Threat Findings User Guide
The information on this page has moved
For the most up to date Threat Findings guidance, go to Threat Findings.
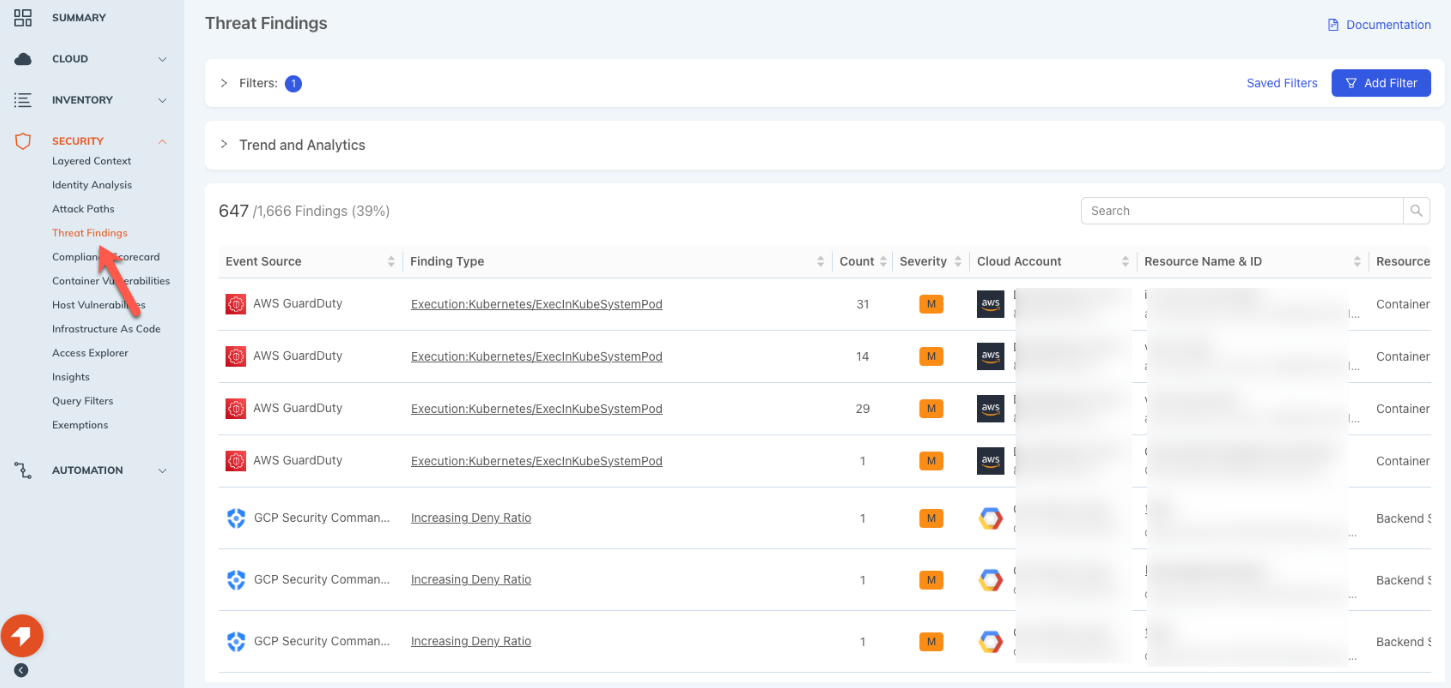
Threat Findings provides access to data visualizations (Trend and Analytics), filtering, saved filters, and a table/list display of Event Sources, Findings Types, and more.
Go to Security > Threat Findings to get started.
Filtering & Searching
Threat Findings has filtering functionality to narrow the scope of the Event Source list. The “Add Filter” button allows you to select a filter/filters that will be applied to the data displayed on the page, including the Trend and Analytics visualizations.
Filter and review threat findings
- Go to Security > Threat Findings.
- On the Threat Findings page, click Add Filter and enter your filter criteria.
- (Optional) Save the filter for repeat use. a. Click the ellipsis and select Save Filter. b. Select whether the filter if the default filter to display. c. Select whether to make the filter public. d. Click OK.
- Review the findings.
Search
Type into the search bar and the list of event sources will automatically filter to match the criteria. Updating the view of Findings and the Trend and Analytics data display.
Data Display
The main Thread Findings page displays a list of Threat Findings (with a total and percentage displayed at the top) with search, and columns for: Event Source, Finding Type, Count, Severity, Cloud Account, Resource Name & ID, Resource Type, and Last Detected.
The main Threat Findings view includes the columns Event Source, Finding Type, Count, Severity, Cloud Account, Resource Name & ID, Resource Type, and Last Seen. The view can be sorted ascending/descending on any of these columns.
| Details | Description |
|---|---|
| Event Source | Identifies the source of the Threat Finding. For this current release only third-party CSP sources are supported. |
| Finding Type | Identifies the Finding Type and links to expanded data. Clicking on the link for an individual Finding Type opens a detail pane that contains additional detail for that finding, as well as a JSON display/download option. |
| Count | Provides a count of the findings for the event source. |
| Severity | Identifies the severity of the Threat Finding (for example, High, Medium, Low). Severities are determined by data reported through the individual 3rd-party severity information. |
| Resource Name & ID | Displays the Resource Name and ID. Clicking on the individual Resource ID opens the detailed resource view. This view contains the option to download the source data as well as a tabbed view (Properties, Public Access, Insight Findings, Thread Findings, etc.) |
| Resource Type | Displays the Resource Type, for example Instance or Serviceaccesskey. |
| Last Detected | Provides the time the Threat Finding was last seen. This will vary based on when the data was last harvested. |
Threat Findings and Automation (Bots)
InsightCloudSec supports the ability to build automation around notifications through our Bot capability out-of-the-box with Threat Findings. Users can export findings to SIEM (for example, Splunk) or generate notifications for a specific scope of findings to an specific email or Slack channel. Your Bot can be scoped with two resource types associated with Threat Findings:
- The Threat Findings resource and the Resource(s) (for example, EC2 instances) on which a Threat Finding as been identified.
For more details about Bot configuration refer to our documentation on Bot Factory & Automation. In general Bots can be created in one of three ways:
- From the Bot Factory landing page via the Create Bot button
- From an Insight
- Through a template as outlined below (InsightCloudSec does not have out-of-the-box Bot templates but this section includes one example below.)
JSON Threat Findings Bot Template
{
"resource_id": "divvybot:1:1234",
"name": "Threat Findings Bot",
"description": "",
"notes": null,
"insight_id": null,
"source": null,
"insight_name": null,
"insight_severity": null,
"owner": "divvyuser:1234:",
"owner_name": "Rapid7",
"state": "RUNNING",
"date_created": "2022-12-14 11:00:15",
"date_modified": "2022-12-21 14:29:28",
"category": "Security",
"badge_scope_operator": null,
"instructions": {
"resource_types": [
"threatfinding"
],
"filters": [
{
"name": "divvy.filter.threat_finding_by_category_and_confidence",
"config": {
"confidence": [
"low",
"medium",
"high"
],
"category": [
"incident",
"anomaly"
]
}
}
],
"actions": [
{
"name": "divvy.action.send_bulk_email",
"config": {
"message_subject": "Found a threat!",
"preamble": "start",
"message_body": "{{resource.serialize(indent=2)}}",
"conclusion": "end",
"recipient_list": [
"john_smith@rapid7.com"
],
"recipient_tag_keys": [],
"walk_resource_group": false,
"recipient_badge_keys": [],
"separator": "",
"send_via_bcc": false,
"html_message": false,
"skip_duplicates": true,
"send_empty_email": false,
"replacement_strings": []
},
"run_when_result_is": true
},
{
"name": "divvy.action.mark_non_compliant",
"config": {},
"run_when_result_is": true
}
],
"groups": [
"divvyorganizationservice:1",
"divvyorganizationservice:2"
],
"badges": [],
"exclusion_badges": null,
"hookpoints": [
"divvycloud.resource.created",
"divvycloud.resource.modified"
],
"schedule": null,
"schedule_description": null
},
"valid": true,
"errors": [],
"severity": "low",
"detailed_logging": false,
"scope": [
"divvyorganizationservice:1",
"divvyorganizationservice:2"
]
}
Creating a Threat Findings Bot from a Template
Import an automation template
- In InsightCloudSec, go to Automation > Bot Factory.
- On the Templates tab, select the Import Template option.
- In the JSON window, paste the JSON automation template, provided above.
- Click Submit to verify and store the template for future use.
- Review Creating Bots for more information on next steps.