About Post-Exploitation
Post-exploitation refers to any actions taken after a session is opened. A session is an open shell from a successful exploit or bruteforce attack. A shell can be a standard shell or Meterpreter. To learn more about the difference between each, see Manage Meterpreter and Shell Sessions.
Some of the actions you can take in an open session include:
- Collect System Information
- Pivot
- Run Meterpreter Modules
- Search the File System
Get a Session
You can get a new session by running a successful bruteforce attack , exploit , or social engineering campaign . A session opens a connection to the target host.
Bruteforce Attack
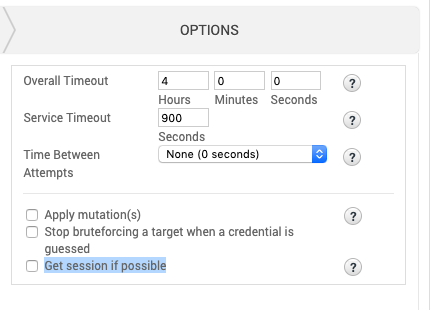
A session will be opened during a bruteforce attack if the option is selected during configuration. Go to **Credentials > Bruteforce, **then under “Options”, and check “Get session if possible”.
Exploit
To get a session with an exploit, you can use either an automated or manual exploit. Metasploit will automatically try to open a Meterpreter session for successful exploits. This setting can be changed under Connection Type when configuring an exploit.

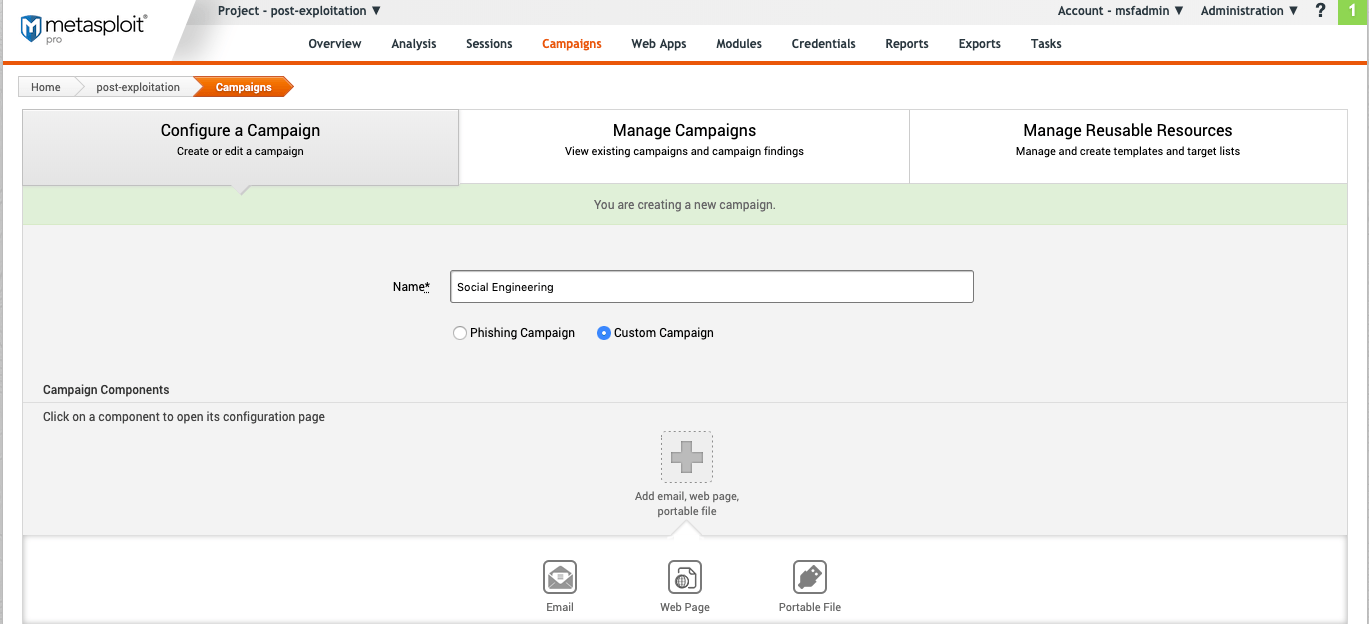
Social Engineering
A session will open on the target user’s computer if the campaign is configured to deliver a file. Once a target user clicks on the file, the listener will open a session on their computer.
To see all available options, go to “Campaigns” and select **Custom Campaign. **From there, select the attack you want to run: Email, “Web Page”, or “Portable File”.
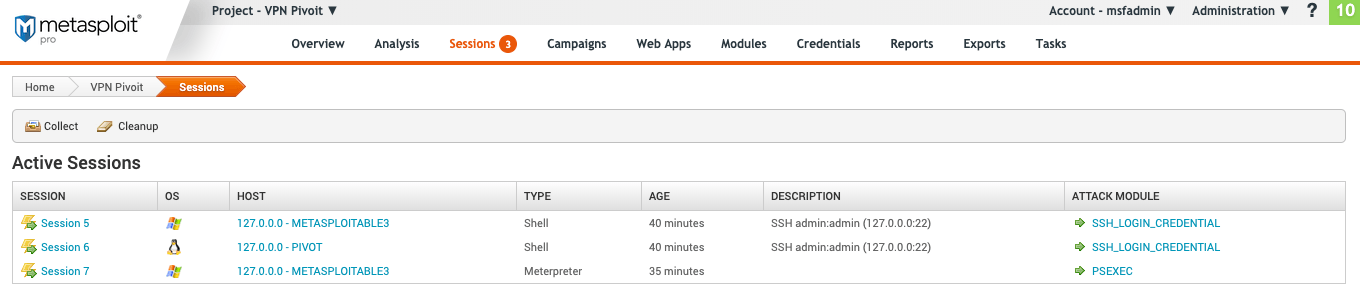
Find Open Sessions
If you have already run a successful attack on a target host, you will find any active and closed sessions under “Sessions” in the top menu.