Audit Report
The Audit Report presents the comprehensive findings for a project. It is useful when you want to obtain a detailed look at targeted hosts in a project. The report data is divided into two sections: Major Findings and Detailed Findings.
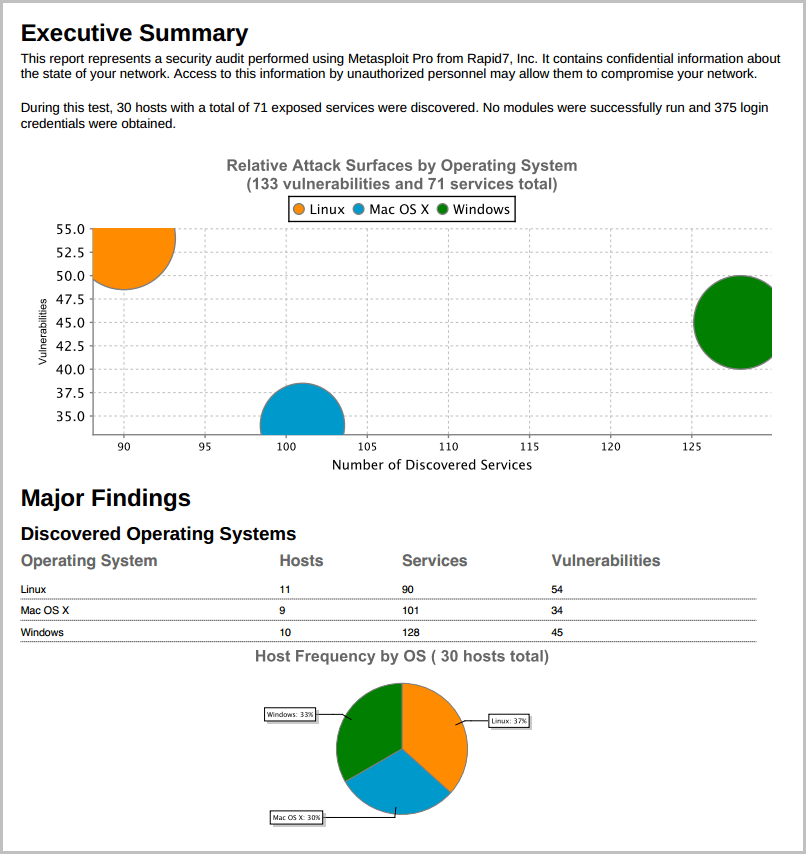
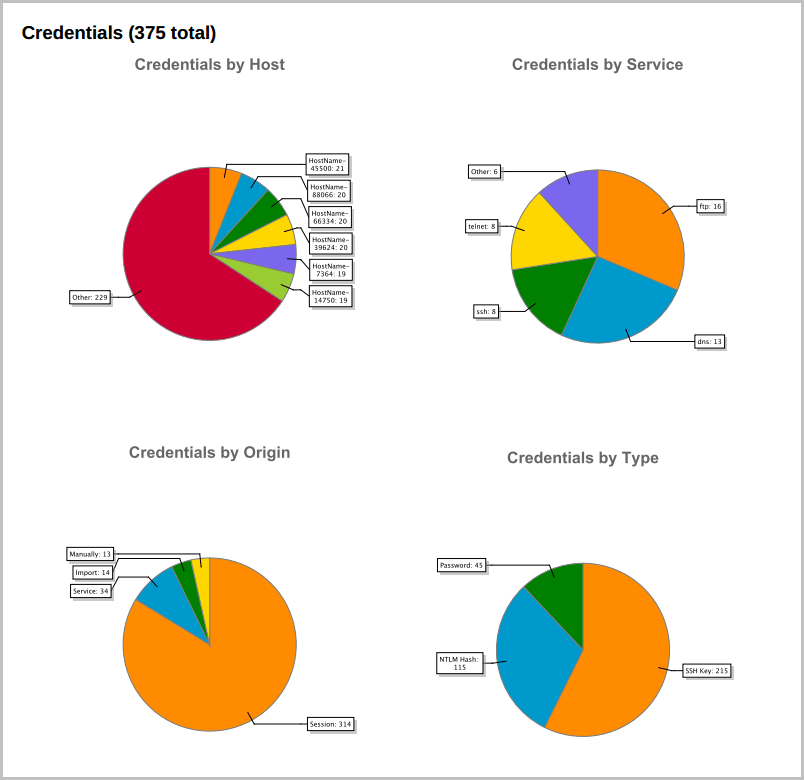
Major Findings The Major Findings section presents host, operating system, and compromised credential data through tables and graphs. Its purpose is to help you quickly summarize and identify important data points in the report.
The Major Findings section includes the following data:
-
The potential attack surface based on the number of discovered vulnerabilities and services per operating system.
-
A breakdown of the host, service, and vulnerability counts for each operating system.
-
The IP address, name, operating system, service count, and vulnerability count for each host in the project.
-
The public and private values, realm type, realm value, origin, host count, and service count for each type of credential found in the project. All credentials are grouped according to their type. A credential can be a plaintext password, NTLM hash, non-replayable hash, or SSH key.
-
A statistical breakdown of credentials by host, origin, service, and type. Detailed Findings The Detailed Findings section provides granular details for each host in the project. It includes the following data:
-
The host names and IP addresses of all the targets in the project.
-
The details of the credentials stored in the project, such as their public (username), private (password), realm type, realm value, and origin.
-
The open services that were discovered on each host.
-
The vulnerabilities that were discovered on each host.
-
The web vulnerabilities that were discovered on each host.
-
The modules that were able to successfully exploit a vulnerability and open a session.
-
The activity for each session, such as when it was opened and closed and the commands that were run during the session. Audit Report Options
| Settings | Options |
|---|---|
| Output formats | PDF, HTML, WORD, RTF |
| Report options | Mask discovered credentials - Removes all credentials, including plain text passwords, hashes, and SSH keys, from the report. The Audit report will display the user name with a blank password. Include session details - Shows the details for each session was able to open, such as the session type and attack module that used to obtain the session. Include charts and graphs - Includes visual aids, such as pie graphs, to accompany statistical findings in the report. |
| Report sections | Executive Summary Compromised Hosts Credentials Discovered OSes Discovered Hosts Host Details Discovered Services Web Sites |