Just In-Time User Provisioning (Authentication Server Support)
Database Backup
As with all significant platform changes we recommend that you back up your database before implementing JIT User Provisioning. If you have questions or concerns reach out to us via the Customer Support Portal .
Feature Summary
Cloud Security (InsightCloudSec) is pleased to offer support for authentication server synchronizations, or a feature we’re calling Just In Time User Provisioning (JIT). Cloud Security (InsightCloudSec) JIT provides the capability to synchronize users and groups from an external Identity Provider (IDP) authentication server such as Okta, LDAP, Ping, and Microsoft Entra ID. When an authentication server is configured in Cloud Security (InsightCloudSec), a scheduled sync job runs once an hour and updates can be applied at user login for SAML authentication servers.
This feature, combined with the group-based entitlements feature, enables Cloud Security (InsightCloudSec) Admins to manage Cloud Security (InsightCloudSec) user access from their identity provider without the need to make additional updates for users in Cloud Security (InsightCloudSec).
How Does it Work
Cloud Security (InsightCloudSec) groups are mapped to corresponding groups from the authentication server. Cloud Security (InsightCloudSec) synchronizes the memberships in its mapped groups to those on the authentication server.
- If a user in an authentication server group is not present in Cloud Security (InsightCloudSec), that user is created.
- If an existing Cloud Security (InsightCloudSec) user is no longer in any of the mapped groups in the authentication server, that user is deactivated in Cloud Security (InsightCloudSec) but can be reactivated if that user returns to a mapped group later.
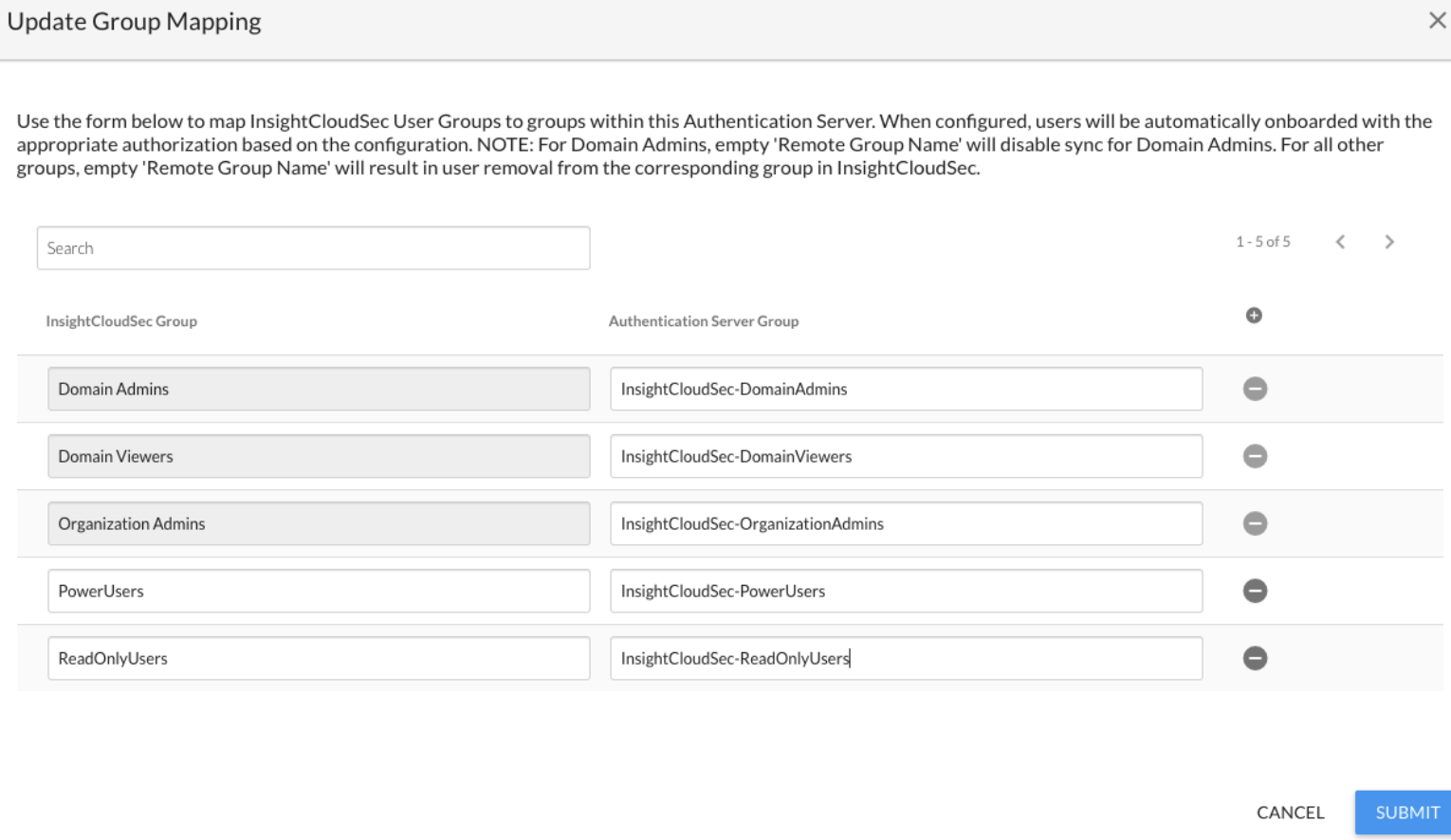
- Cloud Security (InsightCloudSec)’s mappings include authentication server groups to specify Domain Admin, Domain Viewer, and Organization Admin users. An example of group mappings is shown below.
- Domain Admin, Domain Viewer, and Organization Admin users are not available under User groups as they are system-generated and cannot be modified.
Editing Domain Admin and Domain Viewer Mappings
Only Domain Admins can edit Domain Admin and Domain Viewer group mappings.
Prerequisites
Product name to be replaced
You may observe that some components, screen captures, or examples use our former product name, DivvyCloud. This doesn’t affect the configuration or the product’s functionality, and we will notify you as we replace these component names.
Before getting started with Cloud Security (InsightCloudSec)‘s authentication server support using JIT you should have the following:
- A functioning Cloud Security (InsightCloudSec) platform
- Admin permissions for your authentication server
- Only Domain Admins (in Cloud Security (InsightCloudSec)) can edit Domain Admin group mappings
Supported Implementations
At present JIT is available for:
- SAML at user login, through assertions attributes (Any SAML provider)
- Scheduled updates for SAML with Okta. Refer to SAML - Just In-Time Provisioning
- Scheduled updates for LDAP (Any LDAP provider). Refer to LDAP or LDAP - Just In-Time User Provisioning
- Scheduled updates for Active Directory. Refer to Active Directory or Active Directory - Just In-Time User Provisioning
- Scheduled updates for Microsoft Entra ID. Refer to Microsoft Entra ID, Microsoft Entra ID + SAML, or Microsoft Entra ID - Just In-Time Provisioning
Supported Options
Within this documentation for LDAP and SAML we use Okta configurations as an example.
- For specific details on Okta we recommend you refer to their documentation .
- For other providers, we recommend you refer to the specific provider’s configuration documentation.
As always, if you have questions or issues or want details on implementation using something other than Okta we’re here to help, reach out to us through the Customer Support Portal .
Configuration Considerations
Entitlements
You must be prepared to complete the setup of your entitlements. Attempting to create group mappings without completing this setup in Cloud Security (InsightCloudSec) will create groups with users that have NO associated permissions.
- Take a look at our documentation around Basic User Groups, Roles, & Entitlements, and our User Entitlements Matrix if you still need to prepare these configurations.
- The warning shown below is included in our details steps for the various configuration methods to remind you of the potential issues around the creation of Group Mappings without entitlements.
Managing Entitlements
Before you proceed with Group Mappings for external authentication you must have all of your desired entitlements configured.
If you create a group and enable group mapping BEFORE you establish entitlements the users within your groups will have nothing configured and will not be able to access anything.
Refer to our documentation on Basic User Groups, Roles, & Entitlements or the User Entitlements Matrix for details.
Scheduled Updates
In Cloud Security (InsightCloudSec), scheduled updates run once an hour. The authentication server gets lists of members of the mapped user groups, and Cloud Security (InsightCloudSec)’s users and group associations are updated to match.
Credentials
A credential to the authentication server is required to perform the scheduled updates.
- For Okta, this is implemented using a read-only API key.
- For LDAP, Cloud Security (InsightCloudSec) uses the credentials of a user with directory-read privileges.
Frequently Asked Questions (FAQ)
If your issue or concern is not included here or you need assistance with this feature reach out to us through the Customer Support Portal .
What happens if an existing Cloud Security (InsightCloudSec) user is moved out of all mapped groups?
What happens if an existing Cloud Security (InsightCloudSec) user is moved out of all mapped groups?
Cloud Security (InsightCloudSec) users are marked inactive if they no longer have membership in any mapped groups. The user is reactivated if added to a mapped group later.
What happens if a new user is included in a mapped group in the authentication server?
What happens if a new user is included in a mapped group in the authentication server?
Cloud Security (InsightCloudSec) creates a user and places this user in the appropriate mapped group(s). Sync hourly job will create the User in next run. To manually sync, click the actions menu and select Synchronize Users by going to Authentication server setting in Cloud Security (InsightCloudSec).
What happens if a user is included in multiple mapped groups?
What happens if a user is included in multiple mapped groups?
Admin groups are treated differently than basic user groups. A summary of how group mappings are handled is below.
- If a user is in a Domain Admin group, the user will not be placed in Organization Admin group or any basic user groups in Cloud Security (InsightCloudSec), regardless of membership in these groups on the authorization server
- Note that if a user is in both Organization and Domain Admin groups, the user will be a Domain Admin (only) in Cloud Security (InsightCloudSec)
- Users who are not Domain Admins (e.g. an Org Admin) can be members of multiple basic user groups.
What happens if a user is not included in any mapped groups?
What happens if a user is not included in any mapped groups?
If a existing user is not mapped to any groups, they are marked as disabled within Cloud Security (InsightCloudSec). Disabled users will do not appear in typical administrative displays (e.g. under User Management > Users).
User names are unique, so if a disabled user attempts login:
- It won’t work and;
- An administrator will not be able to recreate them with the same name
In this case, return to Okta to ensure they’re properly configured (add them to the appropriate group) and their credentials will sync through the appropriate mapping (e.g. LDAP or SAML). You can force a sync by revisiting the Actions menu for the applicable server once any configuration issues have been resolved.
What happens to deleted users?
What happens to deleted users?
As of 22.3.0 Cloud Security (InsightCloudSec) retains deleted users so that it is possible to reconstruct which users took which actions when examining the API activity. This makes it possible to restore deleted users as active users and preserves the ability to examine users in API activity whether active or deleted.
Can I migrate an existing local user to an SSO provider to avoid having to delete/recreate the user?
Can I migrate an existing local user to an SSO provider to avoid having to delete/recreate the user?
Yes. Under the user and admin actions menu, you can select Change authentication server to view a drop-down of available providers to select.
Transitioning to LOCAL is not supported.
What are the pros and cons of scheduled sync and sync-at-login?
What are the pros and cons of scheduled sync and sync-at-login?
This is only an option for SAML.
Scheduled sync and sync-at-login can be used independently or together, depending on your requirements and the availability of authentication server credentials.
Scheduled Sync Pros:
- Keeps Cloud Security (InsightCloudSec) fully synced with the authentication server
- Including deactivation of users who no longer have access to Cloud Security (InsightCloudSec) (which is helpful for audit around account users that have left)
Scheduled Sync Cons:
- Updates on the authentication server side can take up to an hour to propagate to Cloud Security (InsightCloudSec)
- Cloud Security (InsightCloudSec) Admin has an option to initiate an on-demand sync.
- Requires the Cloud Security (InsightCloudSec) Admin to provide an authentication server credential for Cloud Security (InsightCloudSec) to use when fetching updates from the authentication server
Sync-at-login Pros:
- Users see effects of authentication servers immediately when they log in
- Does not require authentication server credentials
- With some SAML providers, will not require any extra configs on SAML provider side
Sync-at-login Cons:
- Authentication server updates are not propagated to Cloud Security (InsightCloudSec) unless a user logs in
- May require configuration for SAML provider to put required attributes in SAML assertions
What happens to existing Cloud Security (InsightCloudSec) user login sessions if the sync changes user entitlements?
What happens to existing Cloud Security (InsightCloudSec) user login sessions if the sync changes user entitlements?
For scheduled synchronizations, all of a user’s sessions are terminated if:
- A user loses all access to Cloud Security (InsightCloudSec) as a result of the update, or
- The user has a decrease in admin privileges
For sync-at-login, all existing user sessions are terminated if:
- Any changes are made to the user’s group memberships. Since the user is in the act of logging in, and will get the up-to-date permissions, the UX impact of removing other sessions for the user is minimal.