The Payload Generator
The Payload Generator enables you to create a properly formatted executable that you can use to deliver shellcode to a target system without the use of an exploit. The Payload Generator provides a guided interface that walks you through the process of generating a dynamic payload or a classic payload. Depending on the type of payload you choose to build, it will display the applicable options that you can use to customize the payload.
You use the payload generator when you need to build a standalone binary file that delivers a custom-built payload. Binary files, such as .exe and .bin files, are typically delivered through client-side exploits, such as phishing emails or social engineering attacks, which means that you will probably need to be able to bypass anti-virus detection to execute the shellcode on the target system. To help reduce anti-virus detection, the Payload Generator enables you to do things like encode the payload and use a dynamic executable.
Payloads are generated globally, outside the context of a project. This means that payloads are generated on the fly, can only be downloaded once, and are not tied to a particular project. They are useful when you need to quickly generate an executable payload for a single use. Accessing the Payload Generator You access the Payload Generator from the Global Tools area of the web interface. To access the Payload Generator, go to the Projects List. Find the Global Tools area and click on the Payload Generator widget to launch it.
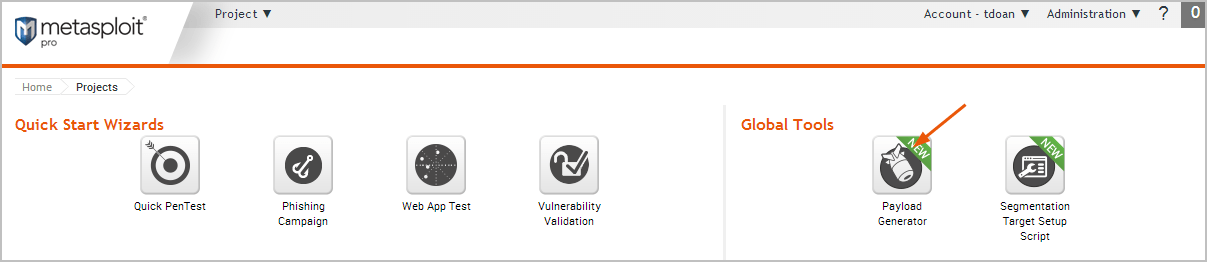
Building Dynamic Payloads The Payload Generator enables you to build a Windows executable that uses a dynamic stager that is written entirely in randomized C code. The dynamic stager does not use an executable template or shellcode, which allows it to behave similarly to a standard Windows application. The resulting executable is different each time it is generated, so that anti-virus software will not be able to identify the stager as Metasploit shellcode.
Metasploit Pro offers dynamic payloads for Windows platforms only. These payloads are compatible with any Windows x86 and x86_64 system.
Dynamic Payload Options
Type of Payload
This is the type of payload that the exploit will deliver to the target. Choose one of the following payload types:
- Command - A command execution payload that enables you to execute commands on the remote machine.
- Meterpreter - An advanced payload that provides a command line that enables you to deliver commands and inject extensions on the fly.
Stager
The stager is what the payload uses to set up the network connection between the target machine and the payload handler running on the Metasploit server. The stager enables you to use a smaller payload to load and inject a larger, more complex payload called the stage.
Choose one of the following stagers:
- Reverse TCP - Creates a connection from the target machine back to the Metasploit server over TCP.
- Bind TCP - Binds a command prompt to a listening port on the target machine so that the Metasploit server can connect to it.
- Reverse HTTP - Creates a connection from the target machine back to the Metasploit server over HTTP.
- Reverse HTTPS - Creates a connection from the target machine back to the Metasploit server over HTTPS.
Stage
Specifies the payload that is delivered by the stager.
LHOST
Defines the IP address the payload connects back to. (Reverse connections only)
LPORT
Defines the port the payload connects back to.
RHOST
Defines the port that the listener binds to. (Bind connections only) Generating Dynamic Payloads
- From the Projects page, launch the Payload Generator.
- Select the Dynamic Payload option.
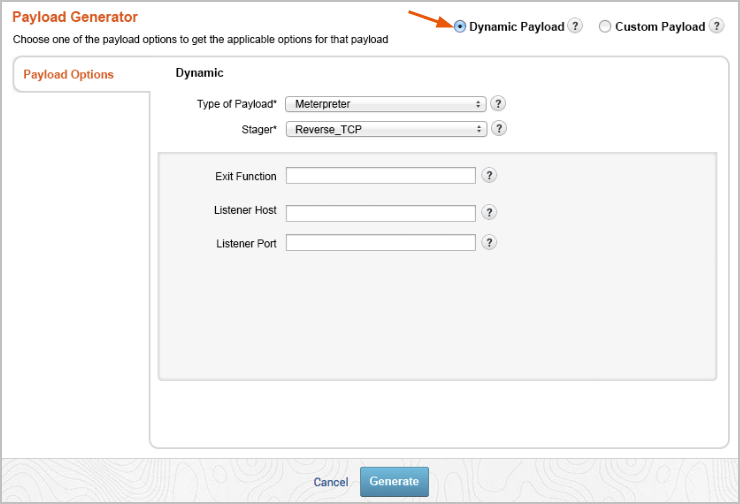
- Click the Stager dropdown and choose one of the following: Reverse TCP, Bind TCP, Reverse HTTP, or Reverse HTTPS.
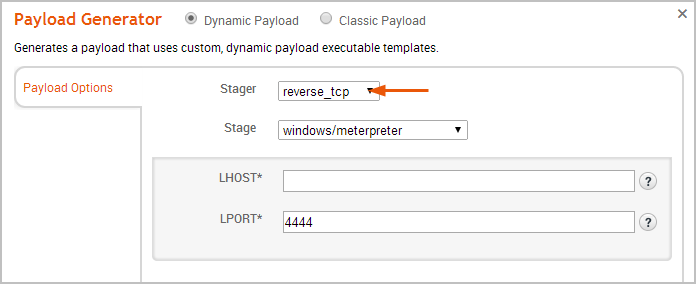
- Click the Stage dropdown and choose the stage you want the stager to download.
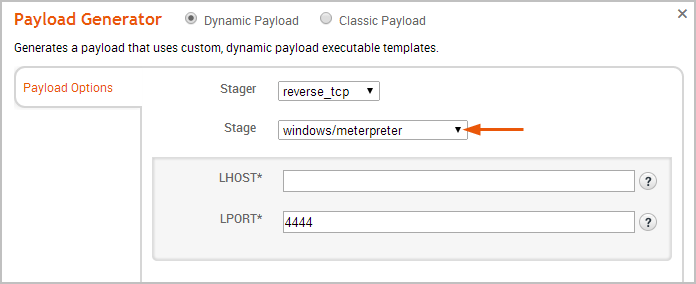
The list will display applicable stages for the stager you have selected.
- Enter the IP address that you want to the payload to connect back to in the LHOST field. (Reverse connections only)
- Enter the port that you want the payload to connect back to in the LPORT field.
- Enter the port that you want the listener to bind to in the RHOST field. (Bind connections only)
- Click Generate.
If the payload generates without error, a window appears and alerts you that the payload has been generated and is ready for you to download. Click Download Now to automatically download the executable.
If your browser is not configured to automatically download files, a dialog window will appear and prompt you to save or run the file. You will need to save the executable to your computer. Building Classic Payloads A classic payload is built the traditional way—from scratch. The Payload Generator is particularly useful when you need to build a payload in various formats and encode them with different encoder modules. You can build a variety of payloads based on the operating system, architecture, type of connection, and output format that you need for a particular host.
Classic Payload Options
The following are the most common options that are available for classic payloads:
Platform
Specifies the platform.
The following platforms are supported: AIX, Android, BSD, BSDi, Firefox, Java, Linux, Netware, NodeJS, OSX, PHP, Platform, Python, Ruby, Solaris, Unix, and Windows.
Architecture
Specifies the processor architecture.
The Payload Generator shows you the options that are available for the architecture you have selected.
The following architectures are supported:
- AIX
- Android
- BSD sparc and x86
- BSDi
- Firefox
- Java
- Linux armle, cbea, cbea64, java, mipsbe, mipsle, ppc, ppc64, x86, and x86_64
- Netware
- NodeJS
- OSX armle, java, ppc, x86, and x86_64
- PHP armbe, armle, cbea. cbea64, cmd, dalvik, firefox, java, mips, mipsbe, mipsle, nodejs, php, ppc, ppc64, python, ruby, sparc, x86, and x86_64
- Solaris java, sparc, and x86
- Unix cmd, java, and tty
- Windows cmd, java, x86, and x86_64
Payload
Specifies the type of payload that the exploit will deliver to the target.
The Payload Generator shows you the payloads that are available for the platform you have selected.
Stager
Specifies the type of stager that the payload will use to set up the network connection between the target machine and the payload handler running on the Metasploit server.
The stager enables you to use a smaller payload to load and inject a larger, more complex payload called the stage.
The list of stagers that are available will vary based on the platform and architecture that you have selected.
Exit Function
Specifies the function to call when a payload completes so that it can safely exit a thread.
Choose one of the following exit functions:
- Thread - Calls the ExitThread API function.
- Process - Calls the ExitProcess API function.
- SEH - Restarts the thread when an error occurs.
- None - Enables the thread to continue executing so that you can serially run multiple payloads together.
Listener Host
Defines the IP address that you want the target host to connect back to.
Listener Port
Defines the port that you want to use for reverse connections.
Added Shellcode
Enables you to specify an additional the shellcode file that will run in a separate, parallel thread while the main thread executes the payload.
Size of NOP Sled
Defines the length of the NOP sled you want to prepend to the payload.
Each NOP you add to the payload adds 1 byte to the total payload size.
The options that are available for a payload vary based on its architecture, platform. and payload type.
Generating PowerShell Payloads PowerShell payloads provide you with the ability to execute PowerShell scripts on compromised systems. To generate a PowerShell payload, generate a classic payload and deselect the stager option.
At a minimum, the payload should use the following settings:
- Platform - Windows
- Payload - windows/bind_shell_tcp
- Output type - Executable file
- Format - psh, psh-net, psh-reflection, or psh-cmd
The generated payload for psh, psh-net, and psh-reflection formats have a .ps1 extension, and the generated payload for psh-cmd format has a .cmd extension.
Encoding the Payload
An encoder enables you to eliminate bad characters from a payload so that you can use it with a particular exploit. A character is considered to be bad if some aspect of the exploit makes it impossible to use. For example, many applications interpret a null byte as the end of a string. If it appears anywhere in the payload, the shellcode will terminate before it completes and cause the payload to fail. In this particular case, you can apply an encoder that removes null bytes from the payload.
An encoder does not guarantee that a payload will evade anti-virus detection, but it will ensure a payload does not contain bad characters that can cause issues with an exploit or produce unintended results.
The following are examples of common bad characters:
- Spaces
- Carriage returns
- Line feeds
- Tabs
- Null bytes
There are many different encoders that are available in the Metasploit Framework, which can be used for various situations. For example, some encoders, such as alpha_mixed and alpha_lower, can be used to replace characters with all alphanumeric characters, which can be useful for applications that only accept text-based characters as input. Other encoders, such as the very reliable and highly ranked shikata_ga_nai, are polymorphic XOR encoders that use an XOR encrypting scheme to help evade detection.
Encoding options are only available for the following platforms:
- AIX
- BSD sparc
- BSD x86
- BSDi
- Linux mipsbe
- Linux mipsle
- Linux ppc
- Linux x86
- Linux x86_64
- Netware
- OSX ppc
- OSX x86
- OSX x86_64
- PHP
- Platform sparc
- Platform x86
- Platform x86_64
- Python cmd
- Solaris sparc
- Solaris x86
- Unix cmd
- Windows cmd
- Windows x86
- Windows x86_64
Encoding Options
You can use the following options to encode a payload:
Encoder
Sets the encoder that is used to encode the payload.
The Payload Generator only displays the encoders that are applicable to the platform and architecture you have selected.
Number of Iterations
Specifies the number of times that you want to encode the payload.
The more times you encode a payload, the larger the payload becomes. You may need to modify the number of iterations if it causes the payload to exceed the maximum payload size.
Maximum Size of Payload
Defines the maximum size of the resulting payload in bytes.
The maximum size takes precedence over the encoding iterations. If the encoder causes the payload to exceed the maximum size you have specified, the Payload Generator will display an error message.
To fix the error, you can select a new encoder, modify the number of iterations, or set a different maximum payload size.
Bad Characters
Specifies the list of characters that you do not want to appear in the payload, such as spaces, carriage returns, line feeds, tabs, and null bytes.
You must enter the values in hex.
You can copy and paste the hex characters into the text box. The text editor will attempt to format the hex
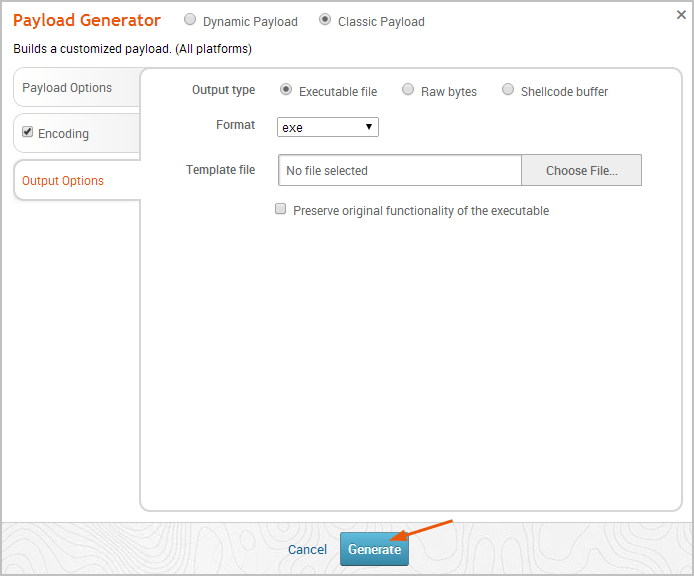
Output Options
You can use the following options to create the binary file:
Output type
Specifies the output type for the payload.
Choose from the following types: executable, raw bytes, or shellcode buffer.
Format
Specifies the format to use to output the payload.
Choose from the following formats: asp, aspx, aspx-exe, dll, elf, elf-so, exe, exe-only, exe-service, exe-small, hta-psh, loop-vbs, macho, msi, msi-nouac, osx-app, psh, psh-net, psh-reflection, psh-cmd, vba, vba-exe, vba-psh, vbs, and war.
Preserve original functionality of executable
Enables you to inject the payload into an existing executable and retain the original functionality of the original executable. The resulting executable will function like the original one.
You should only enable this option only if you have uploaded a template file.
Template file
Specifies the executable template that you want to use to run in the main thread. For example, you can embed the payload in an executable, like calc.exe. When the executable runs, it creates a separate thread for the payload that runs in the background and continues to run calc.exe in the main thread. Generating a Classic Payload The configuration of a classic payload will vary based on the platform, architecture, payload, stager, and stage that you have selected. The following instructions will provide an overview of the steps that you need to perform to generate a classic payload—such as a Linux Meterpreter Reverse TCP payload.
- From the Projects page, launch the Payload Generator.

- Select the Classic Payload option.
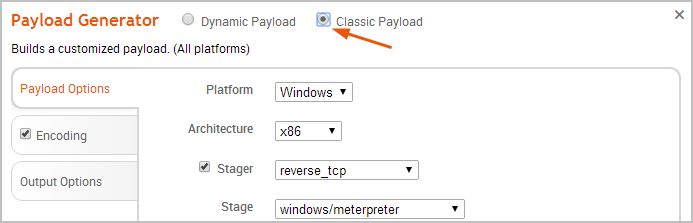
- Click the Platform dropdown button and choose one of the available platforms.
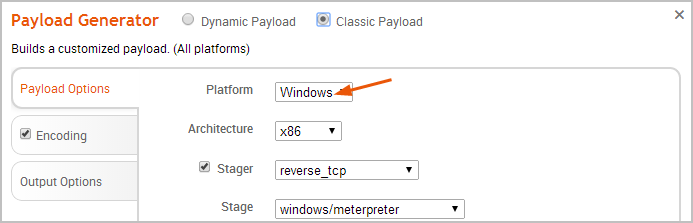
For a list of supported platforms, see Payload Options.
- Click the Architecture dropdown button and select one of the available processor architecture types.
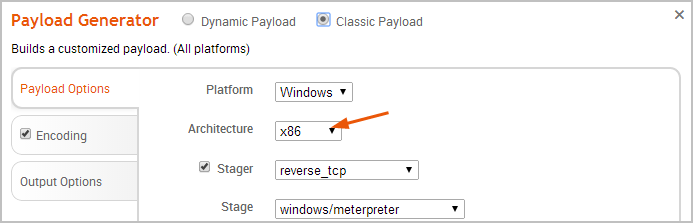
The list of architecture types will vary based on the platform that you have selected. Some platforms, such as Android and AIX, will not have a platform.
From this point on, the steps will vary depending on the platform, architecture, and payload you have selected. Generally, you will need to specify the LHOST (reverse), LPORT, and RHOST (bind) that the payload uses, as well as the output options for the executable. You can also do things like encode the payload.
When you are ready to build the payload, click the Generate button. The Generate button will be active if all required options for the payload are configured.
If the payload generates without error, a window appears and alerts you that the payload has been generated and is ready for you to download. Click Download Now to automatically start the download process.
If your browser is not configured to automatically download files, a dialog window will appear and prompt you to save or run the file. You will need to save the payload to your computer.