Social Engineering Campaign Details Report
The Social Engineering Campaign Details Report contains the comprehensive results and data for a particular campaign. It provides a detailed report of the findings that the campaign has collected and helps you organize your data to share with team members or across an organization. Like the other types of reports, the Campaigns Details Report can be generated in easily distributable formats, such as PDF, Word, RTF, and HTML.
From the Social Engineering Campaign Details Report, you can view the following types of information:
-
A statistical overview of the campaign findings.
-
Actions taken by human targets in a campaign.
-
Statistical analysis of human target behavior and easy identification of high risk targets.
-
Browser and operating systems used by human targets in a phishing attack.
-
Raw data from the components used to create a campaign.
-
Any exploits that were used in the campaign and any sessions that were obtained from compromised systems.
-
Remediation steps that can be implemented or can be recommended to reduce the threat of social engineering attacks across an organization. Social Engineering Campaign Report Options When you generate the Social Engineering Campaign Details Report, there are several options that you can configure to customize the report, such as:
-
Including the code used to create the web pages in the campaign.
-
Masking all email addresses.
-
Selecting the sections you want to include in the report.
-
Emailing the report to a list of recipients.
-
Changing the report name.
Including the Web Page Code in the Report
An image preview of the web page will render in the report if the web page was used as part of a phishing campaign. If a web page was used to deliver malicious code, such as client-side exploits, Java applets, Browser Autopwn, or executable files, a preview will not display in the report.
If you want to include the raw HTML that was used to create a web page, select the Include web page code option on the New Report form. When you enable this option, the raw code will be displayed under each web page preview in the report.
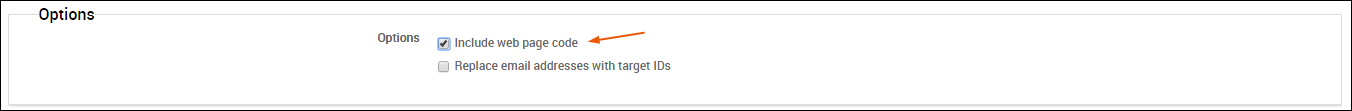
Masking the Email Addresses for All Human Targets
The Social Engineering Campaign Details Report contains sensitive information for each human target that participated in the campaign, including their email address. If you want to mask the email address from the report, you can select the Replace email addresses with target IDs option.
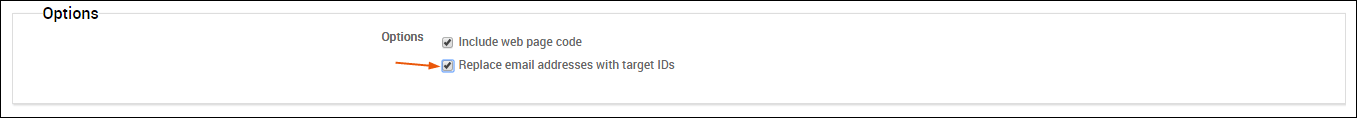
When this option is enabled, the report displays the target’s ID in place of their e-mail address, as shown below.
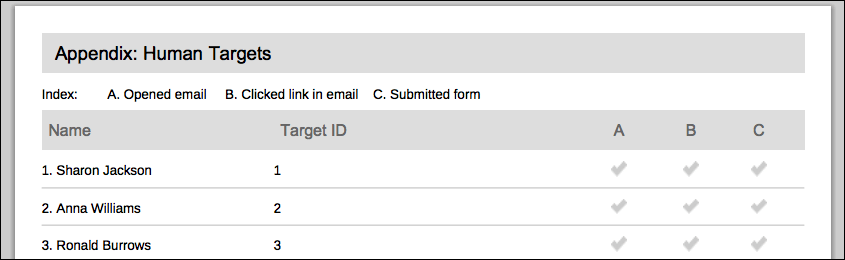
Where can I view the target IDs?
Each human target has an ID that is assigned to them when you add them to a target list. You can find the target ID using the following methods:
- Viewing the results page for the target - You can view the results page for each target by clicking on their email address from the ’% of recipients opened the email,’ ’% of recipients clicked the link,’ or the ’% of recipients submitted the form’ areas of the Campaign Findings.
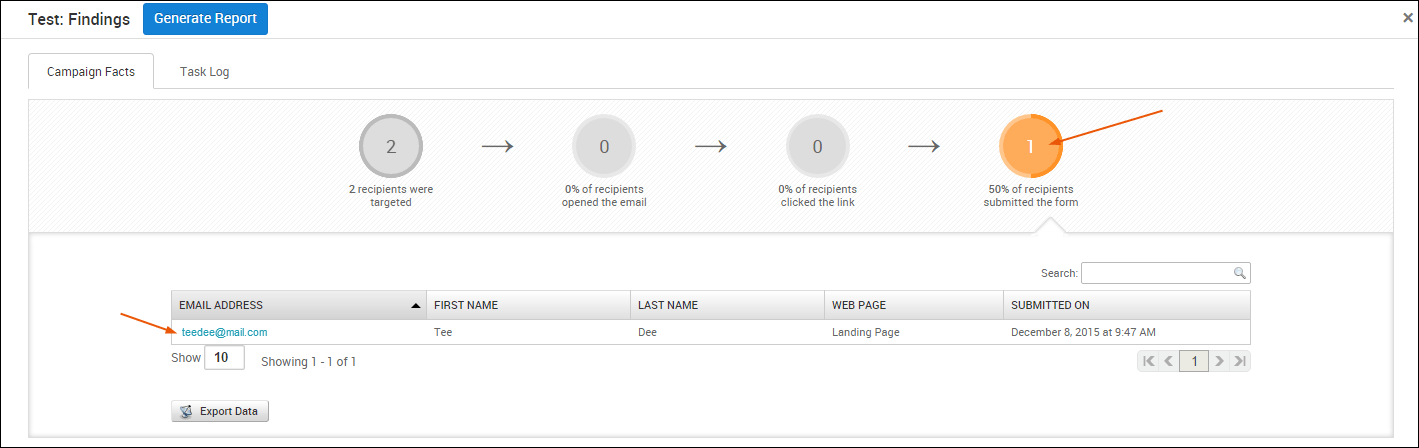
The target ID can be found in the URL of the results page. For example, if the URL for the results page is https://localhost:3790/workspaces/1/social_engineering/human_targets/2 , the target ID is 2.
- Exporting campaign data from the Findings window - You can export data from the ’% of recipients opened the email,’ ’% of recipients clicked the link,’ or the ’% of recipients submitted the form’ areas of the Campaign Findings to easily view the target IDs.
When you export data from the Campaign Findings, the resulting CSV contains the email address, first name, last name and ID for each target that the campaign was able to track. It also identifies the web page name, phishing ID result and web page ID for the campaign.
Including and Excluding Report Sections
By default, the Social Engineering Campaign Details Report includes all sections that are available for the report. However, only sections that are applicable to the campaign will have data present in the report. If a section does not have any data for Metasploit Pro to report on, then the section will be empty in the report.
For example, if you choose to include the ‘Exploits Used’ section in your report, but the campaign does not actually deliver a payload, you will not see any data in the section.
To include or exclude sections from your report, find the Report Sections area on the New Report form. You will see a list of all the sections that are available in the report, such as the Executive Summary, Social Engineering Funnel, Exploits Used, and Form Submission sections, as well as appendices for the report. Any sections that have a marked check box will automatically be included in the report. To remove any sections, deselect the check box.
Emailing the Generated Report
Metasploit Pro enables you to automatically email a report after it is generated. To email a report, you need to enable the Email report option on the New Report form and specify the emails that you want to send the report to. The emails that you specify must be comma separated.
Additionally, before you can email a report, you need to set up the SMTP settings through the Global Settings. If you already have an existing global SMTP server for your campaigns, then Metasploit Pro will just use that mail server to send the emails.
If you do not have a global SMTP server set up, go to Administration > Global Settings > SMTP Settings. You will need to provide Metasploit Pro with the information for your mail server. This information includes the credentials that Metasploit Pro will need to authenticate to the mail server and the domain and SMTP port information for the mail server.
Naming the Report
By default, Metasploit Pro uses a naming convention that uses the report type and the task number to name the report. You can change the name by replacing the default name in the Report Name field on the New Report form. Social Engineering Campaign Details Report Sections The following table shows the sections that the Social Engineering Campaign Details Report includes:
| Section | Included by Default | Included for Campaigns with Specific Components | Included for Campaigns that Opened Sessions |
|---|---|---|---|
| Cover Page | ✔ | ||
| Executive Summary | ✔ | ||
| Social Engineering Funnel | ✔ | ||
| Exploits Used | ✔ | ||
| Form Submissions | ✔ | ||
| Browser/Platform Information | ✔ | ||
| Appendix: Host Details | ✔ | ||
| Appendix: Human Targets | ✔ | ||
| Appendix: Emails | ✔ | ||
| Appendix: Web Pages | ✔ | ||
| Appendix: Portable Files | ✔ | ||
| Appendix: Remediation Advice | ✔ | ||
| Appendix: Notes | ✔ |