SSH Key Testing MetaModule
SSH public key authentication provides a secure method of logging in to a remote host. It uses an SSH key pair to authenticate a login instead of the traditional user name and password combination. The SSH key pair consists of a private and public SSH key. The private SSH key is stored on the local machine and enables you to log in to remote systems on which the corresponding public key is installed.
If you obtain an unencrypted SSH private key from a compromised target machine, you can run the SSH Key Testing MetaModule. This MetaModule enables you to bruteforce logins on a range of hosts to identify remote machines that can be authenticated with the private key. During the MetaModule run, Metasploit Pro displays real-time statistics for the number of hosts targeted, the number of login attempts made, and the number of successful logins. After the MetaModule completes its run, it generates a complete report that provides the details for the hosts it was able to successfully authenticate. Running the SSH Key Testing MetaModule Before you can run the SSH Key Testing MetaModule, you must either have a SSH private key available that you can upload to your project or your project must contain a looted SSH private key obtained from a scan, a bruteforce attack, or some other exploit method.
- From within a project, select Modules > MetaModules.
- Find the SSH Key Testing MetaModule and click the Launch button. The SSH Key Tester window appears.
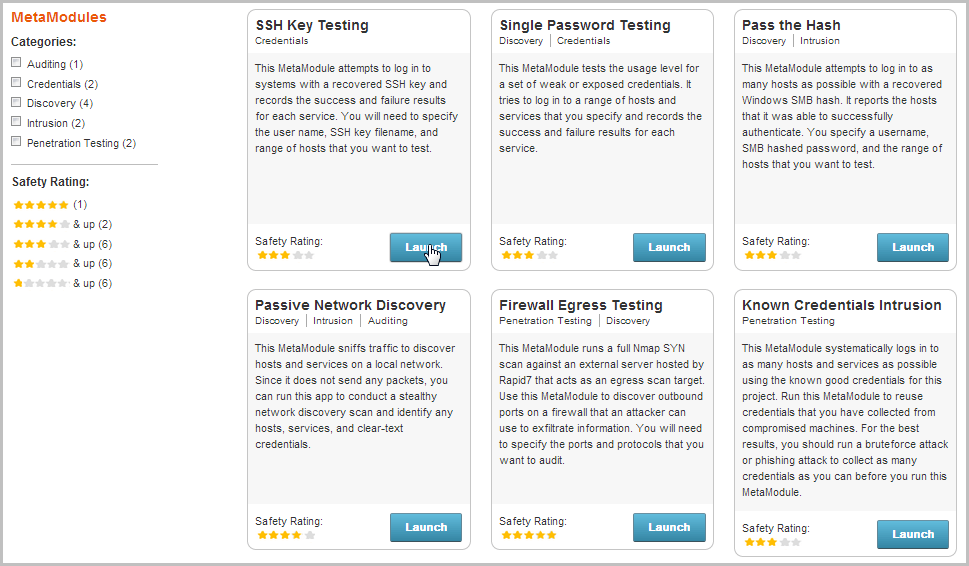
- From the Scope tab, enter the target address range you want to use for the test.
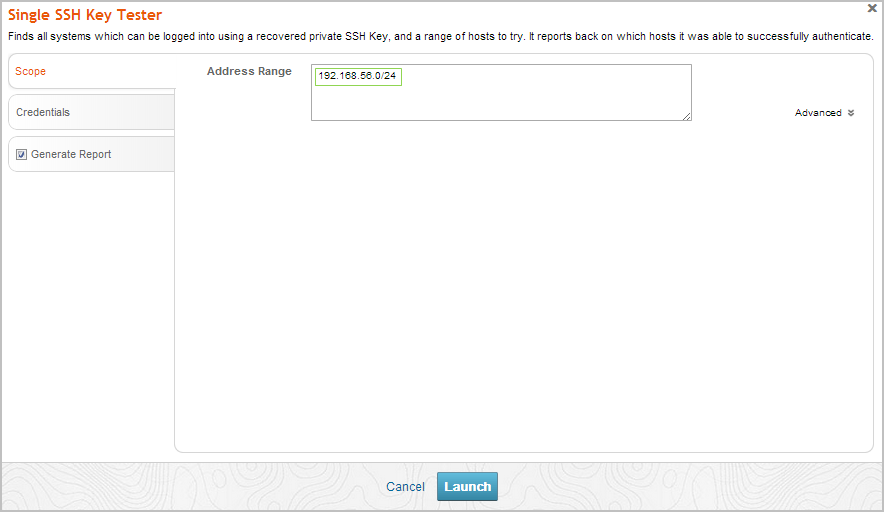
- Click on the Credentials tab. The Credentials form appears.
- Choose one of the following options to supply the MetaModule with an SSH private key:
- Enter a known credential pair - You need to manually enter the user name, and then browse to the location of the private key that you want the MetaModule to use.
- Choose an existing SSH key - You can select a user name and SSH key from a list of looted keys. These keys were obtained from a bruteforce attack, discovery scan, data import, or exploited system.
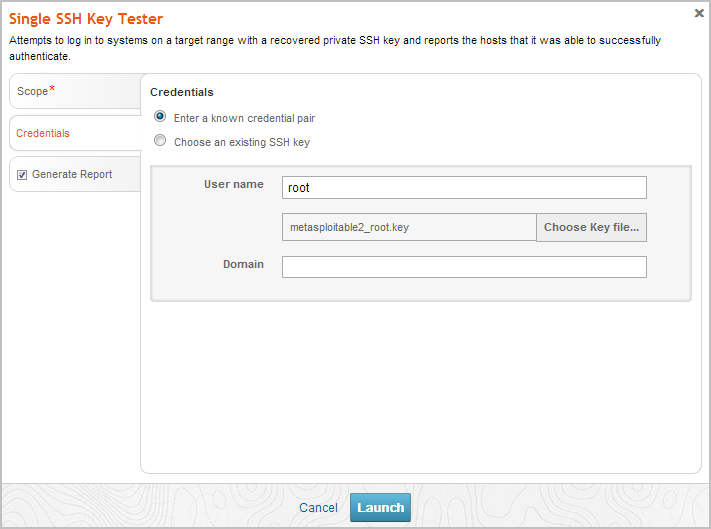
- Click the Report tab. The Report configuration form appears.
- Enter a name for the report in the Report Name field, if you want to use a custom report name. Otherwise, the MetaModule uses the default report name.
- Choose whether you want to generate the report as a PDF, HTML, or RTF file.
- From the Sections area, deselect any sections you do not want to include in the report. Skip this step if you want to generate all the report sections.
- Select the Email Report option if you want to email the report after it generates. If you enable this option, you need to supply a comma separated list of email addresses.
If you want to email a report, you must set up a local mail server or email relay service for Metasploit Pro to use. To define your mail server settings, select Administration > Global Settings > SMTP Settings.
- Click the Launch button.
When the MetaModule launches, the Findings window appears and displays the real-time statistics and tasks log for the MetaModule run. You can track the total number of hosts that the MetaModule attempted to authenticate, the total number of login attempts, and the total number of successful logins. If you want to view all the event details, you can click on the Task Log tab.
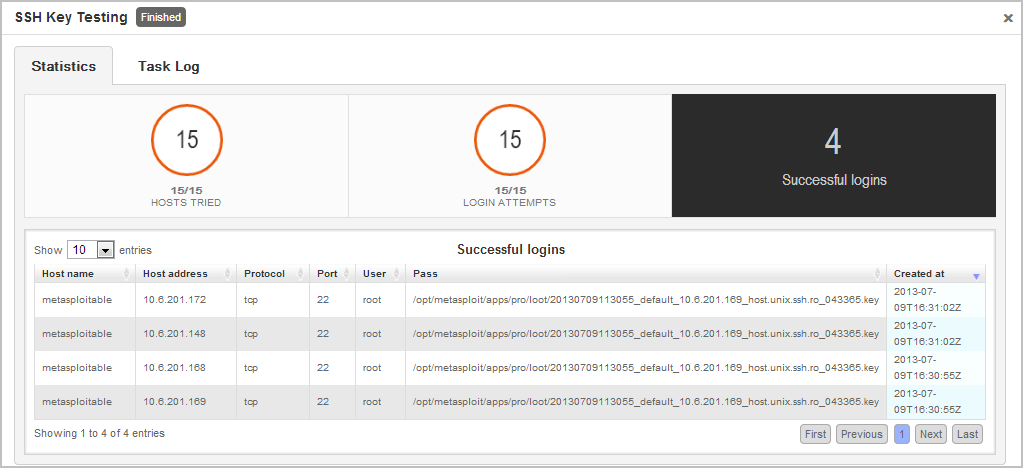
After the MetaModule completes its run, you should go the Reports area to view the SSH Key Testing Report. The first few pages of the report show graphs and tables that provide a high-level breakdown of cracked hosts and services. For a more detailed look at the hosts, you can look at the Authenticated Services and Hosts Details section, which shows the services that were authenticated and the sessions that were opened on each host.