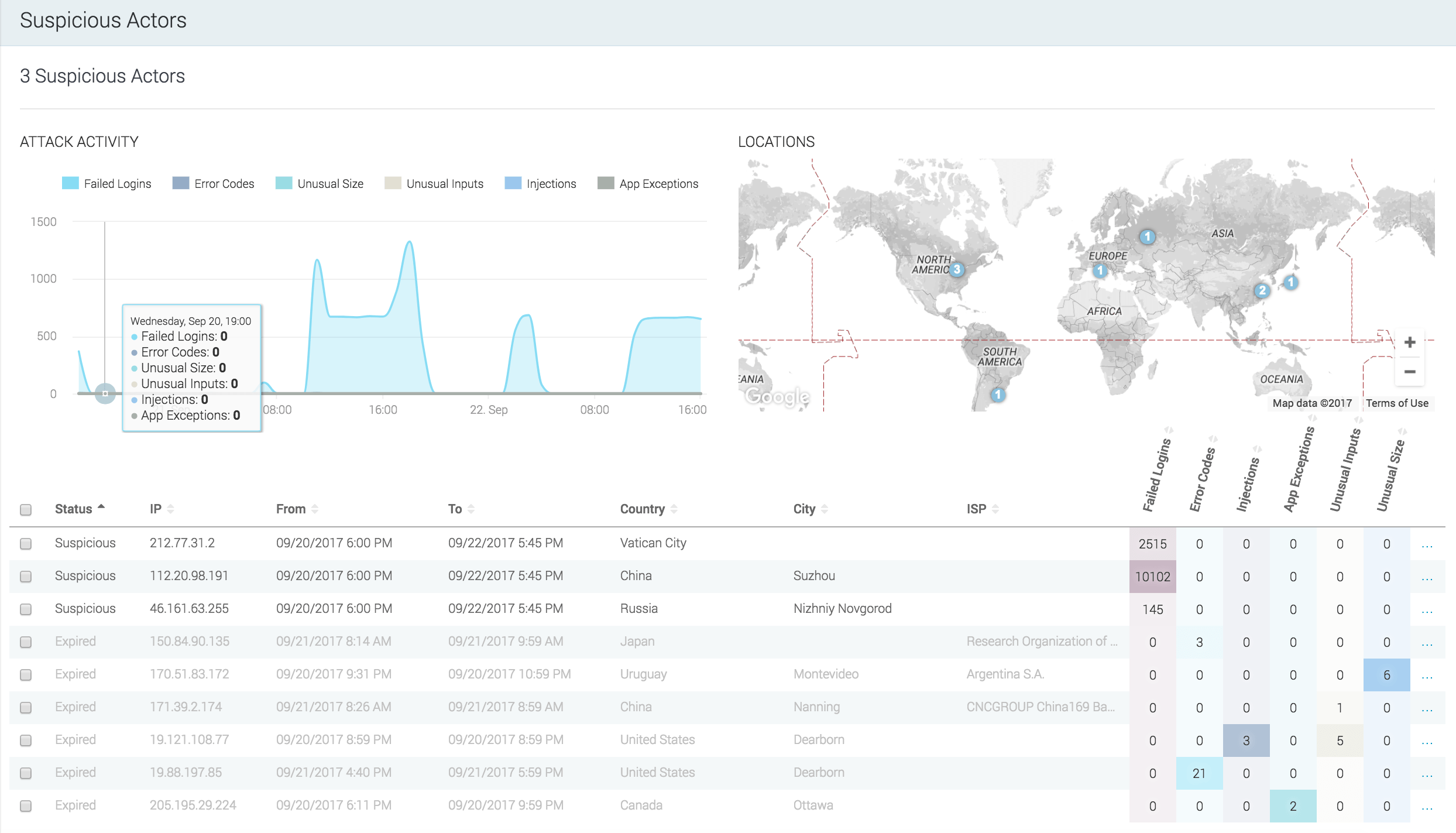
Once Suspicious Actors have been identified, tCell can block them. There are two different blocking modes available. You can configure tCell to block all of the activity or just the suspicious activity coming from the malicious actor’s IP. Blocking just the suspicious activity is advantageous for many organizations because it lowers the risk of potentially blocking good users coming from that same IP. This is important, as shared IP scenarios, such as wifi hotspots and IPv6 to IPv4 NAT, have become very common. To enable blocking of Suspicious Actors, in the tCell console, go to Policies > Suspicious Actors and select the type of blocking you would like under Automatic blocking of Suspicious Actors. Note: Enable IP blocking must be checked for Suspicious Actor blocking to work.
Some more reading: OWASP’s SQL Injection Prevention Cheat Sheet