Known Credentials Intrusion MetaModule
The Known Credentials Intrusion MetaModule logs in to a list of specified services and attempts to open sessions on a range of hosts with the known credentials in the project. You can run this MetaModule if you want to quickly get shells on the hosts in your project.
In order to run the Known Credentials Intrusion MetaModule, the project must already contain credentials that you have either collected from a Discovery Scan, bruteforce attack, or data import. The Known Credentials Intrusion MetaModule will attempt to authenticate to each service that has been enumerated for each host. If the MetaModule is able to successfully log in to the service, it attempts to open a session on the target, which you can use to do things like set up a VPN pivot, collect system data, or launch a shell to interact with the target system. It opens one session per target, and it will move onto the next host in the test if a session has already been established for a host.
During the MetaModule run, Metasploit Pro displays real-time statistics for the number of hosts targeted and the number of sessions opened. When the MetaModule completes its run, it generates a complete report that provides the details for the hosts on which it was able to open a session. You can share this report with your organization to expose weak passwords and to help mitigate vulnerabilities in its security infrastructure. Running the Known Credentials Intrusion MetaModule Before you can run the Known Credentials Intrusion MetaModule, you must run a Discovery Scan on the target network range or import existing host data. This populates the project with the necessary host information, such as open ports and services, that the MetaModule needs to run.
- From within a project, select Modules > MetaModules.
- Find the Known Credentials Intrusion MetaModule and click the Launch button. The Known Credentials Intrusion window appears.
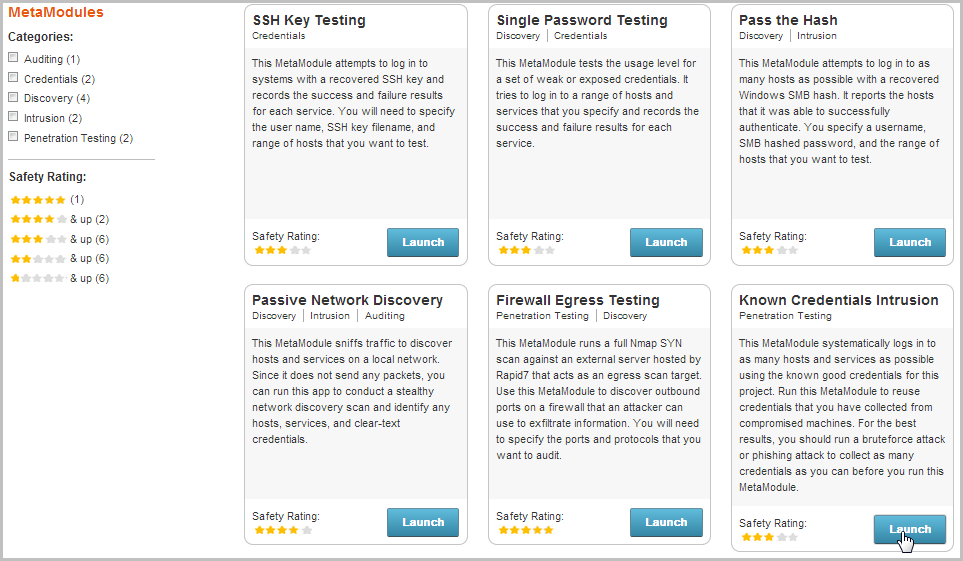
- From the Scope tab, enter the target address range you want to use for the test.
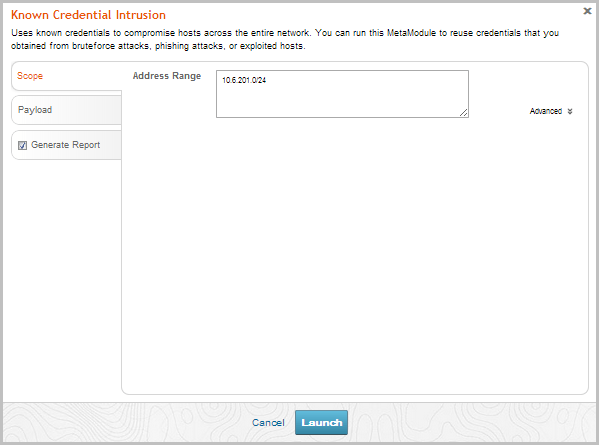
- Click on the Payload tab to configure the payload settings.
- Specify the following settings that you want to use for the payload:
- Payload type - Choose Meterpreter for Windows or Command shell for Linux systems.
- Connection - Choose one of the following connection types:
- Auto - Automatically selects the payload type. In most cases, the Auto option selects the reverse shell payload because it is more likely to establish a connection between a target machine and the attacking machine.
- Reverse - Select this option if the targets are behind a firewall or use NAT. Typically, a reverse shell payload will work for most situations.
- Bind - Select this option if the target devices are unable to initiate a connection.
- Listener Ports - The port that you want the listener to listen on for incoming connections. By default, ports 1024-65535 are selected; however, you can define a specific port that you want the listener to use, such as 4444.
- Listener Host - The IP address that you want the target machine to connect back to. This is typically going to be the IP address of your local machine. If you do not specify a listener host, the MetaModule automatically uses the IP address of your local machine.
- Click the Generate Report tab. The Report configuration form appears.
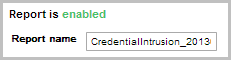
- Enter a name for the report in the Report Name field, if you want to use a custom report name. Otherwise, the MetaModule uses the default report name.
- Choose whether you want to generate the report as a PDF, HTML, or RTF file.
- From the Sections area, deselect any sections you do not want to include in the report. Skip this step if you want to generate all the report sections.
- From the Options area, select the Mask discovered passwords option if you want to obscure any passwords that the report contains. The report replaces the password with **MASKED** . By default, this option is disabled. You should enable this option if you plan to distribute the report.
- Select the Email Report option if you want to email the report after it generates. If you enable this option, you need to supply a comma separated list of email addresses.
If you want to email a report, you must set up a local mail server or email relay service for Metasploit Pro to use. To define your mail server settings, select Administration > Global Settings > SMTP Settings.
- Click the Launch button.