The Administration Page
The Administration page is where you will manage software updates, users, and global settings.
You can access the following sections from Administration:
To access Administration in Metasploit Pro, click Administration in the upper right.
Software Updates
Any time a new version of Metasploit Pro is released or you want to check for updates, you can do this from the “Software Updates” screen.
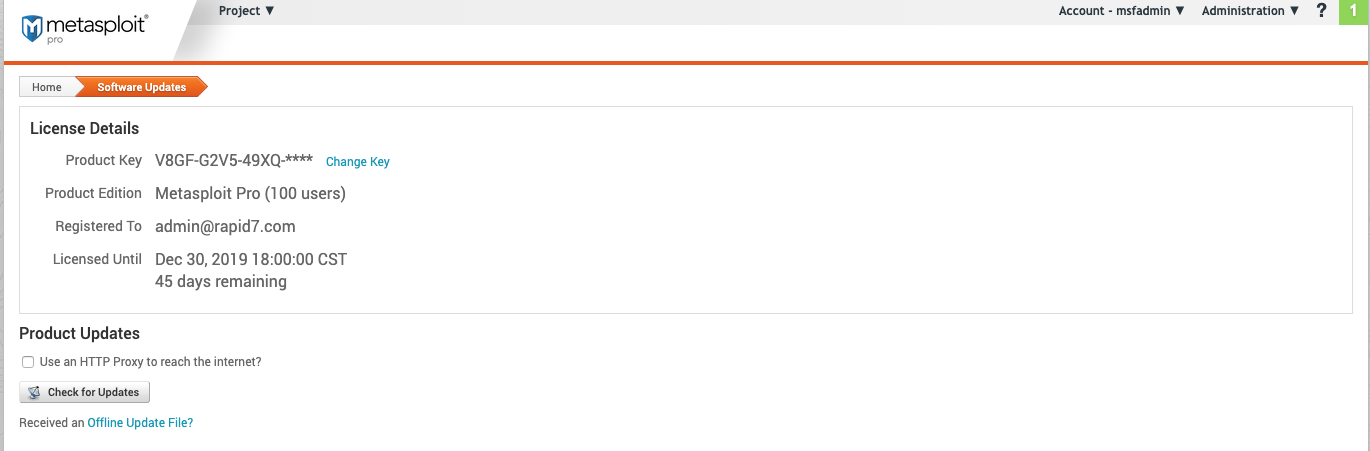
License Details
- Product Key - The current product key for Metasploit Pro.
- Product Edition - The version of Metasploit you are using.
- Registered To - The original email address used to register Metasploit Pro.
- Licensed Until - The date and time the product key will expire. This field also includes a countdown for the number of days remaining.
Product Updates
- **Use an HTTP Proxy to reach the internet?*8 - This will open settings for you to configure if you need to use a HTTP Proxy to reach the internet.
- Check for Updates - Check for any new updates to Metasploit Pro.
- Received an Offline Update File? -After clicking the link, follow the instructions to update using a file.
User Administration
User Administration is where you add, remove, or change the access level of users.
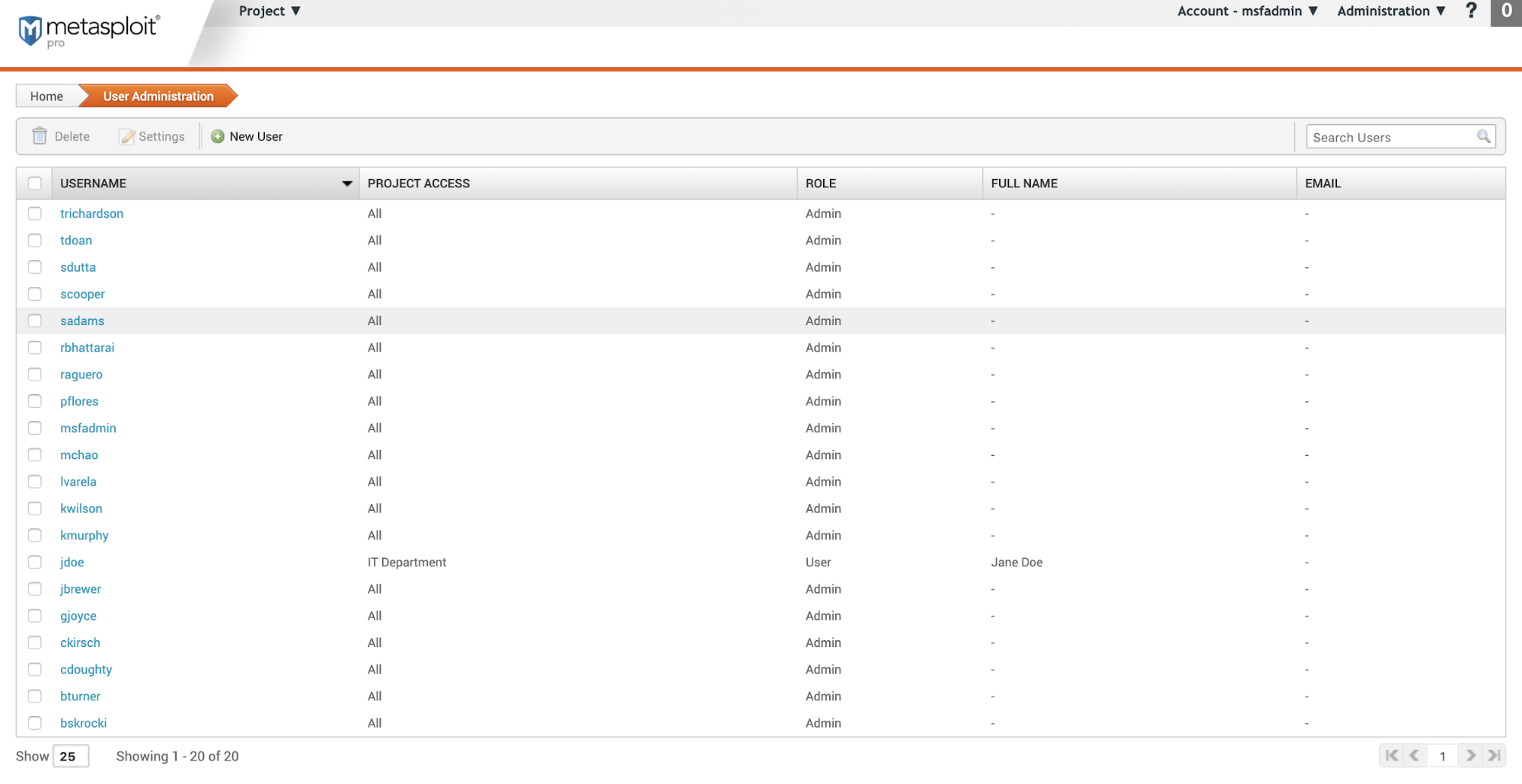
- Username - The username
- Project Access - What projects a user has access to. If a user is an Admin, they will have access to all projects, regardless of what is selected when creating a project.
- Role - If the user is an Admin or User
- Admin - Has access to all projects
- User - Has access to only selected projects
- Full Name - Users full name
- Email - Users email
Software License
The Software License screen is where you can see the number of allowed users, activate a new license, or request a new license.
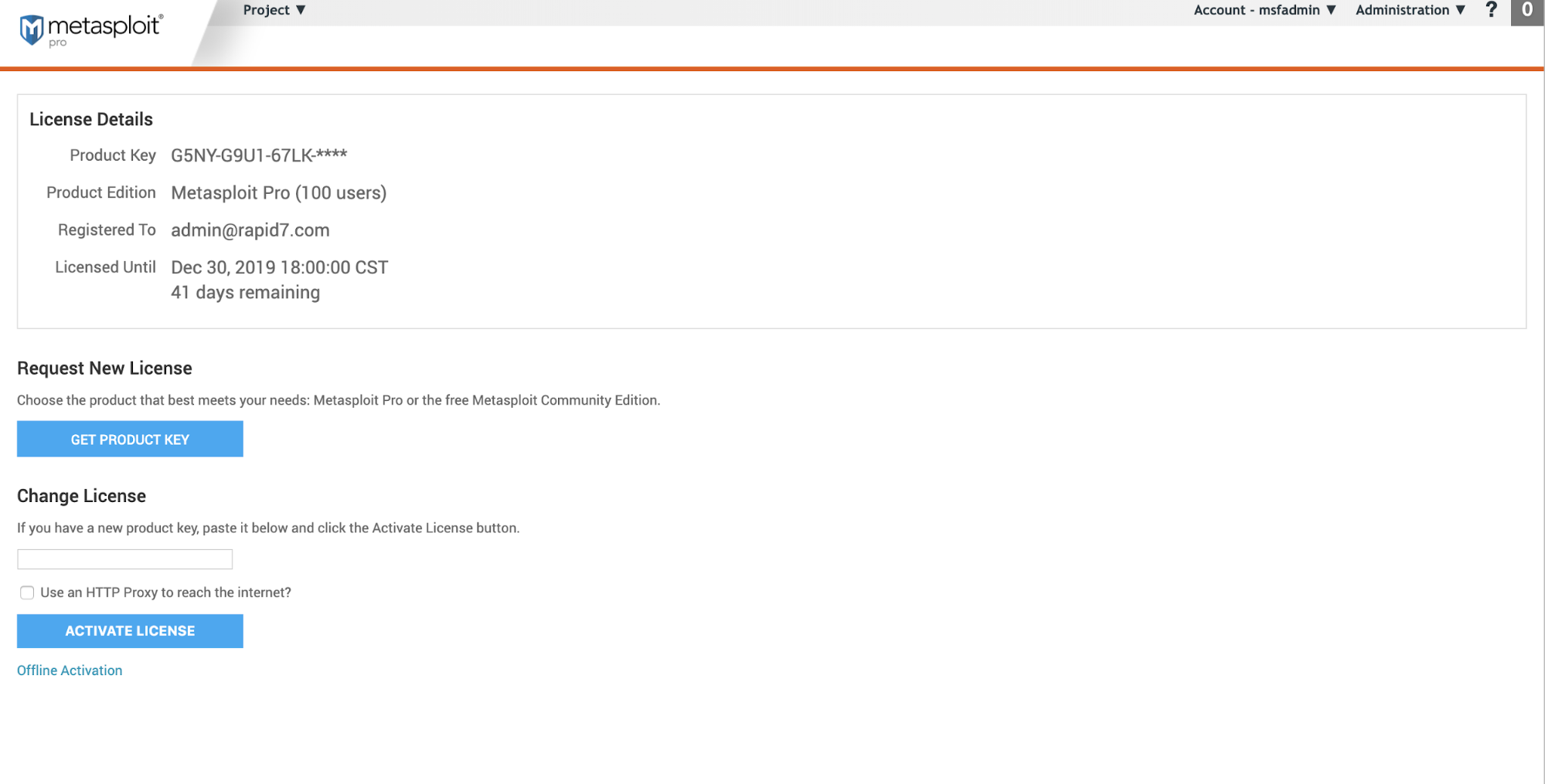
License Details
- Product Key - The current product key for Metasploit Pro.
- Product Edition - The version of Metasploit you are using. The number of users the product allows.
- Registered To - The original email address used to register Metasploit Pro.
- Licensed Until - The date and time the product key will expire. This field also includes a countdown for the number of days remaining.
Request New License
Follow the steps to contact support for a new license key if needed.
Change License
- Enter a new product key to activate the license
- Use an HTTP Proxy to reach the internet? - This will open settings for you to configure if you need to use a HTTP Proxy to reach the internet.
- Offline Activation - After clicking the link, follow the instructions to update using a file.
Global Settings
The Global Settings screen is where you can manage system wide settings. These will not override project level settings.
Global Settings
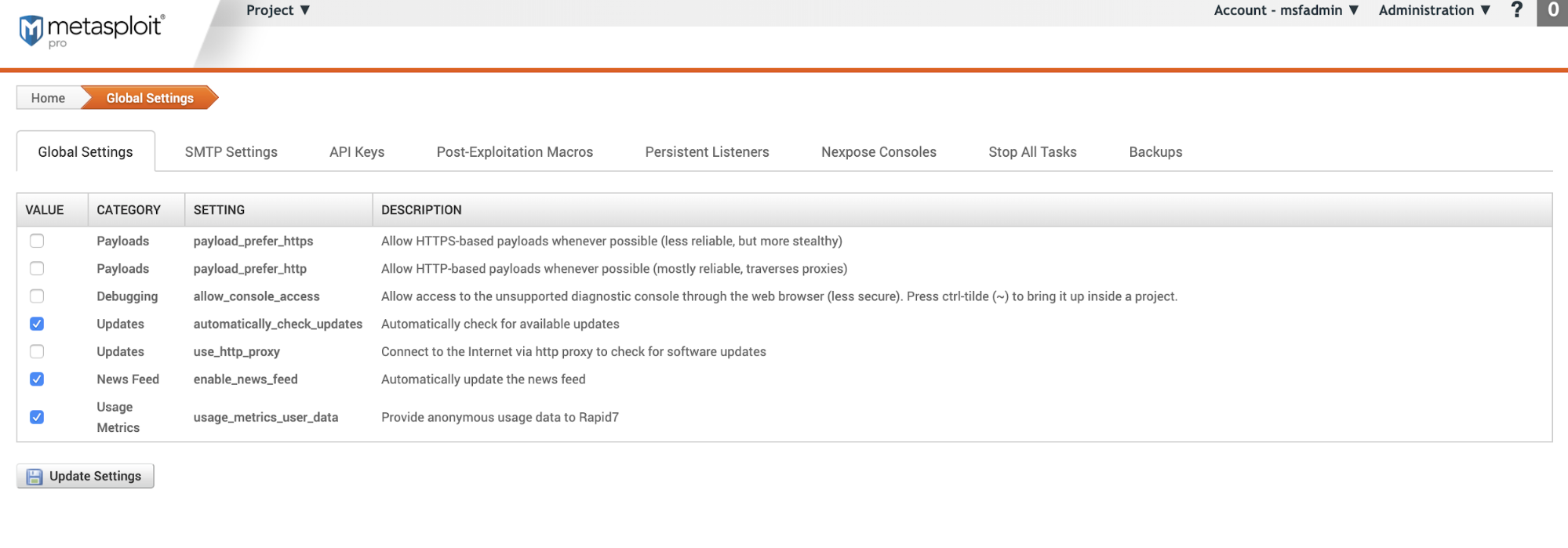
- Value - Toggle to turn the setting on or off.
- Category - What the setting controls.
- Setting - Name of the setting.
- Description -What the setting does.
SMTP Settings
Configureglobal email settings . For social engineering campaigns , the information will automatically populate in the email fields.
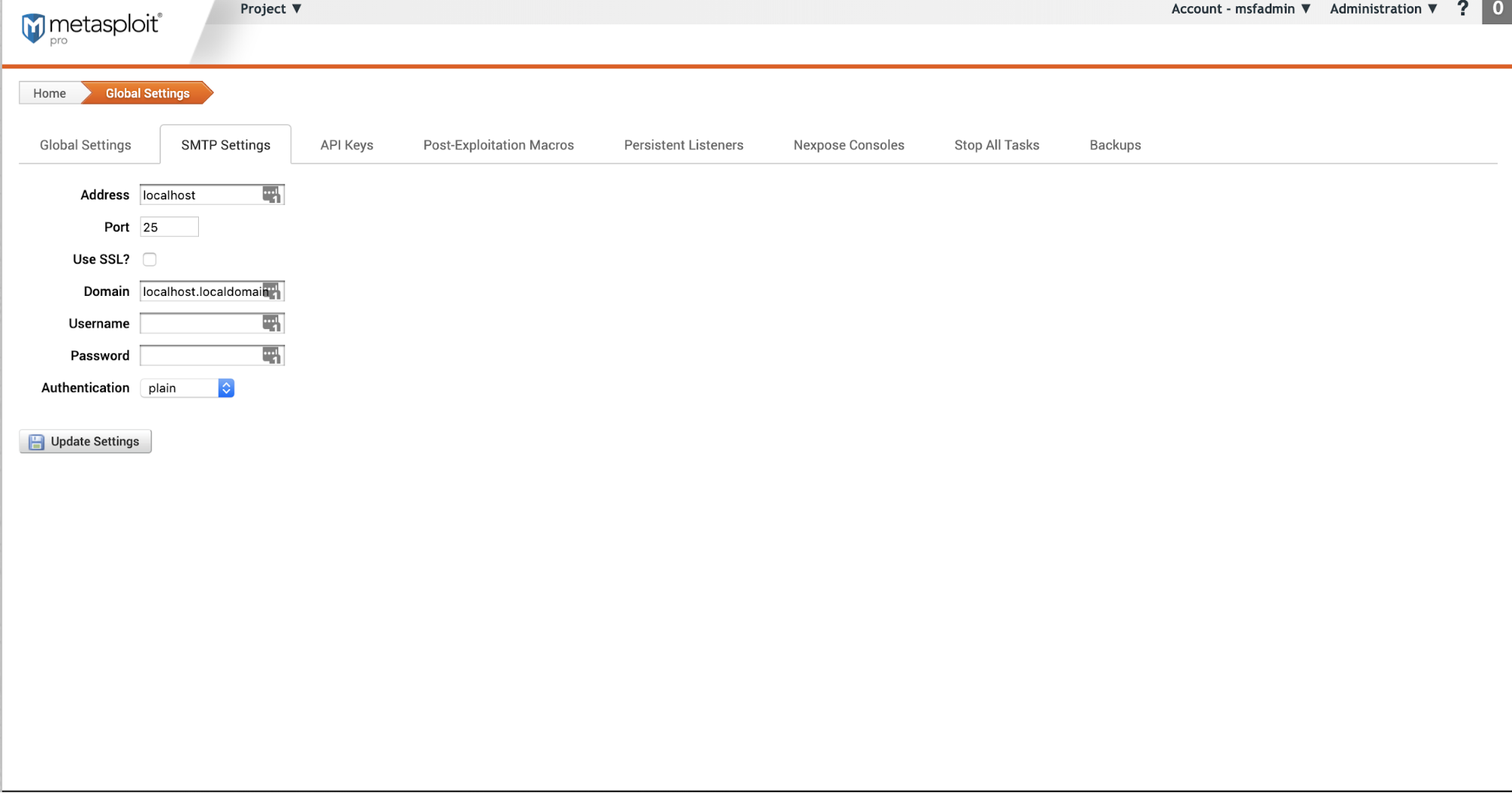
- Address - he fully qualified mail server address (for example,
mail.domain.com). - **Port - The **port that the server uses.
- **Use SSL? - **Enable SSL for emails.
- Domain - The hosted domain name for your mail server (for example,
domain.com). - Username - Login username for the server.
- **Password **- Password for the server.
- Authentication - The type of authentication your server requires.
- plain - The authentication is sent as Base64 encoded. SSL is recommended with this authentication type.
- Login - The server asks for the username and password as Base64 encoded and the response is sent as Base64 encoded. SSL is recommended with this authentication type.
- cram_md5 - Challenge and response authentication.
API Keys
Create and manage API keys. To learn more about the Metasploit API, see Standard API Methods Reference .
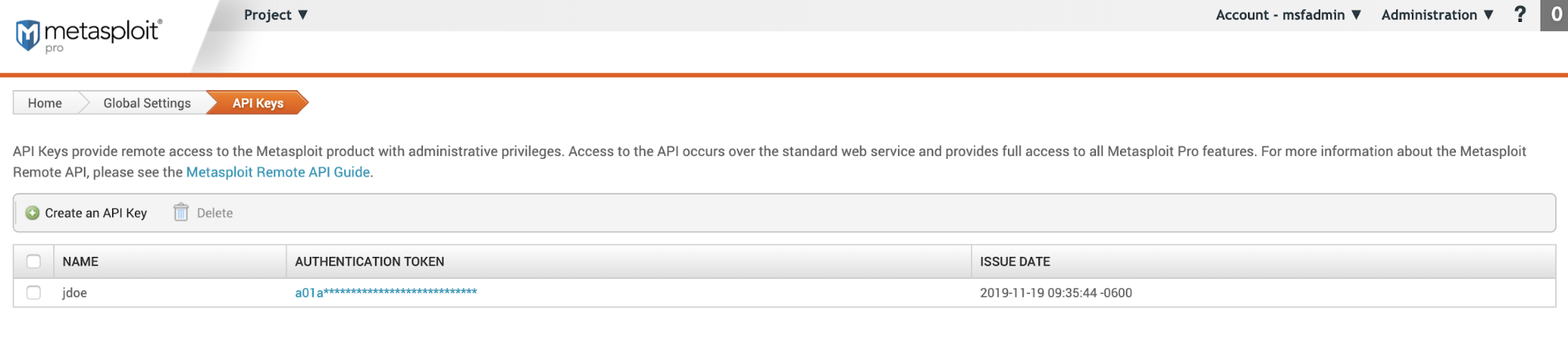
- **Name - The **name given when the API key was created.
- **Authentication Token **- Refers to the API token itself. To see the full text, click on the token link.
- Issue Date - The date the API token was created.
Post-Exploitation Macros
When a vulnerability is successfully exploited, run a module in an open session. You can run one or more modules at a time.
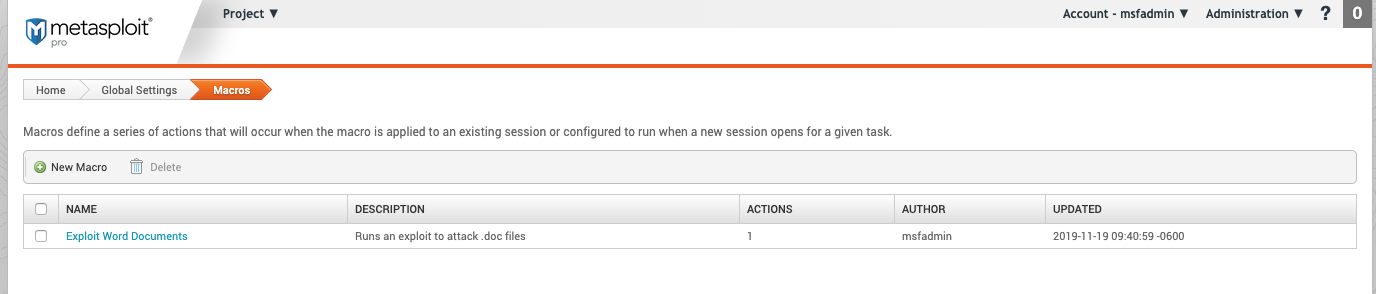
- Name - The name of the macro. User created.
- Description - The description of the macro. User created.
- Actions - The number of actions or steps the macro takes.
- Author - The user that created the macro.
- Updated - The date and time the macro using
yyyy-mm-dd hr:mm:ss -timezone. For example,2019-11-19 10:31:32 -0600.
Persistent Listeners
A listener is a way back into an exploited system. Instead of needing to go through all the exploit steps again, a listener provides a “backdoor”.
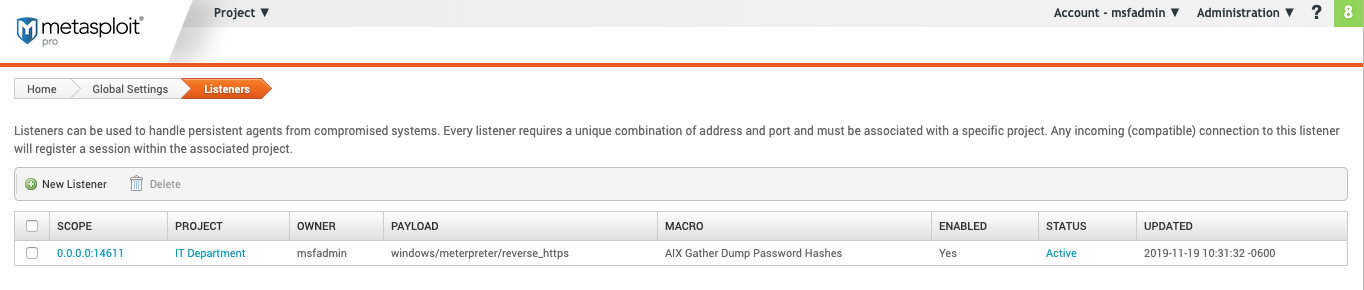
- Scope - The listener address and port.
- Project - The project the listener is used on.
- Owner - The creator of the listener.
- Payload - The payload type
- Macro - If selected, the macro the payload will attempt to run.
- Enabled - If the listeners is enabled.
- Status - The state of the listener:
- Active
- Inactive
- Updated - The last updated date using
yyyy-mm-dd hr:mm:ss -timezone. For example,2019-11-19 10:31:32 -0600.
Nexpose Consoles
Use Nexpose to import data for vulnerability scanning and analysis.
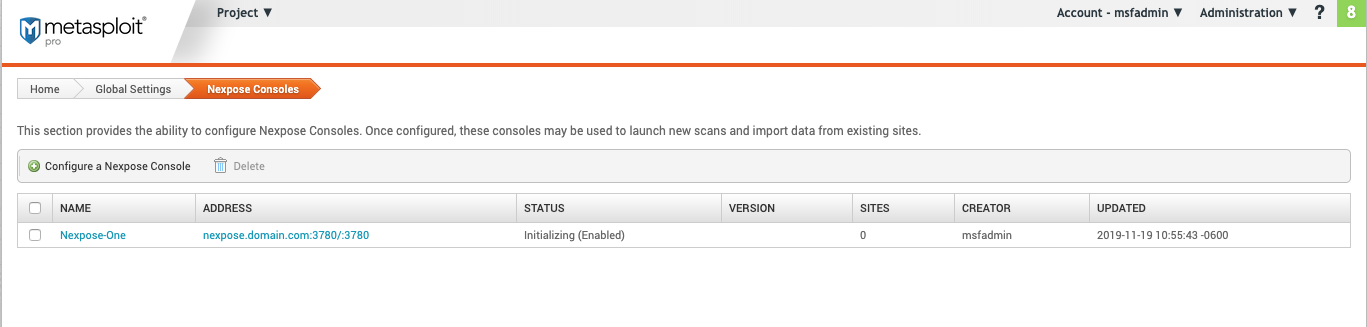
- Name - The Nexpose console name. User created.
- Address - The IP or server address with the port for the Nexpose Security Console.
- Status - The status of the Nexpose Security Console. It will indicate if the console is connected or experiencing issues.
- Version - The software version of the Security Console.
- Sites - The collection of assets targeted for a scan.
- Creator - The user that created the Nexpose console import.
- Updated - The last updated date using “yyyy-mm-dd hr:mm:ss -timezone
. For example,2019-11-19 10:31:32 -0600`.
Stop All Tasks
Stop every running task.
Backups
Create and store backups of projects.
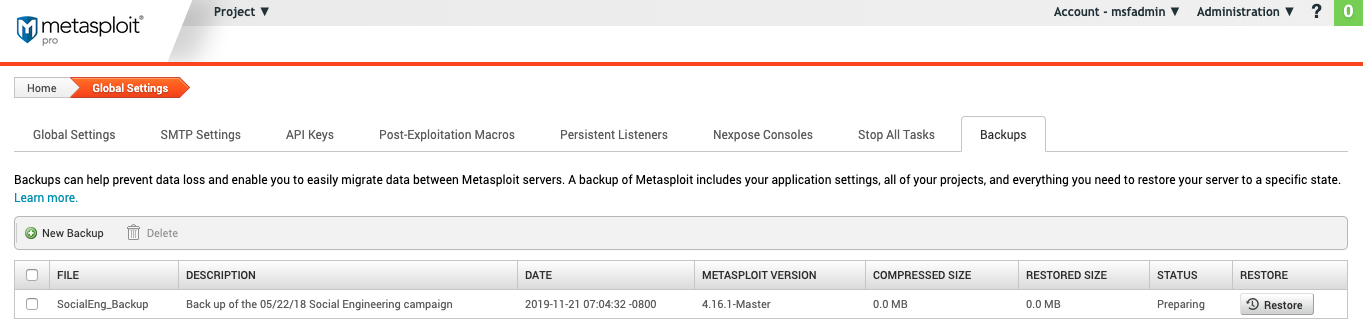
- File - The backup name. User generated.
- Description - The backup description. User generated.
- Date - The date created using
yyyy-mm-dd hr:mm:ss -timezone. For example,2019-11-19 10:31:32 -0600. - **Metasploit Version - The **Metasploit version the backup is based on.
- Compressed Size - The size of the backup file after compression takes place.
- Restored Size -The size of the backup file when it is restored.
- Status -The backup status
- Restore - Click to restore the project to the backup.