Vulnerability Management (InsightVM) Integration
The integration with Rapid7’s Vulnerability Management (InsightVM) provides Cloud Security (InsightCloudSec) with the ability to ingest vulnerability and Common Vulnerabilities and Exposures (CVE) information associated with cloud instances and identify gaps in agent deployment gaps across a company’s cloud footprint. The following use cases are possible using the Cloud Security (InsightCloudSec)/InsightVM integration:
- Identify cloud assets which do/do not have the Vulnerability Management (InsightVM) agent installed
- Leverage CVEs for added context when defining Cloud Security (InsightCloudSec) Insights/controls
- Bot automation based on the presence of specific vulnerabilities
- Risk Score Analysis
For more information check out the Vulnerability Management (InsightVM) Cloud Integration docs , or the main Vulnerability Management (InsightVM) documentation.
Prerequisites and Requirements
Before getting started you will need to have the following:
- An Organization Key from the Command Platform (Insight Platform). An Organization Administrator will need to create this key, more information on this can be found here
- The region in which your Vulnerability Management (InsightVM) Organization is configured
- Nexpose console details are optional; however, if you are interested in deleting content, you will need to include the following:
read + deregistrationpermissions within your Nexpose console- An IP address associated within Vulnerability Management (InsightVM) that is reachable by Cloud Security (InsightCloudSec)
Integration Configuration in Cloud Security (InsightCloudSec)
- To set up this integration navigate to Settings > Integrations and locate the Vulnerability Management (InsightVM) tile from your Cloud Security (InsightCloudSec) platform.
- Configure the integration as follows:
- Name: Provide a name for your Integration (Primary is the default)
- Region: Select your desired region from the drop-down. For the US-based regions, you can specify a location.
- API Key: Provide your API Key (from your desired Vulnerability Management (InsightVM) configuration)
- Console URL: Provide the URL for the Host console associated with your Vulnerability Management (InsightVM) setup (optional field — only used for asset de-registration)
- Console Username: Provide the username associated with console you specified
- Console Password: Provide the password associated with the console you specified Console access is required to effectively implement the Delete Vulnerability Management (InsightVM) Agent Bot action.
- Click Save to complete the integration setup.
Using The Integration
Once configured, the integration will harvest vulnerabilities and agent information from your Vulnerability Management (InsightVM) platform. The harvest operation runs twice a day to limit the amount of traffic and API calls generated against your platform.
The following Query Filters are available for configuration within Cloud Security (InsightCloudSec) once the integration is active:
- Instance scanned or assessed by Vulnerability Management (InsightVM) Agent Last Assessment Threshold
- Instance scanned or assessed by Vulnerability Management (InsightVM)
- Instance not scanned or assessed by Vulnerability Management (InsightVM)
- Resource Vulnerability Management (InsightVM) Risk Score
- Resource Vulnerability Count By Severity
- Resource Vulnerable To Specific Vulnerability (CVE)
- Resource Vulnerability Wildcard Search
Resources
An Agent View option is available when viewing Instances within the Resources interface. Selecting the Vulnerability Management (InsightVM) option for this displays risk and vulnerability assessment information for each instance instead of resource attributes.
If you toggle on the Vulnerability View and open the resource properties for a vulnerable resource, there will be an Vulnerability Management (InsightVM) Vulnerabilities tab available that enumerates and classifies the vulnerabilities for that resource.
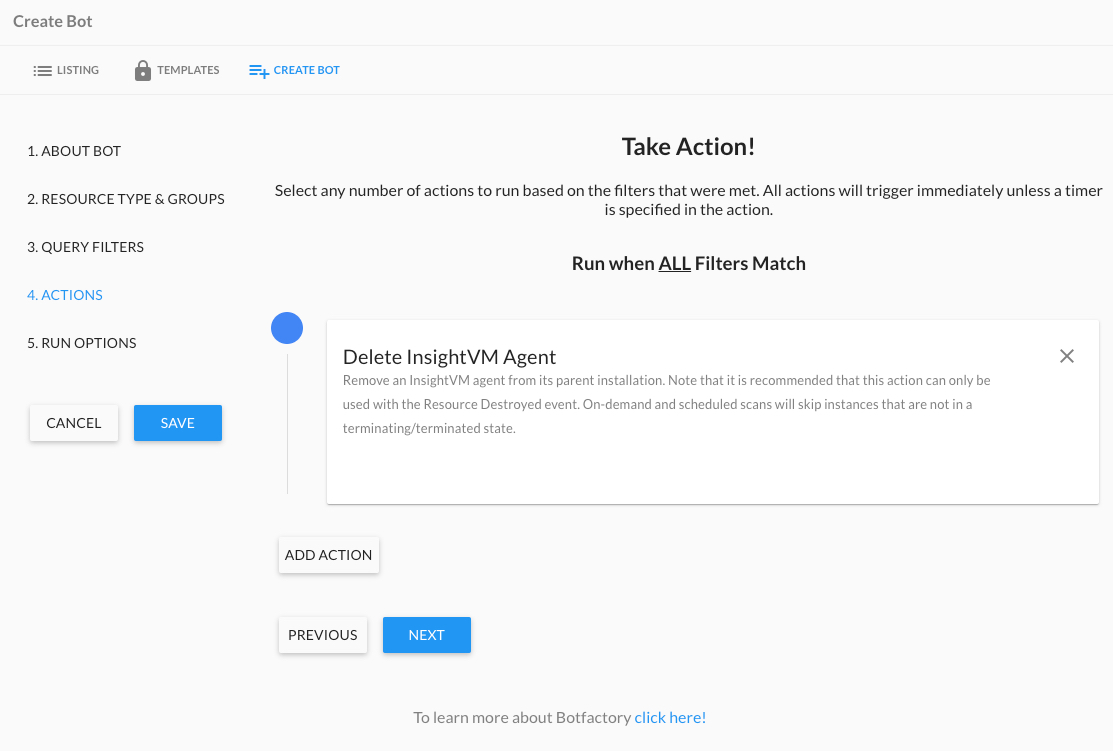
Using the Delete Vulnerability Management (InsightVM) Agent Bot Action
For Vulnerability Management (InsightVM)/InsightCloudSec integrations that include access to the console associated with the Vulnerability Management (InsightVM) integration, you have the ability to enabled a Bot Action called Delete Vulnerability Management (InsightVM) Agent.
This purpose of this Bot action is to provide Cloud Security (InsightCloudSec) users with a mechanism to force the removal of terminated instances that may be stored within Vulnerability Management (InsightVM) (data is retained for 7 days) and removes an Vulnerability Management (InsightVM) agent from its parent installation.
Some other items to note:
- It is recommended that this action can only be used with the Resource Destroyed event.
- On-demand and scheduled scans will skip instances that are not in a terminating/terminated state.
For general details on working with automation, check out our Bot Factory & Automation documentation.
Setting up the Delete Vulnerability Management (InsightVM) Agent Bot
- Navigate to Automation > Bot Factory
- Click Create Bot to launch the Bot creation process.
- Provide a name, description, and category for your Bot and click Next.
- Under Resource Types, select Instance (this is the only resource this Bot action applies to), select any applicable badges, and select your target cloud account(s), click Next.
- Provide your desired Query Filter (for example, “Always Match”) and then locate and select the Delete Vulnerability Management (InsightVM) Agent Bot action and select this action.
- Under the Run Options, we recommend selecting the Resource Destroyed option under Reactive.
- Click Save to complete the setup of your Bot.
Jinja2 Reporting
Once data has been imported from Vulnerability Management (InsightVM), you can use Jinja2 templates in your Bot Actions to send detailed reports about your resources and any detected vulnerabilities. More details on the available attributes can be found in the Compute Resources documentation for Instances.