Troubleshooting SAML set up with AppSpider Enterprise
Make sure the items in the SAML configuration file are correct
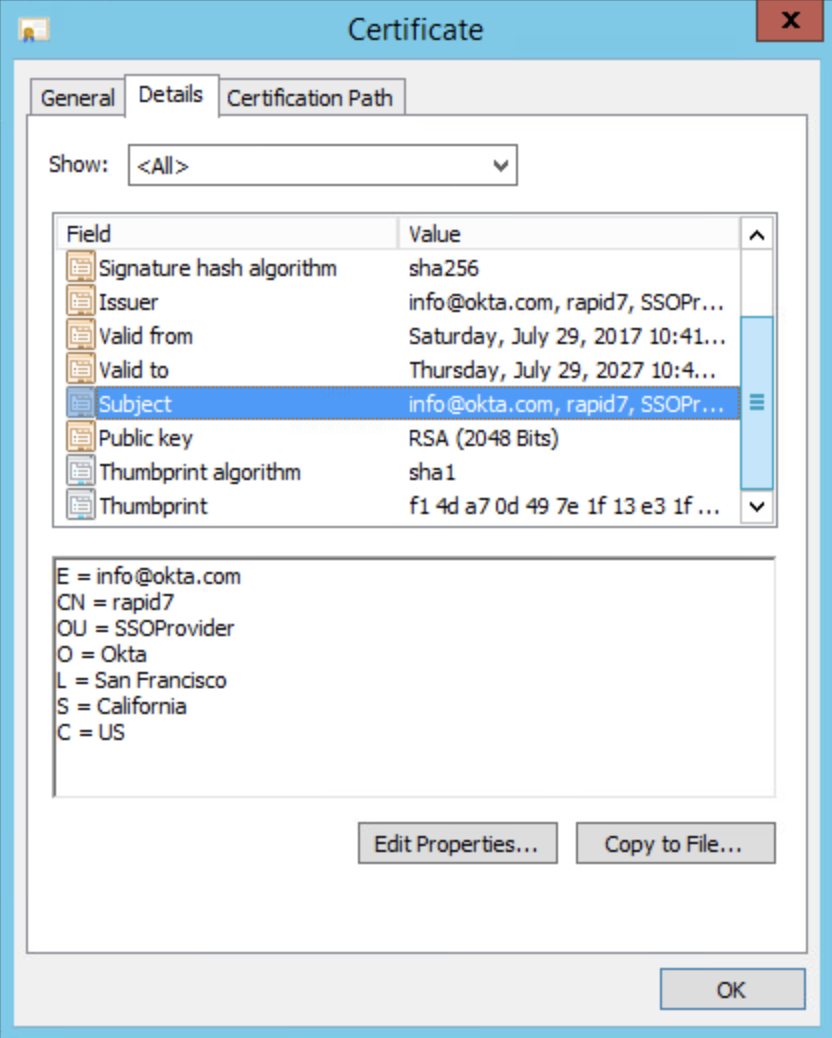
Make sure items defined in Modifying the SAML configuration file for the <certificate> field are valid and correctly entered. The location and identifier of the certificate is a key component in making sure the SAML set up works. As recommended, use the FindByThumbprint element and correctly type in the thumbprint in the FindValue section of the configuration.
Powershell scripts
Some Powershell scripts can be used to identify certificate specific information like the thumbprint value. For example,
$store = New-Object System.Security.Cryptography.X509Certificates.X509Store("My", "LocalMachine")
$store.Open("ReadOnly")
$store.Certificates.Find("FindBySubjectName", "SubjectName", "false")The script may need to be modified based on the SubjectName. The SubjectName can also be the CN value.
Validate the provider
Validate the <provider> value of title inModifying the SAML configuration file when using Service Provider initiated login.
SAML message decoder
You can use any SAML message decoder, for example https://chrome.google.com/webstore/detail/saml-message-decoder/mpabchoaimgbdbbjjieoaeiibojelbhm , to verify the SAML request being captured when logging in via your SSO to identify the parameters being passed to authenticate the user.