AWS Secrets Manager
InsightCloudSec requires the use of AWS Secrets Manager to authenticate into an external database in RDS, as well as the Redis instance in ElastiCache (details are included below.)
This feature necessitates customers create a Secret in Secrets Manager containing the credentials of the RDS instance hosting the database for InsightCloudSec/Elasticache, hosting the Redis data for InsightCloudSec, and for InsightCloudSec to pull credentials using the AssumeRole functionality.
Note: The specific steps provided on this page apply to self-hosted customers. For hosted customers we recommend that you contact your CSA or contact us through the Customer Support Portal .
Prerequisites for RDS
To use Secrets Manager authentication for your RDS database, you will need the following:
- An RDS Database with a
divvyanddivvykeys database - EC2 instances that have an attached role with at least basic user permissions in addition to
secretsmanager:GetSecretValueto access the secrets in Secrets Manager - A properly configured
prod.envfile on each instance running InsightCloudSec
Prerequisites for ElastiCache
To use Secrets Manager authentication for your ElastiCache instance, you will need the following:
- An ElastiCache instance
- EC2 instances that have an attached role with at least basic user permissions in addition to
secretsmanager:GetSecretValueto access the secrets in Secrets Manager - A properly configured
prod.envfile on each instance running InsightCloudSec
Product name to be replaced
You may observe that some components, screen captures, or examples use our former product name, DivvyCloud. This doesn’t affect the configuration or the product’s functionality, and we will notify you as we replace these component names.
Steps for Using Secrets Manager
1. To access the Secrets Manager, login to the AWS console, as an Admin, in the account where your RDS database exists and navigate to its region.
2. Select Store a new secret.
- To create a Secret manually, follow these steps.
- If you create a Secret with RDS, for example, when using Cloudformation, verify the Secret naming and key conventions match the pattern below.
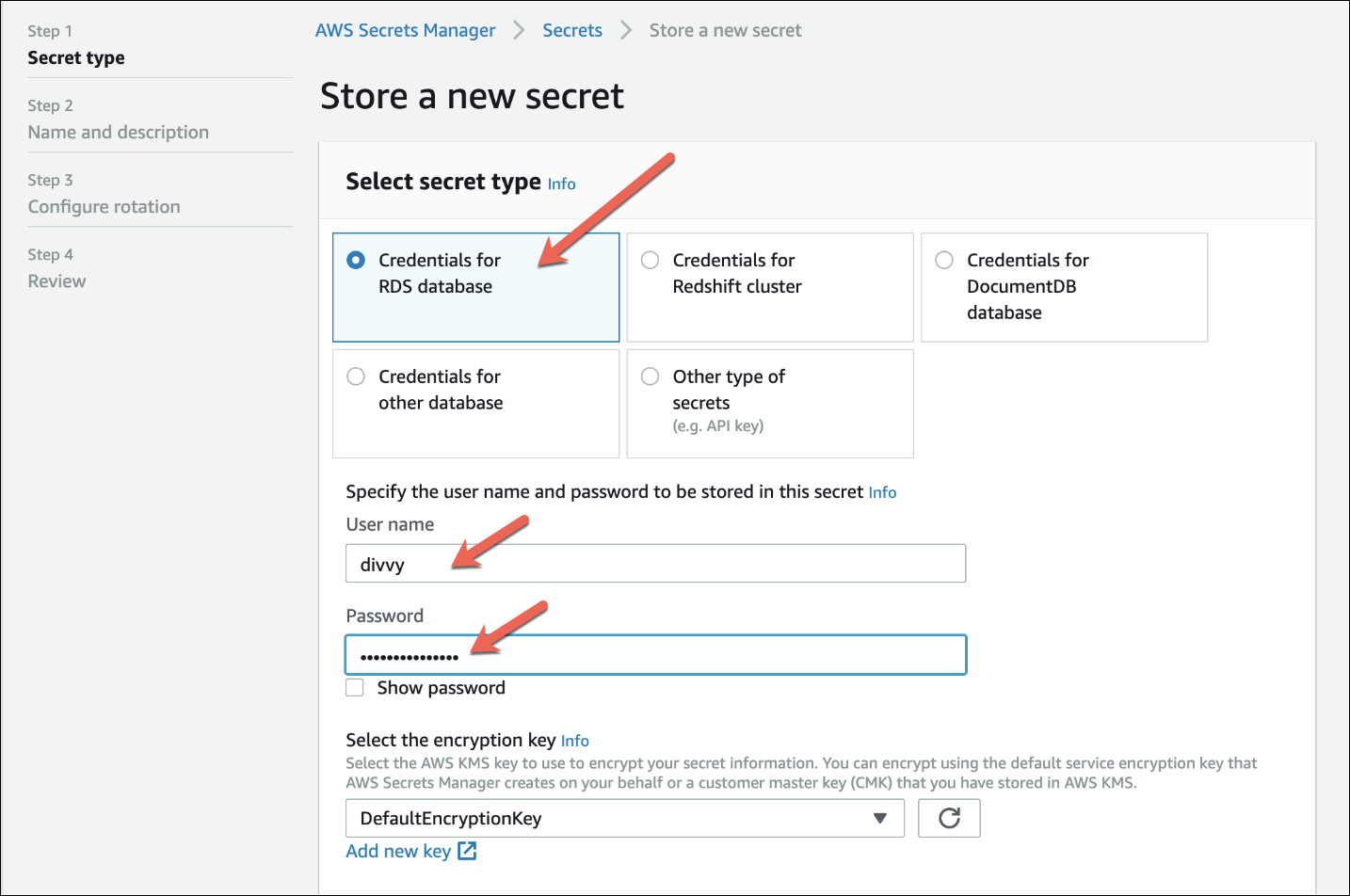
3. Select your secret type. You’ll also need to select the instance of the database your secret will access.
- Specify the User Name and password to be stored in this secret (both User Name and password for the database can be found in the current
prod.envfile, as described below) - Select “Next” (lower right of the screen)
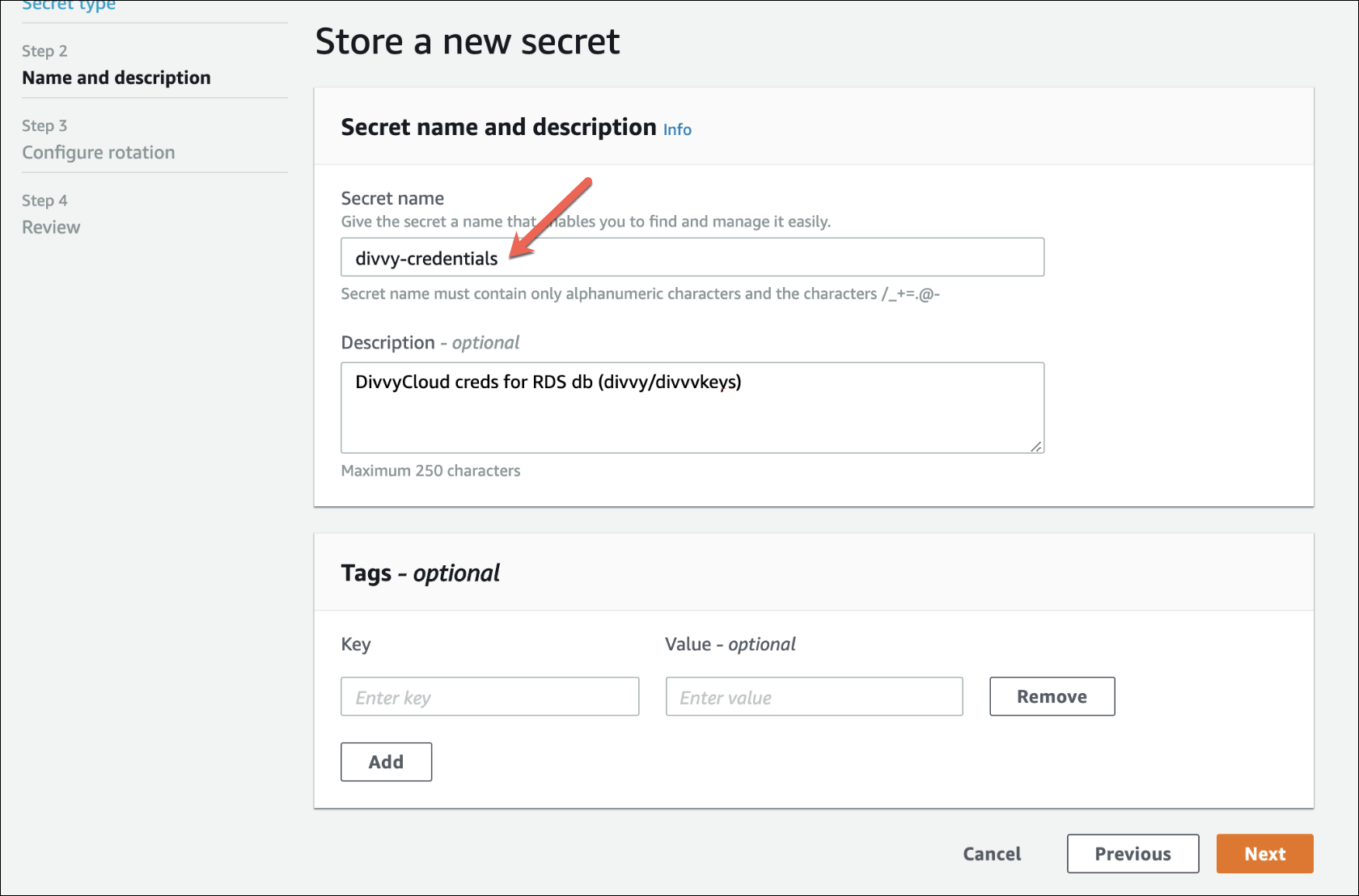
4. Store a new secret. Give your Secret a useful name, for example, insightcloudsec-credentials, and an (optional) description. Make note of this name for use in later steps.
❗️ Secret Creation
If you delete your Secret, you cannot create a new Secret with the same name in the same region for a minimum of seven days. Use “edit” to modify your Secret rather than replacing it.
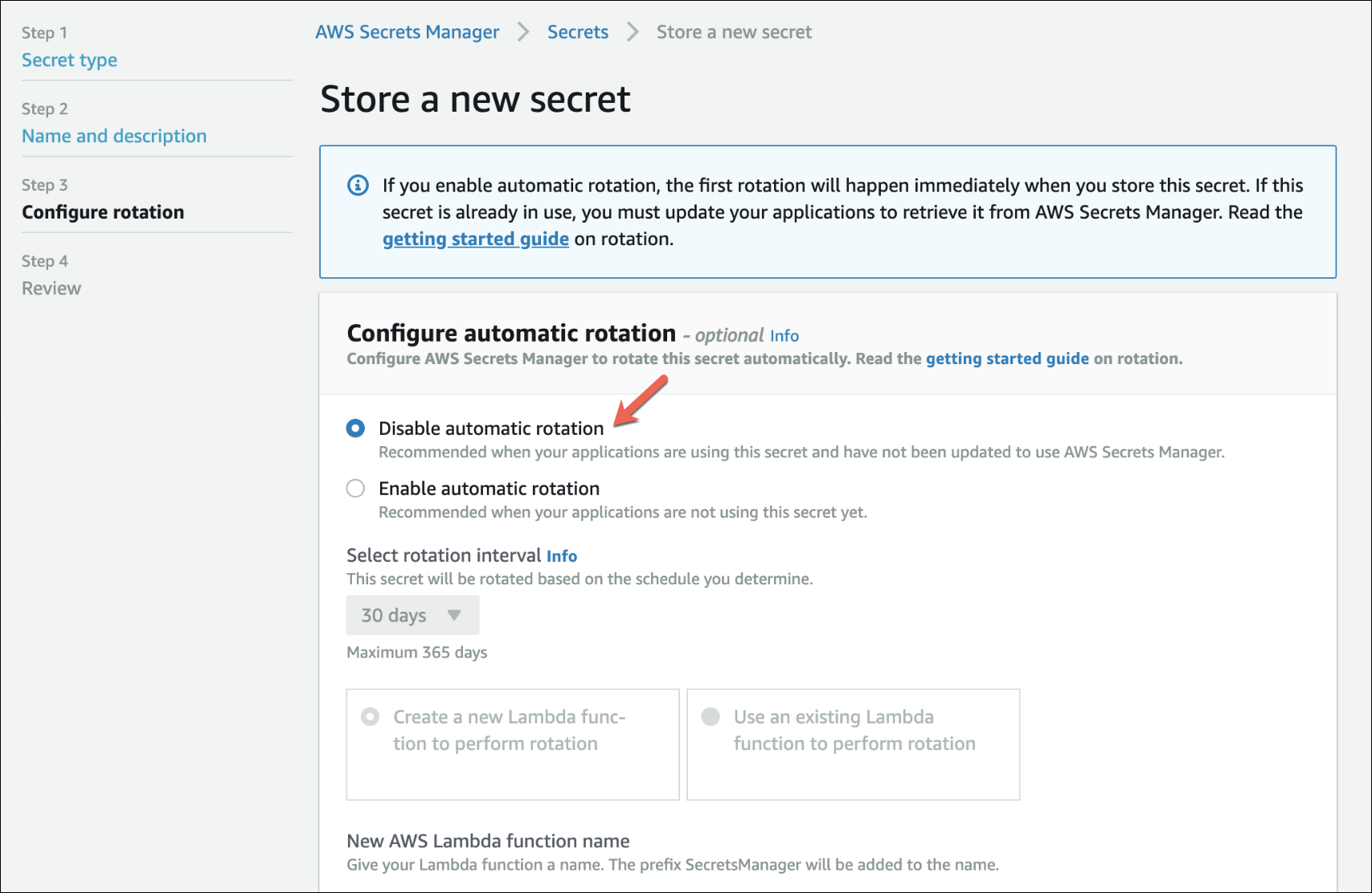
5. To configure automatic rotation, select “Disable automatic rotation” and select “Next”.
If you’d like to set up automatic rotation, you will have to set up an AWS Lambda function to handle this for your secrets as well as RDS databases.
6. Review what you’ve done so far. If everything looks ok, select “Store” (bottom right).

7. Return to the the list of secrets and select your newly added secret.
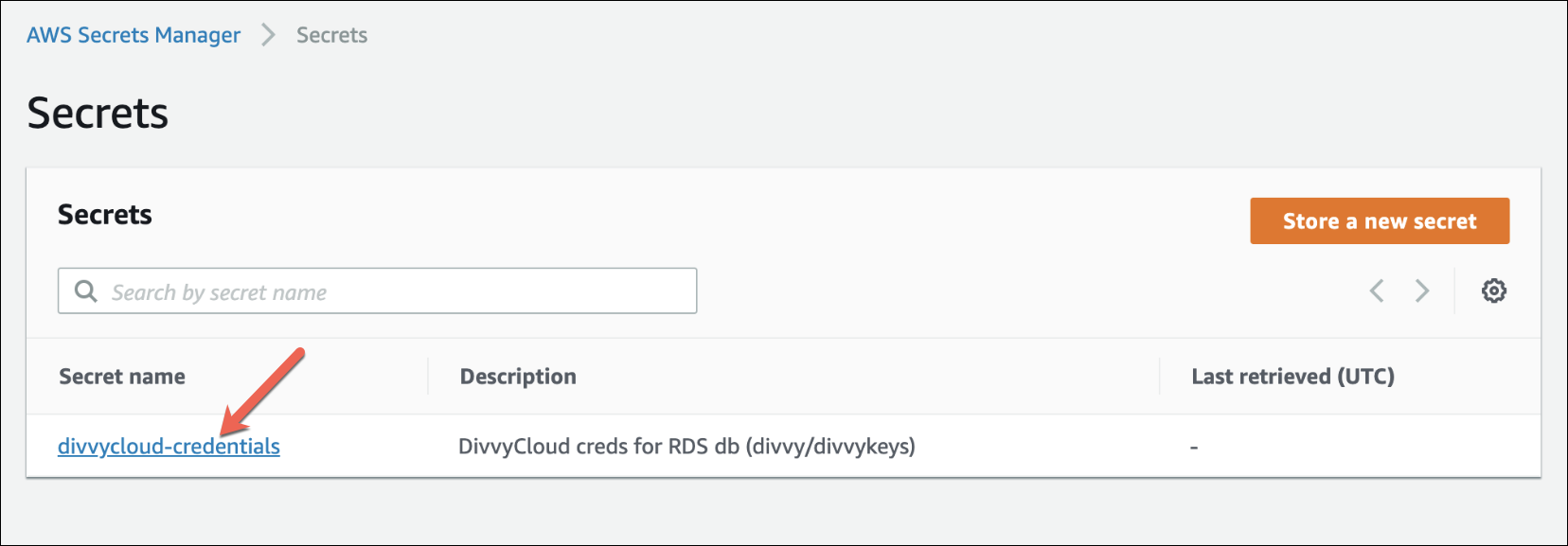
8. Add the following secret keys and values. Most of these values will be present by default; you MUST add the last one, secret_dbname with a value of divvykeys. Select “Edit” to add/change values.
usernamewith the value ofdivvypasswordwith the value of the password you specified on the databasehostwith the value of your RDS endpointportwith the value of the port you set on RDS (default 3306)dbnamewith the value ofdivvysecret_dbnamewith the value ofdivvykeys
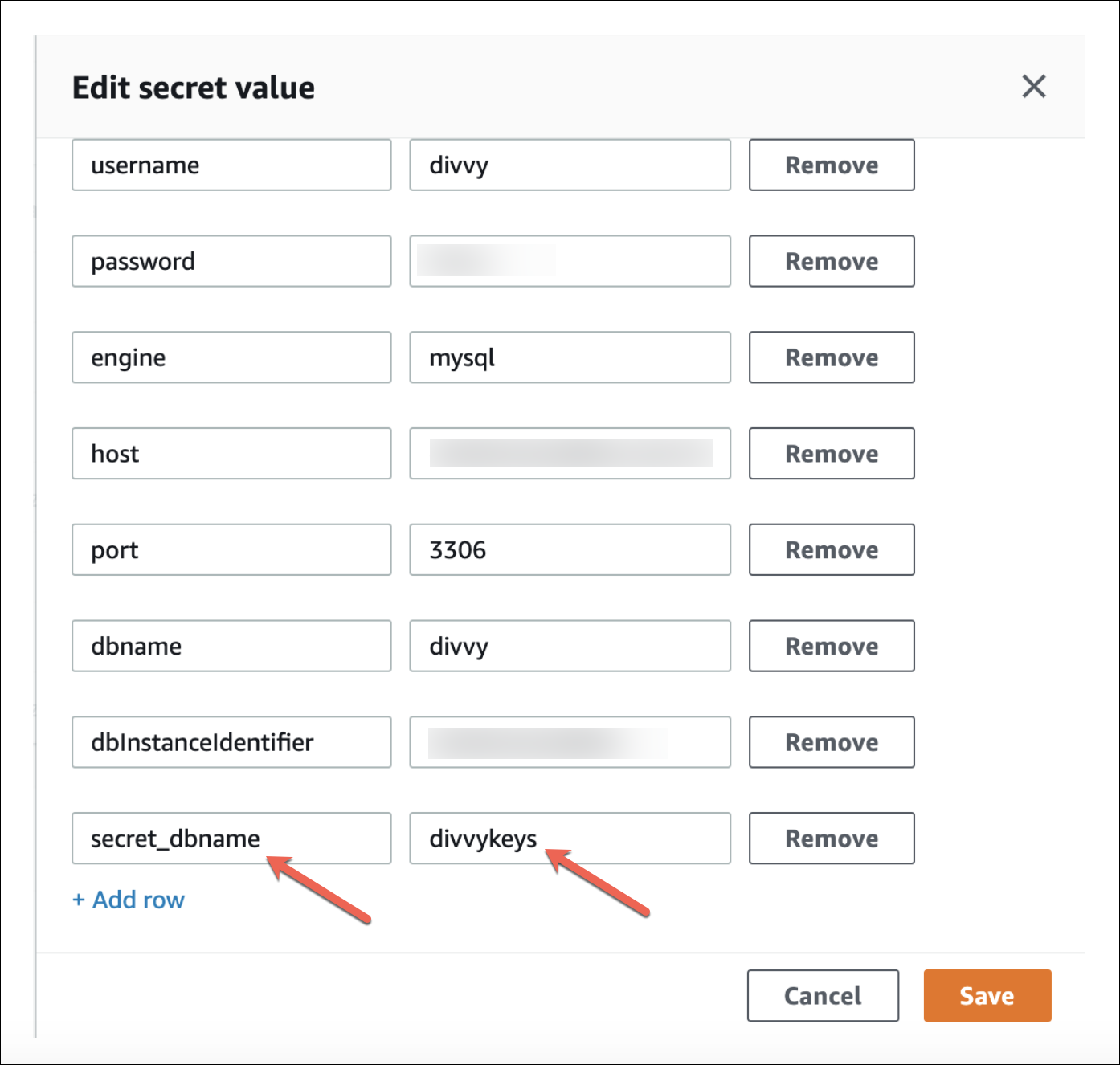
8-b. To include Redis you will need to add the following elasticache values (redis_port and redis_password are optional).
9. Modify the prod.env file on each instance.
📘 Configuring InsightCloudSec
The final step is completed outside of the AWS console. The example in the figure was completed at the local terminal. The
prod.envfiles are located in the folder in which InsightCloudSec resides.
All environment information for the Primary and Secure databases can be replaced with a single variable. Be sure to update the value of region with the region where your Secret is stored in AWS.
# MySQL 5.7 Primary database
DIVVY_SECRETS_PROVIDER_CONFIG=AWSAssumeRole,region=us-east-2,secret_name=divvycloud-credentials
# Redis
DIVVY_REDIS_HOST=divvycloud.sample.0001.use2.cache.amazonaws.com
DIVVY_REDIS_PORT=6379
# Divvy Required - do not modify
VIRTUAL_ENV=/
DIVVY_DB_NAME=divvy
DIVVY_SECRET_DB_NAME=divvykeys
# Uncomment and adjust the below values if behind a proxy. Please note that
# 169.254.169.254 are used for AWS STS AssumeRole.
# http_proxy=http://proxy.acmecorp.com:8000
# https_proxy=http://proxy.acmecorp.com:8000
# no_proxy=mysql,redis,169.254.169.254
# May be needed if proxy is performing MITM operations. This tells the local container where to expect the update to the CA bundle.
# REQUESTS_CA_BUNDLE=/etc/ssl/certs/ca-certificates.crtThe first file above prod.env is what you want to have after you update.
The original file (shown below) is an example of a prod.env that typically appears before updates (STORING THESE VALUES VIA ENVIRONMENT VALUES IS NOW DEPRECATED).
# MySQL 5.7 Primary database
DIVVY_DB_HOST=mydivvycloudrds.sample.us-east-2.rds.amazonaws.com
DIVVY_DB_PORT=3306
DIVVY_DB_USERNAME=divvy
DIVVY_DB_PASSWORD=yourpasswordhere
# MySQL 5.7 Secure database
DIVVY_SECRET_DB_HOST=mydivvycloudrds.sample.us-east-2.rds.amazonaws.com
DIVVY_SECRET_DB_PORT=3306
DIVVY_SECRET_DB_USERNAME=divvy
DIVVY_SECRET_DB_PASSWORD=yourpasswordhere
# Redis
DIVVY_REDIS_HOST=divvycloud.sample.0001.use2.cache.amazonaws.com
DIVVY_REDIS_PORT=6379
# Divvy Required - do not modify
VIRTUAL_ENV=/
DIVVY_DB_NAME=divvy
DIVVY_SECRET_DB_NAME=divvykeys
# Uncomment and adjust the below values if behind a proxy. Please note that
# 169.254.169.254 are used for AWS STS AssumeRole.
# http_proxy=http://proxy.acmecorp.com:8000
# https_proxy=http://proxy.acmecorp.com:8000
# no_proxy=mysql,redis,169.254.169.254
# May be needed if proxy is performing MITM operations. This tells the local container where to expect the update to the CA bundle.
# REQUESTS_CA_BUNDLE=/etc/ssl/certs/ca-certificates.crtIf you are storing ElastiCache Redis values in secrets manager replace the following values:
# add:
DIVVY_REDIS_SECRETS_PROVIDER_CONFIG=AWSAssumeRole,region=us-east-2,secret_name=divvycloud-credentials
# comment out:
# DIVVY_REDIS_HOST=divvycloud.sample.0001.use2.cache.amazonaws.com
# DIVVY_REDIS_PORT=6379