F5 BIG-IP Application Security Manager (ASM) Integration
Web Application Firewalls (WAFs) are critical in the implementation of a robust application security strategy. Ideally placed to break the upstream web stream of web servers (in Reverse-Proxy), WAFs can analyze the contents of HTTP requests and responses to a new level of granularity with respect to an IPS or IDS. Their effectiveness is often measured by their ability to block illegitimate requests without impacting regular traffic. The challenge then lies in the definition of a WAF security policy that will aim to maximize the number of blocked attacks, while limiting the rate of false positives (blocked regular application) and false negatives (dangerous requests allowed).
The fear of the business impact of false positives tends to paralyze security teams. Imagine an e-commerce site that would see its orders fall because the checkout fails validation since the recipient’s address contains “special” characters such as an apostrophe. The business impact often takes priority over security, the result being that too often the WAF is used in non-blocking mode or with a default set of rules, or just not optimized for the application that it must protect. These rules are likely to miss some attacks on the application layer.
If short, iterative cycles of development of web applications like Agile are popular with DevOps, and in line with the needs of businesses eager for new features quickly deployed into production, they represent a challenge for security teams, who are struggling to update the security policies of WAFs to the frequency dictated by the new releases of the application.
The integration of a dynamic web application testing solution, DAST (Dynamic Application Security Testing), and a WAF helps address these challenges by implementing an industrialized process of Virtual Patching: The scanner identifies web vulnerabilities that are not covered by the WAF security policy and proposes new rules that are more granular, specifically addressing the identified vulnerabilities. The best practice is to change the source code of the application (including for ensuring the systematic validation of inputs users), but it is a process that requires time, resources, and application expertise, representing an obvious obstacle in the current context of qualified IT resource constraints. Virtual Patching presents an effective temporary preventive measure, deployed in just a few clicks. A “cyber-dressing”, quick and easy to implement on a small digital wound before it turns into bleeding. Using the results of a scan, the Defend module of Rapid7 AppSpider has the ability to generate rules of WAF and IPS at a high level of granularity, in minutes, instead of the days or weeks necessary to change the code or creating WAF rules manually. This allows you to establish an effective process from the identification of a vulnerability in your application to improving the overall level of safety and maximizing the ROI of your WAF.
Overview of Integration Process
- Scan the web application with Rapid7 AppSpider.
- Import the results of the vulnerabilities found into the Defend AppSpider tool within AppSpider Pro to generate custom rules.
- Import Rules into F5 BIG-IP ASM to customize the security policy rules.
- Check that vulnerabilities are patched.
Integration benefits
- Virtual patching of web vulnerabilities discovered by AppSpider
- Greater uptime of web applications by protecting the application until a patch has been issued
- Optimizing WAF rules specifically for known vulnerabilities present in your application
- Minimizing risk exposure by automatically reducing your attack surface
AppSpider Defend
Defend User Interface: On the top level menu next to the Tools section you will find the Defend menu which when clicked will bring up the Defend UI below.
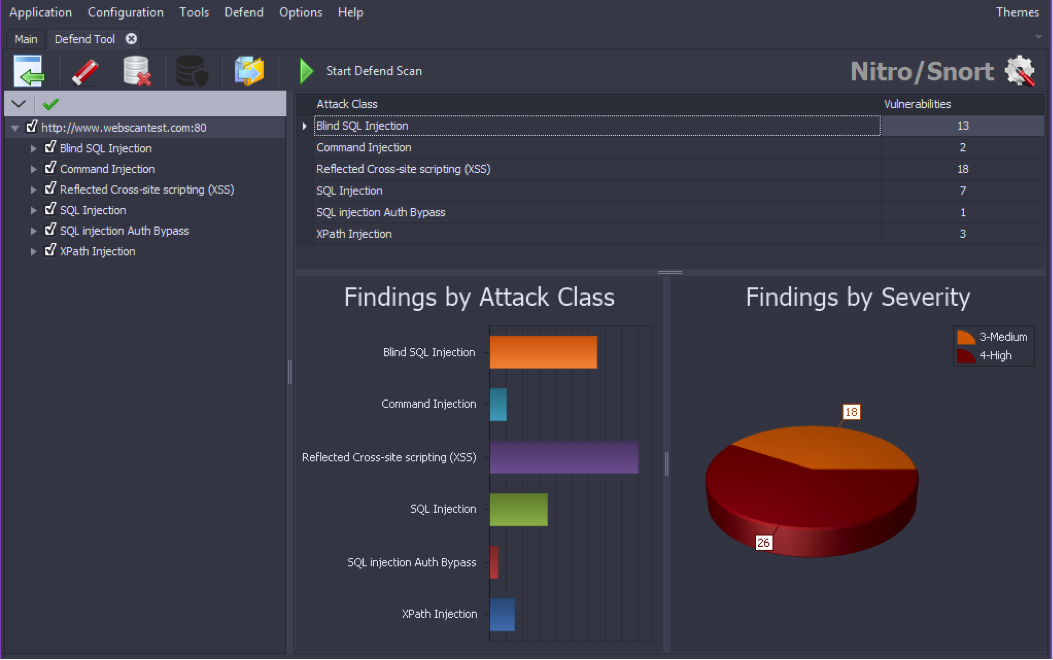
Hovering your cursor over the icons will display a description of what function each icon will accomplish.
- Load Finding
- Clear Findings: removes AppSpider Vulnerabilities Summary data.
- Clear DB: deletes Vulnerabilities and good data.
- Good data UI.
- Export Rules: export custom rules generated by Defend.
- Start Defend Scan: replays attacks to confirm vulnerability is no longer exploitable
- Options: section that opens the UI listed in the next section.
Options UI
The following elements are presented in this Options UI window:
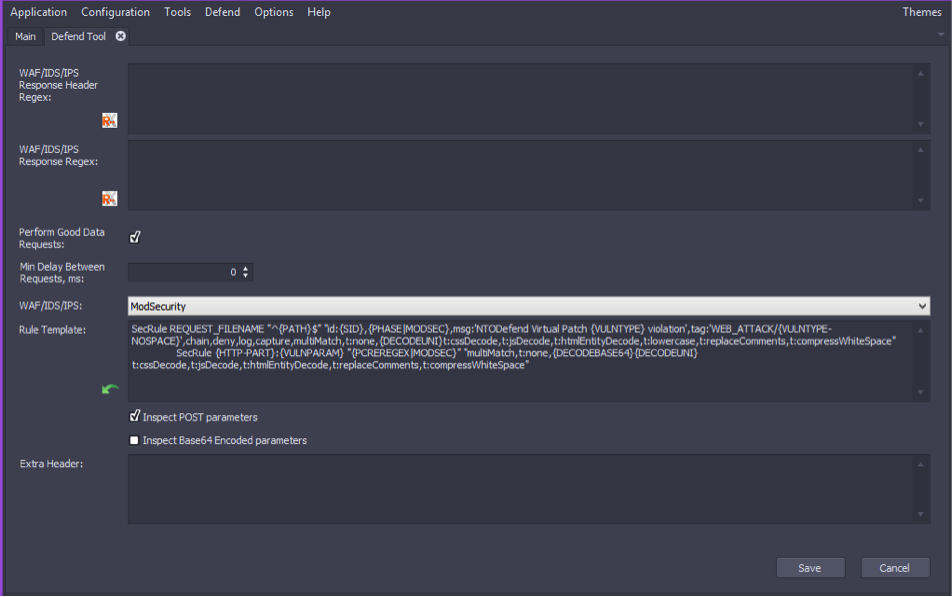
- WAF/IDS/IPS Response Header Regex - Editable field for the regular expression Defend uses to search values in headers.
- Response Regex - editable field for the regular expression Defend uses to search values in responses and exceptions in the processing of responses.
- Perform Good Data Requests - check box is selected by default.
- Min.Delay Between Requests, ms - 0 millisecond delay is predefined.
- WAF/IDS/IPS - select the WAF/IDS/IPS that you want to configure with Defend. The current supported WAF/IDS/IPS’s are the following: ModSecurity, SourceFire/Snort, Nitro/Snort, Imperva, Secui/Snort, Akamai, Barracuda, F5, and DenyAll.
- Rule Template - the set of rules Defend uses with your WAF/IDS/IPS.
- Extra header - append extra headers to requests sent during simple scan.
Generate Filters Use your knowledge of the WAF/IDS/IPS and the application to create custom rules. Load Vulnerabilities Import your desired VulnerabilitySummary generated in AppSpider
- Click on the Load Findings icon.
- The open VulnerabilitySummary widow will open to allow you to select the vulnerability summary XML file for the desired AppSpider scan that has already been completed. The default location for the scan results files is Documents > APPSpider > Scans. From here you can click on the desired scan results directory and navigate to the Reports folder to find the vulnerability summary XML file.
- Once the vulnerability summary XML file is selected and the open file icon is pressed the vulnerability summary data will be loaded into Defend and once complete you should see a screen similar to below.
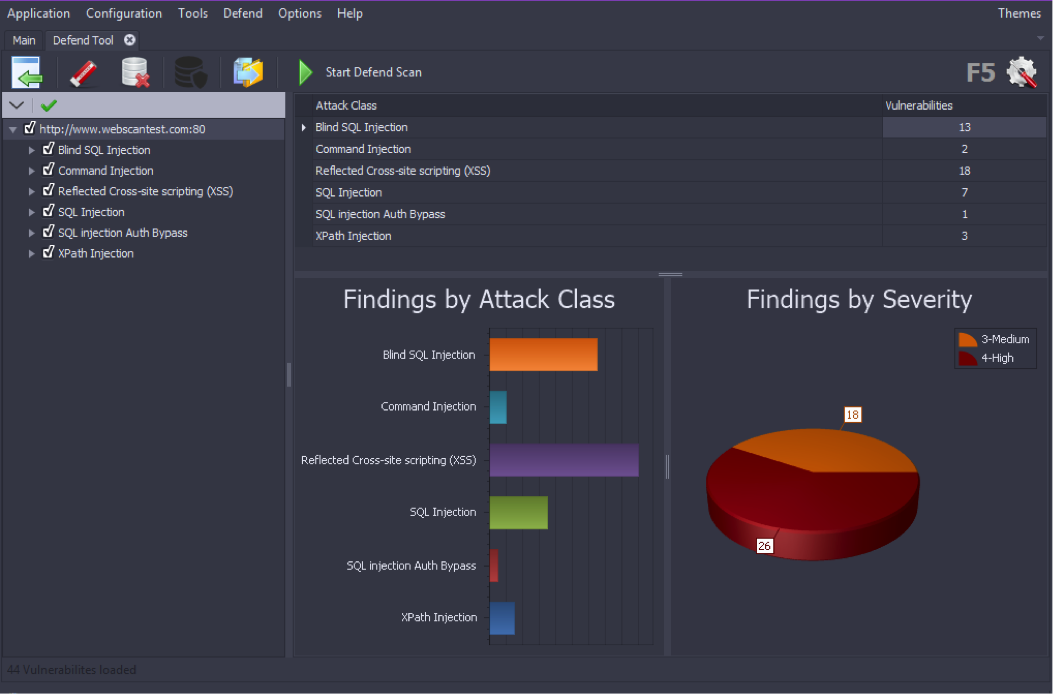
- On this UI screen you can select which vulnerabilities Defend should generated WAF rules sets for by selecting or deselecting the checkbox next to the vulnerability name in the left hand column. From this window you can also select the Options icon in the upper right corner to open the Options UI which will allow you to do a variety of modifications.
- In the Options UI window go to WAF/IDS/IPS selection tab to select F5. Once you are finished with the desired modifications on the Options UI screen press the save button which will take you back to the main UI.
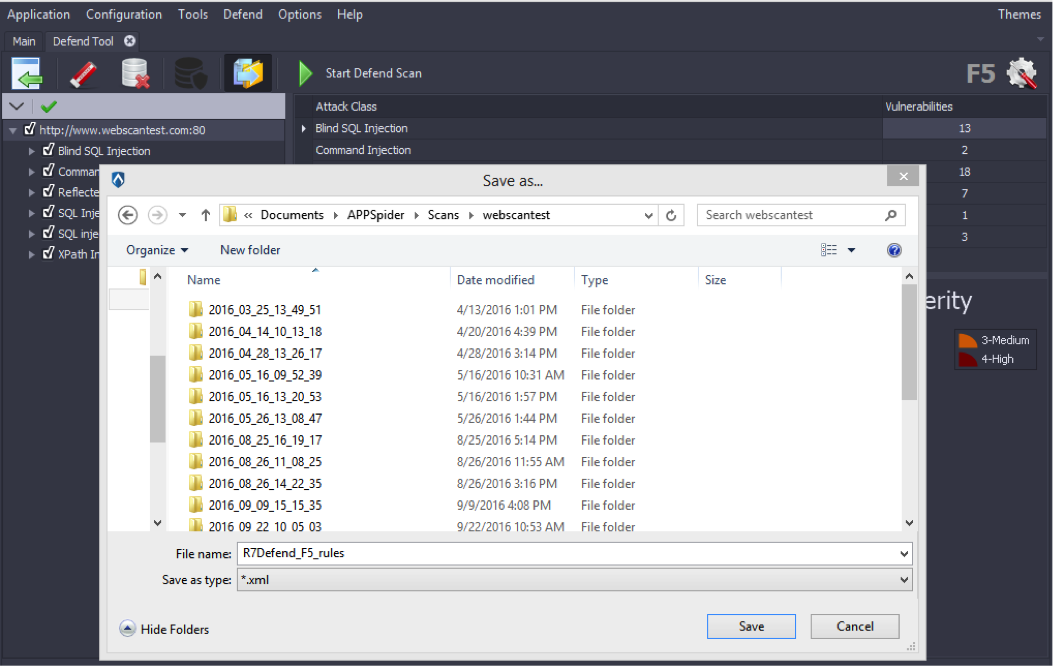
- When finished with any desired modification the Defend rules can be exported to a file by clicking on the Export Rules icon. Once the icon is selected a ‘Save as…’ window will appear to allow you to choose the location of the Defend rules file.
- After completing the upload of the Defend rules into F5 BIG-IP ASM, a Defend scan can be run by clicking on the Start Defend Scan icon. The Defend scan will replay the attacks which were used by AppSpider to discover the vulnerabilities to confirm that they are no longer exploitable due to the deployment of the Defend rules within F5 BIG-IP ASM.
Actions in F5 BIG-IP ASM
- Log on to the F5 BIG IP Configuration Utility.
- Click on Security - -> Application Security - - > Security Policies
- Click on “Create” to create a new policy.
- If the web application is available in a virtual environment, click on Existing Virtual Server.
- Select Create a security policy using third party vulnerability assessment tool output There are two modes available
- Transparent - It will only learn the attacks
- Blocking - It will block all the attacks
- Select web vulnerability scanning technology. In this case we need to select the Generic Scanner option.
- Provide AppSpider’s IP address and Netmask and select appropriate options based on the integration requirement.
- Click the Next button and finish.
Importing Vulnerability report
- Click on the Import button to import vulnerabilities rules created for F5 BIG-IP ASM by AppSpider Defend.
- Select the R7Defend_F5_rules.xml file
- Click on the import button to provide rules created by AppSpider Defend for F5 BIG-IP ASM.
- Vulnerability file with rules is added. Click on the Import button.
- Click on the Close button.
- Vulnerability data can be seen with occurrences