The Analysis Page
During a discovery scan, Metasploit Pro automatically adds the host data to the project. You can review the host data to obtain a better understanding of the network and to determine the best way to exploit each target.
Metasploit Pro offers a couple of different host views. Host views provide visibility into the data that a project contains. Each view provides a different way in which you can view the metadata and findings for hosts within a project.
The following host views are available:
- Project view - Provides a high-level view of all the hosts and data that are stored in the project. To access the project view, click on the Analysis tab. The project view initially shows the Hosts list, which displays the fingerprint and enumerated ports and services for each host. In addition to the Hosts list, you can view the notes, services, vulnerabilities, and captured data from the project view. To access these other views, you can click on their tabs from the project view.
- Single host view - Displays the details for a specific host, such as the services, sessions, vulnerabilities, credentials, captured data, notes, file shares, tags, exploit attempts, available modules, and source. To access the single host view, click on a host IP address.
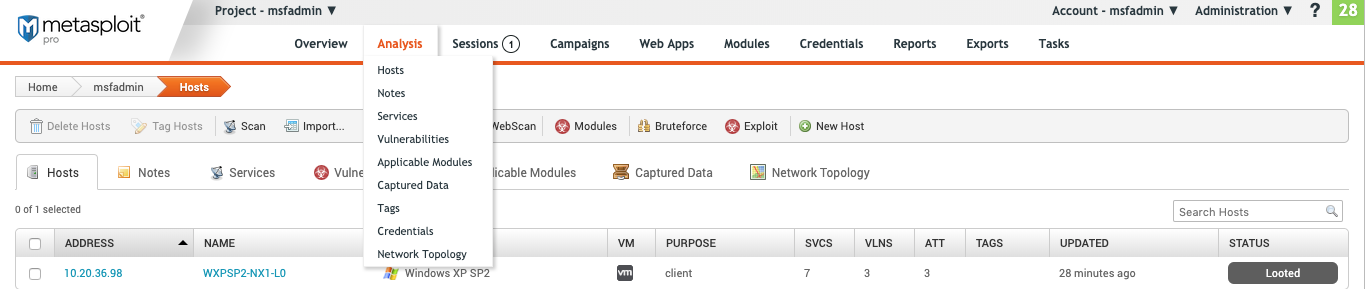
Analysis
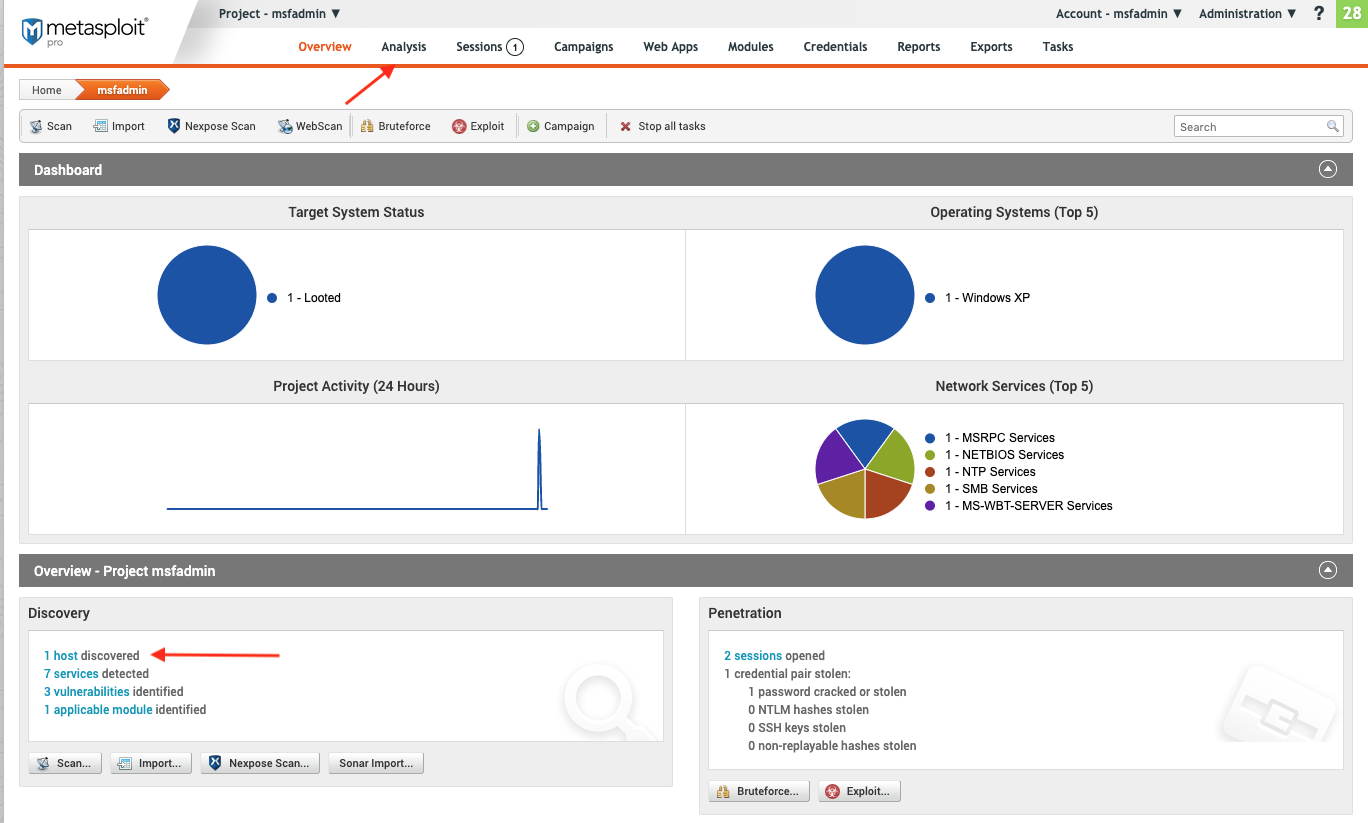
There are two ways to access the “Analysis” home page. Both options will lead to a “Hosts” page.
- From the project page home page, hover over “Analysis” and click **Hosts in the dropdown. **
- From the main menu, click **Analysis. **
Analysis Page
Analysis is where you can exploit hosts, scan for new hosts and run modules. The top tool bar is where you will find things to do such as scan or import. The second bottom toolbar is where you will find information about your selected host.
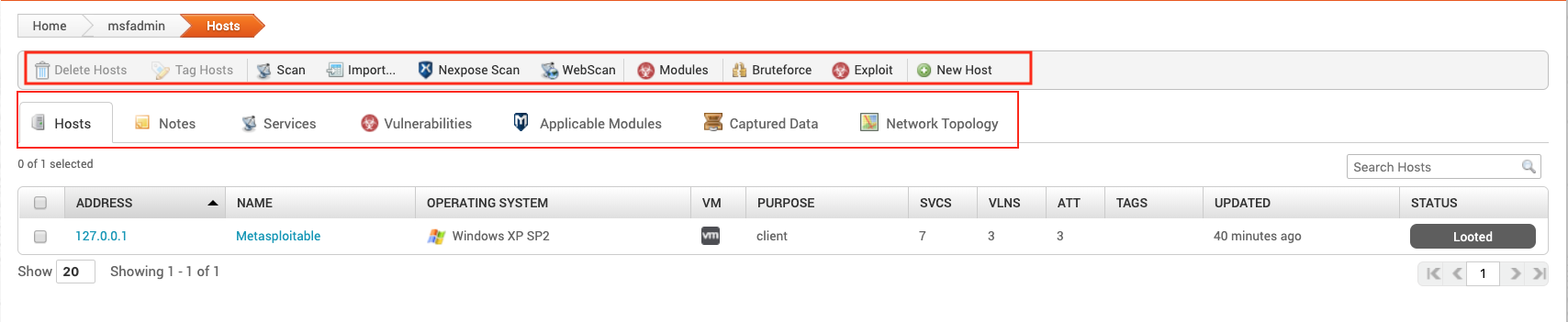
Delete Hosts
Remove a host from the project.
Tag Hosts
Tags are a label that you create to organize hosts. For example you can create a tag ‘High’ and add all high risk hosts to that tag. Click on the tags to see all hosts with that tag.
Scan
Run a discovery scan for vulnerabilities.
Import
Import data from Nexpose, Sonar or file.
Nexpose Scan
Use an existing Nexpose console to run a vulnerability scan .
Modules
Search for any modules available in Metasploit Pro. Any modules found matching the hosts vulnerabilities are listed here. You can then run modules against the target host.
Bruteforce
Use credentials to authenticate against a host. Metasploit Pro will look for valid logins and try to extract the information.
Exploit
Use exploits against found host vulnerabilities.
New Host
Add a new host manually to the existing project.
Hosts
Lists the hosts scanned.
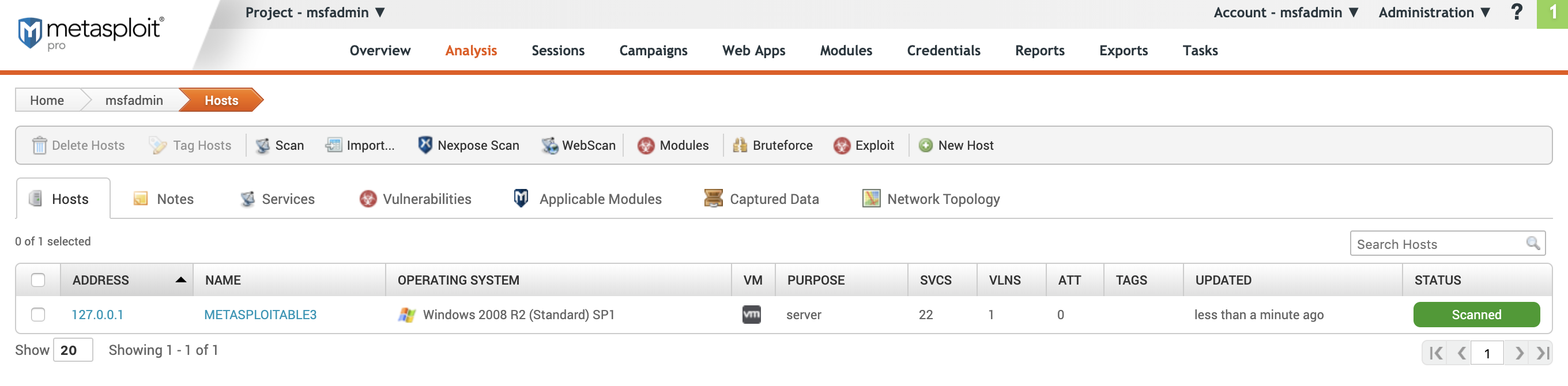
- ADDRESS - IP address of the host
- **NAME ** - Name of the Host . This is populated from the target.
- OPERATING SYSTEM - Operating system detected during the scan
- VM - Indicates whether the host is a virtual machine
- PURPOSE - Indicates whether the host is client or server-side
- SVCS - Number of services found on the host
- VLNS - Number of vulnerabilities found on the host
- ATT - Number of attempts to exploit a vulnerability.
- TAGS - Tags added to the host
- UPDATED - Date and time the host was last used by the project
- STATUS - The status of the host .
Notes
Notes are automatically populated during the scan. Notes contain any information returned by the module. For example, the discovery scan returns Nmap traceroute and os.fingerprint.
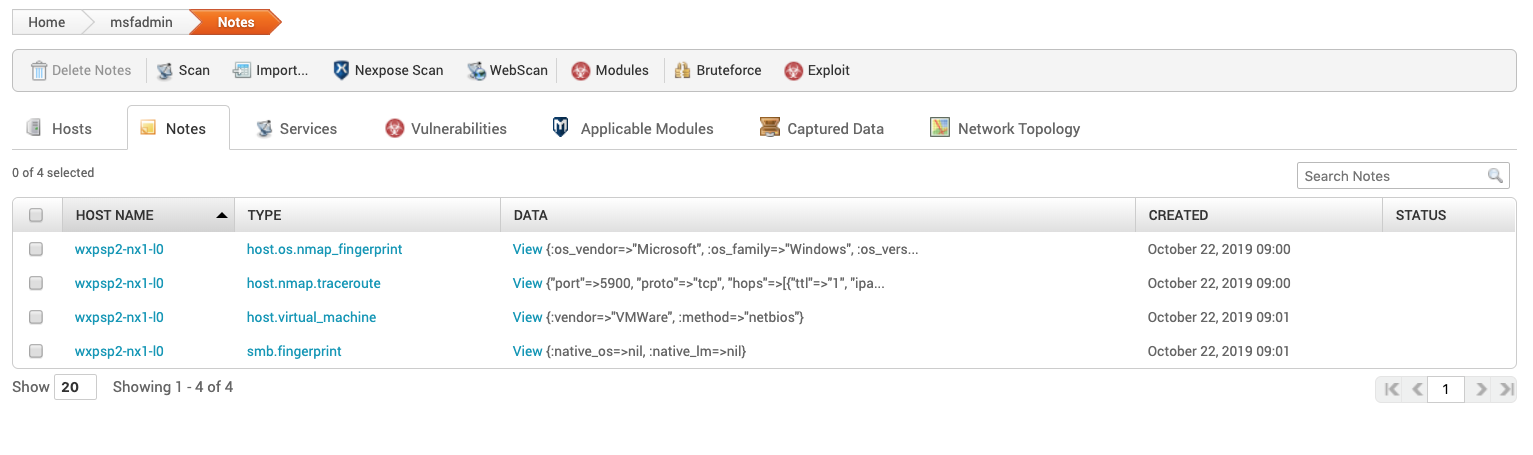
- HOST NAME - The name of the host
- TYPE - The note type can be any value or it can be a system defined type, such as
fingerprint.match.To create a note use the Pro Console . - DATA - Contents of the note
- CREATED - Date the note was created.
- STATUS - The status of the host .
Services
Access this tab to view a list of services exposed on a network.
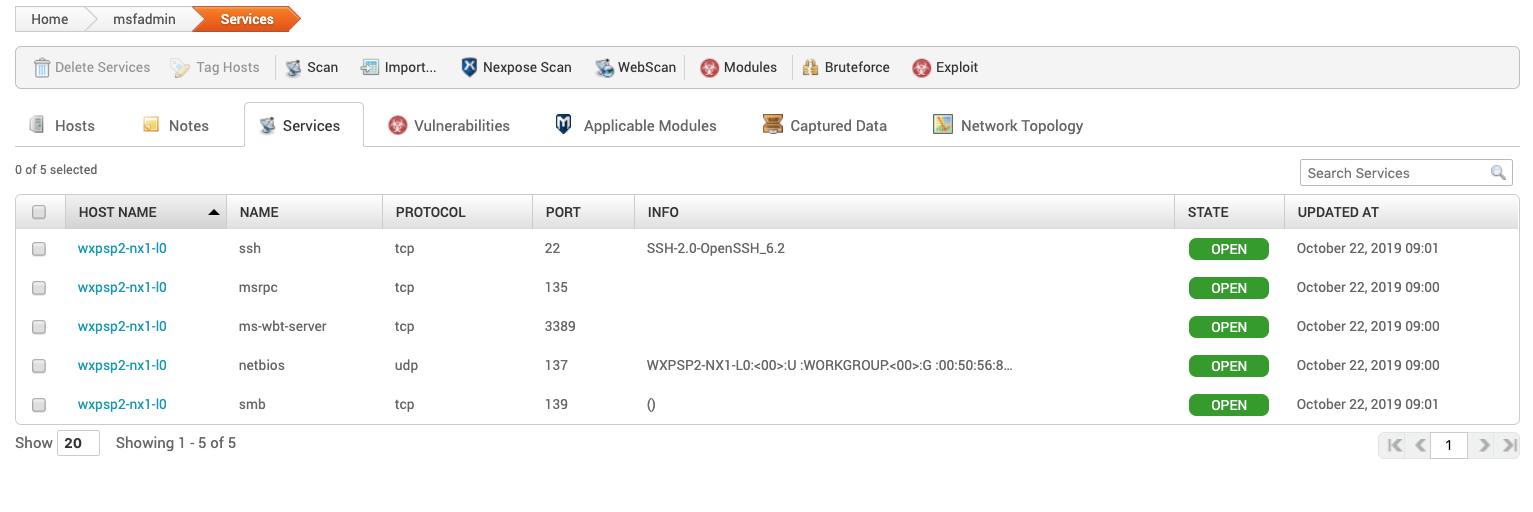
- HOST NAME - Name of the host
- NAME - Type of service
- PROTOCOL - Protocol the service is running on
- PORT - Port the service is running on
- INFO - Any information available about the service. This can be blank since not all scanners or imports do fingerprinting on a service. Some services are not easy to get a fingerprint on.
- STATE - Current state of the service .
The following is a list of the basic states Nmap offers. If you import data, the states may vary.
- Open
- Closed
- Filtered
- Unfiltered
- Open|Filtered
- Closed|Filtered
- UPDATES AT - Date and time the service was updated
Vulnerabilities
This tab contains a list of any vulnerabilities found during the discovery scan.
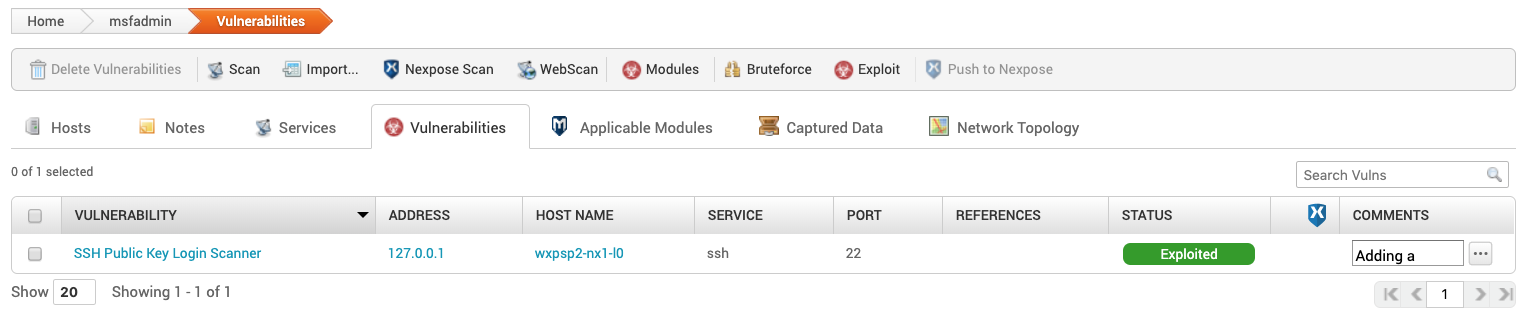
- VULNERABILITY - Name of the vulnerability
- ADDRESS- IP address of the host
- HOST NAME - The host name
- SERVICE - The exposed service the vulnerability targets
- PORT - The port the vulnerability can be run on
- REFERENCES - If there are web references to the vulnerability, they will be linked here.
- STATUS - Current status of the vulnerability
- EXPLOITED
- UNTRIED
- FAILED
- NOT_EXPLOITABLE
- NEXPOSE STATUS - If the vulnerability has been pushed to Nexpose
- COMMENTS - Comments on vulnerability
Applicable Modules
Click this tab to view any modules related to the hosts. Not every host will have a module listed, only those with known vulnerabilities.
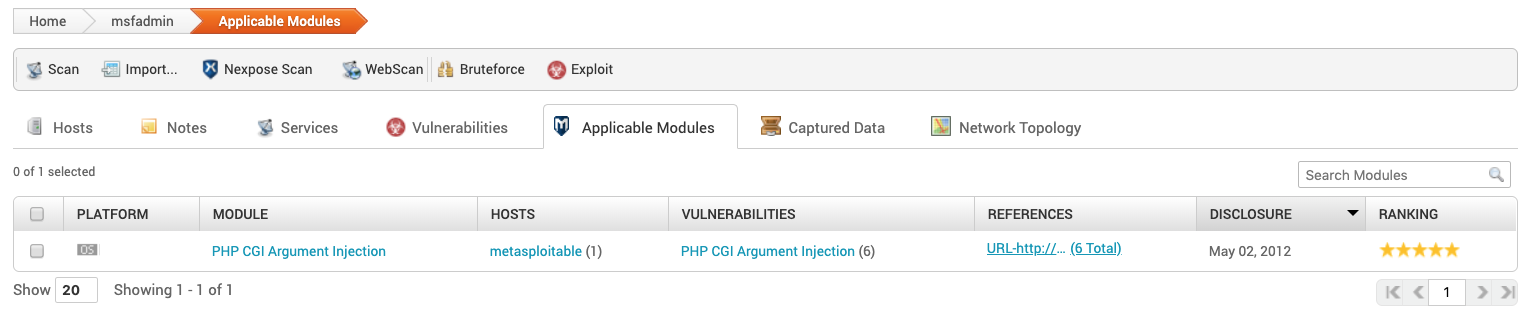
- PLATFORM - OS the module is for
- MODULE - Name of the module
- HOSTS- Host the module applies to
- VULNERABILITIES - Name of the vulnerability found
- REFERENCES - Links to web references associated with the vulnerability.
- DISCLOSURE - Date the vulnerability was reported
- RANKING- The reliability ranking of the module. The higher the rank, the less likely it is to crash when running.
Captured Data
During an open session, data about the host can be collected. Use this data in theCollected Evidence Report .
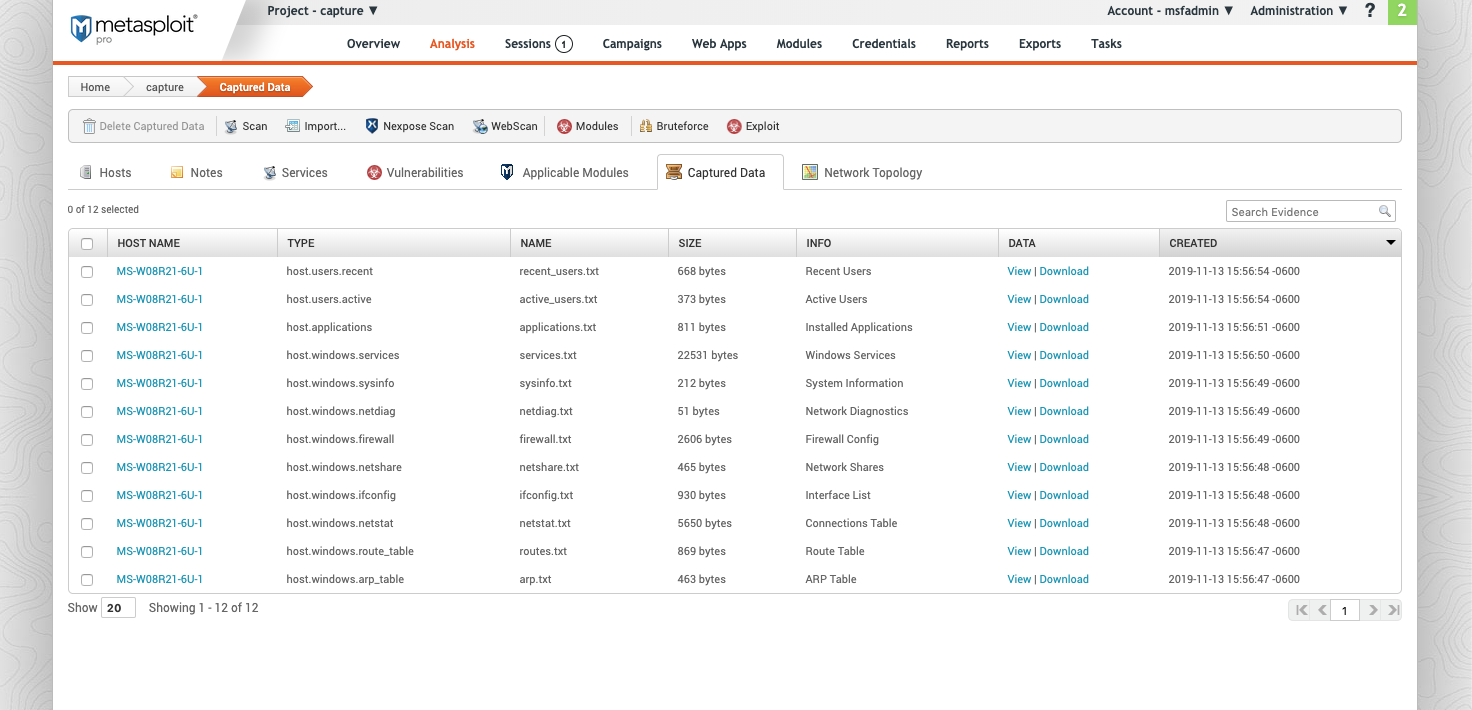
- HOST NAME - The name of the host
- TYPE - Type of evidence collected
- NAME - Name of artifact captured and file type
- SIZE- Size of the data files collected
- INFO - Description of information captured
- DATA - Links to either view or download the data
- CREATED - Date the evidence was collected
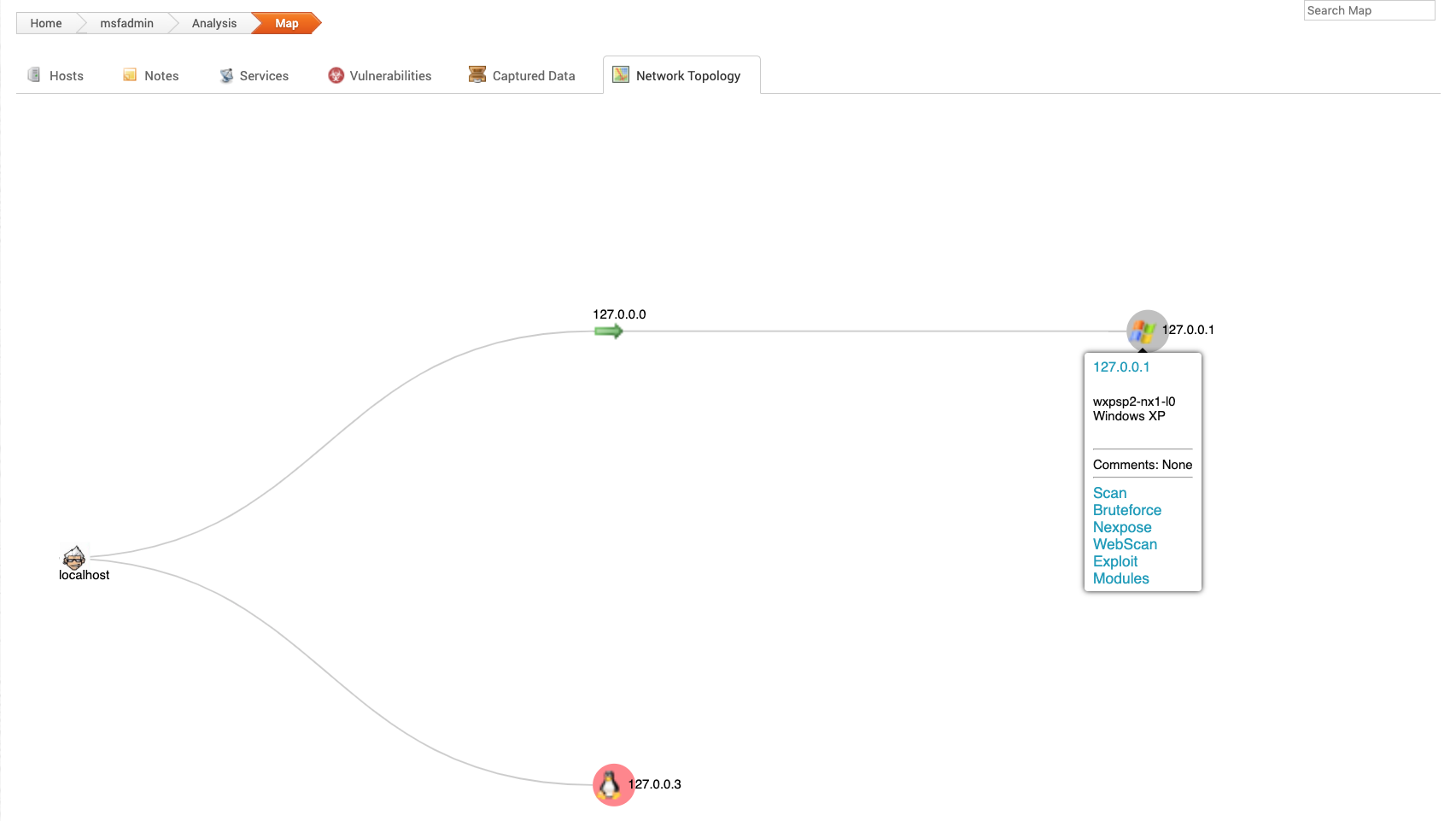
Network Topology
Click this tab to access a map of any hosts discovered on the network. It shows each host’s relation to each other. From there you can run scans and other modules.
The network topology provides insight into the types of applications and devices the target has in place. The more information that you can gather about a target, the more it will help you fine-tune a test for it.