Objective: Prioritize Fixes
Having run your first scan, you can now review the findings discovered by your scan. The vulnerabilities found are aspects of your app that can make it susceptible to attackers. Within each organization, app, and scan-level vulnerability you can view information about the vulnerability to help you prioritize what to fix first.
View vulnerabilities
There are three ways to check your vulnerabilities - at the Organization level, the App level, or the Scan level. View your vulnerabilities on the Apps page, Scans page, and Vulnerabilities page. Additionally, you can view live scan results in the Live Vulnerability View on the Scan Results page.
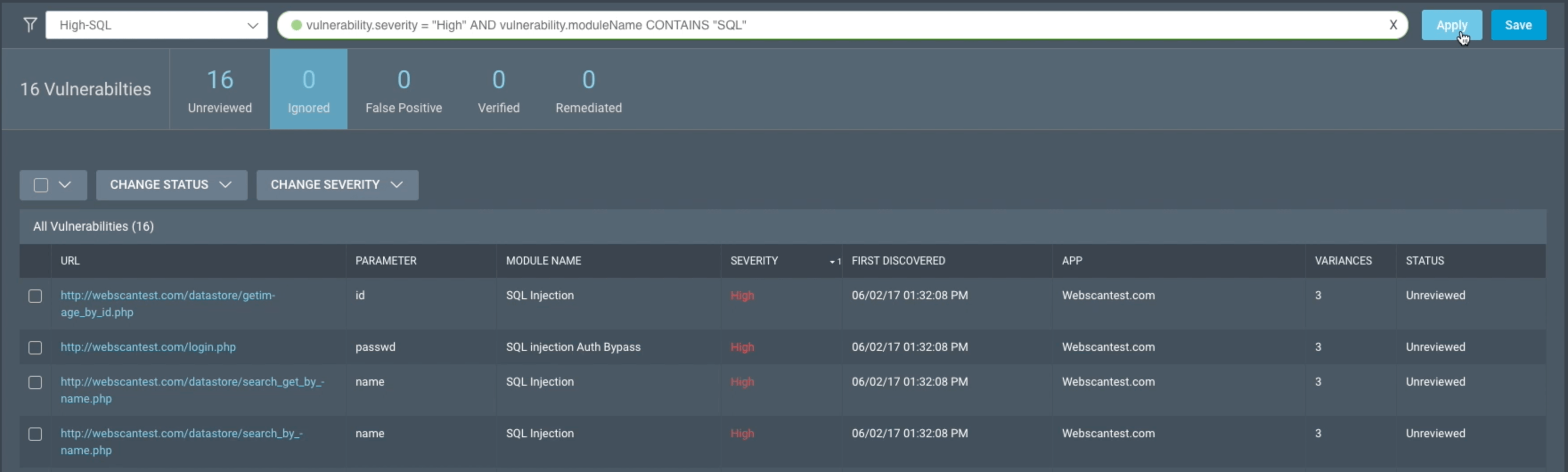
Filter vulnerabilities
Now that you’ve found the vulnerabilities list at the level you want, you can use filters to sort based on your needs. Filtering helps you find vulnerabilities based on your criteria. You can use our pre-built quick filters or create and save your own filters.
Prioritize vulnerabilities
Clicking on any vulnerability will open a panel with details that help you prioritize fixes.
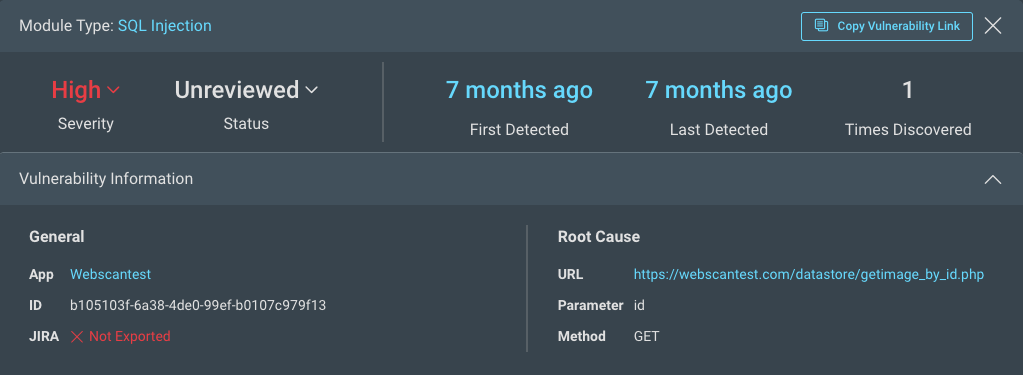
Each vulnerability provides general details about the following:
- Module Type - The name of the attack used, for example SQL Injection.
- Severity - The severity assigned to this type of vulnerability, which can either be the default module severity or the selected severity from a custom attack module. Depending on your level of access, you can also change the severity and status of the vulnerability in this area. Vulnerability status
- Detection - When the vulnerability was first and most recently discovered, as well as how many times it was detected.
- General information - A link to the app where the vulnerability was found, a unique hexadecimal ID for the instance, and an indicator of whether this instance of the vulnerability was exported to Jira.
- Root cause - The URL of the web resource where the vulnerability was found and the HTTP request parameter and method that was used for the attack such as the affected URL, HTTP Method (GET or POST), attack type, and attack value. You can also compare the response of a normal request against a malicious request to your app.
You can adjust the severity, change the status, identify false positives, and much more. For more information on utilizing each detail to help you prioritize, see Review Vulnerabilities.
Severity Levels
We assign different levels of severity, which can either be the default module severity or the selected severity from a custom attack module.
-
High - These vulnerabilities may lead to attackers gaining complete control of the application as well as its data, trust, privacy, and/or availability. Immediate action is recommended to prevent a potentially catastrophic attack, as high severity vulnerabilities are often exploited by automated tools that do not depend upon user interaction.
-
Medium - These vulnerabilities may lead to attackers gaining partial control of the application as well as its data, trust, privacy, and/or availability. Deficiencies and errors in the application configuration are typically how these vulnerabilities are exploited. Although these types of attack require more effort and skill from the attacker, a successful breach can still have a major negative impact.
-
Low - These vulnerabilities may lead to attackers gaining intelligence in preparation for an attack. For these attacks to be successful, several areas of vulnerability such as user error, poor authentication methods, and related vulnerabilities need to be aligned. Any data collected may seem harmless but could be used to facilitate a larger attack.
-
Info - These findings are simply the information we discovered about the application components and configuration. This data could be potentially useful to an attacker collecting information but has no direct impact on vulnerability exploitation.
What’s Next?
After you’ve prioritized vulnerabilities, you can share your results with stakeholders.