Azure AD Plugin Setup
AD LDAP (Active Directory Lightweight Directory Access Protocol) is an application protocol for querying and modifying items in Active Directory. This plugin queries Microsoft’s Active Directory service to programmatically manage and query an Active Directory environment.
Azure AD Admin Plugin Configuration Guide
Azure Active Directory (Azure AD) is Microsoft’s enterprise cloud-based identity and access management (IAM) solution. The Azure AD Admin plugin for Automation (InsightConnect) supports:
- Add user to group
- Add user to group by ID
- Create user
- Disable user account
- Enable user account
- Force user to change password
- Get group by name
- Get user info
- Remove user from group
- Revoke sign in sessions
- Update user info
There are few things you need to do before you get started:
Collect Configuration Information
To collect configuration information, Log into your Azure portal at Azure .
Application ID
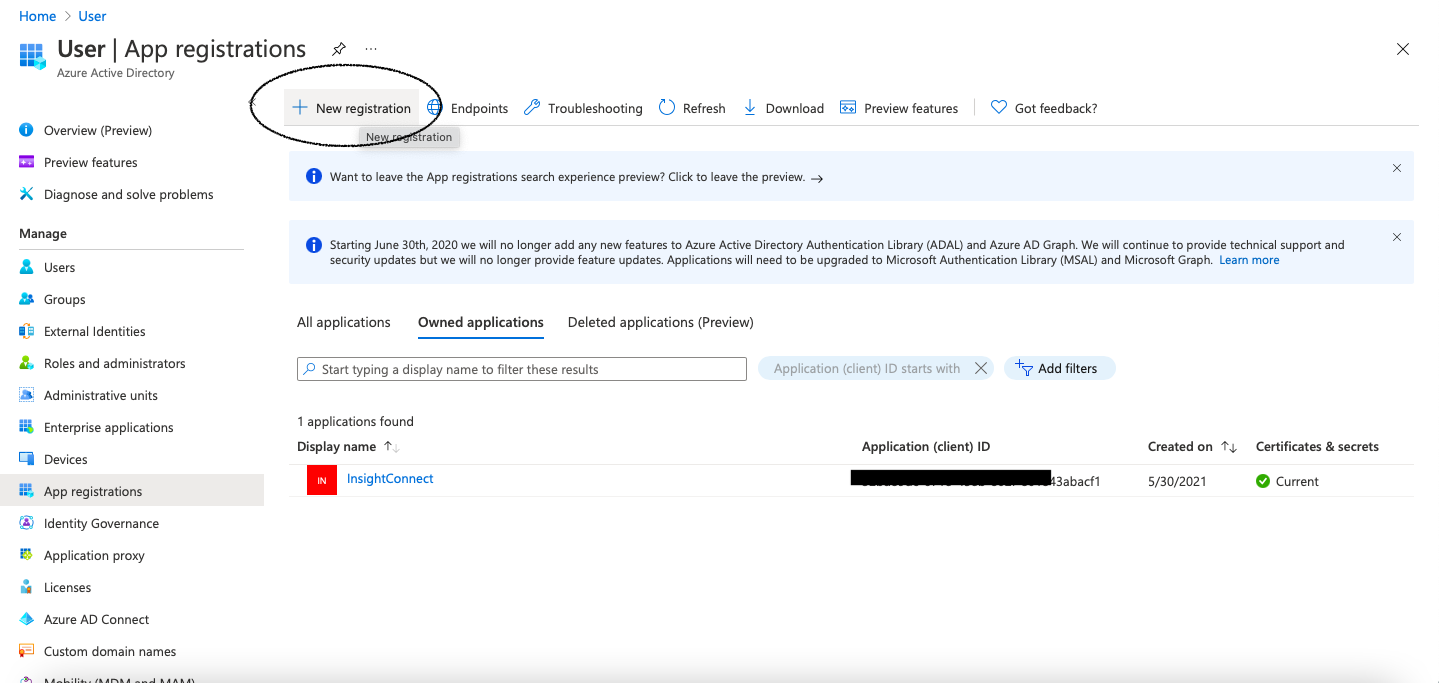
- In the side navigation of the Azure portal, click Azure Active Directory, then select App Registrations in the secondary navigation menu.
- Click New Registration.
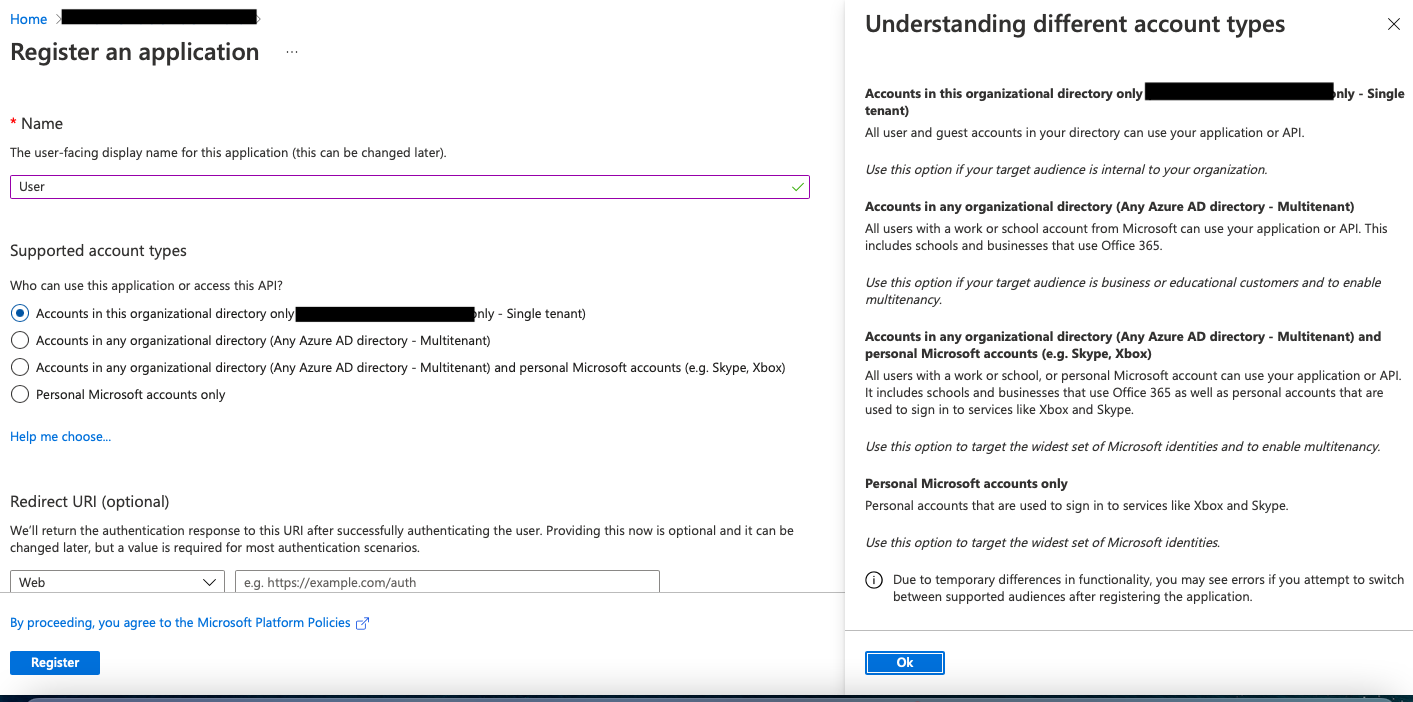
- Complete the form with
Automation (InsightConnect)for the name,Web app/APIfor the application type andhttps://login.microsoftonline.comfor the sign in URL. Then click Create. - Save the application registration to Azure, copy and save Application ID.
Application Secret Key
Azure uses asymmetric keys to authenticate and secure communications with other applications. This can be set up in the Application menu, where you will need to create a new key in Azure to use it with an Automation (InsightConnect) connection.
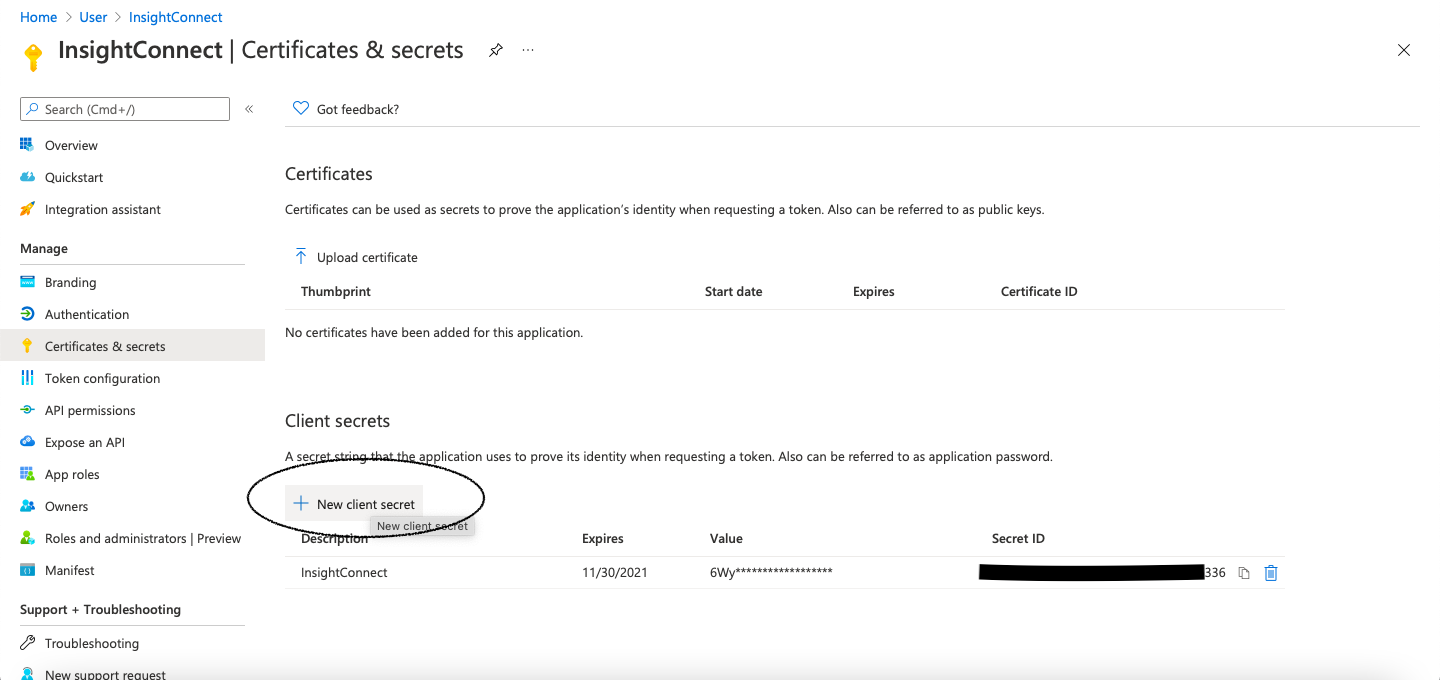
- Select newly registered application.
- Click on Certificates & secrets.
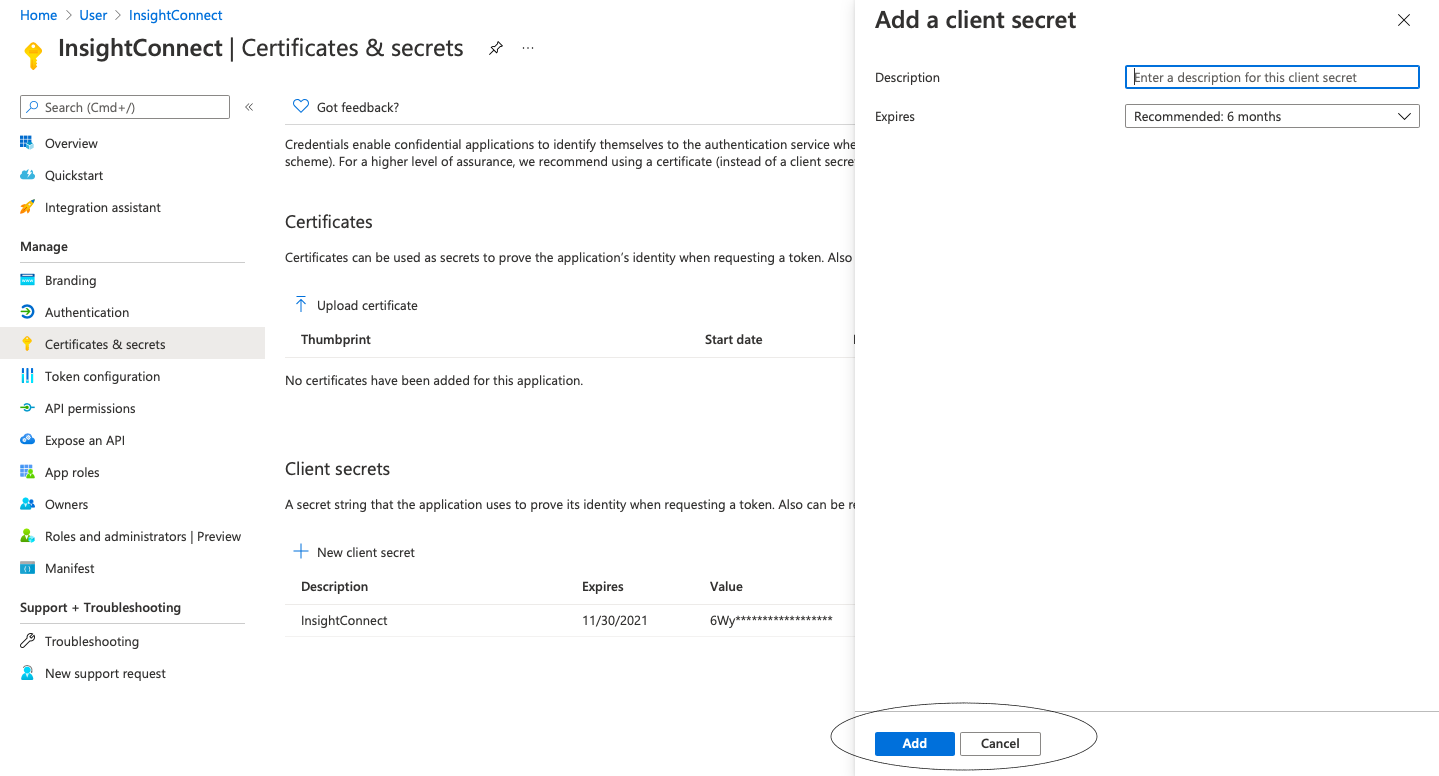
- Select New client secret.
- Give the key a description and set the duration of the key. It will expire after the duration you set. Then click on Add.
- Azure will generate a value for your new key. Copy and save this string now, as you will not be able to see and retrieve it after you leave this page in the Azure Portal.
Tenant ID
The tenant ID can be found in the side navigation of Azure Active Directory. Click Overview to find it.
If you need to create a new Tenant ID, select Overview then choose Manage Tenants and click Create.
Configure Application Permissions
After registering the new Application in Azure, you will need to configure permissions needed for the Azure AD Admin Plugin. To set up all of the permissions below, admin role is required.
- The application this plugin connects needs the following permissions:
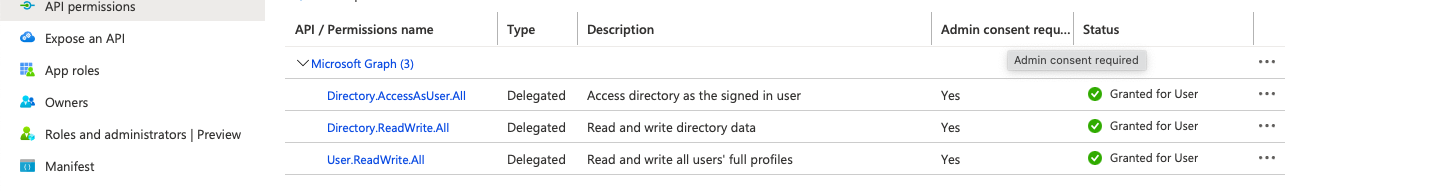
- Directory.AccessAsUser.All
- Directory.ReadWrite.All
- User.ReadWrite.All
- Because all actions in this plugin are user and directory operations, which are administrator tasks, the above permissions are required.
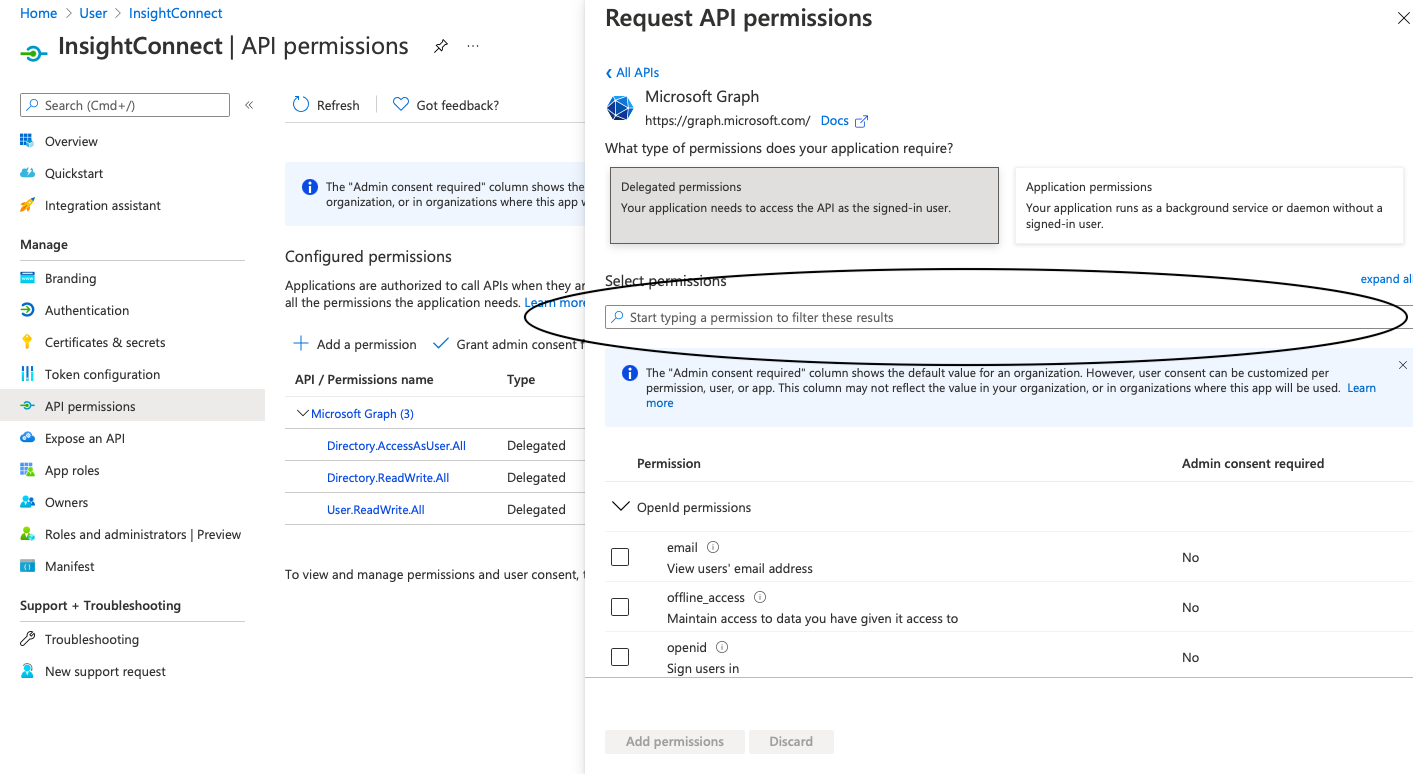
- In Application menu you will find API Permissions, click on it.
- Select Add Permision, then choose Microsoft API’s, from Microsoft Graph, choose Delegated Permissions.
- From following options select and save:
Directory.AccessAsUser.All , Directory.ReadWrite.All , User.ReadWrite.All.
Add Application to the Global Administrator Role
This can be done in Application menu where you have created Certificate & Secrets and API permissions.
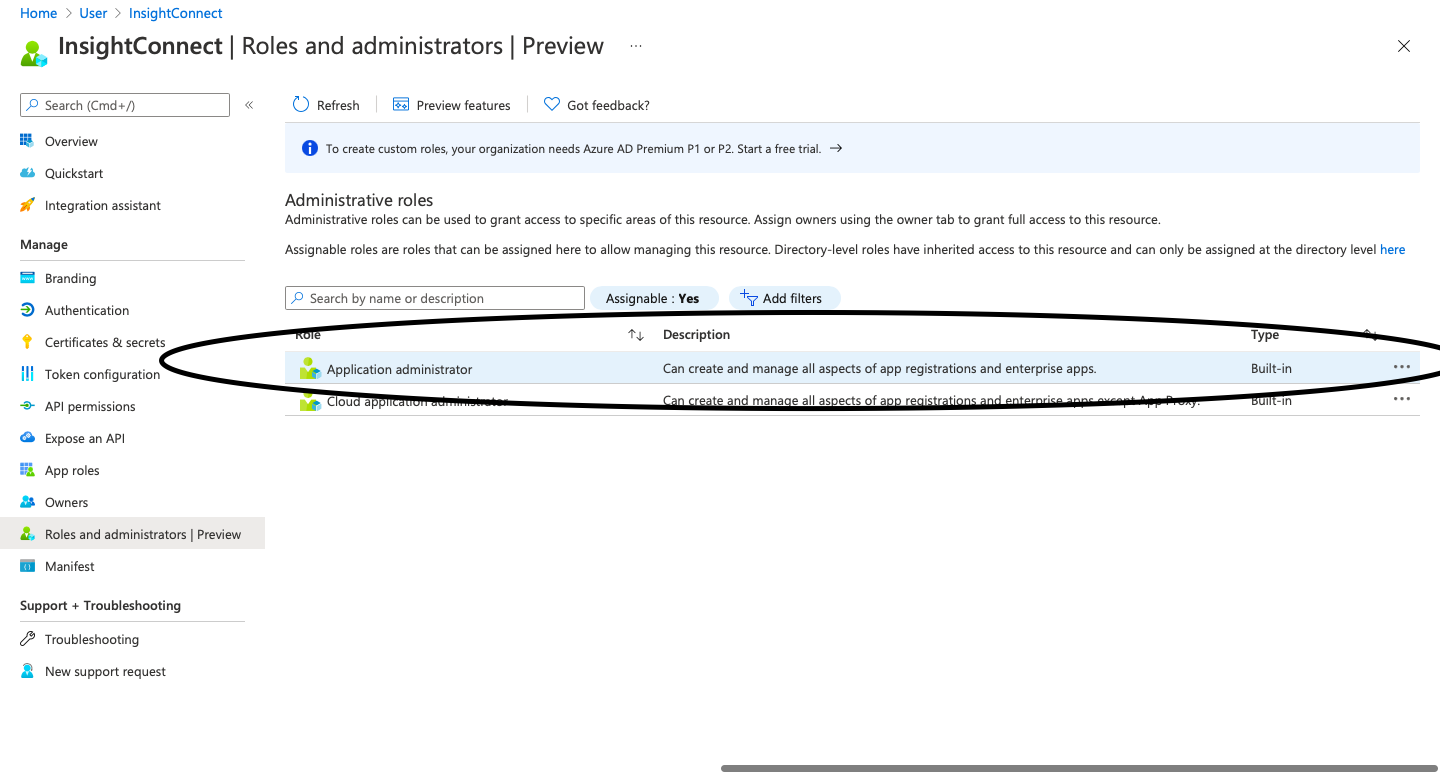
To add the application to the global administrator role, the following steps are necessary:
- Select Roles and Administrators
- Then click on Global Administrator
- And then assign to global administrator role
Troubleshoot the Azure AD Admin Plugin
If your Azure AD Admin plugin fails to authorize, check the plugin’s error logs. It is likely that the connection settings are invalid. Verify that the Application ID, Tenant ID, and Secret Key are correct in your Azure AD Admin connections.
Authentication request status: 401 will tell you that Secret Key is invalid. For example:
Connect: Connecting...
Updating auth token...
Getting token from: https://login.microsoftonline.com/5c824599-dc8c-4d31-96fb-3b886d4f8f10/oauth2/token
Starting new HTTPS connection (1): login.microsoftonline.com:443
https://login.microsoftonline.com:443 "POST /5c824599-dc8c-4d31-96fb-3b886d4f8f10/oauth2/token HTTP/1.1" 401 471
Authentication request status: 401Authentication request status: 400 will tell you that Tenant ID or Application ID is invalid. For example:
Connect: Connecting...
Updating auth token...
Getting token from: https://login.microsoftonline.com/5c824599-dc8c-4d31-96fb-3b886d4f8f10/oauth2/token
Starting new HTTPS connection (1): login.microsoftonline.com:443
https://login.microsoftonline.com:443 "POST /5c824599-dc8c-4d31-96fb-3b886d4f8f10/oauth2/token HTTP/1.1" 400 778
Authentication request status: 400