Learn About Cloud Vulnerability Management (VM)
The Cloud VM feature, also known as Vulnerabilities, helps you efficiently view, prioritize, and orchestrate the response to CVEs detected in the host instances and containers across your cloud environment. This feature is composed of two distinct vulnerability management groups: hosts (using instances) and containers (using images). These groups are assessed and managed differently behind the scenes:
- Host Vulnerability Assessment (HVA): Hosts are assessed when they are detected by the InsightCloudSec without the use of traditional network scanning or an embedded agent. Using snapshots of the instances’ root volume, a thorough vulnerability assessment is performed on all packages in the guest operating system and installed software, on Open Source Software (OSS) dependencies, and on select file types. The snapshots are downloaded to your InsightCloudSec instance, their package inventory is assessed, stored, and then promptly deleted. The host instance inventory is continuously monitored for new vulnerabilities as long as they remain active in your cloud. Select changes to the host instance in the cloud will automatically trigger a fresh snapshot and assessment. Remediations are detected and recognized whether by host instance updates or removals and replacements by updating the base image (e.g., AMI) and relaunching.
- Container Vulnerability Assessment (CVA): Container image IDs and SHA-256 hash digests are harvested from your configured cloud accounts, Kubernetes clusters, and container registries. The package inventory and vulnerabilities detected on each image are presented in the InsightCloudSec platform for review, prioritization, and response. Users can determine and evaluate the riskiest resources by focusing on business segments such as deployed workloads and applications. CVA also analyzes the configured Workload (Workload Definition) used while instantiating a new workload instance.
Configuration
InsightCloudSec requires separate configuration to manage host and container vulnerabilities. For more information on support, installation prerequisites, and configuration details, review the following pages:
Frequently Asked Questions (FAQ)
The following sections highlight the most frequently asked questions about the Cloud VM feature. If you do not see your question here, contact Support or your Customer Success representative.
General
The questions in this section apply to the Cloud VM feature in general.
Why does InsightCloudSec require special permissions to assess vulnerabilities?
Agentless assessment requires that InsightCloudSec has a way to scan a host or image without running anything in your cloud environment. InsightCloudSec ensures that we recommend only the minimal possible permissions for completing assessments of your hosts or containers. See Configuring Host Vulnerability Assessment (HVA) or Configuring Container Vulnerability Assessment (CVA) for more information on setting up your cloud environments for assessments of hosts or containers, respectively.
How do I review the vulnerabilities assessed by InsightCloudSec?
All assessed vulnerabilities are contained within the unified vulnerability dashboard (Security > Vulnerabilities in the InsightCloudSec navigation menu). See Reviewing and Managing Vulnerabilities for details.
How is the Active Risk score calculated?
The Active Risk score rating in InsightCloudSec uses a variety of factors to determine the rating of a vulnerability. Threat Feeds, Exploit Databases, and the vulnerability CVSS score are combined to produce a Risk Score to help prioritize vulnerabilities. When viewing the risk score for a vulnerability there are details about the reason for the score produced: vulnerabilities with published exploits and vulnerabilities that threat feeds have marked as actively exploited will have scores that are higher than other vulnerabilities within the product that have similar CVSS scores.
For example, CVE-2022-0318 has a CVSS score of 9.8. This vulnerability is not actively exploited and does not have published exploits. This vulnerability has a risk score of 810 (if there are threats and/or exploits published in the future this risk score will change accordingly). On the other hand CVE-2020-15999 has a CVSS score of 6.5 and is a known exploited vulnerability according to the CISA KEV Catalog. The active exploitation of the vulnerability raises the risk score to 1000. This calculation enables you to quickly identify vulnerabilities that need to be addressed in order to reduce the risk of your cloud environment.
HVA
The questions in this section apply to HVA.
What does a typical workflow look like for HVA?
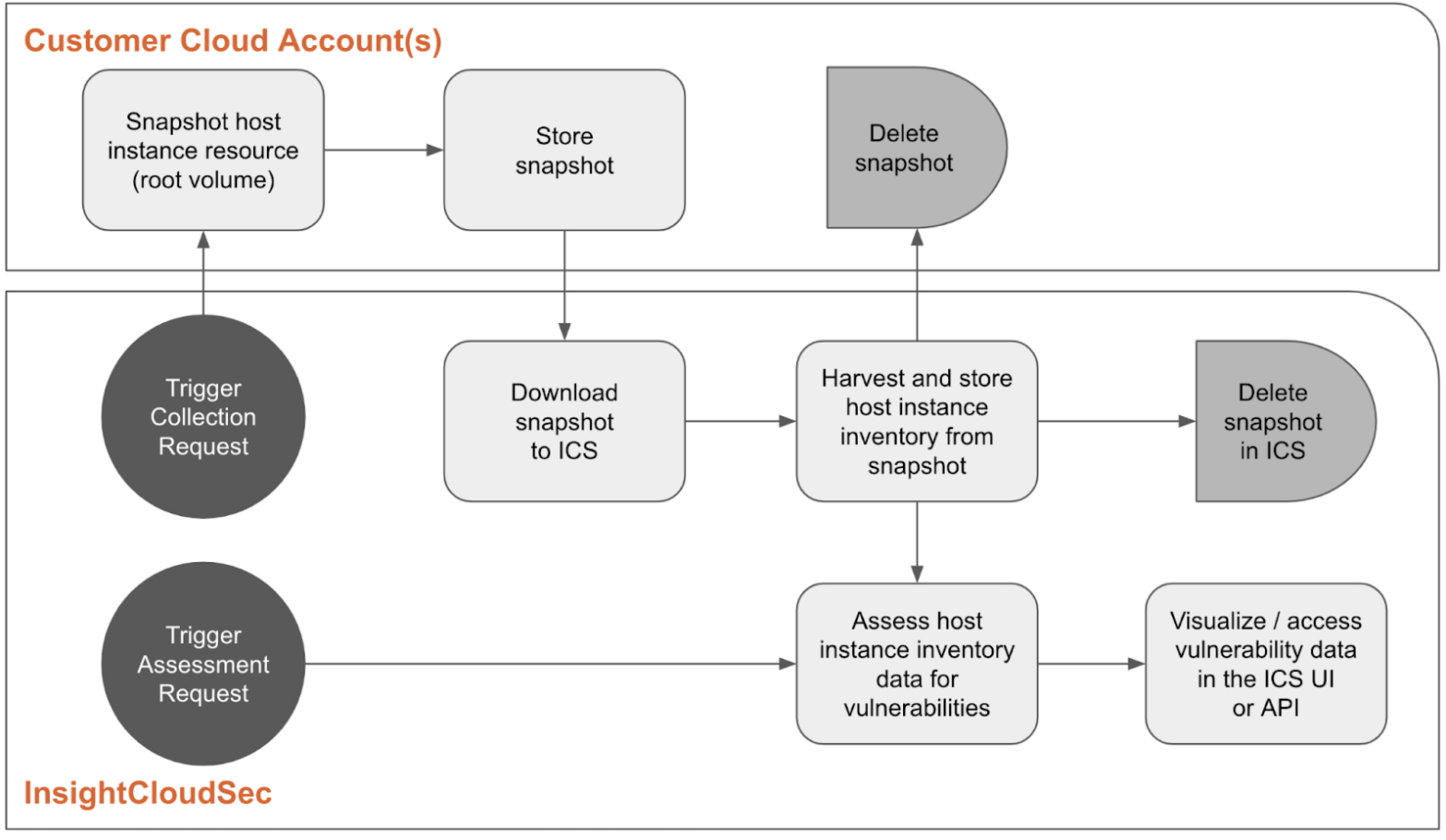
The following workflows gather and store the inventory from the host instances harvested by InsightCloudSec and assess them for vulnerabilities. Host instances are discovered and harvested based on your Assessment Scope. They also continuously monitor and refresh the inventory and vulnerability data based on changes to the instances and for newly disclosed vulnerabilities.
As InsightCloudSec harvesting discovers new host instances, HVA triggers the collection step, which creates and downloads a snapshot of the instance from a customer's cloud account to InsightCloudSec (explore Configuring Host Vulnerability Assessment (HVA) for snapshot size limitations). When HVA is initialized, all host instances already harvested are treated as new, triggering the first collection. The snapshot is then assessed for vulnerabilities in InsightCloudSec and its inventory (versions of the operating system and software packages, OSS dependencies, and other select file types) is saved. InsightCloudSec discards the snapshot once the assessment is complete.
Existing host instances are reassessed and potentially recollected based on the following triggers.
- Automated recollection - a proprietary algorithm determines the need to collect a new snapshot using environmental events indicating the instance changed since the last collection
- Automated reassessment - when new vulnerabilities are reported, InsightCloudSec reviews the host instance inventory and reassesses those with the imaged packages
- Manual recollection and reassessment - you can trigger a recollection and reassessment of a specific host instance using an action in the InsightCloudSec console or an API call
When do host assessments occur and how do I know they are completing successfully?
Assuming you have completed the onboarding process successfully and fully configured HVA, hosts will begin appearing in the Vulnerabilities dashboard with regularly scheduled harvesting. Assessments occur as soon as a new host is discovered in InsightCloudSec. If the dashboard is not updating as you would expect, host assessment status can be found on the Vulnerability Settings page.
What is the frequency of snapshots being created and then deleted?
Snapshots are created:
- When a new host is discovered
- When a new vulnerability is discovered
- When you manually trigger an assessment
What regions do you assess host vulnerabilities in?
Regional assessments are currently only supported for AWS and Azure.
For AWS:
We support the following AWS regions: us-east-1, us-east-2, us-west-2, eu-central-1, ap-northeast-1, ap-southeast-2, and ca-central-1. Any resources located outside of the supported regions will be mapped to a supported region. If a mapping does not exist, the assessment will be sent to us-east-1 by default.
For Azure:
We support all Azure regions and will attempt to map to the closest supported AWS region for assessments. If there is no mapping available, then we will perform the assessment in AWS us-east-1.
Default region mapping can be overridden
You can override the default region mapping from the HVA settings page. Explore In-region Assessment Mapping for details.
Can you assess host vulnerabilities using AWS default key-encrypted snapshots?
Snapshots taken of an AWS instance that uses the default AWS-managed key will automatically have the same encryption. This encryption method cannot be changed and these snapshots cannot be directly shared or accessed. As a workaround, InsightCloudSec automatically copies and encrypts default key-encrypted snapshots using the Rapid7 customer-managed key. This key is stored and managed internally by Rapid7. For this process, a grant is created for the Rapid7 key with the AWS cloud account's role ARN as the grantee and retiring principal. This key grant applies the permission to use the Rapid7 key to copy and encrypt their snapshots and then retire the grant after the assessment is completed.
Limitations:
- This feature is currently only enabled for AWS instances in the following regions:
ap-northeast-1ap-southeast-2ca-central-1eu-central-1us-east-1us-east-2us-west-2
- Assessments for default key-encrypted instances in all other regions will fail with the
DefaultEbsKeyExceptionexception. - Each customer managed key can have up to 50,000 grants. However, it’s unlikely that this quota will be reached since the grants are retired after assessments are complete. See the AWS Documentation for more information.
What if InsightVM is assessing the same host using the Rapid7 Agent?
You don’t need to remove the InsightVM agent. InsightCloudSec Vulnerability Management will snapshot instances with an existing agent and conduct the collection and assessment with no issues. Most vulnerabilities will be reported identically between the two; however, InsightCloudSec has a larger scope of detection and may report more vulnerabilities than InsightVM. This allows time to evaluate the new feature before removing the agent and transitioning Host instance vulnerability management from InsightVM to InsightCloudSec.
CVA
The questions in this section apply to CVA.
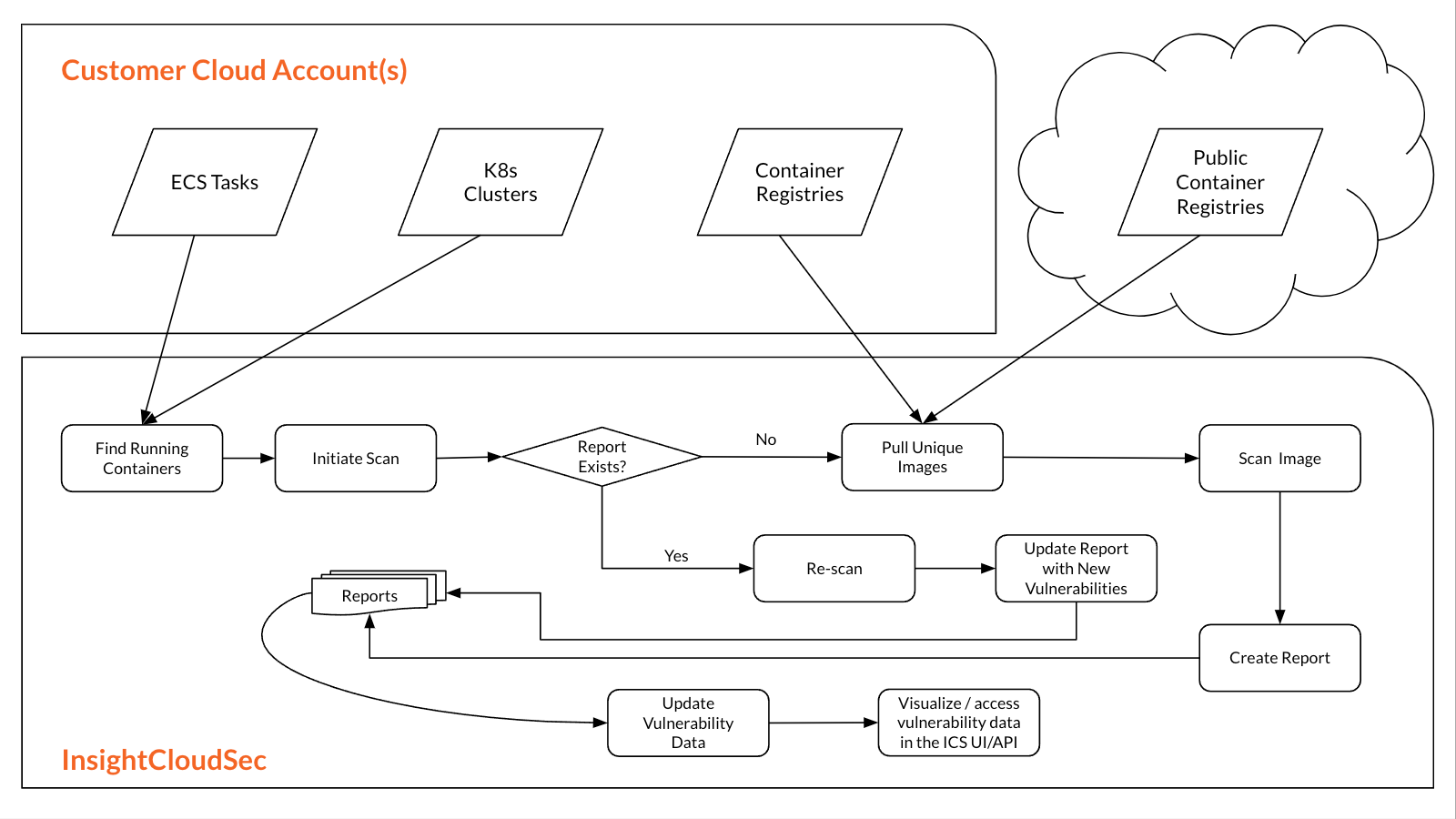
What does a typical workflow look like for CVA?
After you have onboarded Cloud accounts and Kubernetes clusters or associated container repositories with InsightCloudSec, the platform will automatically scan container images (all layers) and workloads for vulnerabilities with regularly scheduled harvesting. Each container-related resource (ECS Task Definition, Kubernetes ReplicaSet, etc.) identified by InsightCloudSec will have an Image ID and SHA-256 hash (or manifest digest) associated with it. Each image or artifact, whether tagged or not, is identified by its digest. The digest value is unique even if the artifact's layer data is identical to that of another artifact. InsightCloudSec regularly updates the Vulnerabilities feature to match the state of the resources in your cloud environments. Once InsightCloudSec has harvested a particular SHA-256 digest, everything that is needed to track vulnerabilities over time is captured and stored.
When do image assessments occur and how do I know they are completing successfully?
Assuming you have completed the onboarding process successfully and fully configured CVA, images will begin appearing in the Vulnerabilities dashboard with regularly scheduled harvesting. Assessments occur as soon as a new image (layer) is discovered in InsightCloudSec. Any image that is on an account that is not visible to InsightCloudSec will not be scanned. If the dashboard is not updating as you would expect, there are two locations to begin your troubleshooting:
Container visibility issues are tracked on the Kubernetes Clusters page.
Image assessment status is surfaced on an image-by-image basis in the Security > Vulnerabilities > Resources table. If there was an issue assessing an image, a red icon will denote the particular issue. The following table includes details on the errors:
Error Troubleshooting Unable to pull an image with this name and digest.Contact support. Unable to assess an image with this name and digest.Contact support. Unable to pull this image due to its size. It is larger than our maximum supported size of 10GB.We do not support image scanning for images larger than 10GB. Anything related to authentication or insufficient permissions, credentials, or logging in Ensure that the harvesting role you set up during onboarding has the required permissions as described in Configuring CVA. Unable to pull an image with this name and digest. The image's tag may have been rewritten to use a different digest.This error often occurs in containers running EKS Add-Ons. Amazon frequently removes old versions of images from these repositories. Work with the application or infrastructure team to ensure that Add-Ons are updated frequently. If this image is owned by your organization, work with the infrastructure or application team that owns the container to ensure this container is re-provisioned to use a new version of the image in the near future. Unable to pull an image from this registry due to rate limiting.Wait. InsightCloudSec will automatically reschedule an assessment as appropriate. Unable to pull an image from this registry. This registry is not supported.We do not support this particular private registry (see Configuring CVA for full support details). If this is a public registry, contact support and we can add this registry to our allowlist. Unable to assess this image. The scan timed out.If this issue persists, contact support. This error can happen repeatedly if an image is too large.
What image registries do you support?
A full list of supported images registries can be found on the CVA Configuration page. Note, however, that images hosted in publicly-accessible, unauthenticated registries are subject to rate limiting. Thus, we cannot guarantee full visibility into the vulnerabilities for these images at this time.
Does CVA support container images within Kubernetes clusters?
Yes! CVA can assess container images within Kubernetes clusters using the Kubernetes Scanner. Review the Kubernetes Scanners Overview for more details.