Credentials Domino MetaModule Report
The Credentials Domino MetaModule performs an iterative credentials-based attack to identify the attack routes that are possible when a session is obtained on or a credential is captured from a particular host. It helps you identify the targets that can be successfully compromised and the additional credentials that can be captured by leveraging a particular credential or session, and it presents the results of the attack in the Credentials Domino MetaModule Report. You can generate the report to provide a record of the results of the attack in a tangible output, such as a PDF file.
To help you navigate through the data to find key information, the report is organized into the following sections:
- Cover Page
- Executive Summary
- Project Summary
- Run Summary
- Findings Summary
- Summary Charts
- Compromised High Value Hosts
- Uncompromised High Value Hosts
- All Compromised Hosts
- All Uncompromised Hosts
- Appendix Executive Summary The Executive Summary provides a high-level recap of the findings from the MetaModule run, which includes the number of hosts that were targeted, the number of hosts that were compromised, and the number of high value hosts that were compromised. Project Summary The Project Summary lists the project name and the user who generated the report. Run Summary The Run Summary lists the runtime data for Credentials Domino MetaModule.
It includes the following data:
- Runtime - The total runtime for the Credentials Domino MetaModule.
- Iterations - The total number of iterations the Credentials Domino MetaModule performed.
- Initial host - The host that has the login or session that the Credentials Domino MetaModule used to start the attack.
- Entry point - The login or session that the Credentials Domino MetaModule used to start the attack. Findings Summary The Findings Summary provides an overview of the data captured by the Credentials Domino MetaModule.
It includes the following data:
- Hosts selected - The number of target hosts selected for the attack.
- High Value Hosts - The number of High Value Hosts targeted during the attack.
- Credentials captured - The total number of credentials collected from the attack.
- Hosts compromised - The total number and percentage of hosts on which a session was opened during the attack.
- High Value Hosts compromised - The total number and percentage of High Value Hosts on which a session was opened during the attack. Summary Charts The Summary Charts section presents a graphical breakdown of the compromise rates based on hosts and services and the activity for each iteration.
This section displays the following graphs:
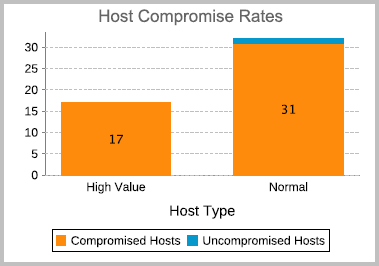
- Host Compromise Rates - Shows the relative distribution of hosts that were compromised. This graph displays findings for High Value Hosts and normal hosts.
- Service Compromise Rates - Shows the relative distribution of all the services that were compromised.
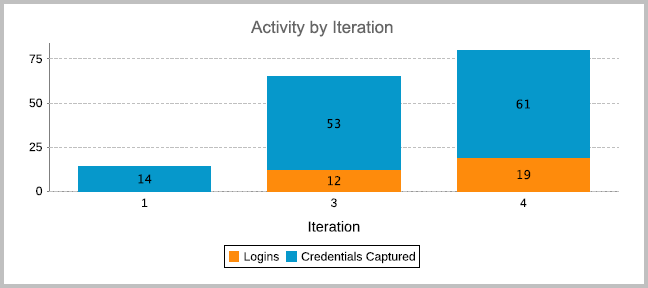
- Activity by Iteration - Shows the number of logins and credentials that were captured during each iteration of the attack.
Compromised High Value Hosts High Value Hosts identify critical hosts in an organization, such as domain controllers and servers that contain sensitive financial information. If you designated High Value Hosts when you configured the Credentials Domino MetaModule, these hosts will be included in the Compromised High Value Hosts section and will be highlighted in the report with a bold red tag. This Compromised High Value Hosts section presents the granular details for each High Value Host on which the MetaModule was able to successfully open a session and capture credentials.
The following information is included for each host:
- The host name
- The host IP address
- The host operating system
- The service that the MetaModule targeted
- The date and time the MetaModule was able to access the target
- The total number of captured credentials
- The compromise chain, which chronologically lists the series of hosts that were compromised in order to access the current host. Uncompromised High Value Hosts This Uncompromised High Value Hosts section presents the granular details for each High Value Host on which the MetaModule was unable to open a session.
The following information is included for each host:
- The host name
- The host IP address
- The host operating system
- The date and time the MetaModule attempted to access the target All Compromised Hosts The All Compromised Hosts section lists all hosts on which the MetaModule was able to successfully open a session and capture credentials.
The following information is included for each host:
- The host name
- The host IP address
- The host operating system
- The service that the MetaModule targeted
- The total number of captured credentials
- High Value Host designation All Uncompromised Hosts The All Uncompromised Hosts section lists all hosts on which the MetaModule was unable to open a session, and therefore, was unable to collect credentials.
The following information is included for each host:
- The host name
- The host IP address
- The host operating system
- The service that the MetaModule targeted
- The date and time the MetaModule attempted to access the target
- High Value Host designation Appendix The Appendix provides additional details about the Credentials Domino MetaModule Report, such as the options that were used to generate the report. Credentials Report Options
| Settings | Options |
|---|---|
| Output formats | PDF, HTML, WORD, RTF |
| Report options | Include charts and graphs - Includes visual aids, such as pie graphs, to accompany statistical findings in the report. |
| Report sections | The Credentials Domino MetaModule Report includes the following sections: Cover Page, Executive Summary, Project Summary, Run Summary, Findings Summary, Summary Charts, Compromised High Value Hosts, Uncompromised High Value Hosts, All Compromised Hosts, All Uncompromised Hosts, and Appendix. |
| MetaModule Options | Lists the options that were configured for the MetaModule run, including the Maximum iterations, Overall timeout, Timeout per service, Included hosts, Excluded hosts, and High Value Hosts. |