Credentials Domino MetaModule
The Credentials Domino MetaModule enables you to determine how far an attacker can get in a network if they are able to obtain a particular credential. It is performs an iterative credentials-based attack to identify the attack routes that are possible if a session is obtained or a credential is captured from a particular host. Its purpose is to help you gauge the impact of a credentials-based attack by reporting the number of hosts that can be compromised and the number of unique credentials can be captured by leveraging a particular credential.
In order to run the Credentials Domino MetaModule, the project must have at least one valid login or one open session that you can use as the starting point. As previously mentioned, the Credentials Domino MetaModule performs an iterative attack, which means that it repeatedly cycles through the network and attempts to authenticate to each host with a particular credential. Each iteration represents a single cycle through a network with a different credential. The Credentials Domino MetaModule continues to run until it opens a session on every target host or it reaches a termination condition.
During the first iteration, if you choose to start with a valid login, the Credentials Domino MetaModule immediately tries to use it to authenticate to and open a session on each target host. If the Credentials Domino MetaModule is able successfully authenticate and open a session, it captures the credentials from the host and stores them in the project. Once the MetaModule has successfully opened a session on a host, it will not try the host again. However, if you choose to start with an open session, the MetaModule begins by collecting credentials from the session. Then, it tries each looted credential until it is able to find a successful login. The MetaModule uses the successful credential to start the next iteration.
To help you see how the network is impacted, the MetaModule includes a specialized report that documents the technical findings and results from the attack. It also presents real-time results for compromised hosts and captured credentials through the findings window and presents a visualization of the attack patterns that it was able to establish from the target network. Accessing the Credentials Domino MetaModule You can access the Credentials Domino MetaModule from the MetaModules page. To access the MetaModules page, select Modules > MetaModules from the Project tab bar. Find the Credentials Domino MetaModule and click the Launch button.
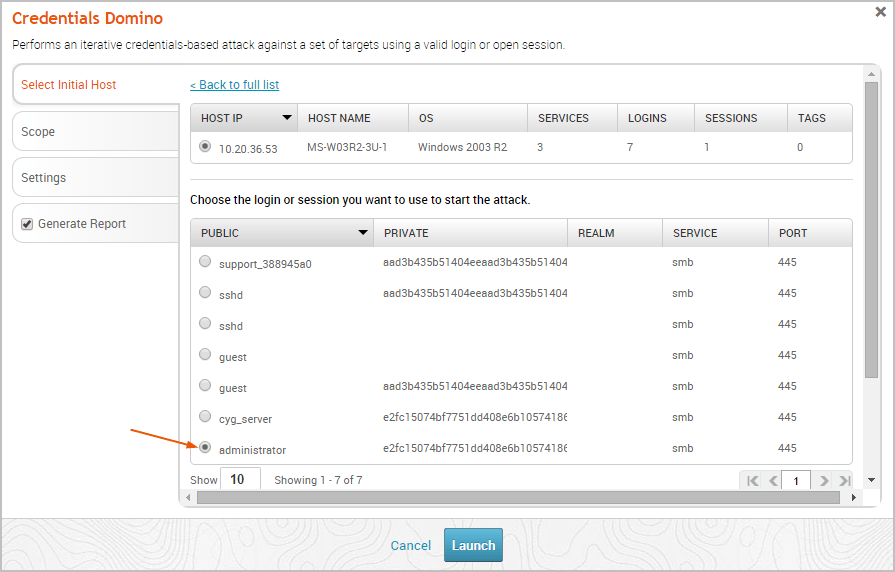
The Credentials Domino MetaModule configuration window appears with the Select Initial Host configuration form displayed. Each configuration step is divided into separate tabs, so you can click on any of the tabs to switch between the different configuration forms. Selecting the Initial Host The first thing you need to do when you configure the Credentials Domino MetaModule is select the host that has the login or session you want to use. From the Select Initial Host tab, you can see a list of all hosts in the project that either have valid logins or open sessions.
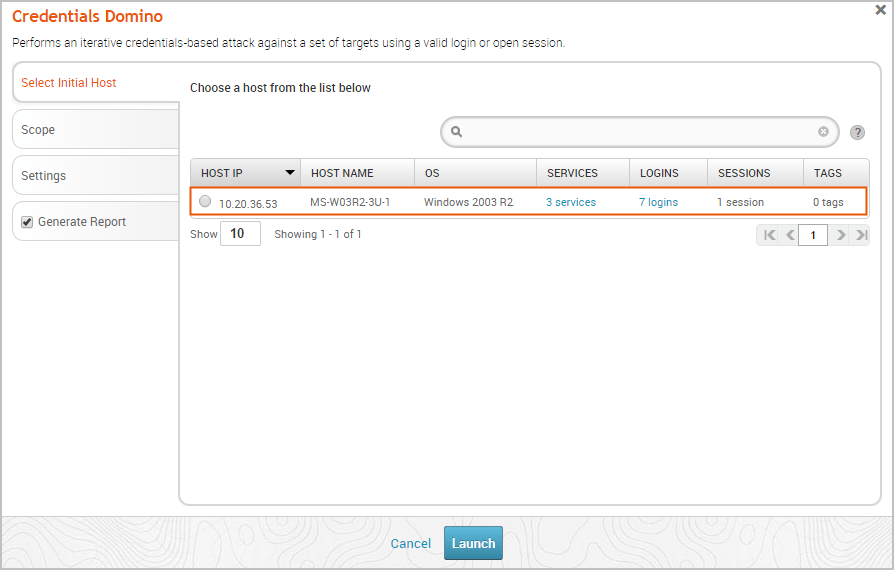
Select the host that you want the MetaModule to use. The login and session details for the host appears after you select a host.
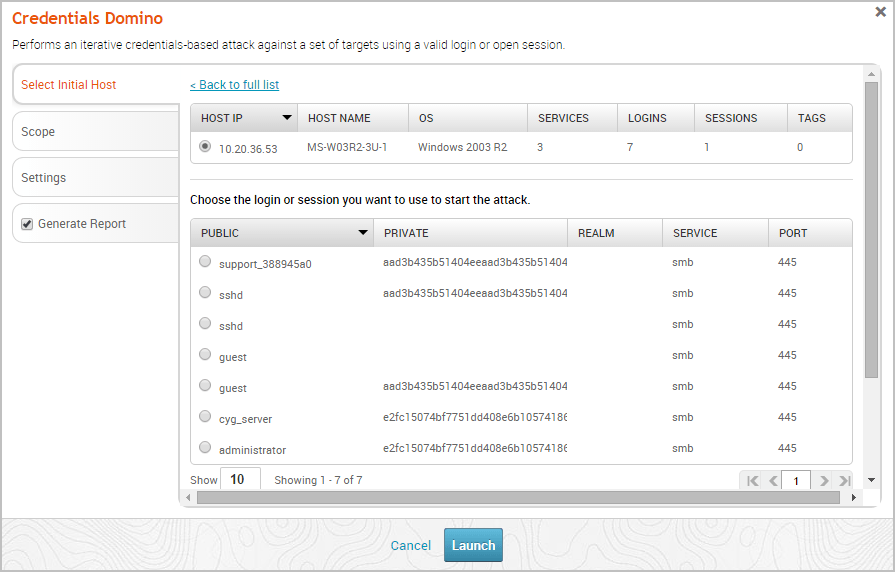
Choose the login or session that you want the MetaModule to use to start the attack.
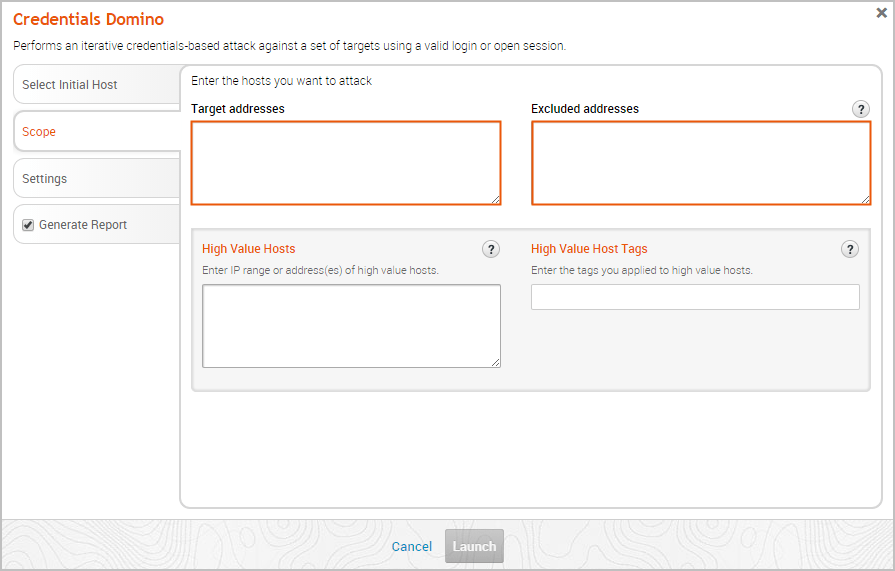
Defining the Scope The scope identifies the hosts that you want the MetaModule to target during the attack. To define the scope, you use the Target addresses and Excluded addresses fields.
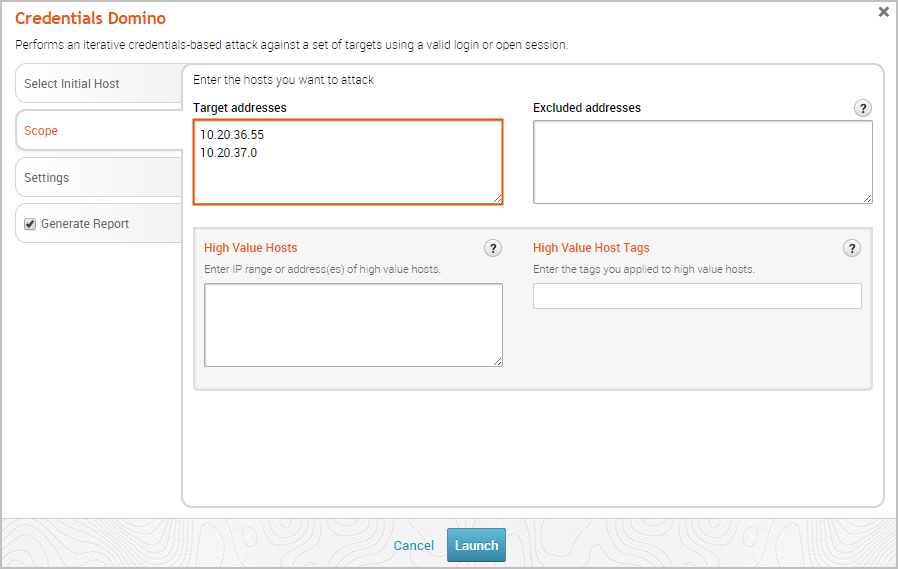
If there are specific hosts that you want to attack, you can enter them in the Target addresses field. You can enter a single address (192.168.1.1), a range (192.168.1.1-192.168.1.100), a CIDR notation (192.168.1.0/24), or a wildcard (192.168.1.*). You must use a newline to separate each entry. If you want to include all hosts in the project, you can leave this field empty.
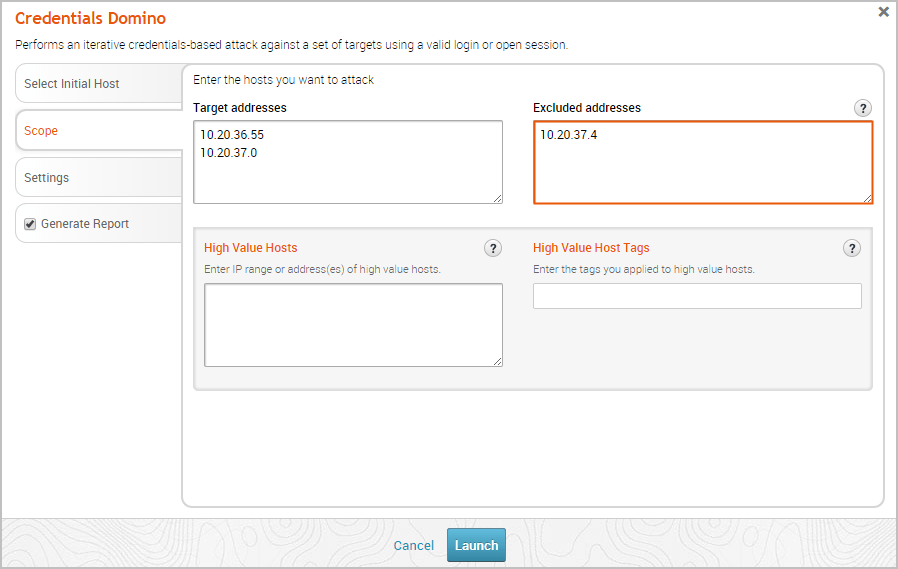
If there are specific hosts that you want to exclude from the attack, you can enter them in the Excluded addresses field. Again, you can specify an address range, a CIDR notation, a comma separated list of host addresses, or a single host address.
Designating High Value Hosts A High Value Host is a designation that you assign to a host that you want to highlight on the Credentials Domino Findings window and in the Credentials Domino MetaModule Report. The High Value Host designation helps you quickly identify the impact of a particular stolen credential pair against critical hosts. A High Value Host designation indicates that the host is of significant importance to an organization, and any attack against the host could negatively impact business operations. For example, domain controllers and servers that contain sensitive financial information may be considered as High Value Hosts.
All High Value Hosts will be highlighted in orange on the Findings window, as shown below in the visualization graph:
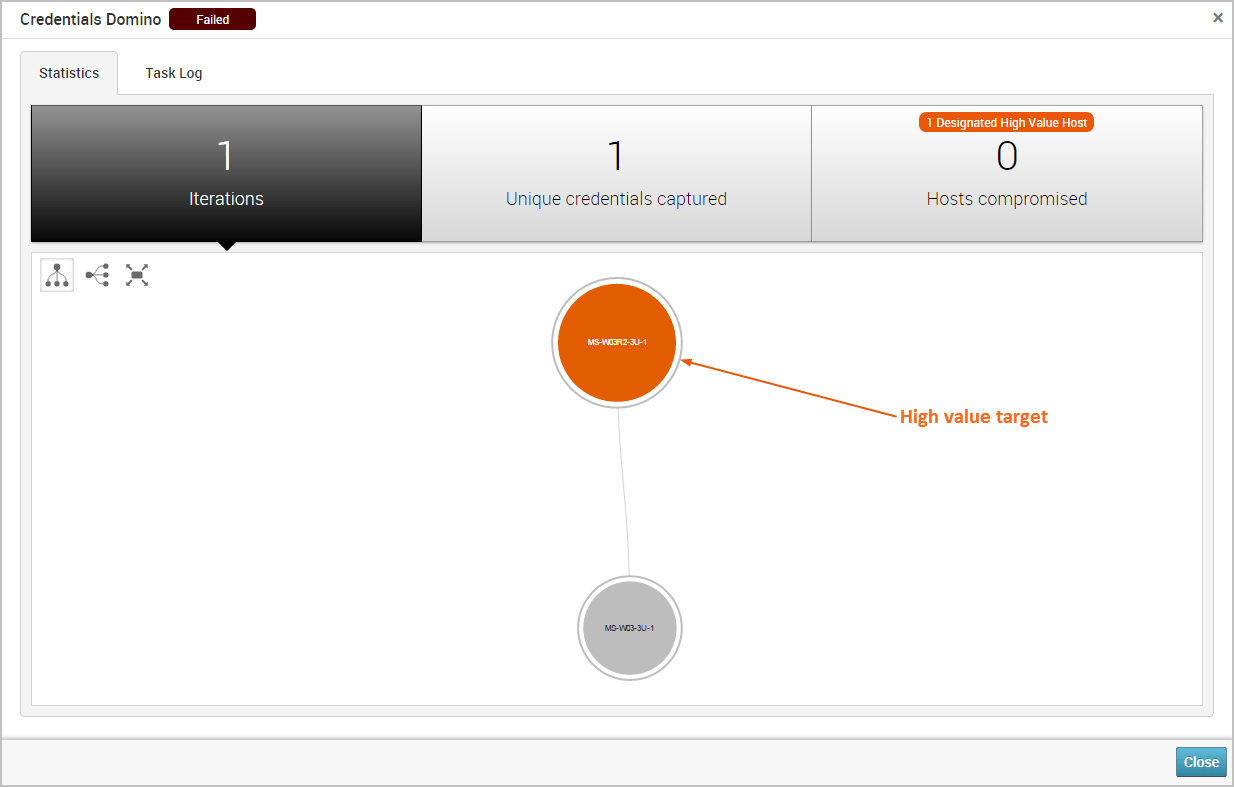
There are a couple of ways you can designate a host as a high value host:
- You can apply host tags - You can apply tags to the hosts that are critical to an organization, which enables you to track, group, and report on hosts according to how they impact an organization. Tags enable you to view and filter hosts at the project level.
For example, you may want to tag all accounting servers with a label like accounting. You may also want to want to create and apply criticality tags, such as High, Medium, and Low, to isolate hosts based on their criticality levels.
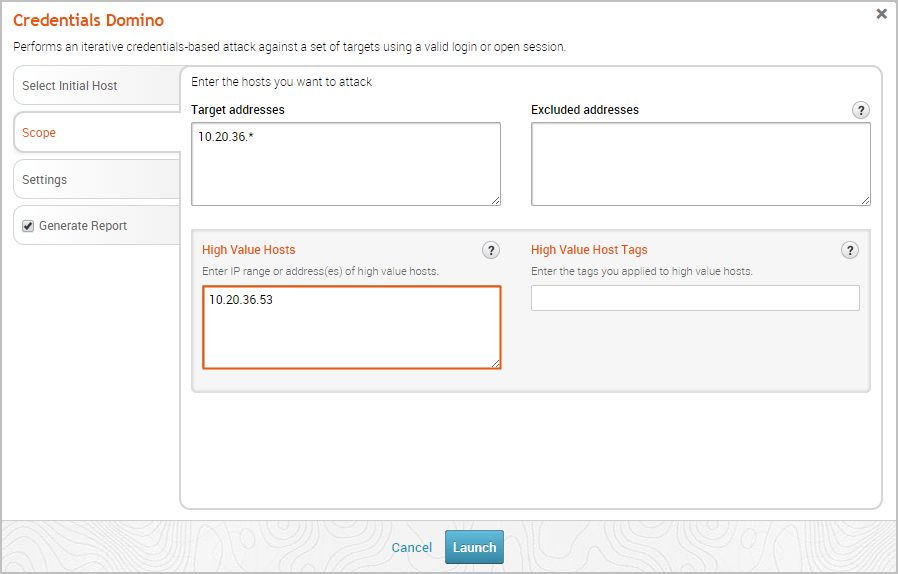
- You can specify high value hosts from the Credentials Domino MetaModule - You can also designate high value hosts by their addresses. You can enter an address range, a single address, or a new line separated list of addresses.
For example, if you know the IP address for a particular host that is of special interest to you, you can specify it when configuring the scope for the Credentials Domino MetaModule. Use this method if you want to manually define the hosts you want to designate as High Value Hosts and do not want to use tags.
Configuring Payload Settings You can specify the payload that you want the Credentials Domino MetaModule to deliver during the attack. To configure the payload settings, you can use the following options, which are located on the Settings tab:
Payload type
This option determines the type of payload that the MetaModule delivers to the target. You can choose one of the following options:
- Meterpreter - This payload provides an advanced interactive shell that provides extensive post-exploitation capabilities that enable you to do things like escalate privileges, dump password hashes, take screenshots, launch and migrate processes, and upload files to the target. Meterpreter also includes command shell capabilities for basic tasks like adding a user account or running a script.
Meterpreter dynamically loads itself into an existing process on the target host using a technique called reflective DLL injection, which enables it to reside entirely in memory and remain undetected by intrusion prevention and intrusion detection systems.
- Command - This payload provides a command shell that you can use to run single commands on a host to perform simple tasks like adding a user account or changing a password. A command shell provides limited capabilities, but can be later upgraded to a Meterpreter shell for more options.
Unlike Meterpreter, a command shell can start a new process that can be easily detected by intrusion prevention and intrusion detection systems.
Connection
This option determines how your Metasploit instance connects to the host. You can choose one of the following options:
- Auto - This connection type uses a reverse connection when NAT or a firewall is detected; otherwise, it uses bind connection.
- Bind - This connection type uses a bind connection. You should use this connection type if there is a direct, unrestricted connection to the target host.
- Reverse - This connection type uses a reverse connection. You should select this connection type if the hosts are behind a firewall or a NAT gateway that will prevent requests from your Metasploit instance to the target.
Listener ports
This option defines the ports that the listener uses to wait for incoming connections. You can specify a specific port, a comma separated list of ports, or a port range. If you enter a port range, the first available open port is chosen from the range.
Listener host
This option defines the IP address the target host connects back to. This is typically going to be the external IP address of your local machine. If you do not specify a listener host, the MetaModule automatically uses the external IP address of your local machine.
Clean up sessions
This option enables you to close all open sessions after the MetaModule finishes. By default, this option is enabled. If you want to keep the sessions open, deselect this option. Setting Termination Conditions You can control the number of times that the Credentials Domino MetaModule cycles through a target network by setting iteration and timeout controls. If you do not set iteration or timeout conditions, the Credentials Domino MetaModule will run until it exhausts all credential and host combinations. Depending on the scope of the attack and the number of credentials captured, the attack can go through a large number of iterations.
To set termination conditions, you use the following options, which are located on the Settings tab:
- Number of iterations - This option sets a limit on the number of iterations the MetaModule attempts. You can leave the fields blank if you want the MetaModule to continue until it runs out of credentials to try.
- Overall timeout - This option sets a timeout limit for how long the MetaModule can run in its entirety. You can specify the timeout in the following format:
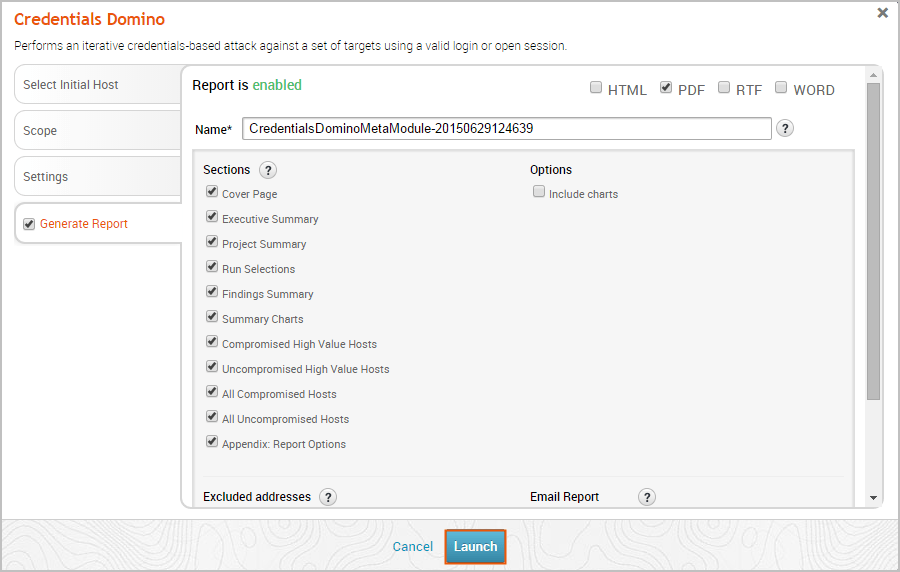
HH:MM:SS. You can leave the fields blank to set no timeout limit. - Service timeout - This option sets a timeout, in seconds, for each target. You can leave the fields blank to set no timeout limit. Including a Generated Credentials Domino MetaModule Report The Credentials Domino MetaModule Report documents the results and technical findings from a credentials-based attack. You can view the report to determine how a validated login or opened session impacted the target network.
To include a Credentials Domino MetaModule Report, you just need to enable the report option.
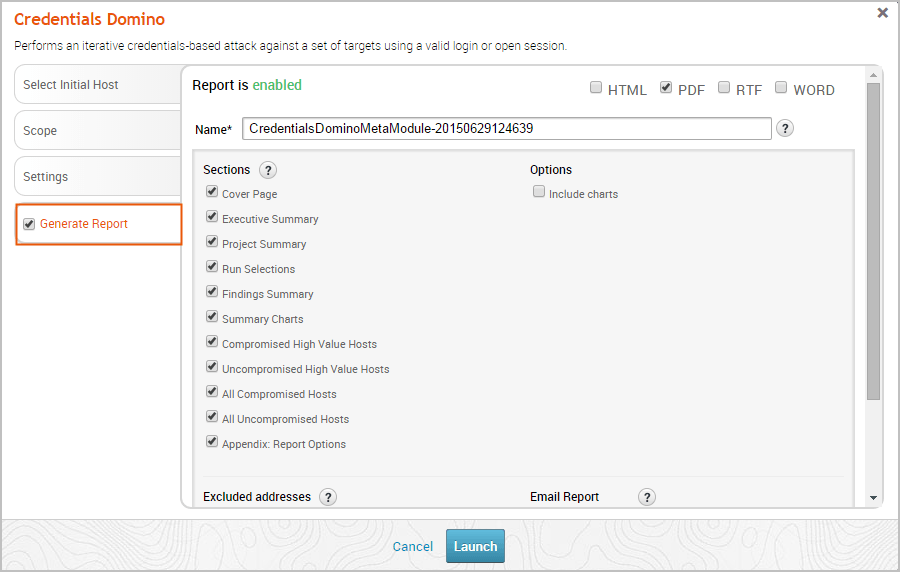
If you choose to automatically generate a report, you can customize the report using any of the following options:
- Format - The report can be generated as an HTML, PDF, or RTF file. You must select at least one format for the report.
- Name - The report has a default name based on the MetaModule and current date. You can use the default name or provide a custom report name.
- Sections - The report includes the following sections: Cover Page, Project Summary, Findings Summary, Authenticated Services and Hosts Summary Charts, Authenticated Services and Host Details, and Appendix. By default, the report includes all sections. You can deselect any sections that you do not want to include in the report.
- Mask discovered credentials - The report displays all captured credentials in plaintext. If you want to mask the credentials from the report, you must enable this option.
- Include charts - The report includes several charts and graphs that visualize the results from the attack. If you do not want to include visualizations in the report, you must enable this option.
- Excluded addresses - The report includes data for all hosts that you included in the scope. If there are specific hosts whose data you do not want to include in the report, you can list them in this field.
- Email report - You can email the report after it is generated. To email the report, you must enter a comma separated list of email addresses in this field.
Please note that you must already have a local mail server or e-mail relay service set up for Metasploit Pro to use. To define your mail server settings, go to Administration > Global Settings > SMTP Settings.
You can only generate a MetaModule report from the MetaModule. If you do not include a generated report when you configure the MetaModule, you will not be able to do so later.
Launching the Credentials Domino MetaModule When you are ready to run the Credentials Domino MetaModule, you can click the Launch button.