Conducting a Basic Test Manually Against Hackazon
To perform manual vulnerability assessment requires a browser and a proxy tool. ZAP proxy is such a tool that commonly used in security testing arena. JRE is required to install and setup both these tools. Burpsuite, ZAP Proxy and JRE can downloaded from the following links:
- ZAP Proxy: https://www.owasp.org/index.php/OWASP_Zed_Attack_Proxy_Project
- JRE: http://www.oracle.com/technetwork/java/javase/downloads/jre8-downloads-2133155.html
ZAP proxy requires minimal configuration to setup. Sites tab shows the the tree map of the application. Enable “Set Break” as shown to intercept HTTP request and response when modification is needed after it leaves the browser.
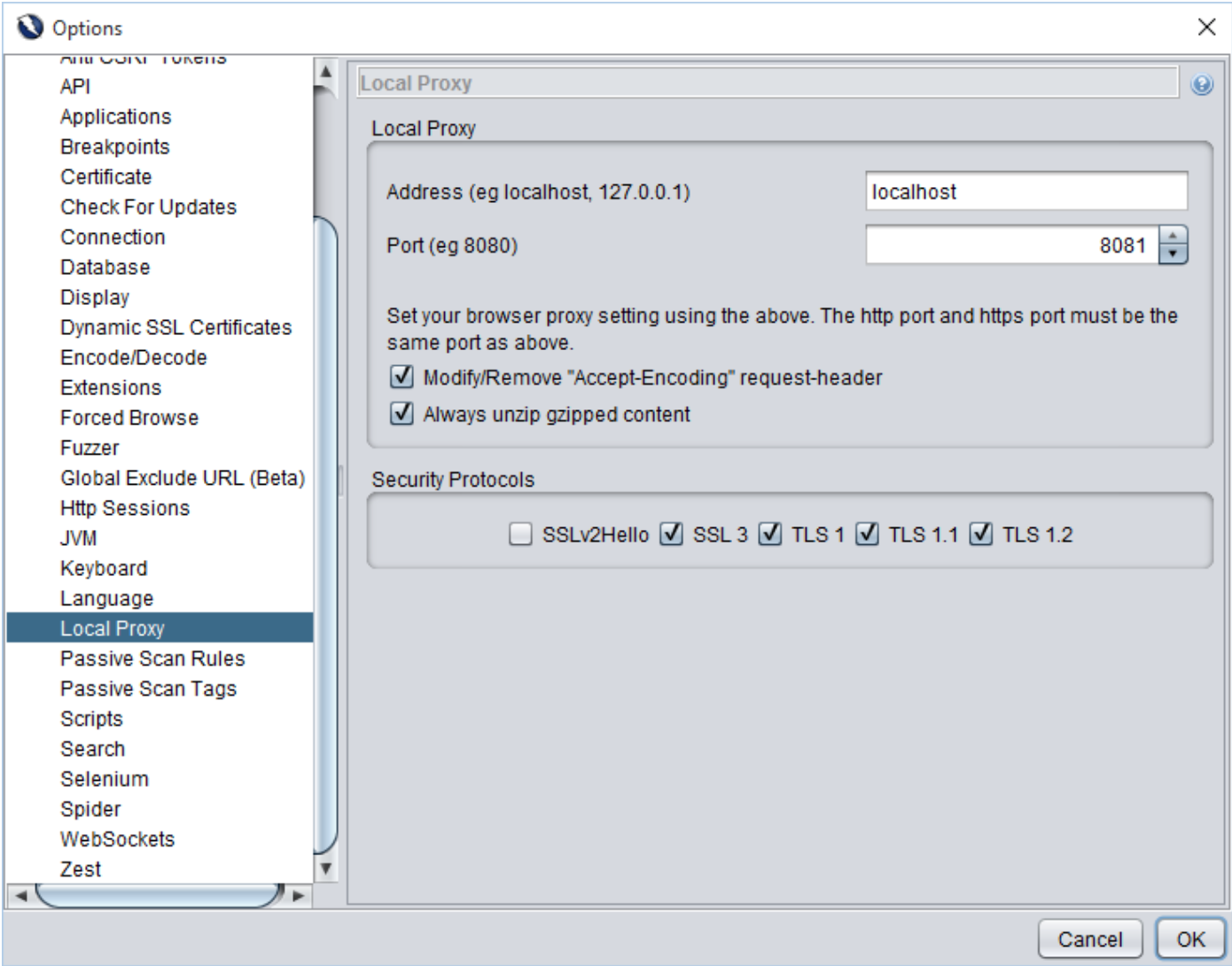
In addition to that, Ports can be bind by applying port number in “Options” >> “Local Proxy”
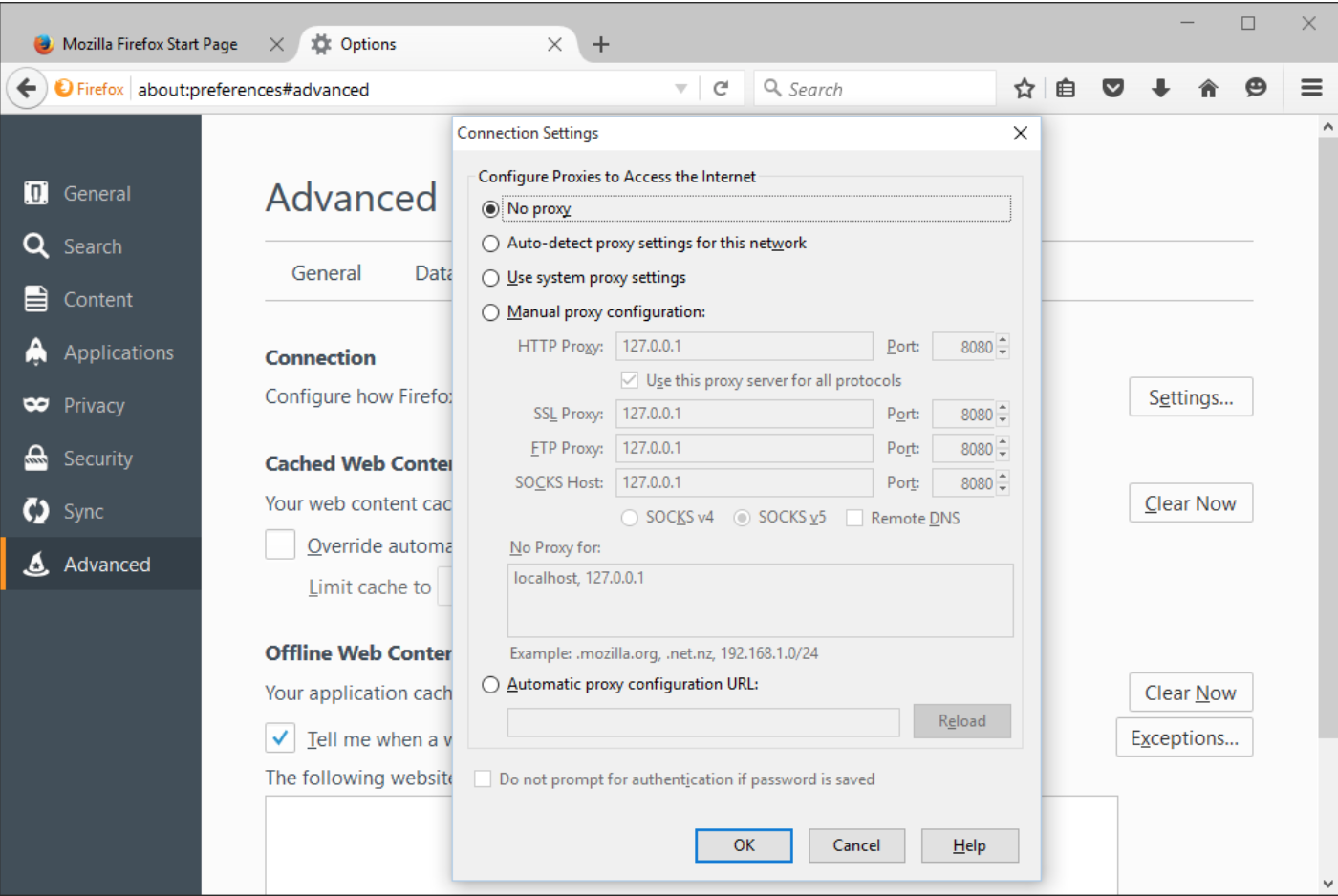
Furthermore, browser must be configured to use the web proxy. This can be done within Mozilla Firefox via “Options” >> “Advanced” >> “Network” >> “Settings” configuration window. To test the proxy open http://localhost in the browser.
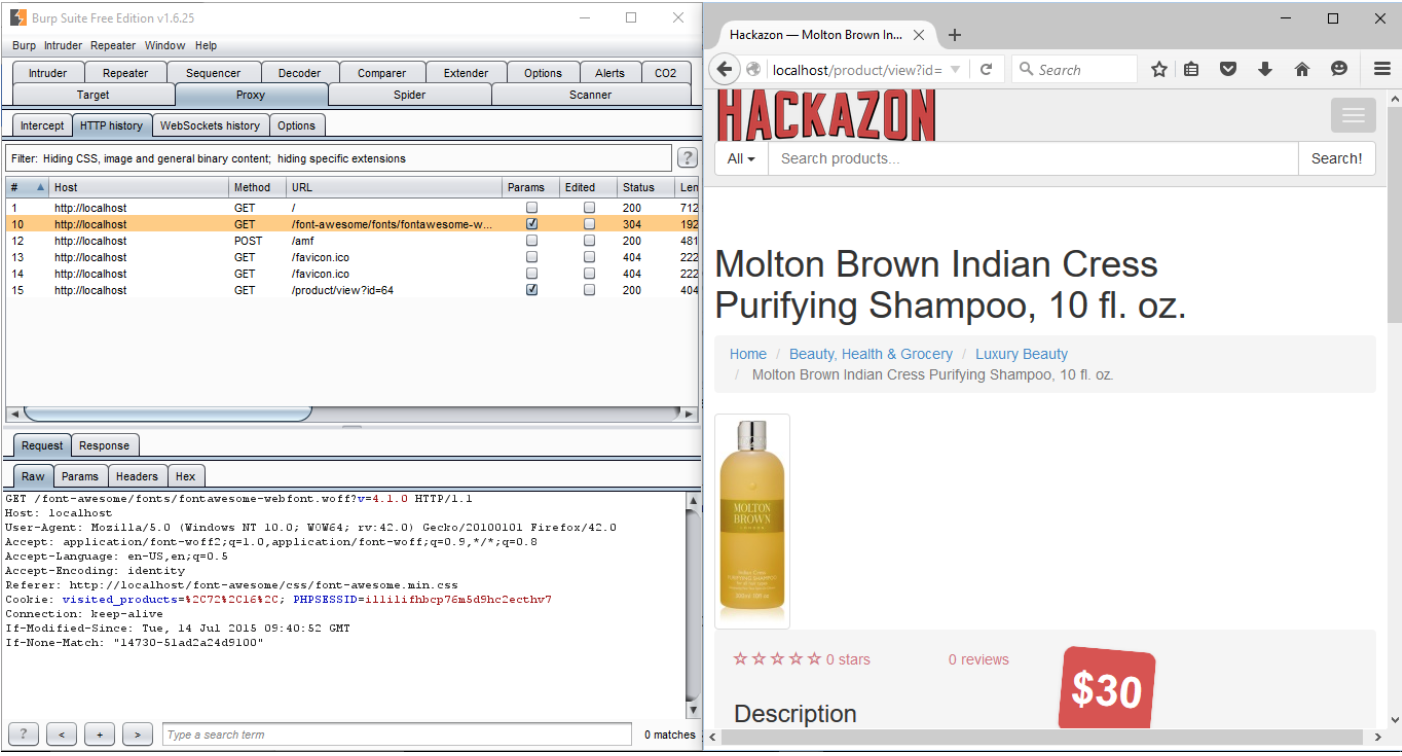
All traffic from the web browser will route through burp proxy tool. Request and response can be intercepted and modified using proxy tool. Thus, using proxy tool and browser, manually test can be performed on Hackazon.
How to find vulnerabilities from Hackazon application
Cross Site Scripting
URL: http://192.168.1.108/search?id=&searchString=NBA
Parameter name: searchString
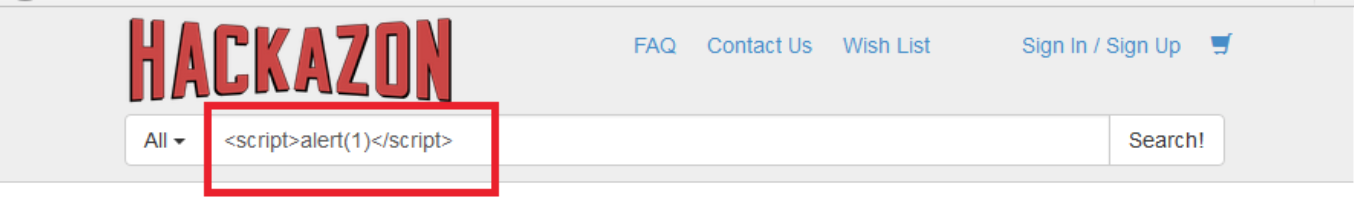
Attack value: <script>alert(1)</script>
The following screenshot displays search functionality of the application. For example, we searched for “NBA” keyword and application search result based on user input.

Enter a malicious script in the “Search” field.
Javascript injected into the code is executed.

OSCommand injection
URL: http://192.168.1.108/account/documents?page=delivery.html
Parameter name: page
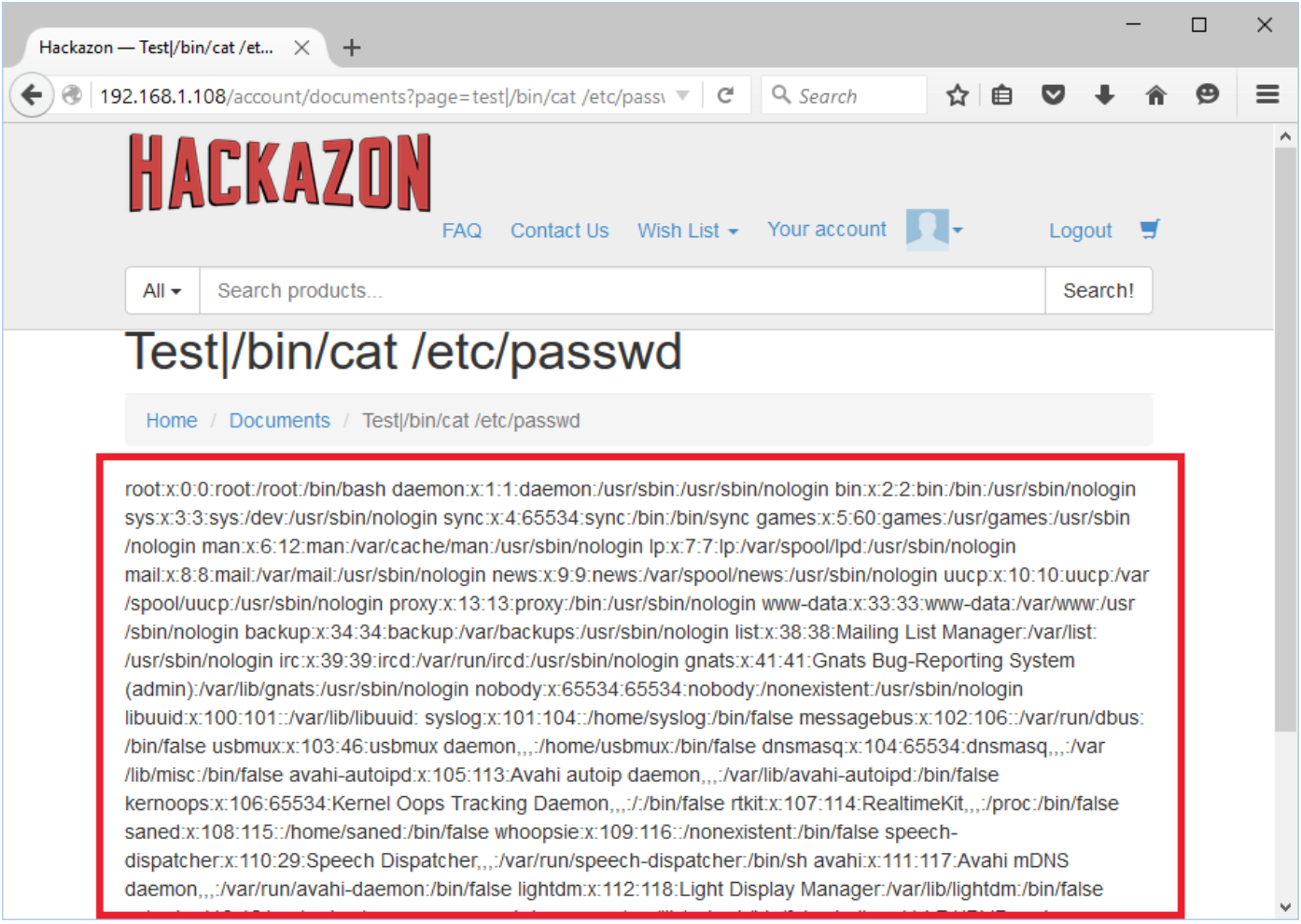
Attack value: test|/bin/cat /etc/passwd
The following demonstrates the read document functionality of the application.

We have injected a system command to to read a /etc/passwd system file.
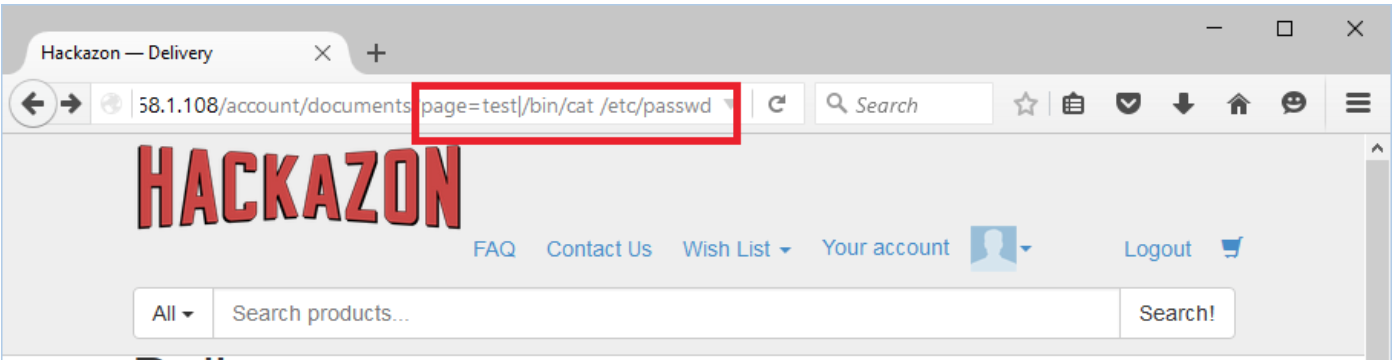
Application has executed a system command and shown a system file to end user.
Unvalidated Redirect
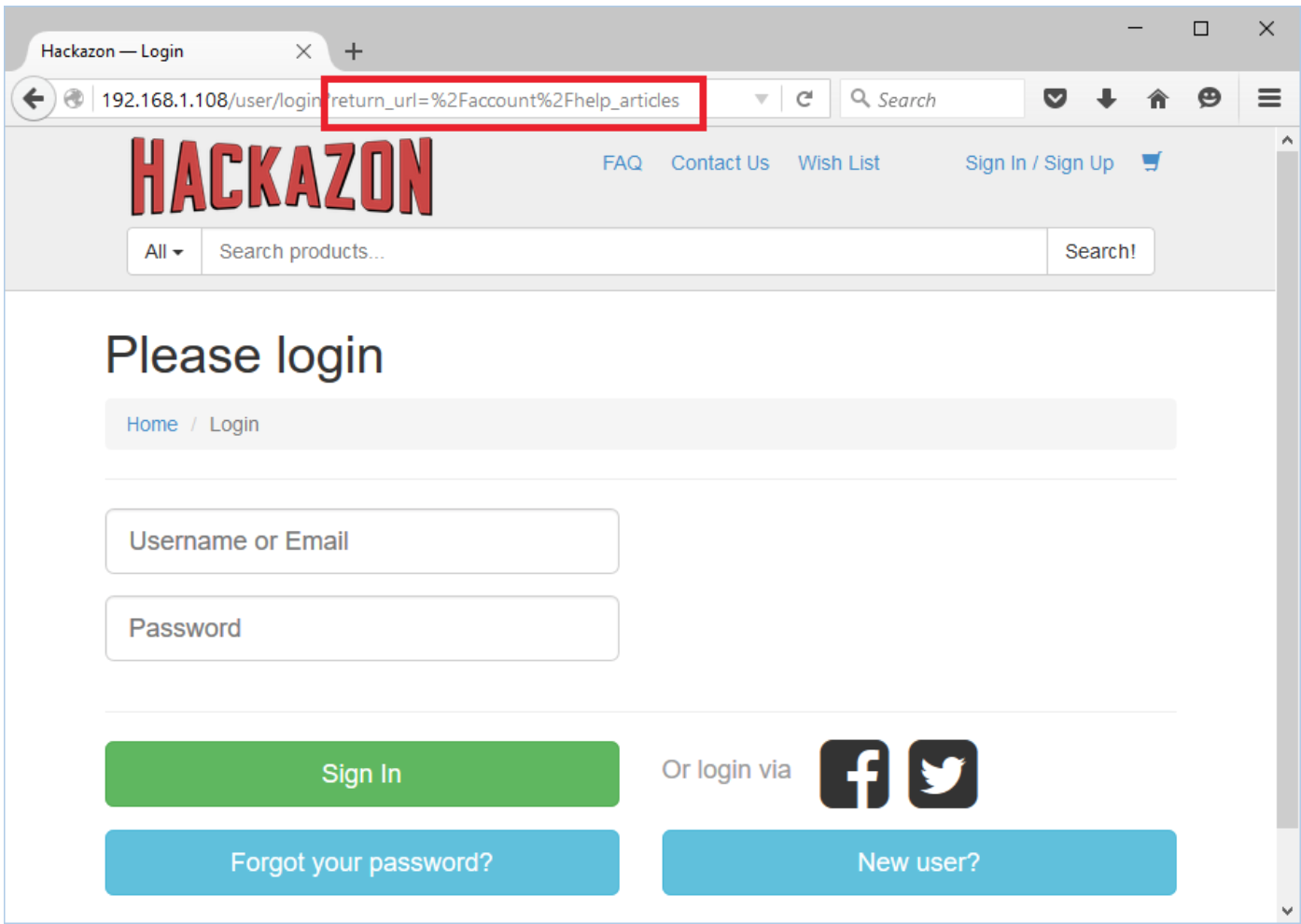
URL: http://192.168.1.108/user/login?return_url=%2Faccount%2Fhelp_articles
Parameter name: return_url
Attack value: http://www.google.com
Hackazon application has functionality to redirect to an internal application page after a login. The application will redirect to a help_artical page after successful login.
Replace the “return_url” parameter value from “/account/help_articles” to “http://www.google.com” and login into the application.
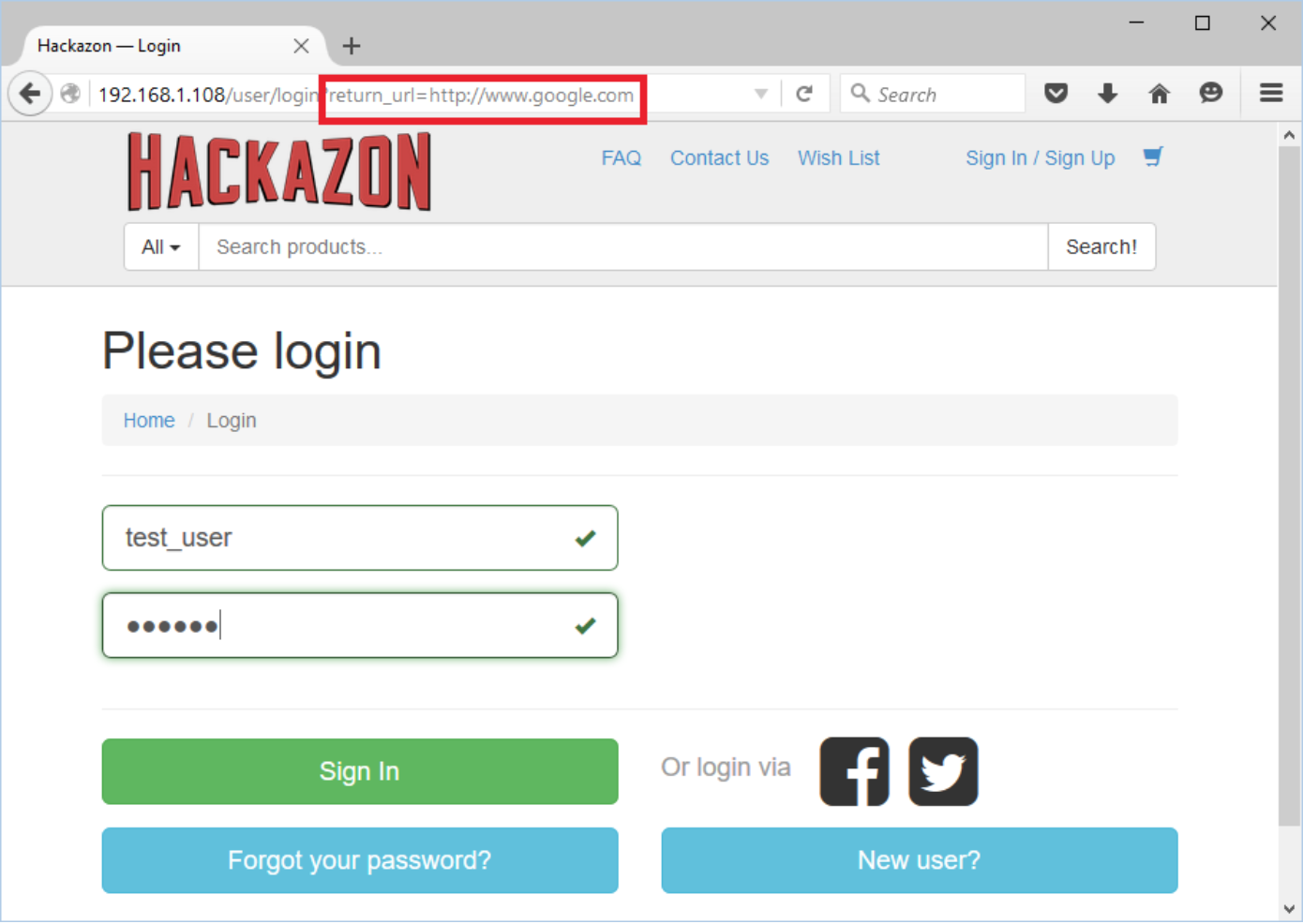
Application allows user to redirect without any validation. This vulnerability is used in phishing attacks to get users to visit malicious sites without realizing it.