Pass the Hash Report
The Pass the Hash Report presents the results from using a particular username and hash against targeted hosts and services. At a high level, the report displays graphs to show the relative distribution of the top five hosts and services that were authenticated using the credential pair. The report also includes the technical details for each target that was successfully authenticated to using the username and hash.
To help you navigate through the data to find key information, the report is organized into the following sections:
-
Project Summary
-
Findings Summary
-
Authenticated Services and Hosts Summary Charts
-
Authenticated Services and Hosts Summary Details
-
Appendix Project Summary The Project Summary shows the project name and the user who generated the report. Findings Summary The Findings Summary lists the following information:
-
MetaModule - The MetaModule that was run.
-
Runtime - The total duration of the MetaModule run.
-
Username selected - The username that the MetaModule used to attempt to authenticate to a target.
-
NTLM hash selected - The hash that the MetaModule used to attempt to authenticate to a target.
-
Hosts selected - The total number of hosts that were selected as targets for the MetaModule.
-
Services selected - The total number of services that were targeted.
-
Hosts tried - The total number of hosts that the MetaModule attempted to authenticate to.
-
Services tried - The total number of services that the MetaModule attempted to authenticate to.
-
Successful logins - The total number of logins that the MetaModule was able to establish. Authenticated Services and Hosts Summary Charts The Authenticated Services and Hosts Summary Charts section uses pie charts to visualize the relative distribution of the top five hosts that the MetaModule was able to authenticate to and the top five services that the MetaModule was able to find logins for using the provided username and hash.
The following image shows the Authentication Services and Hosts Summary Charts:
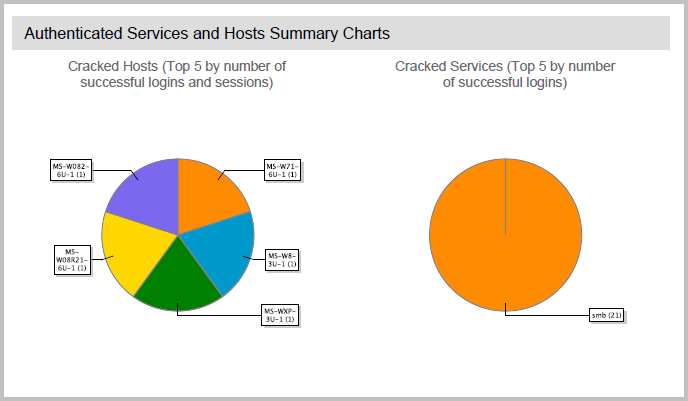
Authenticated Services and Hosts Details The Authenticated Services and Hosts Details section lists the technical details for each target on which the MetaModule was able to authenticate with the provided username and hash. Targets are listed by host name. For each host, the report lists the services that the MetaModule was able to successfully authenticate to and the details for each service.
Each service will have the following information:
- The port number
- The protocol
- The service name
- The timestamp for the login attempt
- The result of the login
- The access level for the login Appendix The Appendix provides additional details about the Pass the Hash Report, such as the options that were used to generate the report. Report Options
| Settings | Options |
|---|---|
| Output formats | PDF, HTML, WORD, RTF |
| Report options | Mask discovered credentials - Masks all credentials from the report. It replaces the private with *MASKED*. Include charts and graphs - Includes visual aids, such as pie graphs, to accompany statistical findings in the report. |
| Report sections | Cover Page Project Summary Findings Summary Authenticated Services and Hosts Summary Charts Authenticated Services and Hosts Summary Details Appendix |
| Selected services | Lists the services that were selected for the MetaModule to attempt to authenticate to. |