Show progress with reports
Generate, share, and download app-level and scan-level reports to share your progress with stakeholders.
Which report should I generate?
| Report | Description |
|---|---|
| Application Security (InsightAppSec) Applications (Apps) Executive Report | Executive data on all the apps scanned by Application Security (InsightAppSec) for a selected calendar month. Use this report to show a CISO or other executives the monthly progress you are making with your application security program, or highlight areas you may need to make greater investments in. |
| Application Security (InsightAppSec) and Vulnerability Management (InsightVM) | Executive data on the apps and assets scanned by Application Security (InsightAppSec) and Vulnerability Management (InsightVM) for a selected calendar month. Vulnerability management has many facets and, with this report, you can give your CISO or other executives a holistic view of your vulnerability management program. |
| Application Security (InsightAppSec) (App) Executive Report | Executive data for an individual app scanned by Application Security (InsightAppSec) for a selected date range. |
| Vulnerabilities Summary Report | Basic or detailed vulnerability data on a scan run for a specific application. Scan managers can use the Vulnerabilities Summary Report to get quick yet detailed insights into the most recent scan or particular scan they’re reporting on. This report could also benefit engineering team managers planning for resource allocation, and identifying issues that need to be addressed. |
| Vulnerabilities with Remediation Report | This report provides vulnerability data on a scan by Application Security (InsightAppSec) for a specific application along with remediation recommendations. |
| Scan compliance reports | You can use the scan compliance reports to advise on your compliance with specific regulations. These reports allow you to see how the results of a scan compare with the regulations your organization must comply with. |
Application Security (InsightAppSec) reports are advisory only
If a report shows no vulnerabilities, or low severity or safe vulnerabilities, this should not necessarily be taken as affirmation of compliance.
Create a report for one or more apps
You can generate executive-level reports containing data on all of your apps from the Apps page and for an individual app from within the app.
Generate a report for multiple apps
- Click Apps in the left navigation menu.
- Click Generate Report.
- From the Generate Executive Report screen, enter a Report Name and select a calendar month. The report pulls in data for completed calendar months only, so you have to wait until the beginning of the next month to generate the report. It may take up to 7 days from the start of each month for the previous month’s data to become available.
- In Report Types, select one of the following:
- Application Security (InsightAppSec) All App Executive Report
- Combined Application Security (InsightAppSec) and Vulnerability Management (InsightVM) Executive Report
- Click Generate Report.
Generate a report for one app
- Click Apps in the left navigation menu.
- Select an app from the Apps vulnerability table.
- Click Generate Report.
- On the Generate Report screen, enter a Report Name and select a date range.
- Select Executive Report under Report Types.
- Select a Format Type (PDF or HTML).
- Click Generate Report.
Create a scan-level report to view vulnerabilities
You can generate scan-level reports with vulnerability or compliance-related information from within an individual scan.
Generate an Application Security (InsightAppSec) scan level report
- Click Scans in the left navigation menu.
- Select a scan from the scan-level vulnerability table. You can also select scans from within an App.
- Click Generate Report.
- From the Generate Report screen, enter a Report Name and select a Report Type.
- Select a scan report.
- Select a Format.
- Click Generate Report.
Filter scan report data
You can add filters to a scan-level report to refine the data before generating the report.
- Go to the Scans page and select a scan.
- Select the filter criteria.
- Click Apply.
- Click Generate Report.
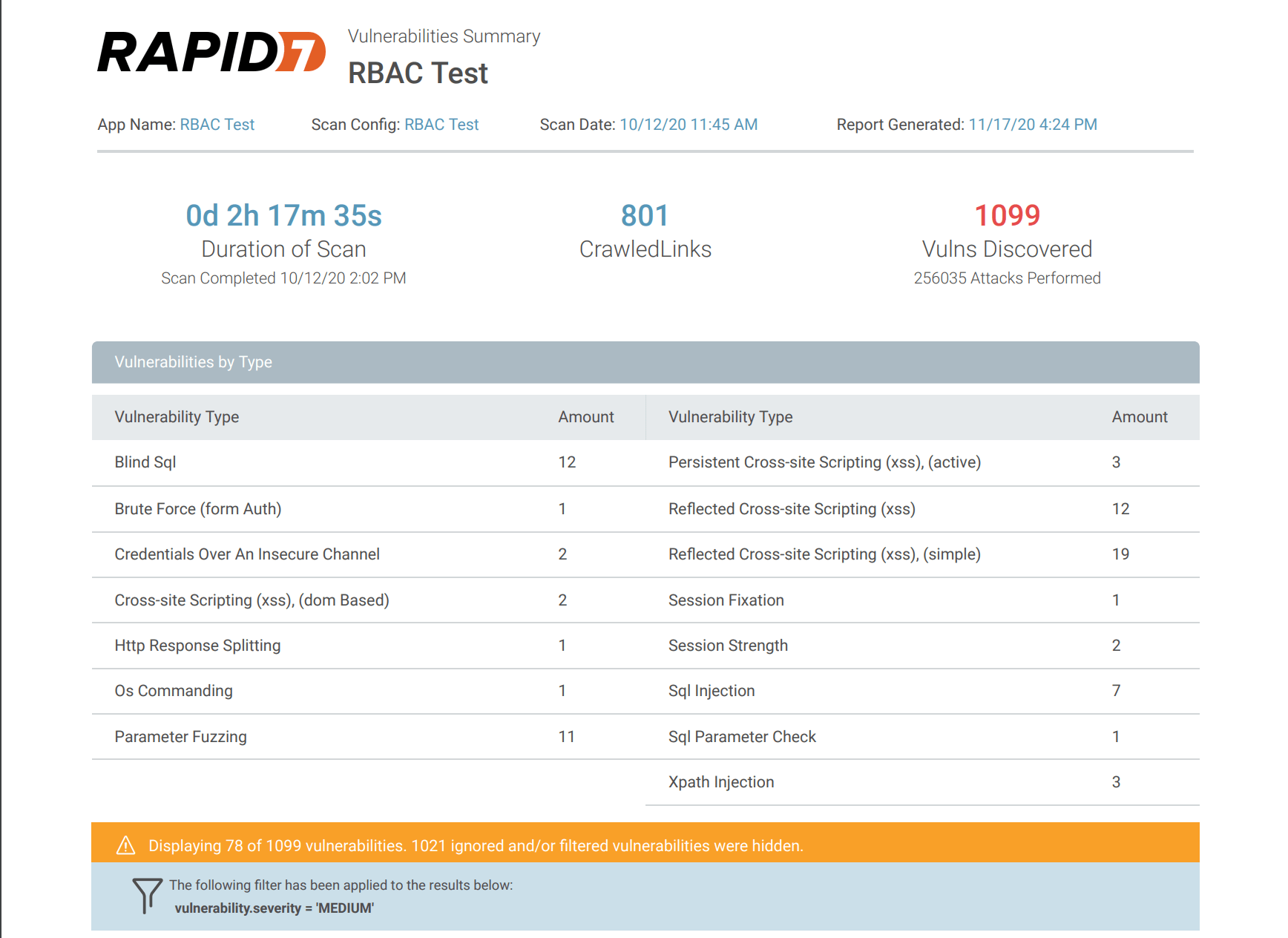
Applied filters are visible in a banner on the Vulnerabilities Summary and the Vulnerabilities with Remediation Report in PDF or HTML format when printed.
Download previously generated reports
You can download reports created across all apps, including previously generated reports, from the Reports page located in the left navigation menu.
Types of reports you can download
You can access all app level reports for the apps that you are assigned, including:
- Single app executive report
- Scan-level vulnerability reports
- Scan-level compliance reports
You can only download the multi-app executive level reports and the combined Application Security (InsightAppSec) Vulnerability Management (InsightVM) all apps reports that you generated.
Download reports
Only reports generated after March 28, 2022 are displayed on the Reports page. Historical reports are not available.
- Click Reports in the left navigation menu.
- Select the report(s) you want to download and click
 .
.
Learn more about reports
App Reports
Application Security (InsightAppSec) Apps Executive Report
This report provides an overview of all apps scanned during a selected month. The report contains the number of apps scanned, unreviewed vulnerabilities, high severity vulnerabilities and remediated vulnerabilities with each of these compared to the previous month. It also shows the top vulnerability types and the vulnerabilities by severity and status.
Combined Application Security (InsightAppSec) and Vulnerability Management (InsightVM) Executive Report
This report provides an overview of the assets and apps scanned by Application Security (InsightAppSec) and InsightVM. The report contains sections relating to your overall vulnerability management programs, including details on apps and assets scanned along with the vulnerabilities found and remediation efforts. Where applicable, it also showcases details on location, owner, and criticality tags.
Vulnerability Reports
Vulnerabilities Summary
The Vulnerabilities Summary is an overview of the vulnerabilities found in the app during the scan. The report is organized by vulnerability and the number of vulnerabilities found during the scan for the app.
Vulnerabilities with Remediation Report
The Vulnerabilities with Remediation report contains all vulnerabilities found in an app from the chosen scan and the recommended remediation. Before making the report, you can use a filter to focus on certain vulnerabilities. Within the report, you can view the attack type, recommendation, and replay the attack using the Rapid7 Chrome Plugin.
Open Worldwide Application Security Project (OWASP) Reports
The OWASP foundation focused on helping organizations build more secure applications. They educate the community about top security risks to web applications along with top remediations. The OWASP Top 10 is a popular reference framework used by developers and web application security teams for guidance on the most critical security risks to web applications.
OWASP 2025 Web Application Report
Still need OWASP 2021 Web Application reports?
If you are still using OWASP’s 2021 Web Application report, you can view details here.
The OWASP 2025 Report identifies their top 10 application security risks for the year. For each risk category, the report shows whether your scan passed or failed and shows web application vulnerabilities for these issues. Each web application vulnerability includes request and response data to support investigation and remediation.
OWASP Top 10 for LLM Applications 2025
Based on scan data, the OWASP Top 10 for LLM applications - 2025 Report shows whether the LLM has passed or failed on each of the top 10 OWASP LLM risks and related attacks. It also shows vulnerabilities within each of the top 10 issues where coverage is provided along with the response and request data for the vulnerability.
OWASP TOP 10 API Security Risks - 2023
Based on scan data, the OWASP Top 10 API Security Risks - 2023 Report shows whether the API passed or failed on each of the top 10 OWASP API security risks and related attacks. It also shows vulnerabilities within each of the top 10 issues along with the response and request data for the vulnerability.
Compliance Reports
Payment Card Industry Report (PCI Report)
The Payment Card Industry report helps you prepare for an audit, an assessment, or a questionnaire around PCI compliance. Uncovering potential issues that will affect the outcome of any of these exercises allows you to take action and secure critical vulnerabilities on any assets that deal with payment card data.
SOX Report
The SOX (Sarbanes-Oxley Compliance) details compliance issues and whether you passed or failed on each, for that particular scan. The report shows each requirement and the details of the vulnerabilities that caused you to fail, if you did.
HIPAA Compliance Results
The HIPAA compliance report shows each requirement, if you passed or failed, and the details of the vulnerabilities that caused you to fail, if you did.
GDPR Report
The GDPR report is an advisory report that shows how vulnerabilities in scanned targets might jeopardize your GDPR compliance and highlights which vulnerabilities need to be addressed.
Mapping OWASP Categories to Attack Modules
LLM Applications
| OWASP top 10 for LLM applications 2025 | Attack Modules |
|---|---|
| LLM01: 2025 Prompt Injection | LLMPromptInjection |
| LLM02: 2025 Sensitive Information Disclosure | LLMSensitiveInformationDisclosure |
| LLM03: 2025 Supply Chain | |
| LLM04: 2025 Data and Model Poisoning | |
| LLM05: 2025 Improper Output Handling | LLMImproperOutputHandling |
| LLM06: 2025 Excessive Agency | |
| LLM07: 2025 System Prompt Leakage | LLMSystemPromptLeakage |
| LLM08: 2025 Vector and Embedding Weaknesses | |
| LLM09: 2025 Misinformation | LLMMisinformation |
| LLM10: 2025 Unbounded Consumption | LLMUnboundedConsumption |
Web Applications
| OWASP 2025 top 10 web application categories | Attack Module |
|---|---|
| A01: Broken Access Control | Anonymous Access Business logic abuse attacks Collecting Sensitive Personal Information Cross Origin Resources Sharing (CORS) Cross-Site Request Forgery (CSRF) Directory Indexing Email Disclosure File Inclusion Forced Browsing FrontPage Checks HTTP User-Agent Check Information Disclosure in response Information Disclosure in scripts Information Leakage in responses Java Grinder Local Storage Usage Predictable Resource Location Privacy Disclosure Privilege Escalation Reverse Proxy Server Configuration Server Side Request Forgery Source Code Disclosure Subdomain discovery Unvalidated Redirect X-Powered-By |
| A02: Security Misconfiguration | ASP.NET Misconfiguration Autocomplete attribute Clients Cross-Domain Policy Files Content Security Policy Header Cookie attributes HTTP Strict Transport Security JavaScript Memory Leaks Web Beacon XML External Entity Attack |
| A03: Software Supply Chain Failures | Apache Struts 2 Framework Checks Apache Struts Detection Heartbleed Check Nginx NULL code Out of Band Log4Shell JNDI Injection (OOB Log4Shell JNDIi) Remote Code Execution |
| A04: Cryptographic Failures | Credentials over an insecure channel HTTPS Downgrade HTTPS Everywhere SSLStrength Sensitive Data Exposure Sensitive data over an insecure channel Session Strength |
| A05: Injection | Blind LDAP Injection Blind NoSQLi Blind SQL Command Injection Cross-site scripting (XSS), (DOM based reflected via AJAX request) Cross-site scripting (XSS), (DOM based) Cross-site tracing (XST) Expression Language Injection HTTP Headers HTTP Response Splitting JSON Injection LDAP Injection LLM Improper Output Handling LLM Misinformation LLM Prompt Injection LLM Sensitive Information Disclosure LLM System Prompt Leakage LLM Unbounded Consumption NoSQLi Injection Out of Band Cross-site scripting (XSS) Out of Band SQL Injection (OOB SQLi) Out of Band Stored Cross-site scripting (XSS) PHP Code Execution Parameter Fuzzing Persistent Cross-site scripting (XSS) (passive) Persistent Cross-site scripting (XSS), (active) Reflected Cross-site scripting (XSS) Reflected Cross-site scripting (XSS), (simple) Reverse Clickjacking SQL Injection SQL Injection Auth Bypass SQL Parameter Check Server Side Include (SSI) Injection Server Side Template Injection Swagger UI XSS Web DAV Flaws Check XPath Injection |
| A06: Insecure Design | ASP.NET ViewState security Arbitrary File Upload Browser Cache directive (leaking sensitive information) Credentials stored in clear text in a cookie HTTP Query Session Check HTTP Verb Tampering URL rewriting Web Service Parameter Fuzzing X-Content-Type-Options X-Frame-Options X-XSS-Protection |
| A07 Authentication Failures | Brute Force (Form Auth) Brute Force (HTTP Auth) Form Session Strength HTTP Authentication over insecure channel Information Disclosure in comments JSON Web Token Session Fixation Session Upgrade Swagger UI (DOM based) |
| A08: Software and Data Integrity Failures | ASP.NET Serialization Secure and non-secure content mix Subresource Integrity |
| A09: Logging and Alerting Failures | - |
| A10: Mishandling of Exceptional Conditions | .NET Specific Exception (Information Leakage in responses)* ASP Server.Execute Error (Information Leakage in responses)* CFM error statement that prints full file path (Information Leakage in responses)* CFM error that indicates file could not be opened from a parameter value (Information Leakage in responses)* CFM error that indicates file could not be opened from a parameter value, but the file probably exists (Information Leakage in responses)* Error produced within a Perl module (Foo.pm line 123) (Information Leakage in responses)* Generic ASP.NET error (Information Leakage in responses)* Generic CFM error (Information Leakage in responses)* Generic MS VBScript error (Information Leakage in responses)* Information Leakage .NET Stack Trace (Information Leakage in responses)* JHTML error that indicates file could not be opened from a parameter value (Information Leakage in responses)* Lotus Notes error (Information Leakage in responses)* MS VBScript “File not found”, ASP Include file not found (Information Leakage in responses)* PHP error that indicates a php source file could be opened from a parameter value, but doing so “stomps” on previously defined variables (Information Leakage in responses)* PHP error that indicates file could not be opened from a parameter value (open_basedir) (Information Leakage in responses)* PHP error that indicates file could not be opened from a parameter value (scanner) (Information Leakage in responses)* PHP error that indicates file could not be opened from a parameter value (stream) (Information Leakage in responses)* PHP include statement found in error strings (Information Leakage in responses)* SQL Information Leakage Verbose ASP.NET error (Information Leakage in responses)* mkdir() failure (Information Leakage in responses)* * - An individual Attack Variance from “Information Leakage in responses” has been mapped to this category |
APIs
| OWASP 2023 top 10 categories | Attack Module |
|---|---|
| API1: 2023-Broken object level authorization | LogicAttack |
| API2: 2023-Broken authentication | BruteForce HTTPAuth SessionFixation SessionStrength SessionUpgrade |
| API3: 2023-Broken object property level authorization | EmailCheck InformationDisclosure InformationLeakage PrivacyDisclosure Server Configuration SQLErrors XPoweredByHeader |
| API4: 2023-Unrestricted resource consumption | |
| API5: 2023-Broken function level authorization | AnonymousAccess Arbitrary File Upload Cross Origin Resources Sharing (CORS) CSRF Forced Browsing HTTPS Downgrade |
| API6: 2023-Unrestricted Access to Sensitive Business Flows | ServerSideRequestForgery |
| API7: 2023-Server side request forgery | CookieAttributes HTTPHeaders HTTPSEverywhere SSLStrength Unvalidated Redirect X-Content-Type-Options |
| API8: 2023-Security misconfiguration | |
| API9: 2023-Improper inventory management | |
| API10: 2023-Unsafe consumption of APIs | ASP.NET Serialization BLDAPInjection BSQLInjection ExpressionLanguageInjection LDAPInjection NoSQLInjection Blind NoSQLInjection OSCommanding OutOfBandLog4ShellJNDIInjection Out of Band Cross-site scripting (XSS) Out of Band Stored Cross-site scripting (XSS) Out of Band SQL Injection (OOB SQLi) ParameterTampering SQLInjection SQLInjection_Auth SQL Information Leakage SqlParameter SQL Parameter Check XMLExternalEntity XPathInjection XSS_Persistent |
OWASP 2021 Web Application report
OWASP 2021 Web Application Report
2025 Web Application report now available
For the most up-to-date version of this information, view the 2025 Web Application report.
The OWASP 2021 Report shows the top 10 risks in 2021 that OWASP determined. The report shows whether you passed or failed on each OWASP Top 10-based attack for the scan. It also shows vulnerabilities within each of the top 10 issues along with the response and request data for the vulnerability.
The Log4Shell attack is not included in our OWASP Top 10 2021 attack
Although the Log4Shell Out of Band (OOB) attack is listed in the OWASP Top Ten of 2021, we exclude this attack in the OWASP 2021 attack template for efficiency.
The OOB Injection for Log4j attack significantly extends scan times, so we kept it separate from the OWASP Top 10 and All Modules attack templates. To scan specifically for Log4shell, use the Out of Band Injection for Log4j attack.
| OWASP 2021 top 10 web application categories | Attack Module |
|---|---|
| A01: Broken Access Control | Anonymous Access Business logic abuse attacks Cross Origin Resources Sharing (CORS) Cross-Site Request Forgery (CSRF) Directory Indexing Email Disclosure File Inclusion Forced Browsing Information Disclosure in response Information Disclosure in scripts Information Leakage in responses Java Grinder Local Storage Usage Predictable Resource Location Privacy Disclosure Privilege Escalation Server Configuration Source Code Disclosure Unvalidated Redirect X-Powered-By |
| A02: Cryptographic Failures | Credentials over an insecure channel HTTPS Downgrade HTTPS Everywhere Sensitive Data Exposure Sensitive data over an insecure channel Session Strength |
| A03: Injection | Blind LDAP Injection Blind NoSQLi Blind SQL Command Injection Cross-site scripting (XSS), (DOM based reflected via AJAX request) Cross-site scripting (XSS), (DOM based) Cross-site tracing (XST) Expression Language Injection HTTP Response Splitting JSON Injection LDAP Injection LLM Improper Output Handling LLM Misinformation LLM Prompt Injection LLM Sensitive Information Disclosure LLM System Prompt Leakage LLM Unbounded Consumption NoSQLi Injection Out of Band Cross-site scripting (XSS) Out of Band SQL Injection (OOB SQLi) Out of Band Stored Cross-site scripting (XSS) Parameter Fuzzing Persistent Cross-site scripting (XSS) (passive) Persistent Cross-site scripting (XSS), (active) PHP Code Execution Reflected Cross-site scripting (XSS) Reflected Cross-site scripting (XSS), (simple) Server Side Include (SSI) Injection Server Side Template Injection SQL Injection SQL Injection Auth Bypass SQL Parameter Check Swagger UI XSS XPath Injection |
| A04: Insecure Design Failures | Arbitrary File Upload ASP.NET ViewState security Browser Cache directive (leaking sensitive information) Credentials stored in clear text in a cookie HTTP Query Session Check SQL Information Leakage URL rewriting |
| A05: Security Misconfiguration | ASP.NET Misconfiguration Autocomplete attribute Clients Cross-Domain Policy Files Content Security Policy Header Cookie attributes FrontPage Checks HTTP Strict Transport Security Web Beacon XML External Entity Attack |
| A06: Vulnerable and Outdated Components | Apache Struts 2 Framework Checks Apache Struts Detection Heartbleed Check Nginx NULL code Out of Band Log4Shell JNDI Injection (OOB Log4Shell JNDIi) Remote Code Execution |
| A07: Identification and Authentication Failures | Brute Force (Form Auth) Brute Force (HTTP Auth) Form Session Strength HTTP Authentication over insecure channel Information Disclosure in comments JSON Web Token Session Fixation Session Upgrade |
| A08: Software and Data Integrity Failures | ASP.NET Serialization Secure and non-secure content mix Subresource Integrity |
| A09: Security and Logging Failures | - |
| A10: Server-Side Request Forgery (SSRF) | Reverse Proxy Server Side Request Forgery |