This product is no longer sold. We no longer update these help pages, so some information may be out of date.
Alert Settings
When you configure a basic detection rule, there are several different settings to consider in order to receive the optimum and most efficient alerts.
Trigger Notification Settings
For Log Pattern Detection Rules, an alert triggers every time the event occurs on a rolling basis by default. If you choose Custom Match Settings, you can specify how many times an event must occur within a given time frame before it can trigger an alert.
For example, if the pattern match threshold is 100 times in the throttle window of 60 minutes, 100 alerts must occur within the next hour before you receive the first alert. Similarly, 100 more alerts must occur in the same hour before you receive a second alert.
Note that when the pattern is matched, an alert will be triggered. However, if that pattern is continually matched above the Match threshold, you will not get any further alerts until it falls below the threshold that you’ve set. If you want to be alerted on every time the pattern occurs, set the alert to Match Once.
For Log Change Detection Rules, new queries require that you specify a calculation to use, and a key to apply the calculation. Any changes of the key based off of the calculation will trigger an alert.
Notification Settings
For Log Change Detection and Log Inactivity Detection Rules, define one or more communication methods. You can choose PagerDuty, Slack, Webhook, and email. Select existing recipients or create new ones and provide the appropriate details for the communication method.
If you are using email, select existing recipients from the dropdown or create new ones. Use commas to separate email addresses if you are sending to multiple recipients. See Third Party Integrations for more information.
Define what log information you’d like included in your notifications. By default, the matching log line and context will be included. To change this, open the Edit a Basic Detection Rule modal, click Alert Notifications > Notification(email/integrations) and select the communication method tab you’d like to edit:
- Email: Click the Recipients drop-down and select Add & select recipient. Click the Log Context drop-down to view options.
- PagerDuty: Click the Service key for Pagerduty account drop-down and select Add & select key. Click the Log Context drop-down to view options.
- Slack: Click the Slack webhook URL drop-down and select Add & select webhook. Click the Log Context drop-down to view options.
- Webhook: Click the Webhook URL and select Add & select webhook. Click the Log Context drop-down to view options.
- Automation (InsightConnect) Workflow: Click the Automation (InsightConnect) Workflow drop-down and select Add & select Automation (InsightConnect) workflow. Tick the ‘Send Log Line’ box if you wish for Log Line information to be included in your notifications.
Alternatively, you can also select Manage Alerts > Labels & Notifications > Notification Target to define the log information you’d like to be included.
For Log Pattern Detection Rules, use labels to identify the logs in your notifications. You can create a new label, or use an existing one by searching for labels, filtering by severity, or sorting them alphabetically.
Create New Email Recipients
When you using email to send alerts to your team, you can create a new email recipient.
- From the “Recipients” dropdown, click on Add & select recipient.
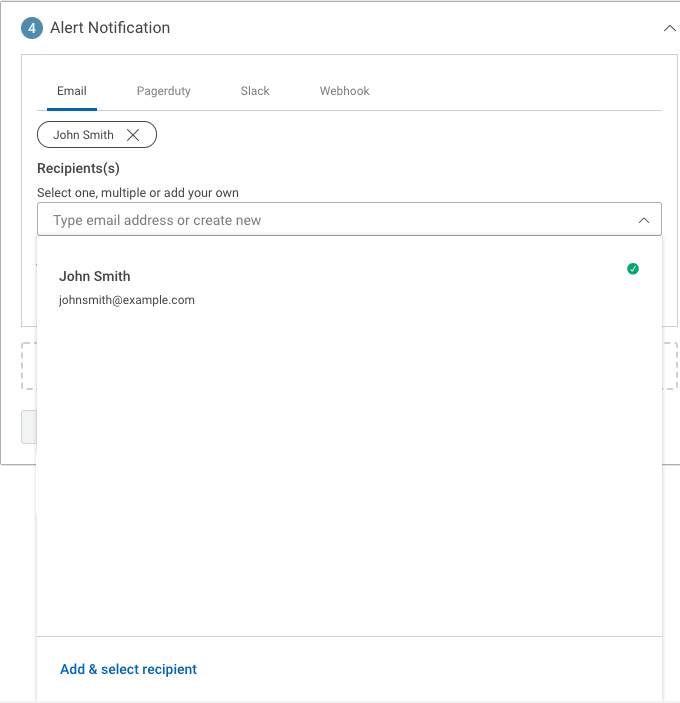
- Name the recipient, and then enter one or more email addresses separated by commas.
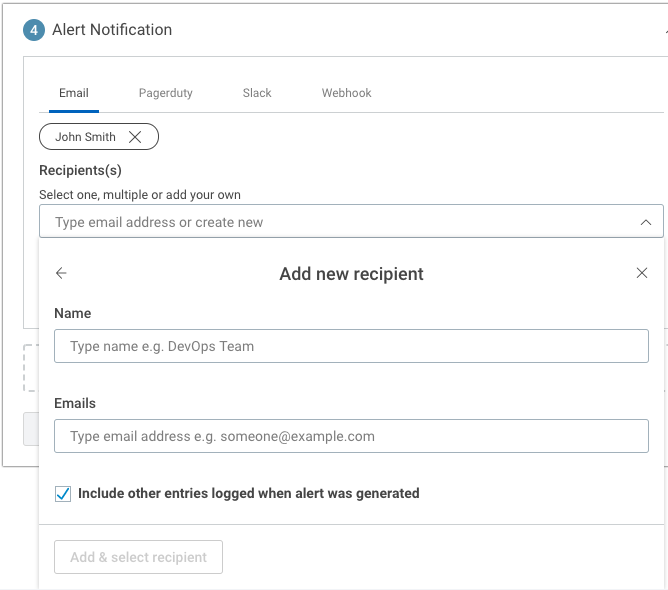
- Optionally check the box to include other entries logged when the alert was generated.
- Click the Add & select recipient button.
The new email will populate the Recipients field.