Understanding Bruteforce Findings
After you launch the bruteforce attack, the findings window appears and displays the real-time results and events for the attack. To help you navigate the data, the findings window is organized into two major tabs: the Statistics tab and the Task Log tab.
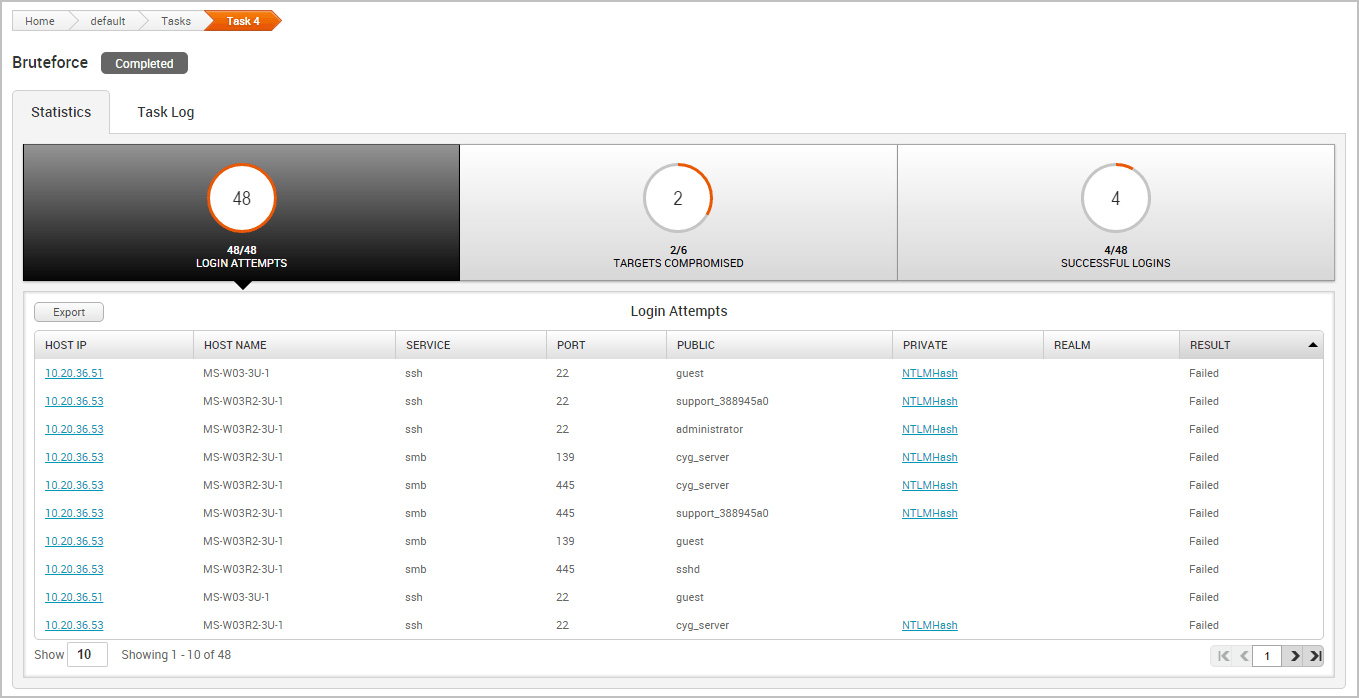
The Statistics Tab The Statistics tab tracks the real-time results for the following:
- The total number of login attempts
- The total number of targets compromised
- The total number of successful logins
Each statistic is displayed on its own tab. You can click on a tab to view the corresponding table for each statistic.
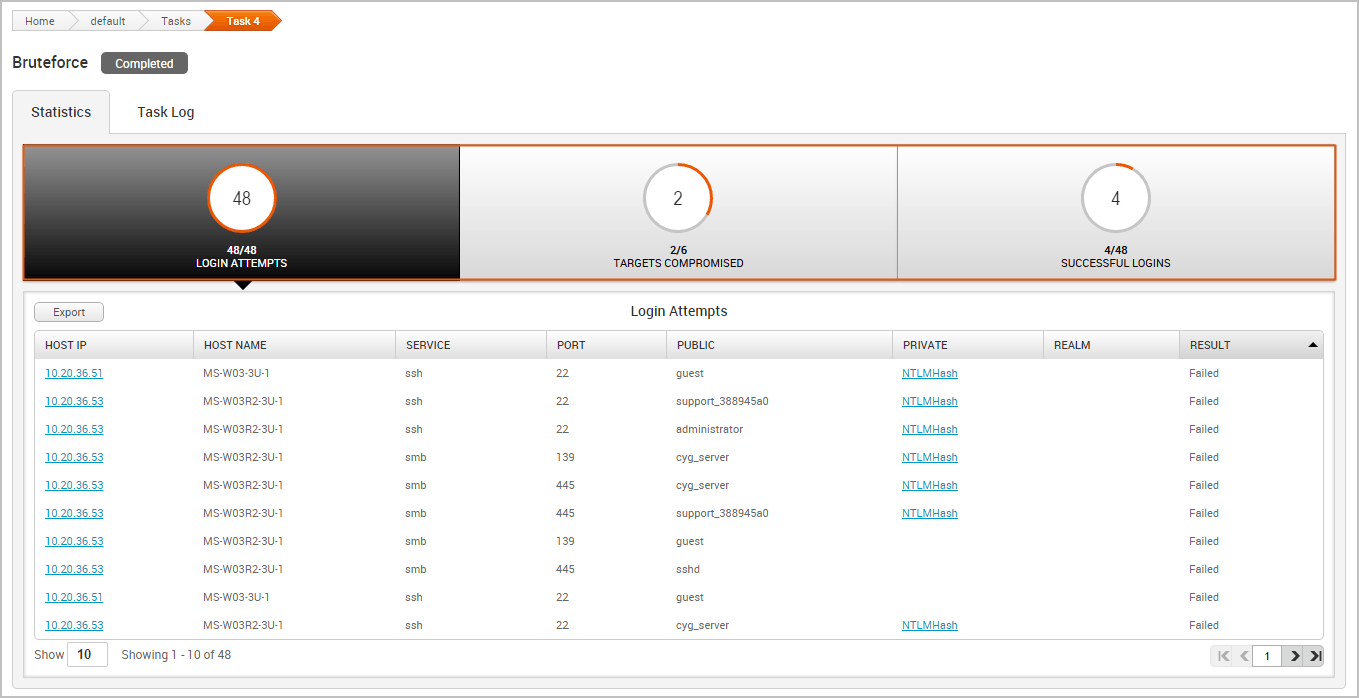
Viewing the Login Attempts Table
The Login Attempts table displays every login that the bruteforce attack has tried. The following information is listed for each login:
- The IP for each host
- Host name
- Service name
- Service port
- Public
- Private
- Realm type
- Login result
Viewing the Targets Compromised Table
The Targets Compromised table displays every target to which the bruteforce attack was able to successfully authenticate. The following information is listed for each compromised target:
- Host IP
- Host name
- Operating system
- Service name
- Service port
- Number of captured credentials
- Sessions*
If you configured the bruteforce attack to get sessions, the Targets Compromised table includes a Sessions column that lists the total number of sessions that were opened on each target. You can hover over the session count to view a list of links that you can use to access the details page for each session.
Viewing the Successful Logins Table
The Successful Logins table displays all the logins that the bruteforce attack was able to validate. The following information is listed for each login:
- Host IP
- Host name
- Operating system
- Service name
- Service port
- Public
- Private
- Realm type
- Sessions details*
*If you configured the bruteforce attack to get sessions, the Targets Compromised table has a Go to Sessions column that displays a link for each open session. You can click on the link to access the details page for the session. If you did not configure the bruteforce attack to get sessions, the Targets Compromised table has an Attempt Session column, which enables you to try to validate the login from the findings window. The Task Log Tab The task log tracks the activity for the bruteforce attack. It lists the target that is being bruteforced and the result for each guess attempt. A successful login will be highlighted in yellow, as shown below:
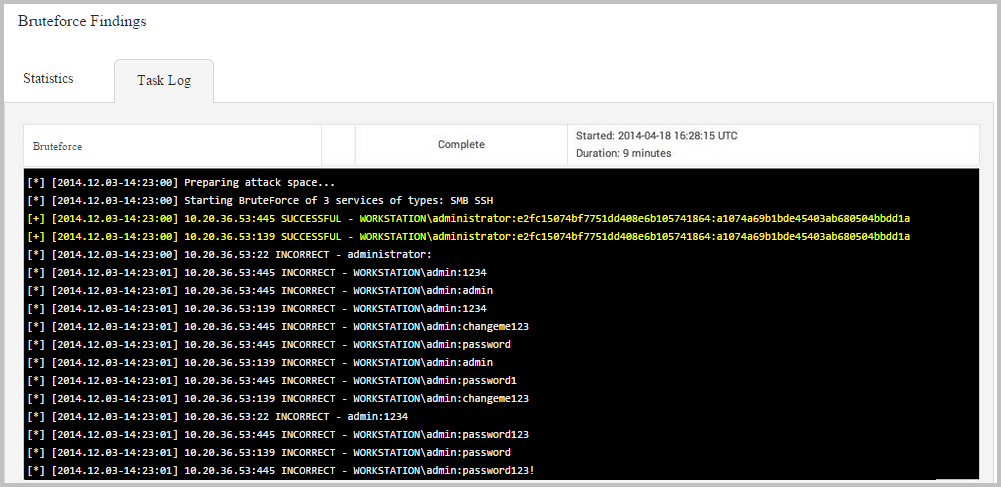
The task log also documents any errors or failures that occurred during the attack and can be used to troubleshoot any issues related to the bruteforce run. This is especially helpful if, for example, the attack has been running for a long time, appears to be hanging, or does not complete.