Installing Metasploit Pro
The standard Metasploit installer uses a graphical interface to guide you through the installation process. Installation is a simple process that takes you through a series of prompts to identify the location where you want to install Metasploit and the ports that you want Metasploit to use. After you define your installation preferences, the installer installs the dependencies and services that are necessary to run Metasploit.
All Metasploit commercial editions use the same installer. The license key you use to activate the product unlocks the edition that you have purchased. Before You Begin
- Obtain a license key - To activate Metasploit, you will need to have a license key. If you do not have one, please submit a request .
- Verify that you can obtain root privileges or have administrator rights - You must have root or admin privileges on the system to install Metasploit.
- Disable anti-virus software - Antivirus software detects Metasploit as malicious and may cause problems with the installation and runtime of Metasploit. Before you install Metasploit, disable any antivirus software that your system uses.
- Disable any firewalls - Local firewalls, such as Iptables and Windows Firewall, interfere with the operation of exploits and payloads. Disable any local firewalls before you install Metasploit.
Supported Operating Systems and Minimum System Requirements
The following system requirements are necessary to ensure you have the best experience with Metasploit Pro.
Hardware requirements
| Hardware | Minimum | Recommended |
|---|---|---|
| Processor | x86_64 2 GHz+ | - |
| RAM | 4 GB | 8 GB |
| Disk space | 1 GB | 50 GB |
Operating Systems
64-bit versions of the following platforms are supported.
| Platform | Versions |
|---|---|
| Linux |
|
| Microsoft Windows |
|
| RedHat |
|
Browsers
We support the most recent version of the following browsers:
- Google Chrome (latest)
- Mozilla Firefox (latest)
- Microsoft Edge (latest)
Installing Metasploit and Nexpose It is recommended that you install Nexpose and Metasploit on separate systems. You may experience performance problems if you attempt to run both products on the same machine. For more information on installing Nexpose, visit https://insightvm.help.rapid7.com/docs/support-technical-support-and-customer-care . Installing Metasploit on Windows
- Visit https://www.rapid7.com/products/metasploit/download/pro/thank-you and download the Windows installer.
- After you download the installer, locate the installer file and double-click on the installer icon.
- When the Setup screen appears, click Next to continue.
- Read the license agreement. To proceed, you must accept the license agreement. Select the I accept the license agreement option and click Next to continue.
- Choose an installation directory for Metasploit. The directory you choose must be empty. Click Next to continue.
- When the Disable Anti-Virus and Firewall screen appears, click Next if you have disabled the anti-virus software and firewalls on your local system. If you have not disabled them, you must disable them at this time.
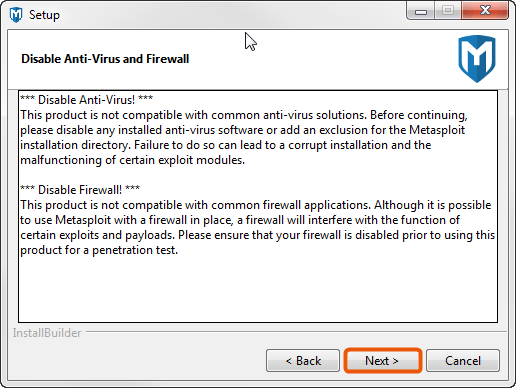
If the install detects that anti-virus software or a firewall is enabled, you will see a warning. Click OK to close the warning. The installer will not allow you to continue the installation process until the firewalls and anti-virus software are disabled. If you cannot disable them, you will not be able to install Metasploit.
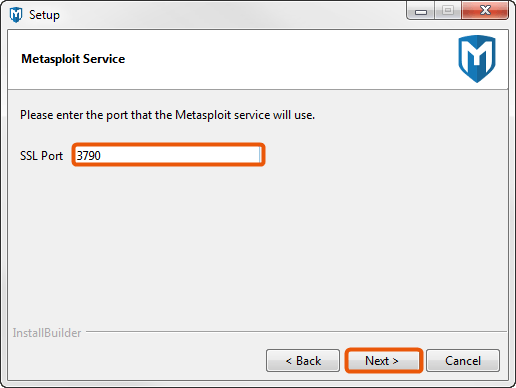
- Enter the SSL port that the Metasploit service should use and click Next. By default, the server uses port 3790 for HTTPS. If the port is already bound to another process, you can use netstat to determine if a process is already listening on that port and kill the process, or you can enter another port such as 8080 or 442.
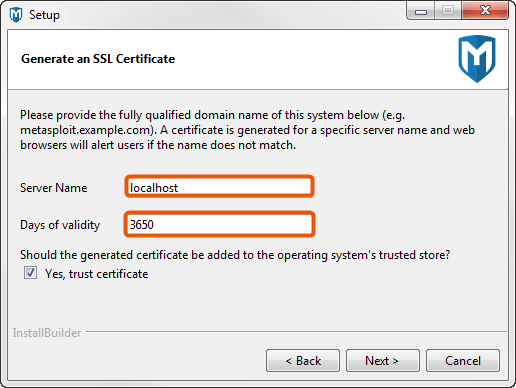
- Enter the web server name that you want to use to generate the SSL certificate and the number of days that the certificate should be valid in the Days of validity field.
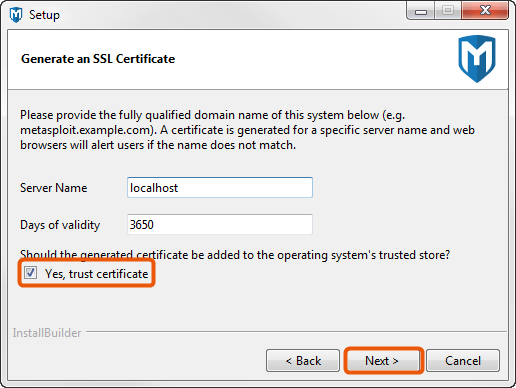
- Select Yes, trust certificate to install the self-signed Metasploit SSL certificate to your operating system’s trusted certificate store. If you install the certificate, browsers that utilize the operating system’s certificates, such as Internet Explorer, will not prompt you about an insecure SSL certificate.
Please note that the installer creates a temporary certificate authority to generate the certificate and immediately discards it in order to prevent phishing attacks and the potential resigning of the certificate.
- The installer is ready to install Metasploit and all its bundled dependencies. Click Next to continue.
- When the installation completes, click the Finish button.
After the installation completes, a window appears and prompts you to launch the Metasploit Web UI. At this point, you should launch the Metasploit Web UI to create a user account and to activate your license key . You do not need to restart your system to launch Metasploit for the first time. Installing Metasploit on Linux
-
Open the command line.
-
Download the Linux installer:
wget https://downloads.metasploit.com/data/releases/metasploit-latest-linux-x64-installer.run- Change the mode of the installer to be executable:
$ chmod +x ./metasploit-latest-linux-x64-installer.run- Run the installer:
$ sudo ./metasploit-latest-linux-x64-installer.run
or
$ ./metasploit-latest-linux-x64-installer.run- When the Setup window appears, click Forward to start the installation process.
- Read the license agreement. To proceed, you must accept the license agreement. Select the I accept the license agreement option and click Forward to continue.
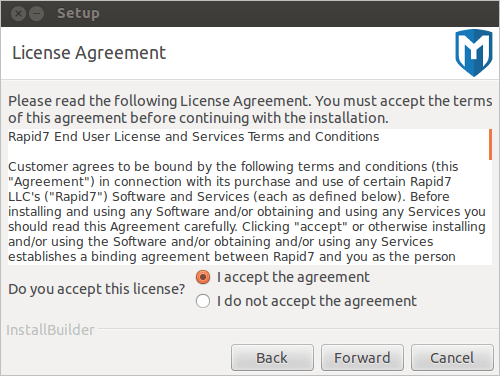
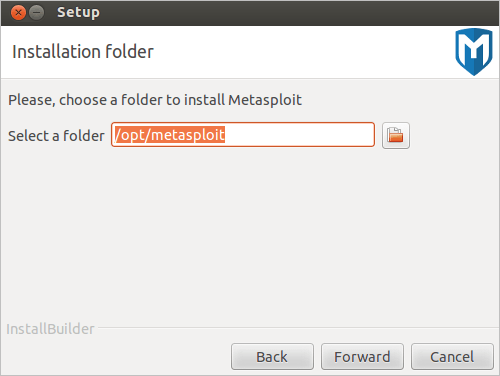
- Choose an installation directory for Metasploit. The directory you choose must be empty. Click Forward to continue.
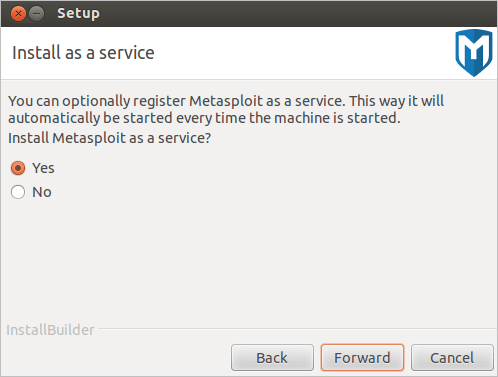
- Select Yes to register Metasploit as a service (recommended). Then, click Forward to continue.
- When the Disable Anti-Virus and Firewall screen appears, click Forward if you have disabled the anti-virus software and firewalls on your local system. If you have not disabled them, you must disable them at this time.
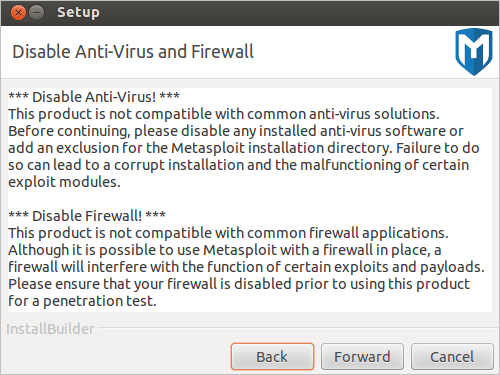
If the install detects that anti-virus software or a firewall is enabled, you will see a warning. Click OK to close the warning. The installer will not allow you to continue the installation process until the firewalls and anti-virus software are disabled. If you cannot disable them, you will not be able to install Metasploit.
- Enter the SSL port that the Metasploit service should use and click Forward.
By default, the server uses port 3790 for HTTPS. If the port is already bound to another process, you can use netstat to determine if a process is already listening on that port and kill the process, or you can enter another port such as 8080 or 442.
- Enter the web server name that you want to use to generate the SSL certificate and the number of days that the certificate should be valid in the Days of validity field.
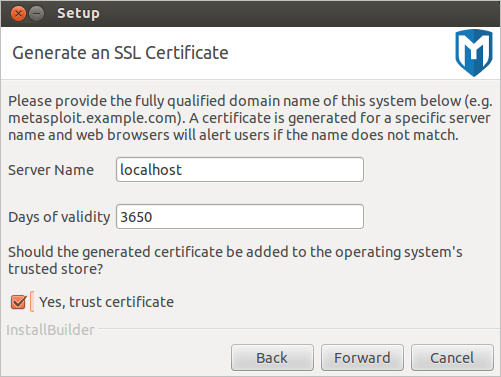
- Select Yes, trust certificate to install the self-signed Metasploit SSL certificate to your operating system’s trusted certificate store. If you install the certificate, browsers that utilize the operating system’s certificates will not prompt you about an insecure SSL certificate.
- When the Ready to Install screen appears, click Forward to start the installation process.
- When the installation completes, click the Finish button.
After the installation completes, a window appears and prompts you to launch the Metasploit Web UI. At this point, you should launch the Metasploit Web UI to create a user account and to activate your license key . You do not need to restart your system to launch Metasploit for the first time. Installing Metasploit on Headless Servers The standard Linux installer guides you through installing Metasploit on Red Hat Enterprise and Ubuntu Linux distributions. The installer takes you through a series of prompts to identify the location where you want to install Metasploit and the port that you want Metasploit service to use. When installation begins, the dependencies and services that are necessary to run Metasploit are installed.
- Open the Linux console.
- Download the installer and save it to your system.
$ wget https://downloads.metasploit.com/data/releases/metasploit-latest-linux-x64-installer.run- Change the mode of the installer to be executable:
user@ubuntu:~4 chmod +x ./metasploit-latest-linux-x64-installer.run- Run the installer:
sudo ./metasploit-latest-linux-x64-installer.run- When the welcome message appears, press Enter to start the installation process.
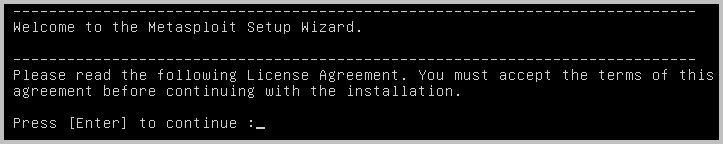
- Read each part of the License Agreement and continue to press Enter until you have read all of it.
- When you get to the end of the License Agreement, the installer shows the following screen. Press Enter to continue.
- Enter Y to accept the License Agreement.

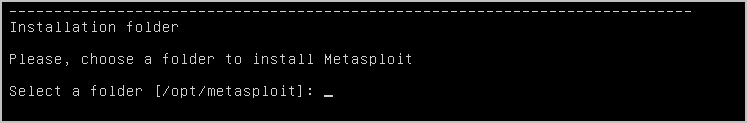
- Press Enter to install Metasploit in the default location of
/opt/metasploitor enter the location you want to install Metasploit and then press Enter.
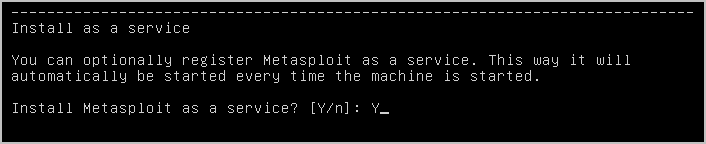
- Enter
Yto install Metasploit as a service.This adds an init script that callsctlscript.sh, which enables you to start, stop, and restart the Metasploit service.
The next message alerts you to disable any firewall or anti-virus applications that are enabled on the machine. 11. Verify that you do not have any firewall or anti-virus applications running, and then press Enter. 12. Enter the port that you want the Metasploit service to run on and press Enter.
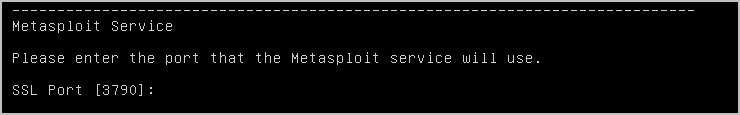
By default, the Metasploit service runs on port 3790. If you want to use the default port, leave the port field blank and press Enter.
- Enter the server name that you want to use to generate the SSL certificate.
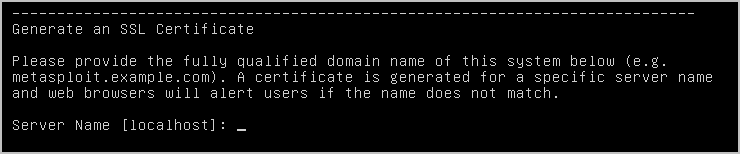
If you want to use the localhost, press Enter.
- Enter the number of days you want the SSL certificate to be valid and press Enter.

If you want to use the default value of 3650 days, press Enter.
- Enter
Yto trust the certificate.

- The installation process is now ready to start. Enter
Yand press Enter to install Metasploit and all of its components.
The next message tells you that Metasploit is being installed. Please wait while the installation completes. 17. When installation is complete, press Enter to continue.
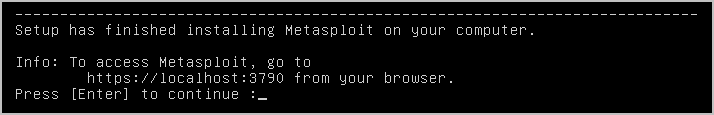
Creating a User Account on Headless Servers
After the installation completes, you will need to create a user account before you can activate your Metasploit license key. The initial user account must be created by running the createuser script.
To create a user account:
- From the Linux console, enter the following command to run the
createuserscript:
user@ubuntu:~? sudo /opt/metasploit/createuser- The script prompts you to enter a user name. Enter the user name that you want to assign to the account and press Enter.
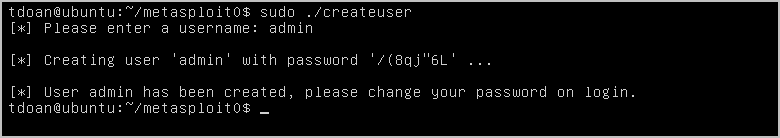
The script creates the user account and automatically generates a password for you. You should copy the password so that you can log in to the Metasploit Pro web interface. You can change the password after you log in to Metasploit for the first time.
Activating Your License Key with a Text Based Browser
If you do not have access to a web browser, you can activate your license key from a text based browser, like Lynx.
- Launch your browser and go to
https://<server address>:3790.

- When the SSL self-signed certificate message appears, enter
yto continue.

- When the cookie message appears, enter
yto add the cookie and to continue.

- If the SSL self-signed certificate message appears again, enter
yto continue. - When the login page appears, enter the user name and password that you created earlier and press Enter.
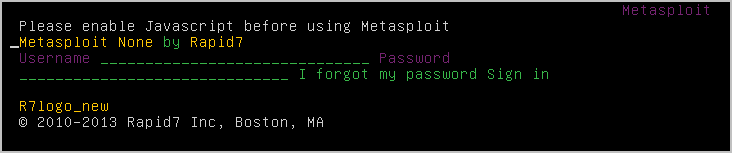
- If the SSL certificate and cookie messages appear again, enter
yto continue. You will need to do this until you see the Metasploit menu.
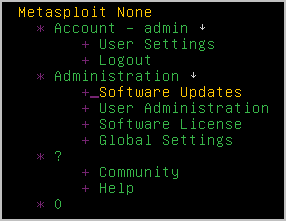
- When the Metasploit menu appears, press the space bar twice to view the License Activation screen.
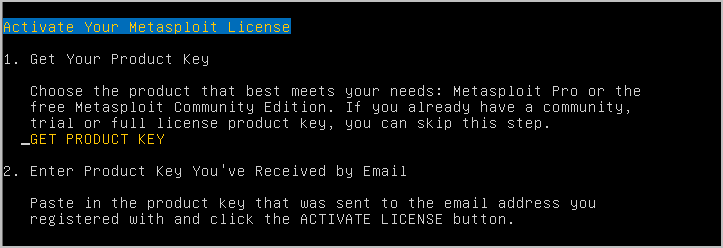
- Use the down arrow to navigate to the product key field and enter the license key. The license key should be entered using the following format: xxxx-xxxx-xxxx-xxxx.
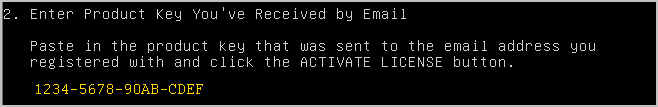
- Use the down arrow to navigate to the ACTIVATE LICENSE link and press Enter.
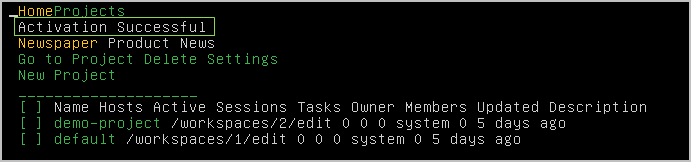
- If the activation is successful, the Projects screen appears and indicates that the activation was successful.
You are now ready to run Metasploit.
Launching the Pro Console
After you have activated your license key, you can run Metasploit from the command line. If you have a Metasploit Pro license, you can run the Pro Console. The Pro Console provides you command line access to the Metasploit Framework, as well as Metasploit Pro-only features, such as the Discovery Scan, auto-exploitation, bruteforce, and reporting. Learn more about the Pro Console.
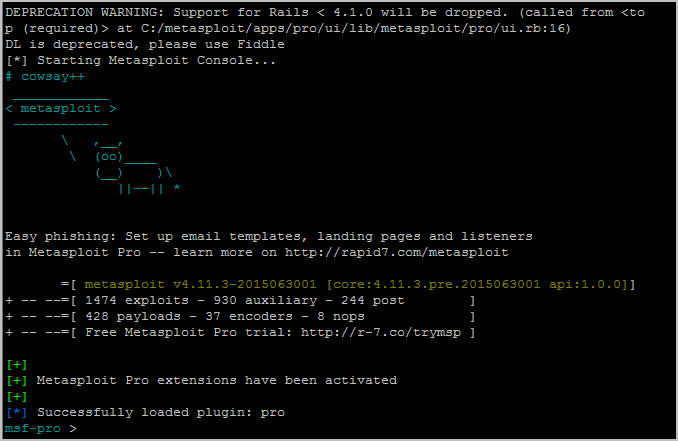
To launch the Pro Console on a Linux system, open the command line terminal and type sudo msfpro when the command prompt appears. You must run the console as root.
$ cd /opt/metasploit
$ sudo msfproWhen the Pro Console loads, the command line drops to an msf-pro > prompt, as shown below:
Activating a License Key Now that you’ve installed Metasploit, the next thing you need to do is activate your license key. Each license key is bound to a specific edition of Metasploit and gives you access to the edition you that you’ve registered for.
- Open a browser and go to
https://localhost:3790.
If you receive a warning about the trustworthiness of the security certificate, select that you understand the risks and want to continue to the website. The wording that the warning displays depends on the browser that you use.
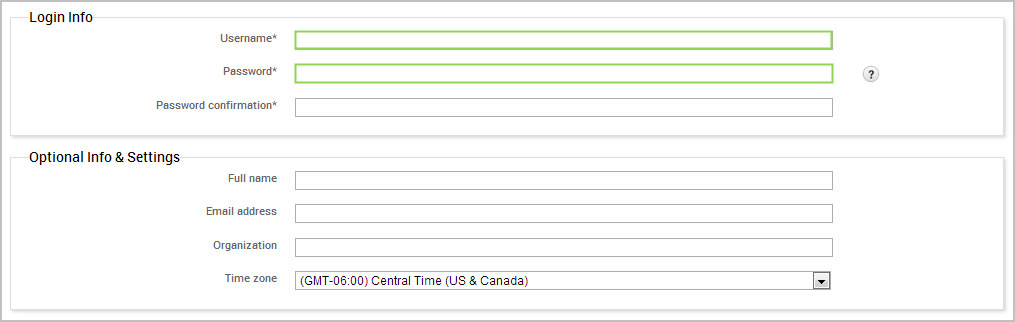
- When the web interface for Metasploit Pro appears, the New User Setup page displays. Follow the onscreen instructions to create a user account for Metasploit Pro. Save the user account information so that you can use it later to log in to Metasploit Pro.
- After you create a user account, the Activate Metasploit page appears. Enter the license key that you received from Rapid7 in the Product Key field.
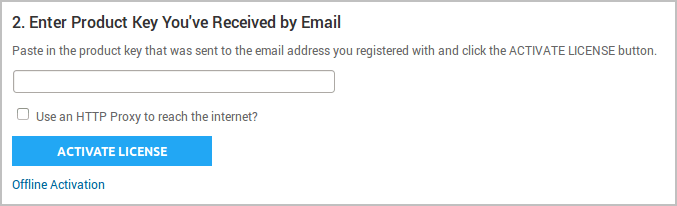
- If you need to use an HTTP proxy to reach the Internet, you can select the HTTP proxy option and provide the information for the HTTP proxy server that you want to use.
- Activate the license key.
After you activate the license key, the Projects page appears. You can now create a project and start working on your first pentest.