The Sessions Page
The Sessions page is where you can see any open shells from a successful exploit or bruteforce attack . You can also see a list of open and closed session or click into a session and run a module.
Click Sessions from the top menu to access any active or closed sessions.
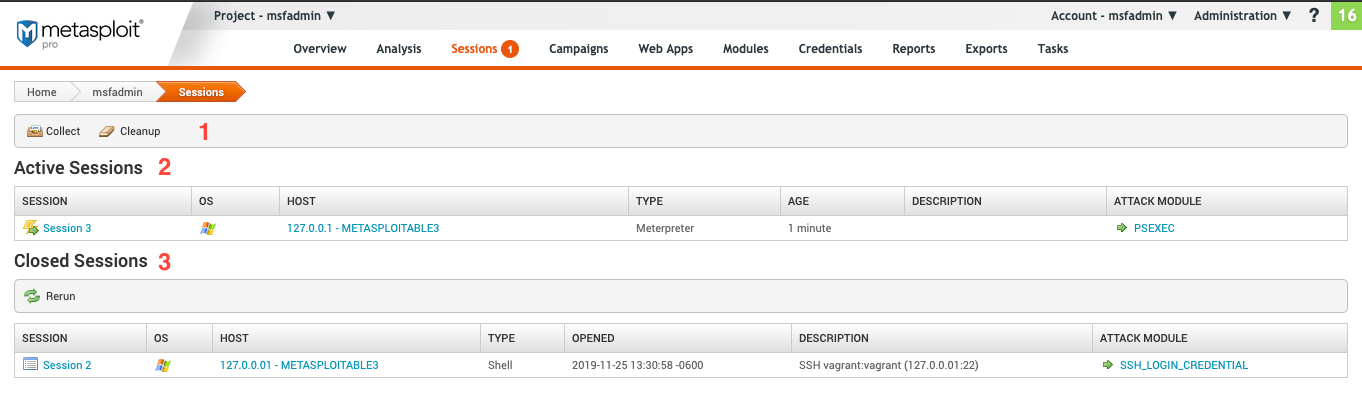
The page is broken into three sections:
Menu
From the menu, you can collect evidence or close open sessions.
- **Collect - **Collect will try to gather information about the exploited host. This includes credentials, screenshots, and text files. You will be able to configure the options after clicking Collect. You can view collected evidence from Tasks, Analysis > Captured Data or in the Collected Evidence Report .
- Cleanup - Closes the open session.
Active Sessions
The “Active Sessions” tab displays a list of any open sessions for an exploited host.
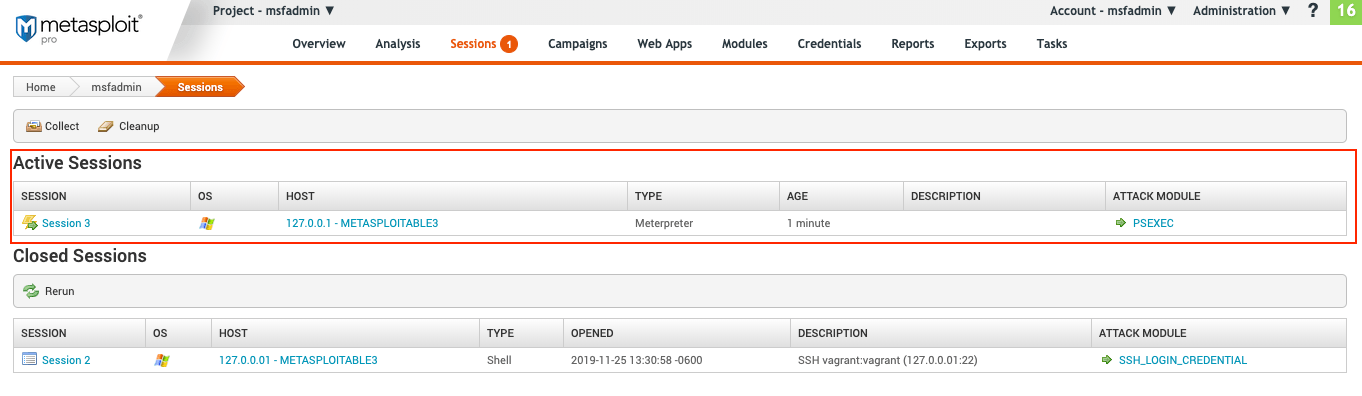
- Session - This column refers to the session number. Sessions are assigned a number based on when the session is opened, the first of which is assigned an ID of
1. Clicking Session will allow you to pick which modules to run during the open sessions or use a terminal instead. - OS - Exploited host operating system.
- Host - Name of the exploited host. Clicking the host will take you to a details page, where you can see the host status and detailed information about the target host.
- Type - The session type opened. The session type will be either a shell or Meterpreter session.
- Age - The amount of time the session has been opened.
- Description - The description of the credential type used to open the session. If the credential type is unknown, this is left blank.
- Attack Module - Module used to exploit the target host and open a session. Clicking the module will take you a dedicated page where you can run the module on a different target host and see more information about the module.
Closed Session
The “Closed Sessions” tab displays a list of any closed session for an exploited host.
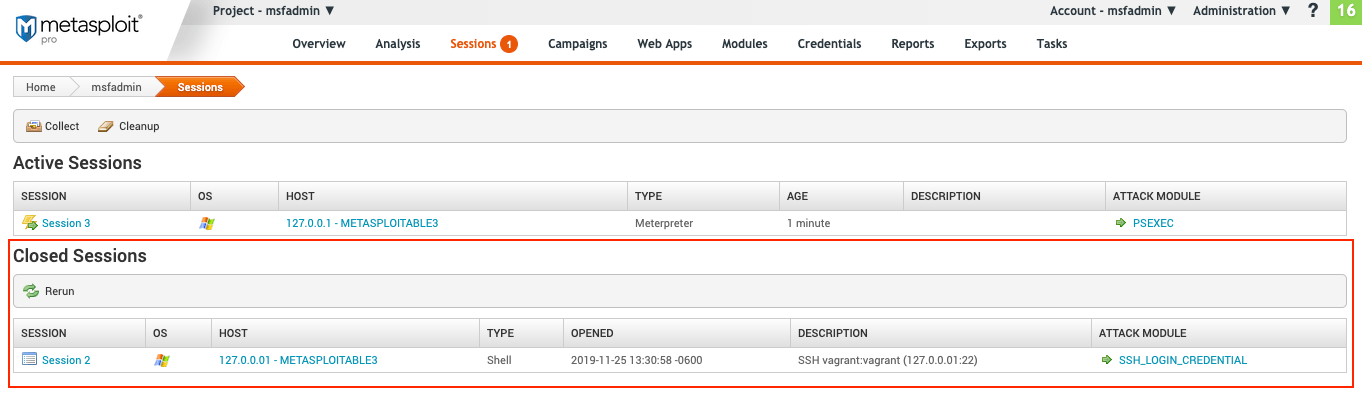
- Session - This column refers to the session number. Sessions are assigned a number based on when the session is opened, the first of which is assigned an ID of
1. Clicking Session will allow you to pick which modules to run during the open sessions or use a terminal instead. - OS- Exploited host operating system.
- Host - Name of the exploited host. Clicking the host will take you to a details page, where you can see the host status and detailed information about the target host.
- Type - The session type opened. The session type will be either a shell or Meterpreter session.
- Opened - The date and time the session was opened using format
yyyy-mm-dd hr:mm:ss -timezone. - Description - The description of the credential type used to open the session with the host IP address. If the credential type is unknown, this is left blank.
- Attack Module - Module used to exploit the target host and open a session. Clicking the module will take you a dedicated page where you can run the module on a target host and see more information about the module.