Trigger Workflows with Slack ChatOps
Automation (InsightConnect) ChatOps triggers allow you to use Slack messages to run workflows and create jobs. This allows your teams to quickly and easily perform security tasks without having to navigate away from Slack.
Before configuring the trigger in Automation (InsightConnect), you’ll first need to configure Slack for ChatOps to make sure Slack and Automation (InsightConnect) communicate correctly.
How it Works
ChatOps triggers listen for predetermined chat behavior in your preferred chat environment. With Slack ChatOps, you can trigger workflows by mentioning the Rapid7 Automation (InsightConnect) Slack app with match parameters in the message or by mentioning the app in specified channels.
To trigger workflows with Slack ChatOps:
- Make sure you have the Rapid7 Automation (InsightConnect) Slack app in your organization’s workspace
- Make sure the workspace is available in Automation (InsightConnect)
- Configure the match parameters for trigger mentions in Automation (InsightConnect)
- Type messages into Slack that match the configurations you set in Automation (InsightConnect)
Configure a Slack ChatOps Trigger in Automation (InsightConnect)
ChatOps triggers are slightly different than ChatOps steps in a workflow. You will need to configure different fields for the Slack application to listen to before triggering a workflow.
To set up a Slack ChatOps trigger in a new workflow:
- Choose Slack App for the trigger type. You can find this under the “From Chat Apps” category.
- Click Continue.
- Select the Slack workspace that will send data to the ChatOps trigger, or add a new Slack workspace. Click Continue.
- Select the New Message action, then click Continue.
- Name the trigger and add an optional description.
- Configure the trigger input fields to the specifications in the following table. Click Continue.
| Input Field | Configuration Specifications |
|---|---|
| Match Channel | Enter the channel name or regex (omit the # prefix) you want the chat bot to listen on. You can also direct the bot to listen to channels based on regular expressions. If this field is left blank, the Slack app will listen for mentions in any channel. |
| Match Text | Enter a regular expression you want the chat bot to trigger on when mentioned in the Slack channel. Workflows will only execute if the Slack app is mentioned with the matched term. Other mentions to the chat bot will be ignored. |
| Type | Choose from one of the following: * direct: workflows can be triggered only by messages in a one-to-one direct message with the Rapid7 Automation (InsightConnect) app. * group: workflows can be triggered by references to @Rapid7 Automation (InsightConnect) in any channel* any: workflows can be triggered by references to @Rapid7 Automation (InsightConnect) in any channel in your workspace, or direct messages with the app. This field encompasses both direct and group types This field is required and cannot be left blank. If you only configure this field and leave the two “Match” fields blank, workflows with this trigger will execute jobs every time the chat bot is mentioned by name with @. |
You can now add steps to your workflow.
Trigger a Workflow from Slack
To trigger a workflow from Slack, mention the Rapid7 Slack App by typing @Rapid7 Automation (InsightConnect) into a message.
Trigger Configurations for Slack
You can limit the Slack content that will trigger the workflow. The more fields you configure, the more restrictive your trigger conditions will be, which prevents Automation (InsightConnect) from creating accidental jobs.
No Match Fields Configured
If you don’t set anything in the “Match Channel” or “Match Text” fields, the Slack bot will trigger your workflow on every “@Rapid7 Automation (InsightConnect)” mention in your workspace.
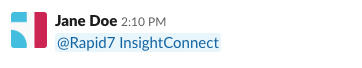
Match Channel Only
The workflow will only execute when @Rapid7 Automation (InsightConnect) is mentioned in the channel you entered in the “Match Channel” field when you configured your trigger. Mentions in other channels will not trigger this workflow.
Match Text Only
The workflow will only execute when @Rapid7 Automation (InsightConnect) is mentioned with the regex pattern you entered into the “Match Text” field when configuring your trigger. Mentions including other text patterns will not trigger this workflow.
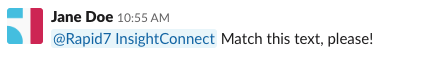
For example, if your “Match Text” field was configured for the string Match this text, please!, the following Slack message would correctly trigger the workflow.
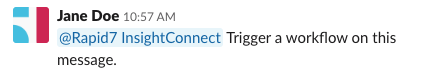
If you typed the following Slack message instead, the workflow would not execute.
Match Channel and Match Text Configured
Configuring both match fields further limits the trigger conditions. Calls made to @Rapid7 Automation (InsightConnect) must be sent in the specified channel and contain the match text pattern. Messages that only meet one of the requirements will not trigger this workflow.
Automatically Extract Indicators from a Chat Message
Our chatbot automatically extracts commands and common network or security indicators from your ChatOps messages. You can use these variables to configure additional workflow actions without the hassle of manually parsing that information yourself.
Each of your ChatOps messages follows the same format: @Rapid7 Automation (InsightConnect) [command] [indicator]. An example command might look like this: @Rapid7 Automation (InsightConnect) block-host 1.1.1.1. We automatically extract and capture commands, like block-host in this case, in a variable called $first_word.
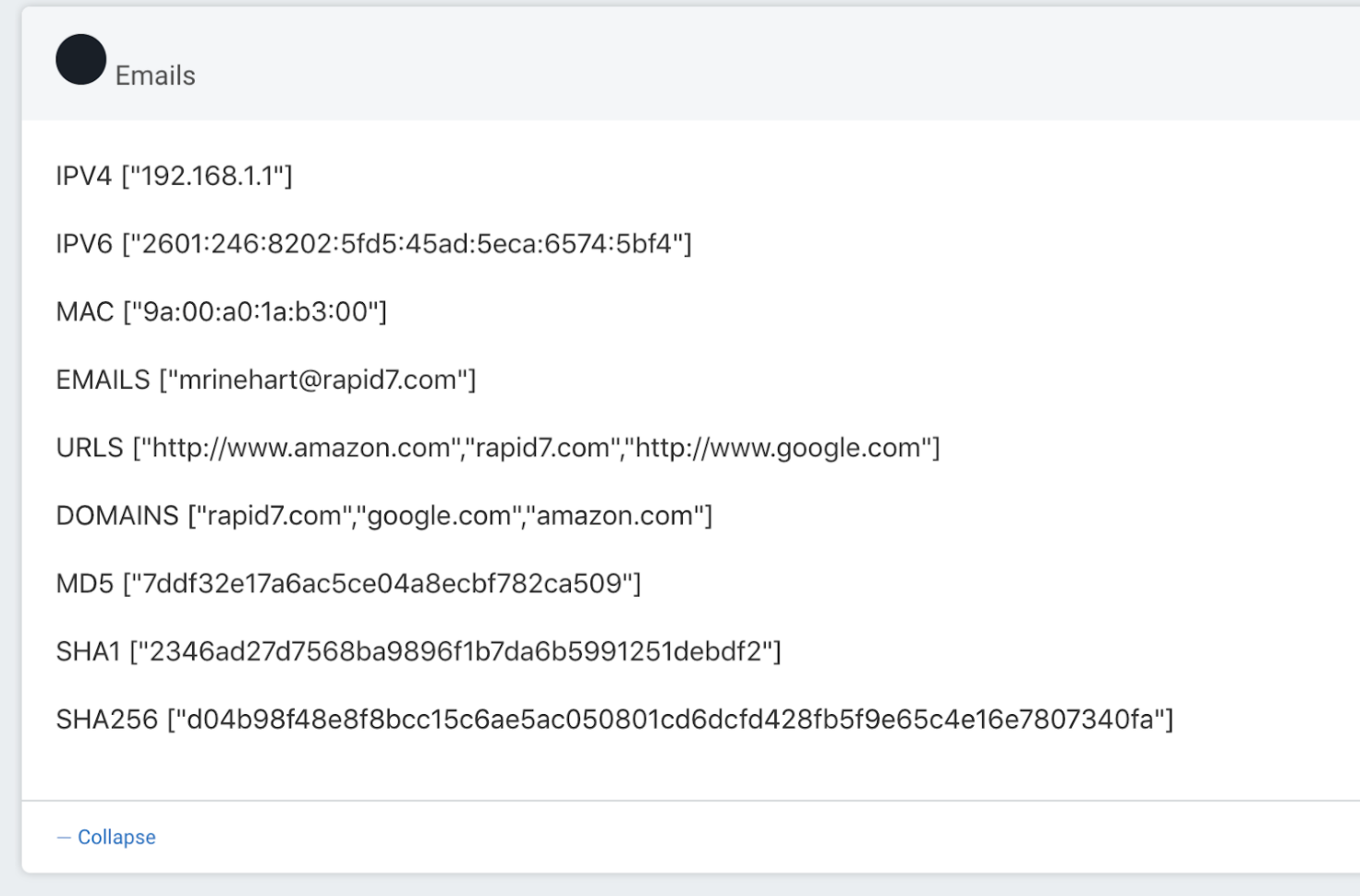
When your command is followed by a commonly used network or security indicator, our chatbot detects the format of the indicator, extracts it automatically, and stores it in an output variable.
These are the commonly used network and security indicator types we capture and store:
- IP addresses (IPv4 and IPv6)
- MD5 hashes
- SHA1 hashes
- SHA256 hashes
- MAC addresses
- Email addresses
- Domain names
- URLs
You can use these output variables later in your workflow to easily configure further actions. For example, add a hash to a denylist, enrich a URL or domain with a threat intelligence plugin, delete an email from user inboxes, or block an IP address, all without having to parse these indicators out of your chat messages manually.