Host Vulnerability Assessment Overview
The information on this page has moved
For the most up to date Host Vulnerability Assessment (HVA) guidance, go to Learn About Vulnerabilities.
Feature Summary
Host Vulnerability Assessment (HVA) enables Security and DevOps teams to efficiently view, prioritize, and orchestrate the response to vulnerabilities (Common Vulnerabilities and Exposures (CVEs)) detected on host instances across their clouds accounts. Hosts are automatically assessed when they are launched and detected by the InsightCloudSec harvesters without the use of traditional network scanning or an embedded agent. Using snapshots of the instances’ root volume, a thorough vulnerability assessment is performed on all packages in the guest operating system and installed software, on Open Source Software (OSS) dependencies, and on select file types.
The snapshots are downloaded to your InsightCloudSec instance, their package inventory is assessed and stored, and then promptly deleted. The host instance inventory is continuously monitored for new vulnerabilities as long as they remain active in your cloud. Select changes to the host instance in the cloud will automatically trigger a fresh snapshot and assessment. Remediations are detected and recognized whether by host instance updates or removals and replacements by updating the base image (for example, AMI) and relaunching.
Capabilities
HVA offers the following capabilities:
- Comprehensive assessment and visibility including:
- All host instances (resources), plus their base image, metadata, and detected vulnerabilities
- All packages plus their prevalence across the host instances
- All vulnerabilities detected across the instances and packages in total plus their metadata and link to exploit references
- Vulnerability Risk scores for each CVE calculated by a new, proprietary model leveraging intelligence about available exploits and their use by attackers in the wild
- Advanced filters to narrow the focus on select resources and their packages and vulnerabilities for risk-based prioritization and remediation
- Recommended solutions for each vulnerability as package and OSS version updates.
- Actions and automation that trigger alerts, ticketing, remediation workflows, and data exports
- Assessment coverage and health monitoring to identify any errors or access issues impacting feature operations
Current Support
Host Vulnerability Assessment supports AWS EC2, Azure Virtual Machine (VM), and GCP VM instances and is only available to InsightCloudSec SaaS customers. In addition, Windows hosts are not supported and will fail assessment.
Additional Details
Check out the Host Vulnerability Assessment - Configuration & Workflows page for details on the common workflows for Host Vulnerability Assessment and information on the require prerequisites.
The Host Vulnerability Assessment - User Guide provides details on feature operation and capabilities.
Frequently Asked Questions (FAQ)
Why does InsightCloudSec require AWS/Azure/GCP permissions to assess host vulnerabilities?
Agentless assessment requires that InsightCloudSec has a way to scan a volume/disk without running anything in your cloud environment. InsightCloudSec downloads a snapshot of a resource’s root volume to our own cloud provider account (using the users/roles/policies you configured during onboarding), runs the assessment, and deletes the snapshot. We use the minimal required permissions for creating, downloading/exporting, and then removing the snapshot.
The process looks something like this:
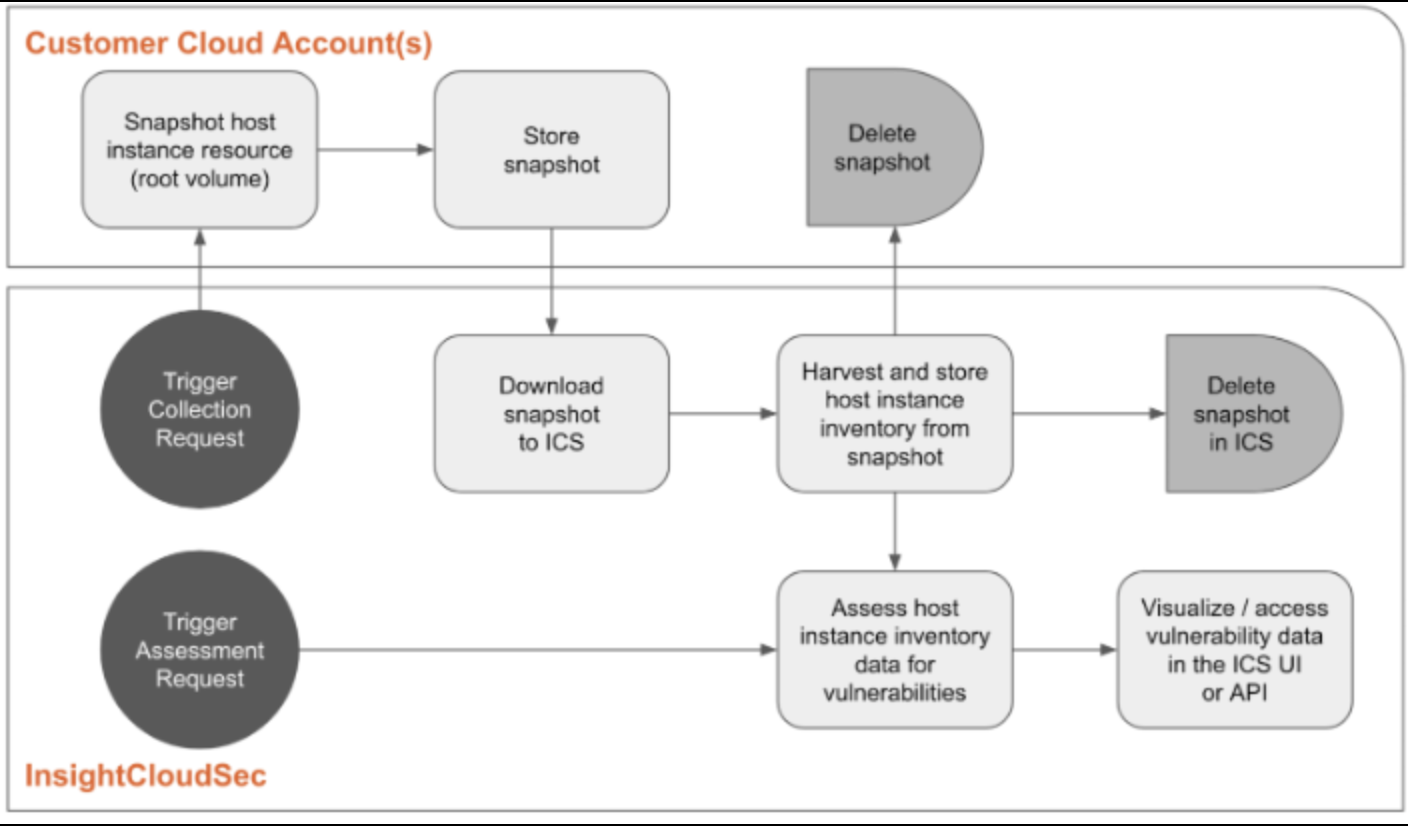
What is the frequency of snapshots being created and then deleted?
Snapshots are created:
- When a new host is discovered
- When a new vulnerability is discovered
- When you manually trigger an assessment
In what regions do you assess host vulnerabilities?
- Regional assessments are only supported for AWS right now
- All Azure and GCP resources get assessed in
us-east-1
- All Azure and GCP resources get assessed in
- We support running assessments in seven AWS regions:
us-east-1,us-east-2,us-west-2,eu-central-1,ap-northeast-1,ap-southeast-2, andca-central-1 - Any resources located outside those regions will get mapped to a supported region according to internal logic
- If a mapping does not exist, the assessment will get sent to
us-east-1by default
Can you assess host vulnerabilities using AWS default key-encrypted snapshots?
Snapshots taken of an AWS instance that uses the default AWS-managed key will automatically have the same encryption; this encryption method cannot be changed and these snapshots cannot be directly shared or accessed. As a workaround, default key-encrypted snapshots will have to be copied and encrypted using the Rapid7 customer-managed key. This key is stored and managed internally by Rapid7. For this process, a grant will be created for the Rapid7 key with the AWS cloud account’s role ARN as the grantee and retiring principal. This key grant will apply the permission to use the Rapid7 key to copy and encrypt their snapshots and then retire the grant after the assessment is completed.
Limitations:
- This feature is currently only enabled for AWS instances in the following regions:
ap-northeast-1ap-southeast-2ca-central-1eu-central-1us-east-1us-east-2us-west-2
- Assessments for default key-encrypted instances in all other regions will fail with the exception
DefaultEbsKeyExceptionand error reason"You can’t share snapshots that are encrypted with the default AWS managed key. You can only share snapshots that are encrypted with a customer managed key." - Each customer managed key can have up to 50,000 grants. However, it’s unlikely that this quota will be reached since the grants are retired after assessments are complete. See the AWS Documentation for more information.