How to Test the Web Application (Automated)
Create a “New Configuration.”
Apply the scan name and list of URLs to be scan. In the following example, we have applied scan name “hackazonwebtest” and the URL “http://192.168.1.108” and click on the Next button.
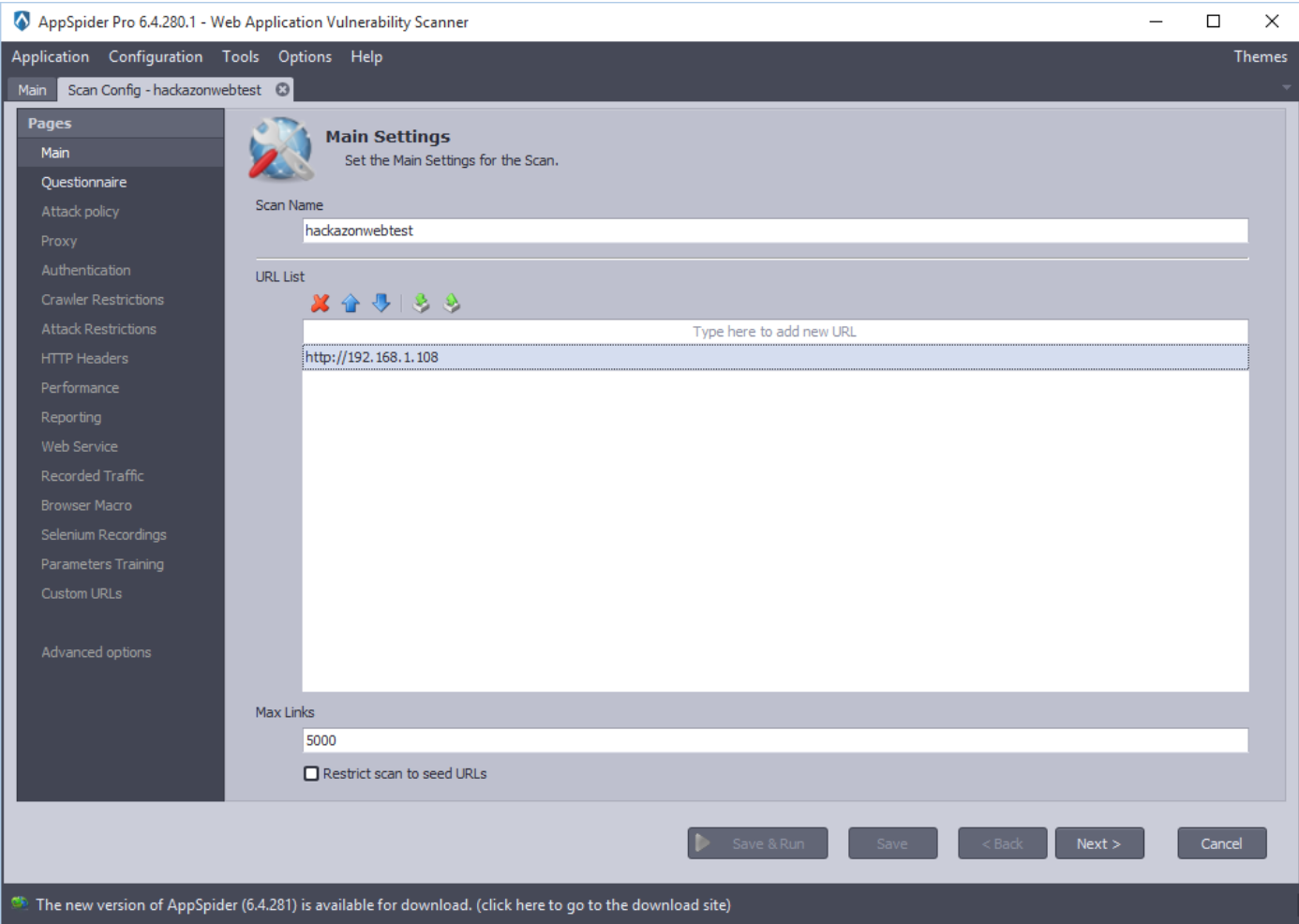
This panel allows the user to enable advanced options for the scan configuration. The list of advanced options is displayed. In this case, we have checked “Attack Policy,” “Authentication” and “Browser Macro” options.
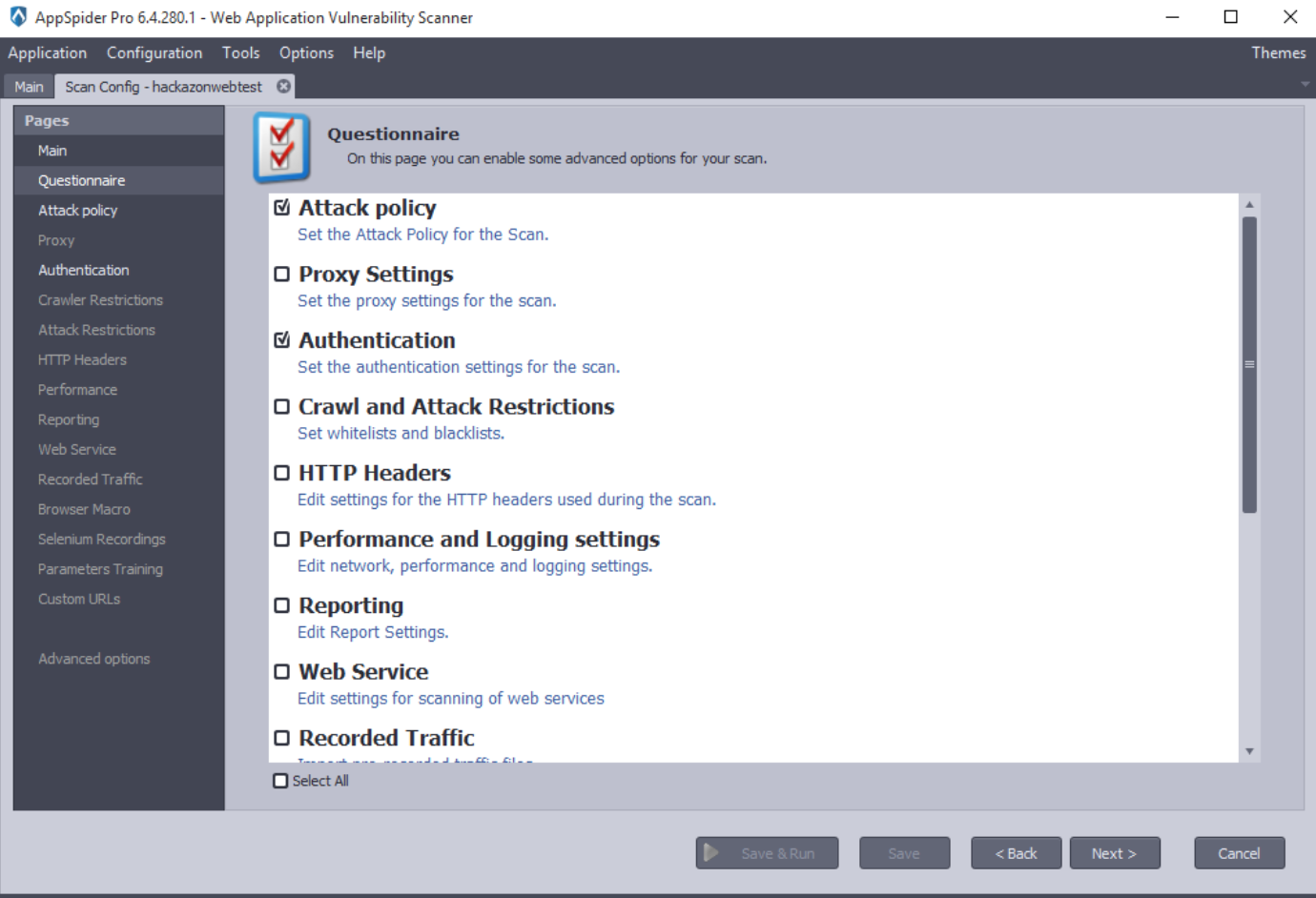
By clicking the Next button, it will land on Attack Policy module. “Attack Policy Template” contains the types of predefined attack policies and a Load button to load the selected template:
- “All Modules” - selects all modules.
- “Crawl Only” - deselects all modules.
- “Passive analysis” - selects modules for passive analysis.
- “SQL Injection” - selects SQL Injection modules.
- “XSS” - selects XSS modules.
- “SQL Injection and XSS” - selects SQL Injection and XSS modules Users are able to save and load the custom/user attack policies. In the following example, we have selected “All Modules” as we would like to test Hackazon application against all the threats. Click on the Next button.
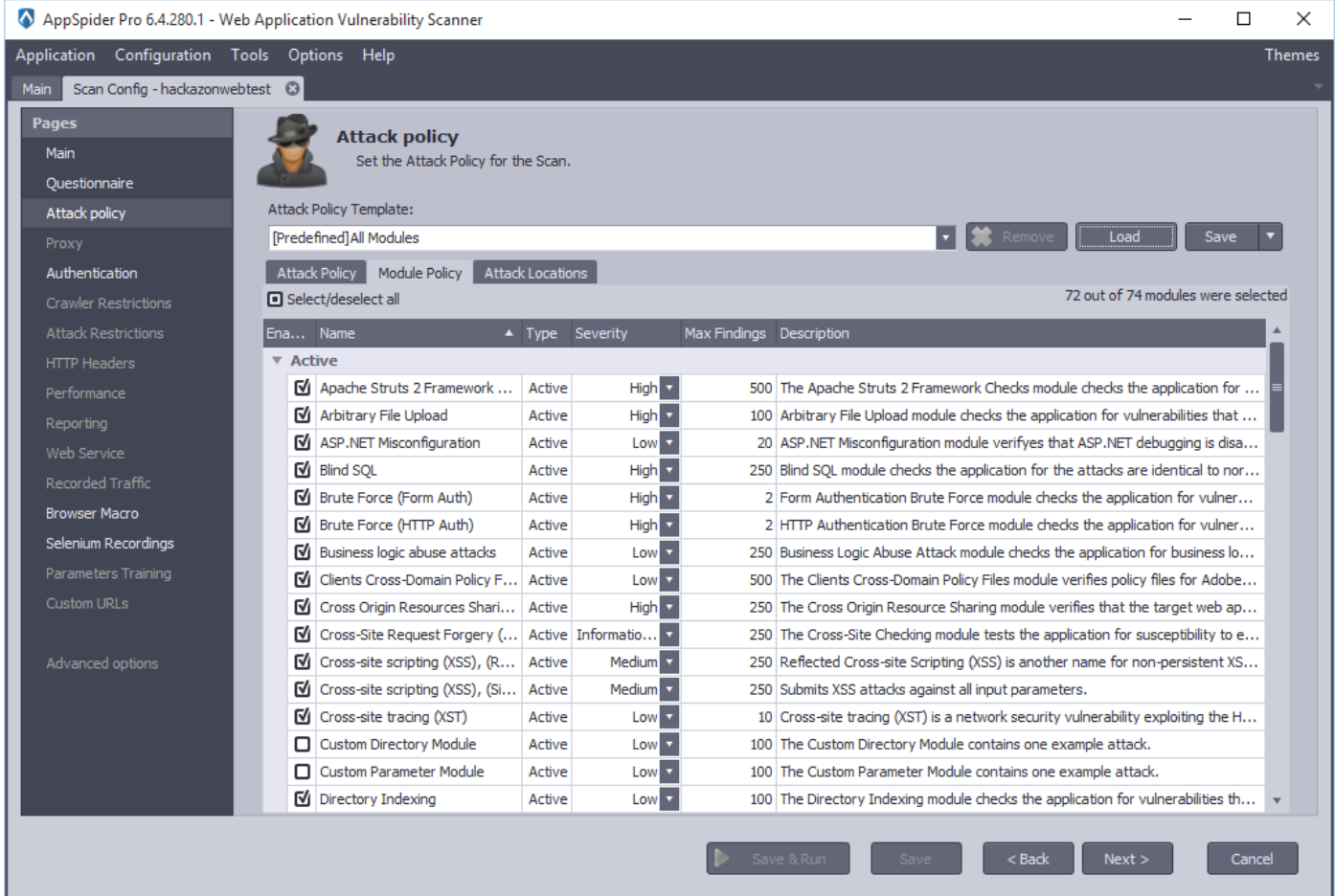
Authentication panel allows user to set the authentication settings. AppSpider has variety of Authentication mechanism in place such as “Form Authentication,” “SSO login,” “Macro Authentication” and many more. In the following example, we have selected “Form authentication” as Hackazon application is using Form based authentication technique.
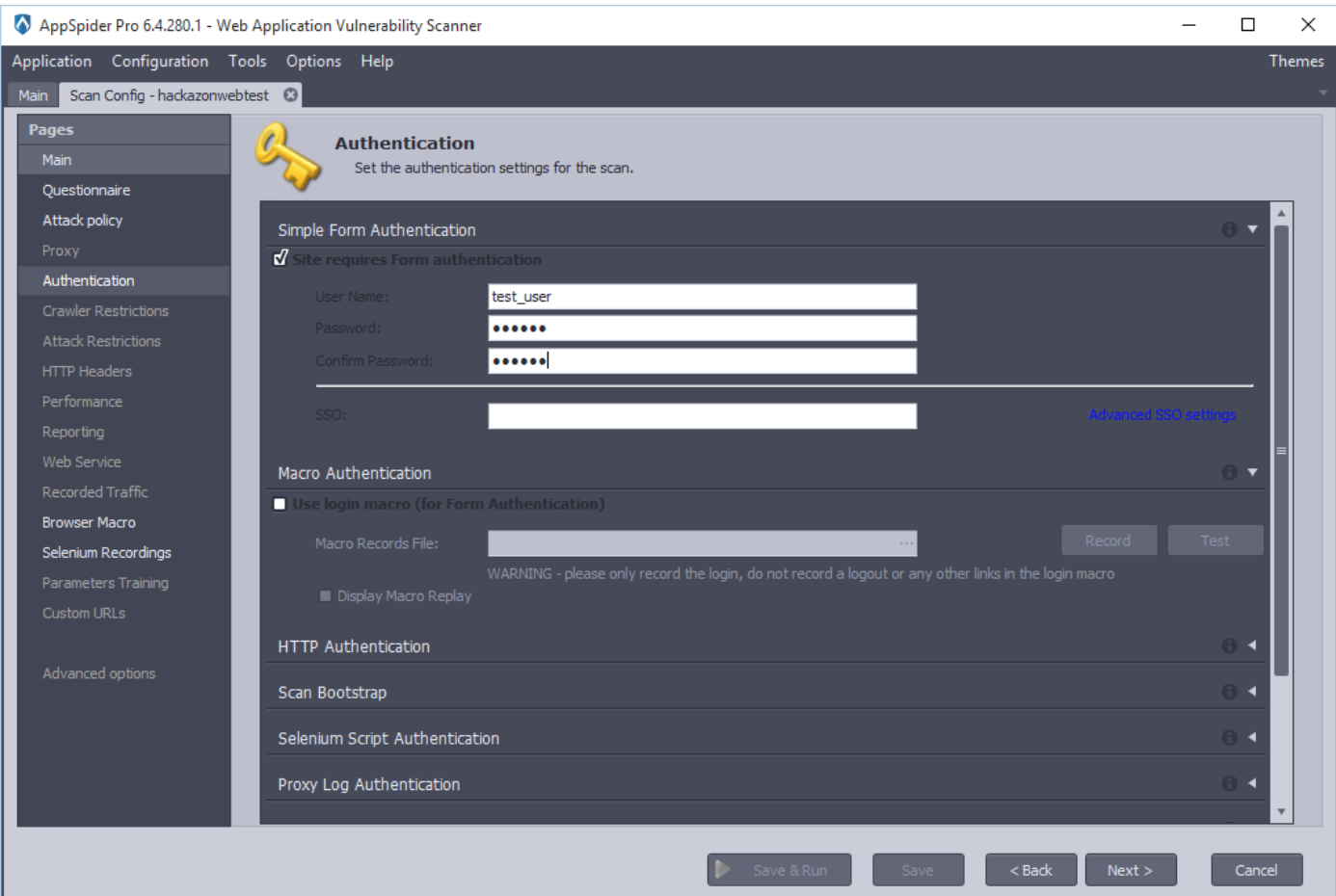
By clicking the Next button, AppSpider will open “Browser Macro” panel. This panel allows user to record or pre-recorded macro files. Macro is a sequence of actions (e.g. menu selections, link executions, value entries, etc.) that will be replayed exactly as input by the user.
In this case, we have recorded a macro sequence using a AppSpider’s native macro recorder.

After completion of the recording, click on the save button and save the macro recording file.
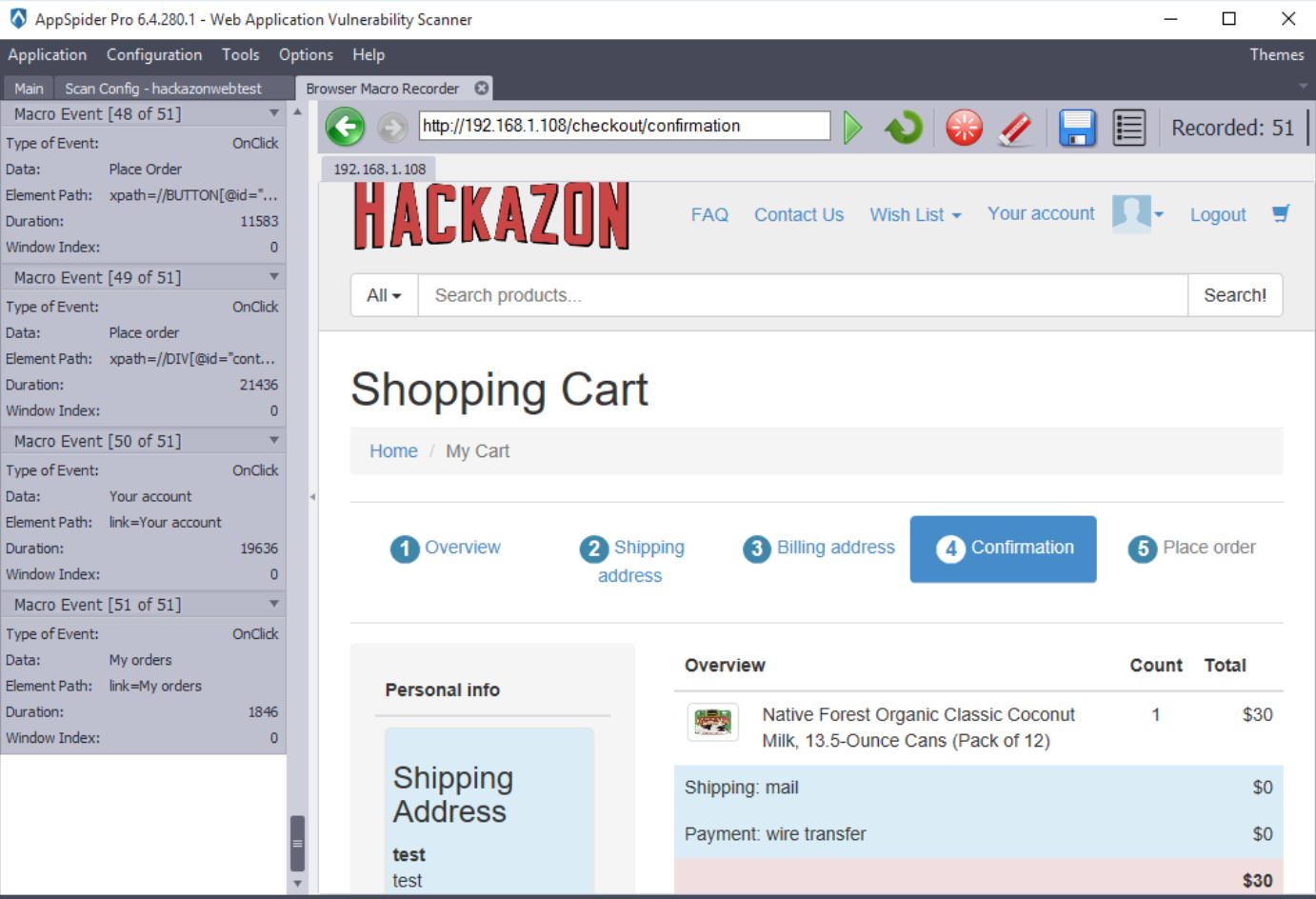
The “Browser Macros” panel will show the HTTP traffic we have recorded earlier. Now, click on the Next and Save and Run button.
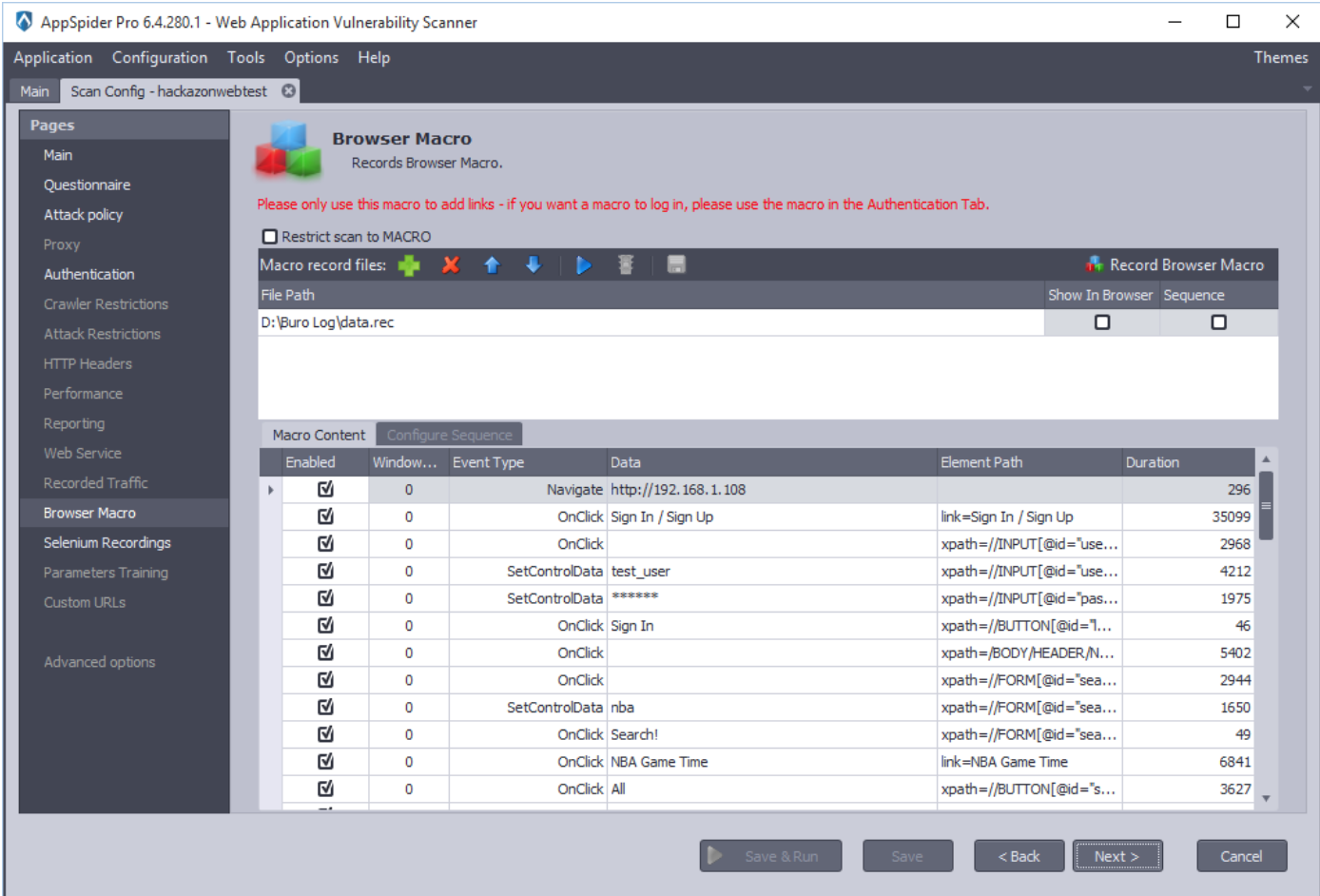
As we have completed the configuration, AppSpider will initiate the scan and shows the scan results on the fly.
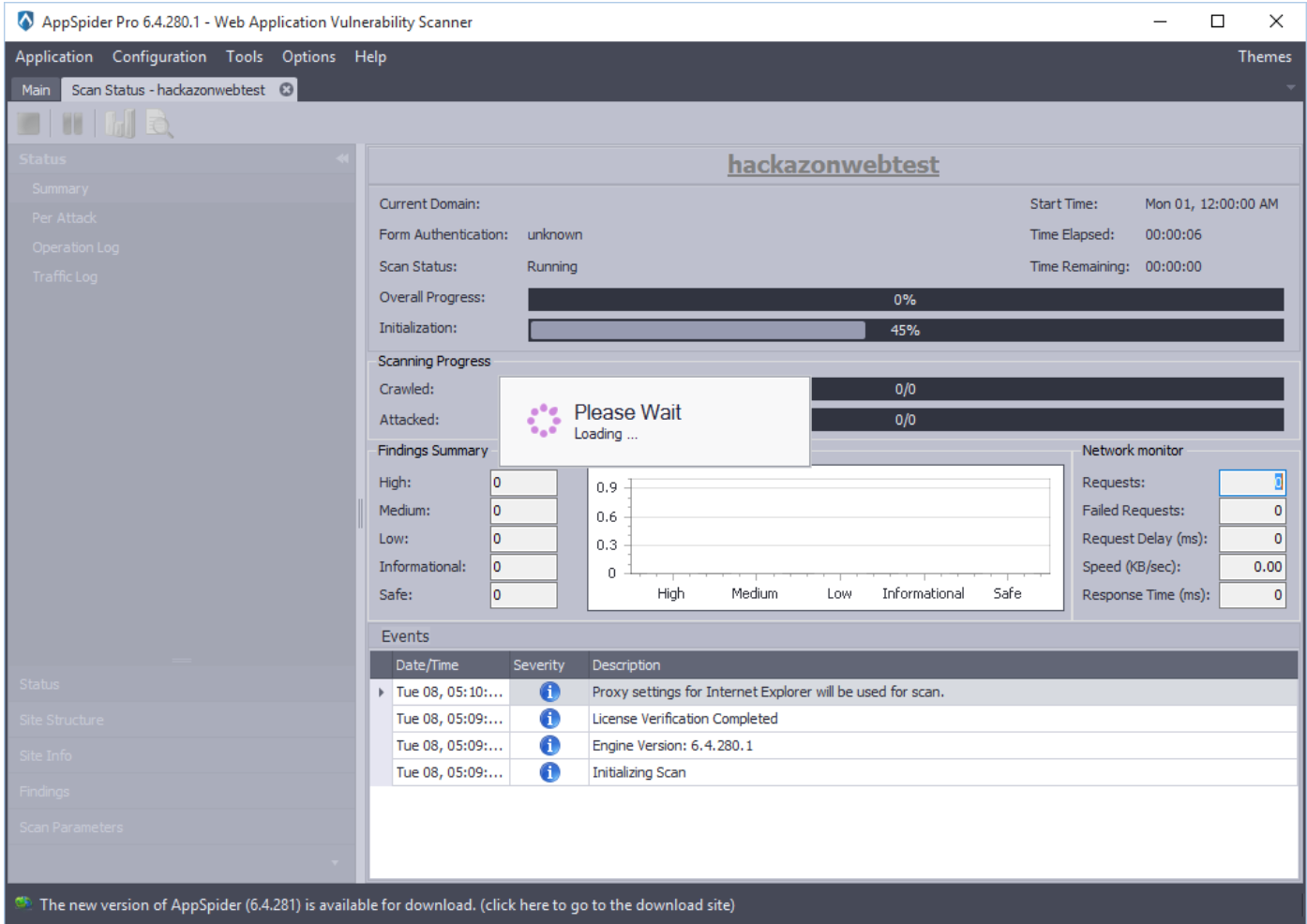
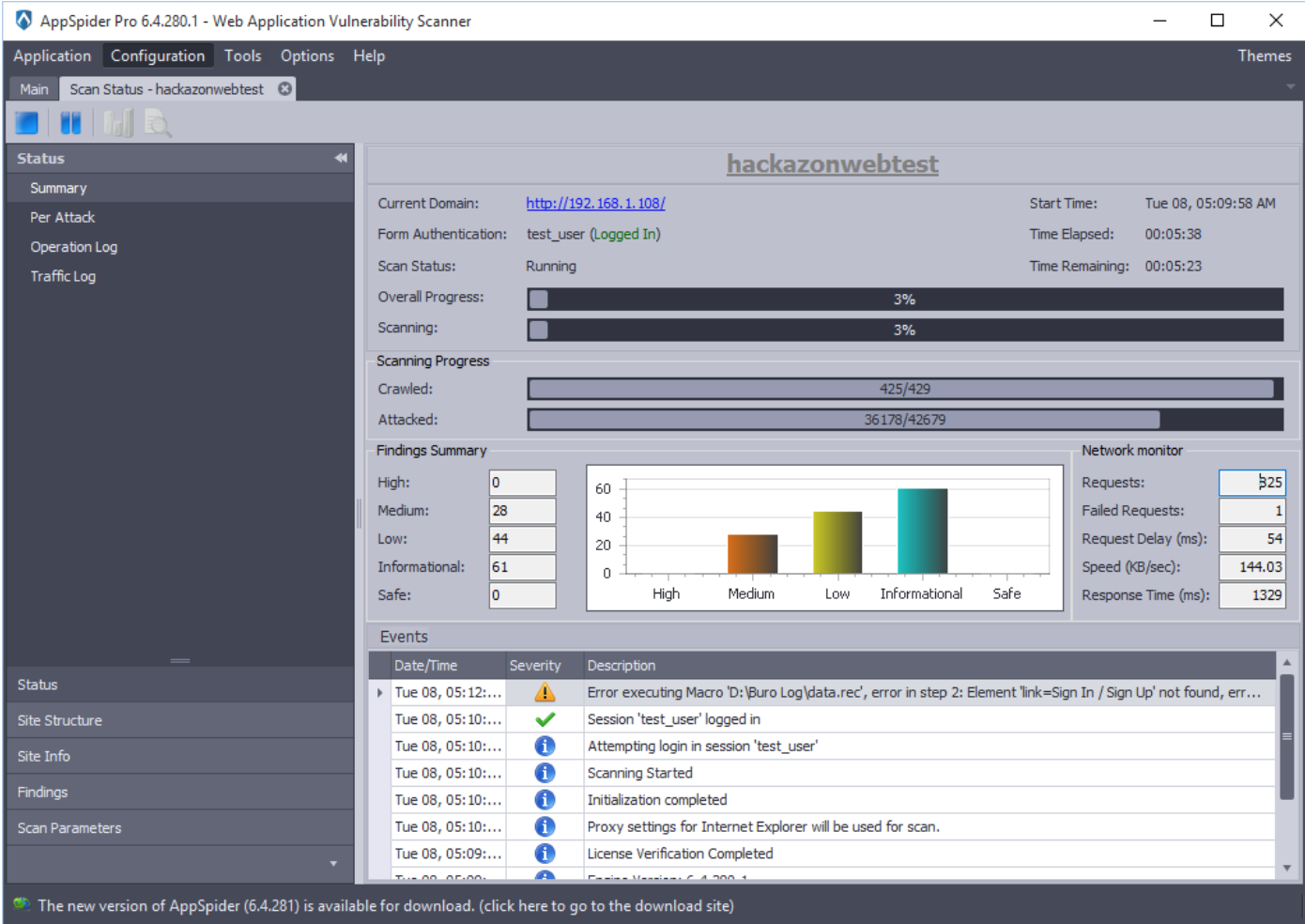
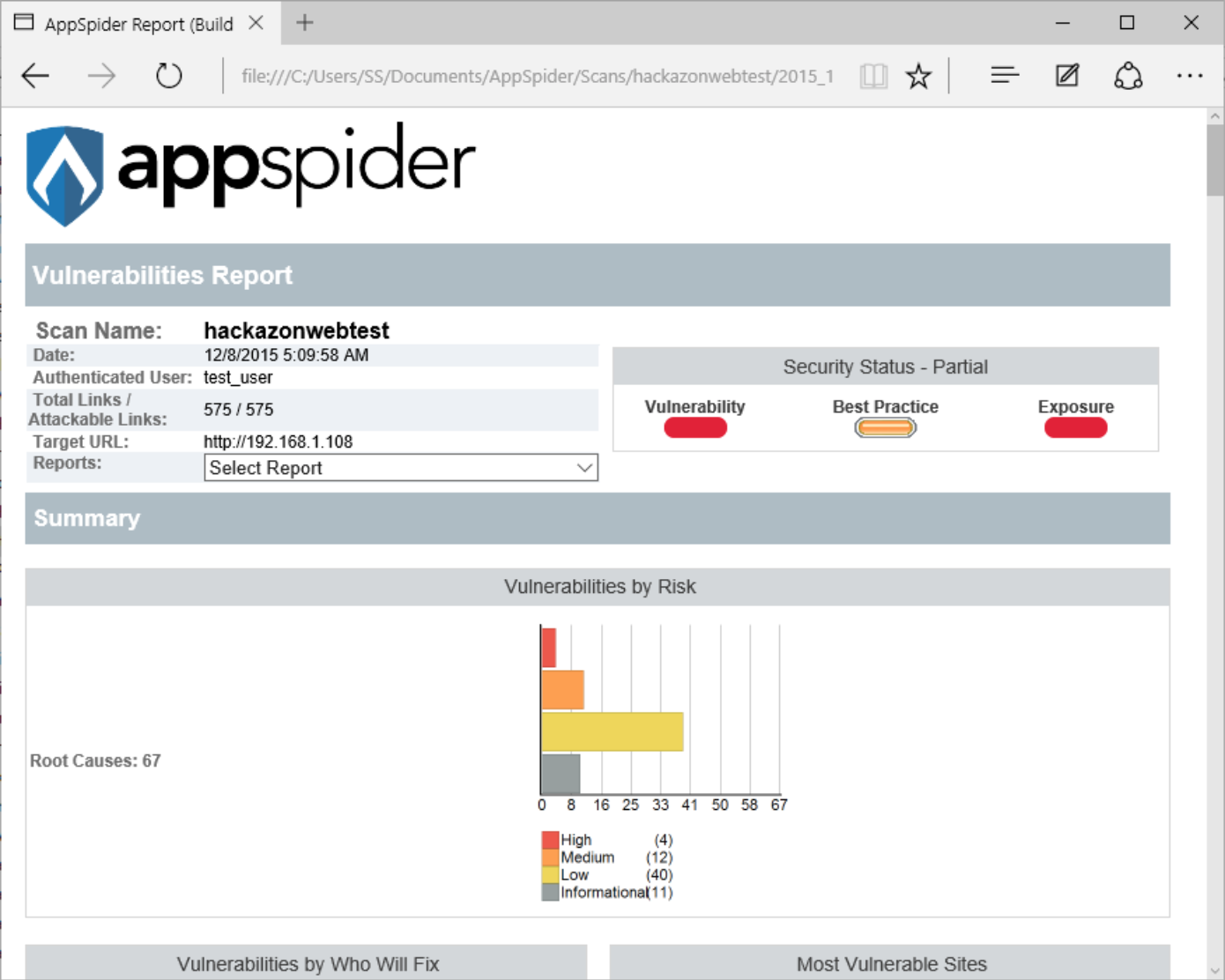
After completion of the scan, AppSpider will show the summary. AppSpider has found 4 High, 40 Medium, 57 Low, and 76 Informational vulnerability during the scan.
AppSpider has generated a HTML report.
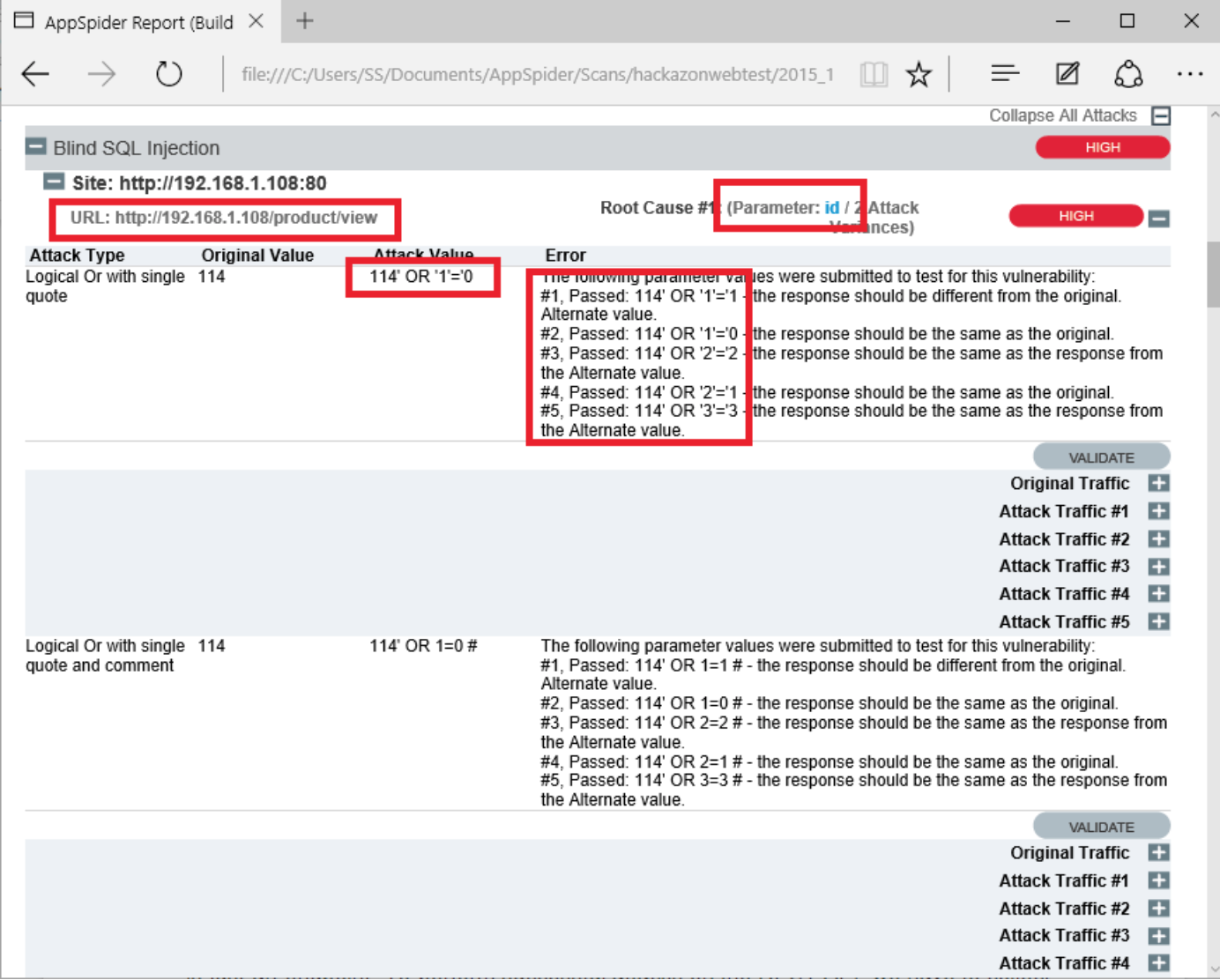
AppSpider has Found a Blind SQL injection. Blind SQL Injection attack that asks the database true or false questions and determines the answer based on the application response. AppSpider has used Logical OR with single quote to identify the vulnerability.
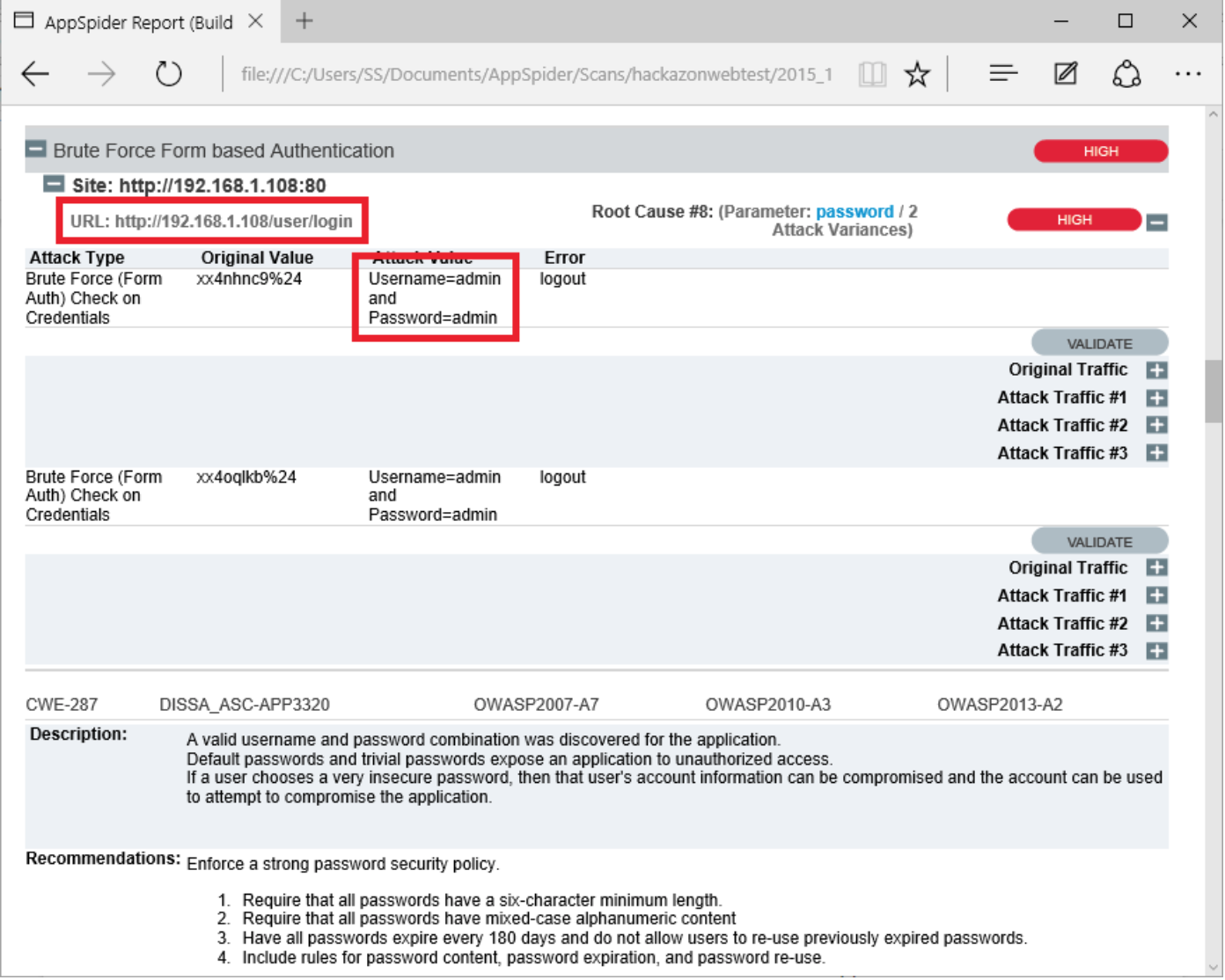
In another case, AppSpider has found a login credentials via brute force attack. Hackazon application is default username password “admin” and “admin”. AppSpider has a list of commonly used usernames and passwords.
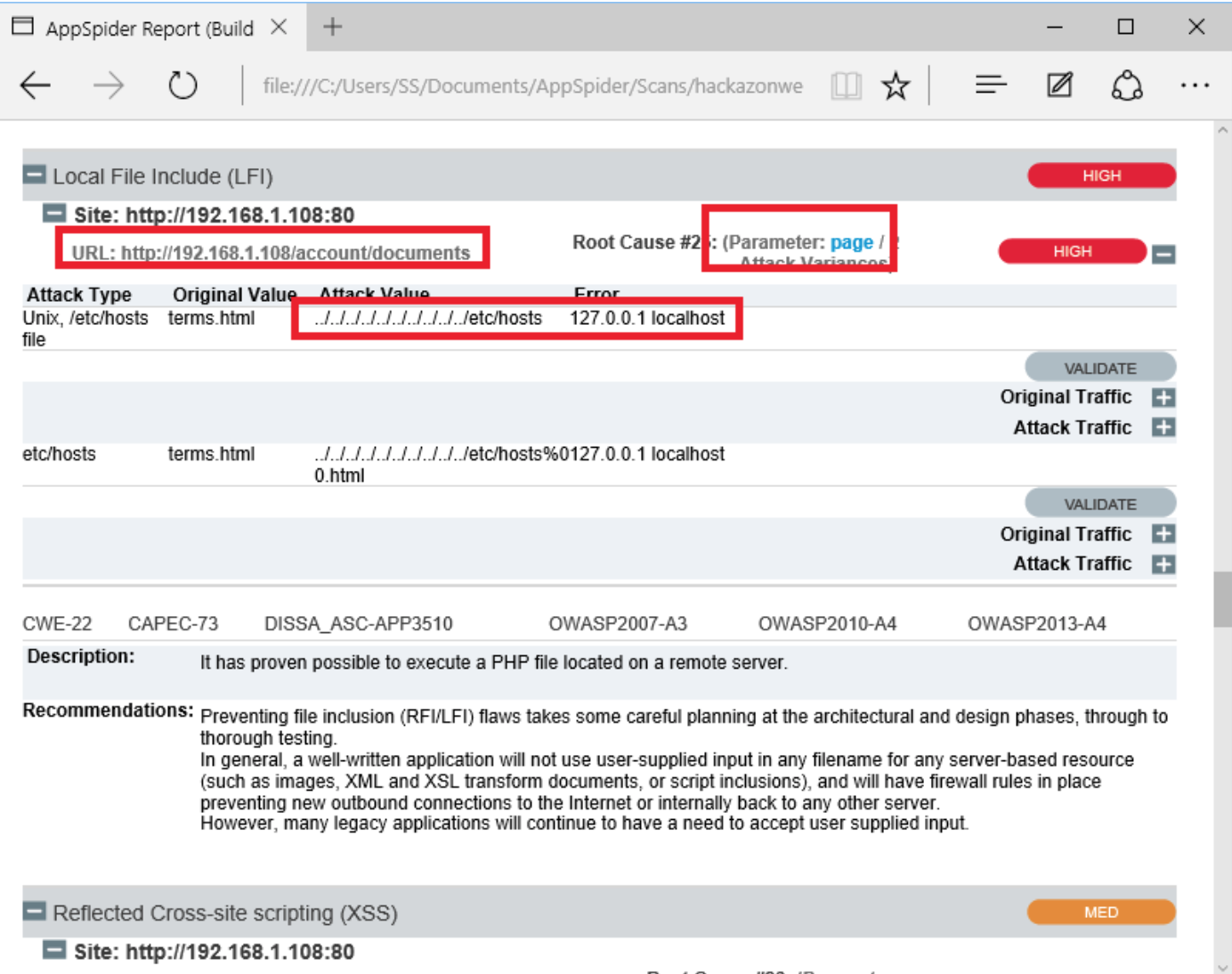
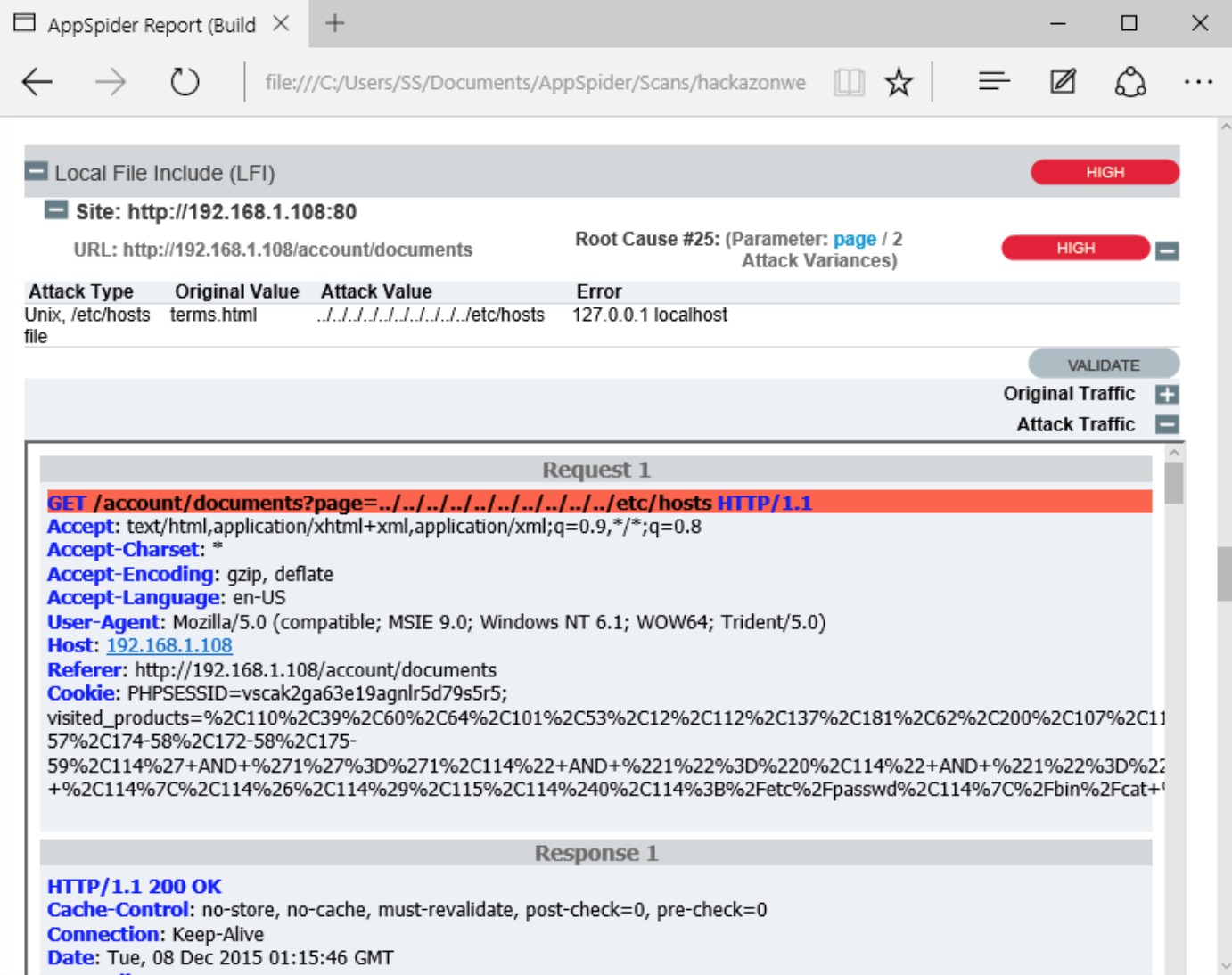
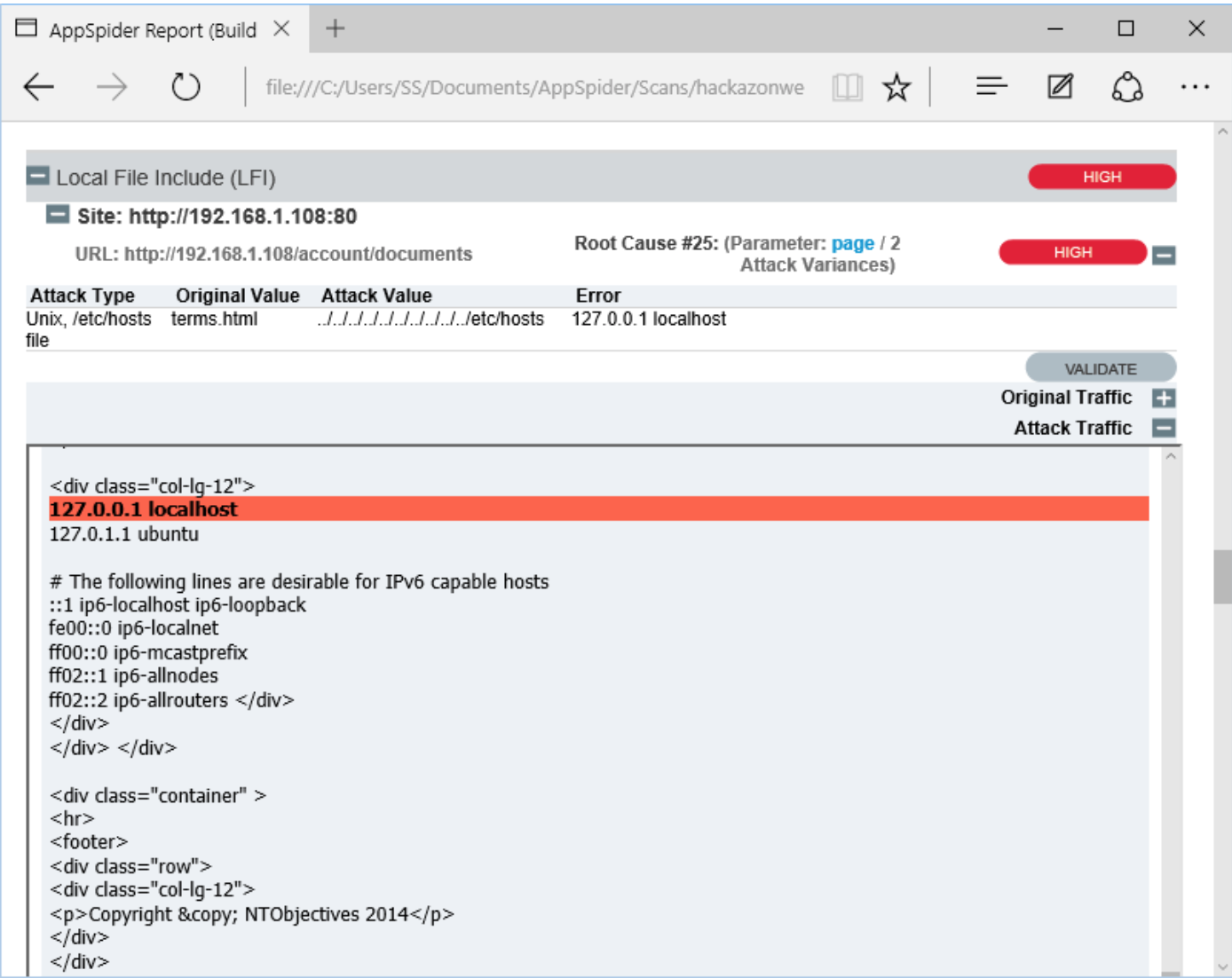
AppSpider has also found a Local File inclusion vulnerability (LFI). The File Inclusion vulnerability allows an attacker to include a file, usually exploiting a “dynamic file inclusion” mechanisms implemented in the target application. The vulnerability occurs due to the use of user-supplied input without proper validation. In following case, a page receives, as input, the path to the file “terms.html terms.html” that has to be included and this input is not properly sanitized, allowing directory traversal characters to be injected.