The Modules Page
The Modules page is where you can review module information and run a module against your target host.
You can access the following sections from the Modules drop-down:
To access “Modules”, click **Modules **on the page.
Search
After navigating to “Modules”, the search screen is the first page you encounter. From here you can see information such as the operating system and CVE ID.
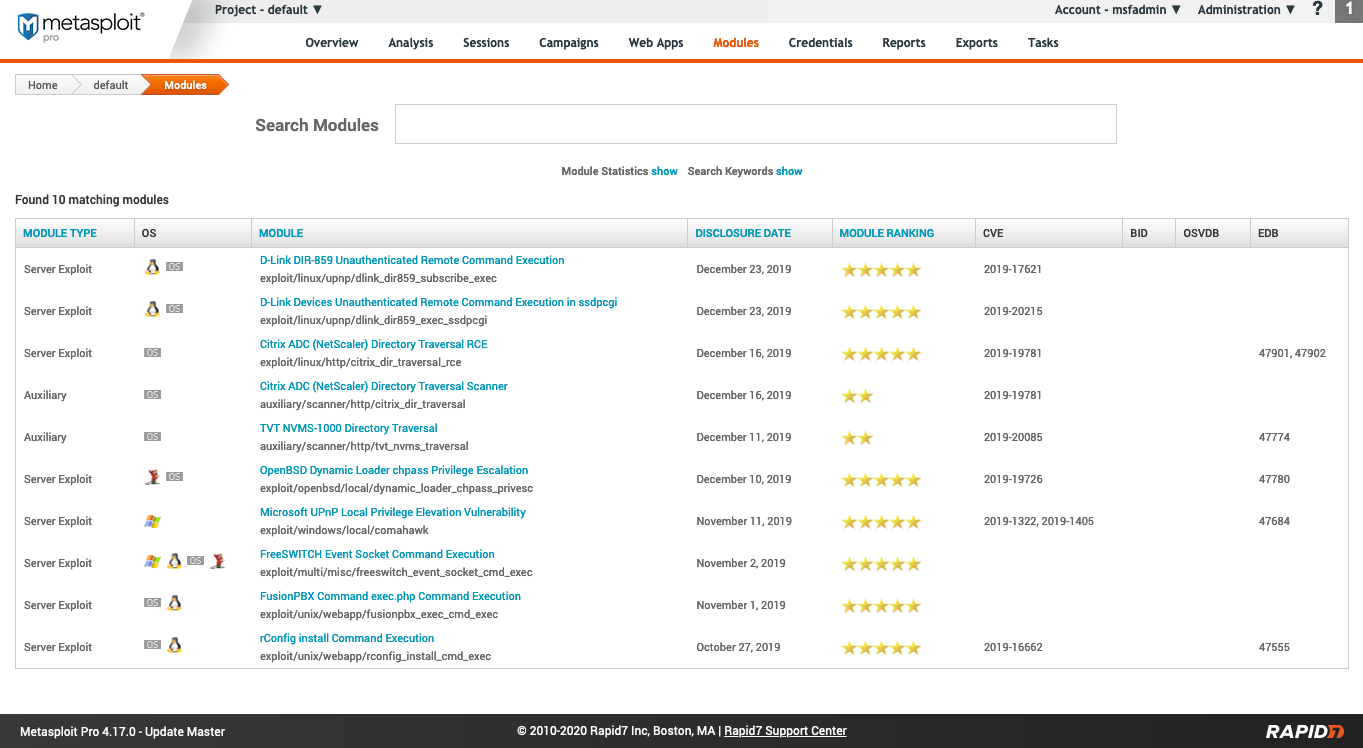
- Module Statistics - Shows the total number of modules and breaks them down by categories such as exploit and auxiliary.
- Search Keywords - The available search options for modules.
- Module Type - The type of module.
- OS - The operating systems the module targets.
- Module - The module name and path in Metasploit. To run a module, click on the name.
- Disclosure Date - The date the original exploit was reported.
- Module Ranking - The rank is determined based on its potential impact to the target system. See Module Rankings below.
- CVE - This field contains the Common Vulnerabilities and Exposures (CVE) ID of the exploit if it exists. Once a set of criteria is met, an exploit gets a CVE ID. See https://cve.mitre.org/about/faqs.html for more information about the CVE system.
- BID - The Bugtraq ID. See https://www.securityfocus.com/archive/1/description#0.1.1 for more information.
- OSVDB - Open Sourced Vulnerability Database. This database is now defunct. This field will be empty. https://blog.osvdb.org/
- EDB - The Exploit Database ID. https://www.exploit-db.com/ .
Module Rankings
Modules can have one of the following rankings listed here in descending order of reliability:
- ExcellentRanking - The exploit will never crash the service. This is the case for SQL Injection, CMD execution, RFI, LFI, etc. No typical memory corruption exploits should be given this ranking unless there are extraordinary circumstances (WMF Escape() ).
- GreatRanking - The exploit has a default target AND either auto-detects the appropriate target or uses an application-specific return address AFTER a version check.
- GoodRanking - The exploit has a default target and it is the “common case” for this type of software (English, Windows 7 for a desktop app, 2012 for server, etc).
- NormalRanking - The exploit is otherwise reliable, but depends on a specific version and can’t (or doesn’t) reliably auto-detect.
- AverageRanking - The exploit is generally unreliable or difficult to exploit.
- LowRanking - The exploit is nearly impossible to exploit (or under 50% success rate) for common platforms.
- ManualRanking - The exploit is unstable or difficult to exploit and is basically a DoS. This ranking is also used when the module has no use unless specifically configured by the user (e.g.: exploit/unix/webapp/php_eval ).
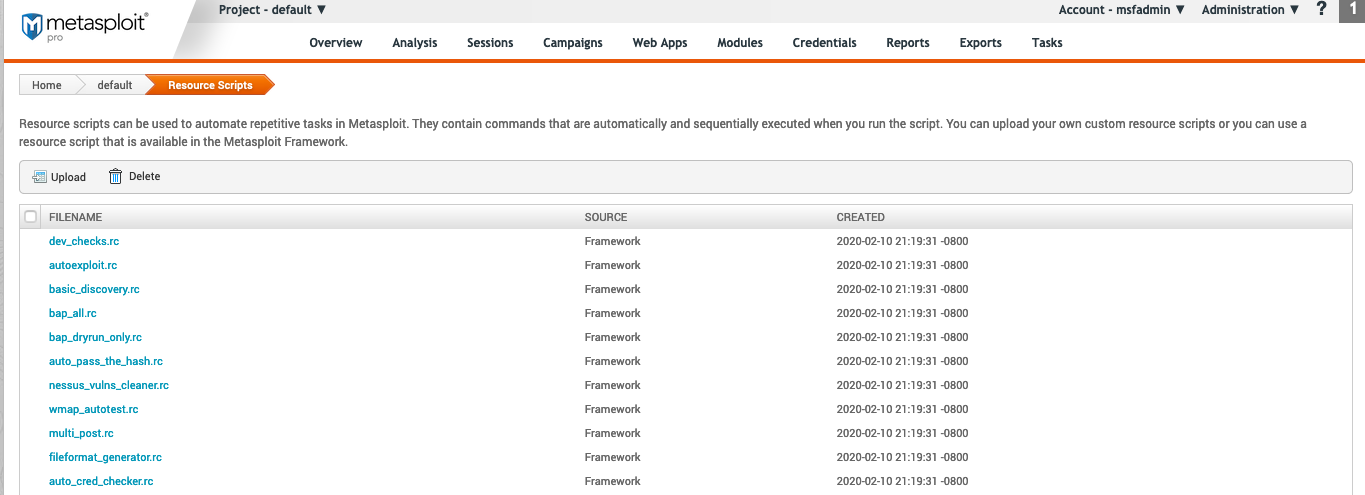
Resource Scripts
To access Resource Scripts, navigate to “Modules” then choose Resource Scripts from the dropdown.
Resource Scripts are used to automate tasks in Metasploit. They contain a set of commands that are automatically and sequentially executed when you load the script in Metasploit. To learn more about using resource scripts, see the Resource Scripts page.
MetaModules
To access MetaModules, navigate to “Modules” then choose MetaModules from the dropdown. MetaModules extend the capabilities of modules in Metasploit Pro.
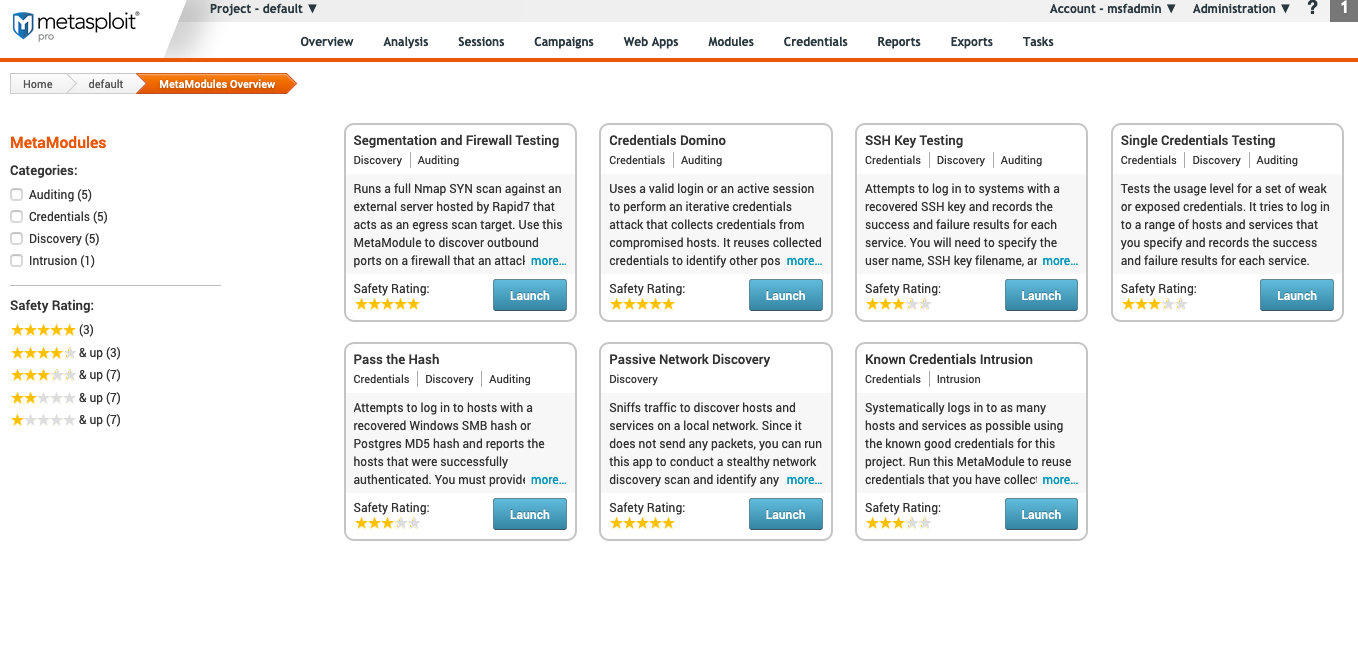
- Segmentation and Firewall Testing - Runs an Nmap SYN scan against an egress target to identify the ports that allow egress traffic out of the network.
- Credentials Domino - Uses a valid login or an active session to perform an iterative credentials attack that collects credentials from compromised hosts.
- SSH Key Testing - Attempts to log in to systems on a target range with a recovered private SSH key and reports the hosts that it was able to successfully authenticate.
- Single Credentials Testing - Attempts to use a known credential pair to authenticate services on a range of target hosts and reports the ones it was able to authenticate.
- Pass the Hash - Attempts to log in to systems with a recovered password hash and user name and reports the hosts it was able to authenticate.
- Passive Network Discovery - Stealthily monitors broadcast traffic to identify the IP addresses of hosts on the network and updates the Hosts page with the information that it finds.
- Known Credentials Intrusion - Uses known credentials to compromise hosts across the entire network. You can run this MetaModule to reuse credentials that you obtained from bruteforce attacks, phishing attacks, or exploited hosts.